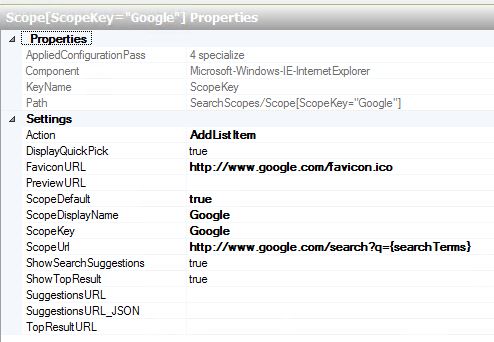
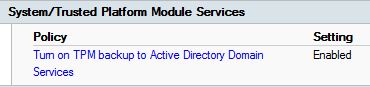
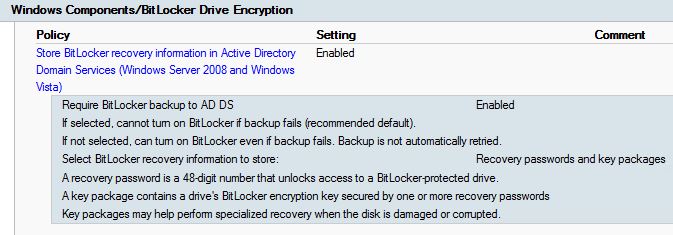
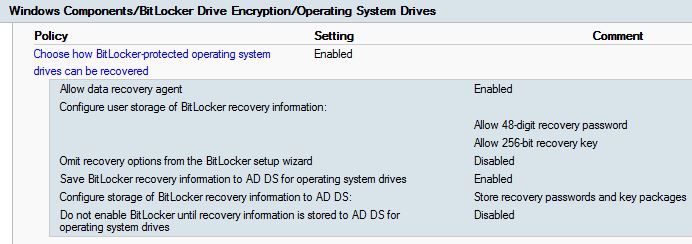
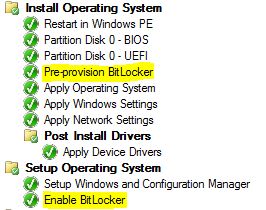
Quick and short post.
Nowadays if a BSOD happens in Windows, the OS automatically restarts the system. The users in an enterprise never notice that an BSOD just occured, but will find their computer automatically rebooting and as a result hereof, the users calls the helpdesk.
If a BSOD just happened, windows will log the errors in .dmp files. Typical location is %SystemRoot%\MEMORY.DMP
To view the .dmp files, you will need the Windows Software Development Kit (SDK). This one is for Windows 8.1: https://msdn.microsoft.com/da-DK/windows/desktop/bg162891
Following the SDK, comes windbg.exe. This is the tool that allows you to view the content of the .dmp files.
Before opening any .dmp files, you will need to specify a symbol search path. You do so by launching WinDbg and click File -> Symbol File Path.
Insert following path: SRV*C:\Symbols*http://msdl.microsoft.com/download/symbols
(Replace the text in bold with your preffered location for the symbols)
More on the symbols: http://support2.microsoft.com/kb/311503