Introduction
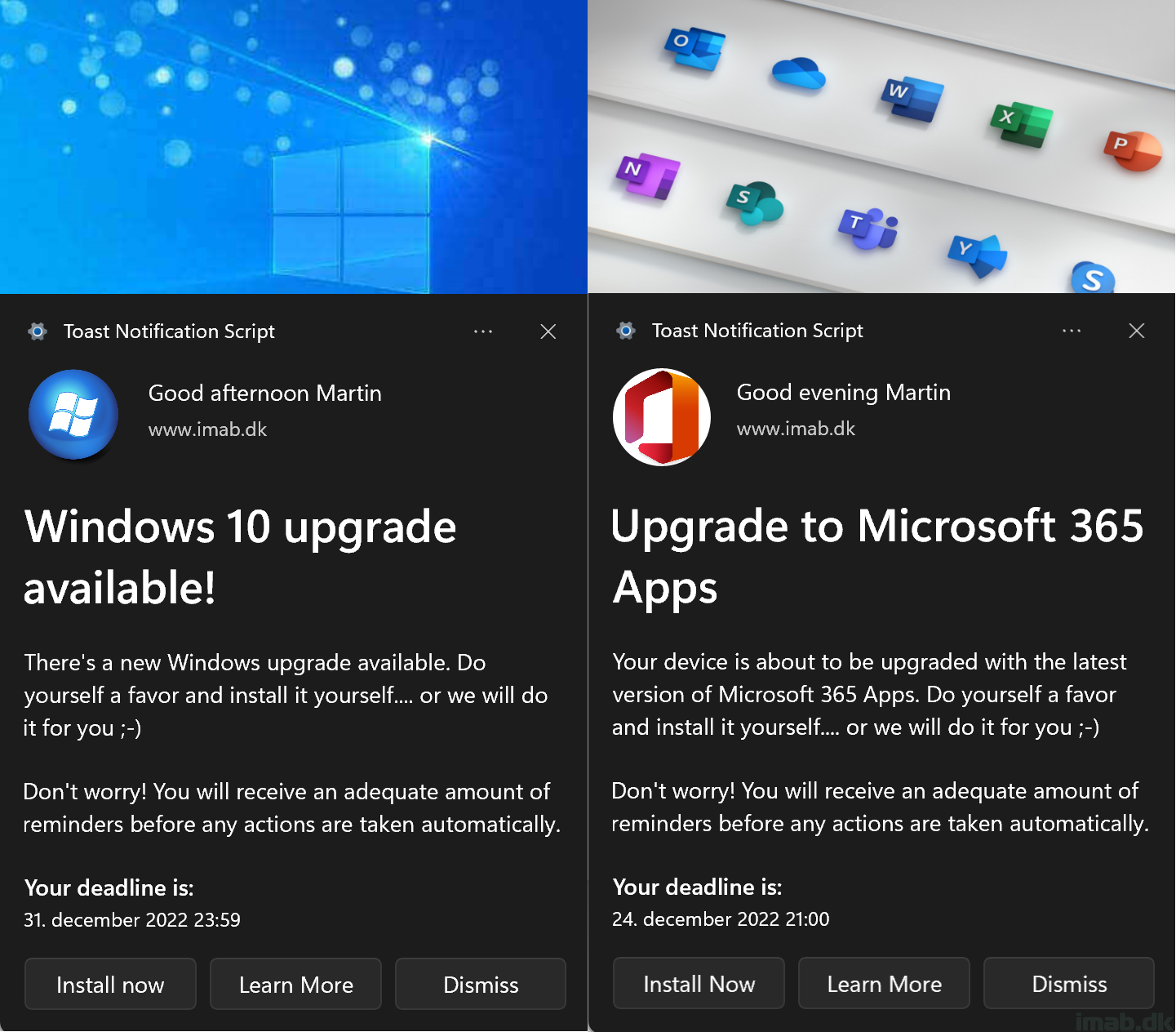
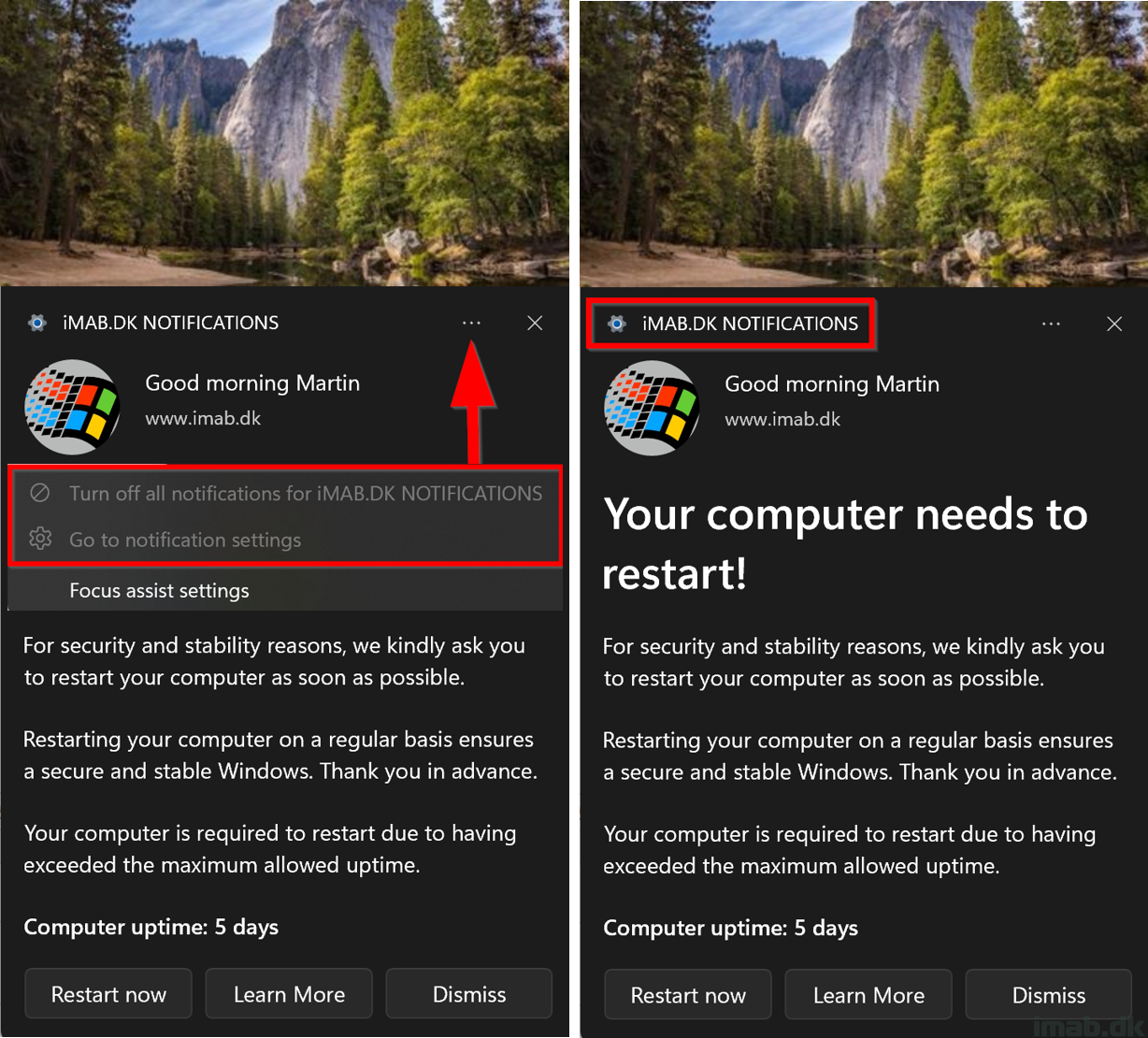
A new version of the Windows 10 Toast Notification Script is here. The script is now being on version 2.2.0.
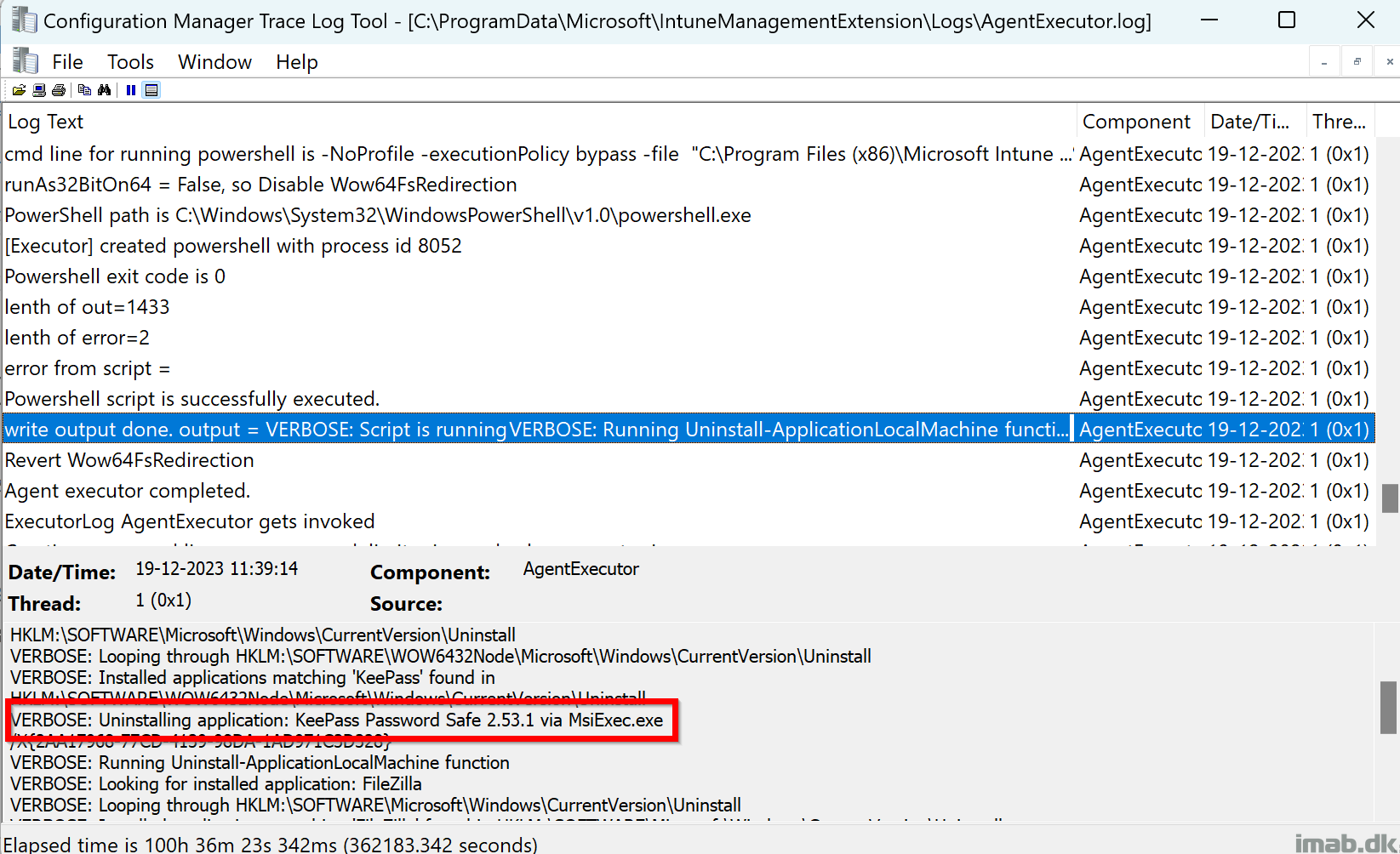
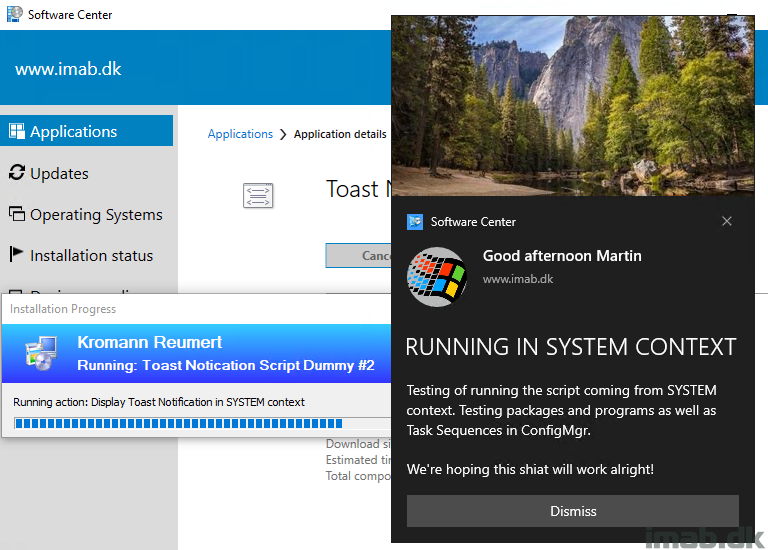
This version brings the option to run the script and thus display toast notifications coming from SYSTEM context.
A requirement has been so far, that the script is being run with the logged on user’s credentials. This is still recommended, but for scenarios where this is not possible, like running this with a task sequence (task sequences always run as local system), this new ability will give you the option to display toast notification for the logged on user, even if coming from local system context.
The work done here, with running the script under SYSTEM, is entirely done by Andrew. Thank you!
Also, with a built-in prevention of having multiple toast notifications being displayed in a row, the script is now also better at handling the re-run behavior in ConfigMgr. Having multiple toast notification displayed in a row, is something that can happen, if a device misses a deployment schedule. The nature of ConfigMgr is to catch up on the missed schedule, and this can lead to multiple toast notifications being displayed.
Read more…