Introduction
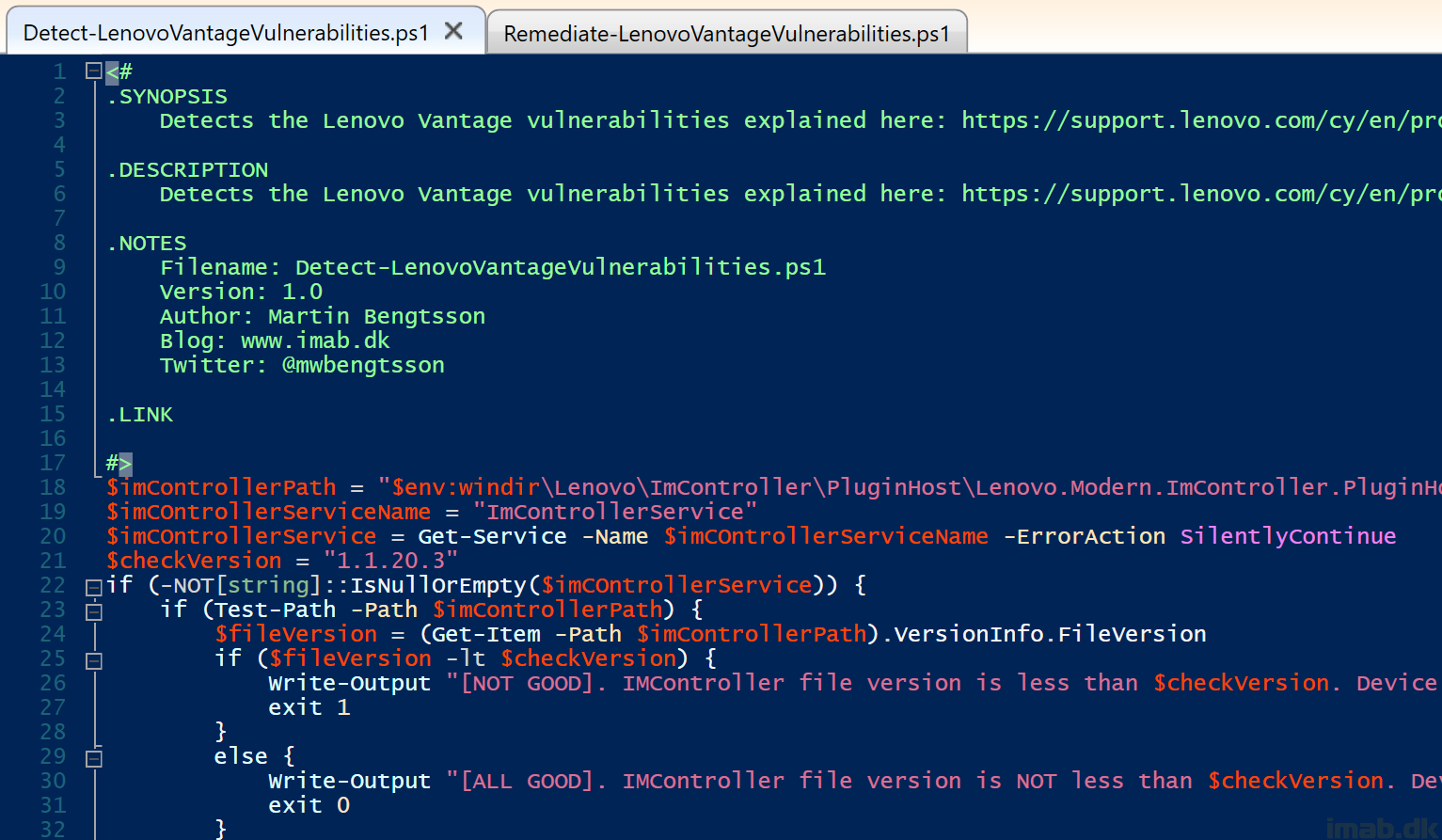
Just a quick blog post, on how to detect and remediate the Lenovo Vantage Vulnerabilities disclosed this week.
- More information here: Lenovo Vantage Component Vulnerabilities – Lenovo Support CY
- And here: Lenovo laptops vulnerable to bug allowing admin privileges (bleepingcomputer.com)
This surely has been an eventful week for most IT professionals, beginning with the #Log4j nightmare, and now ending with some Lenovo Vantage fun. Joking aside, this fix is pretty easy, but making sure and proving the vulnerability has been mitigated throughout your environment, might be something else. This post explains how I did.