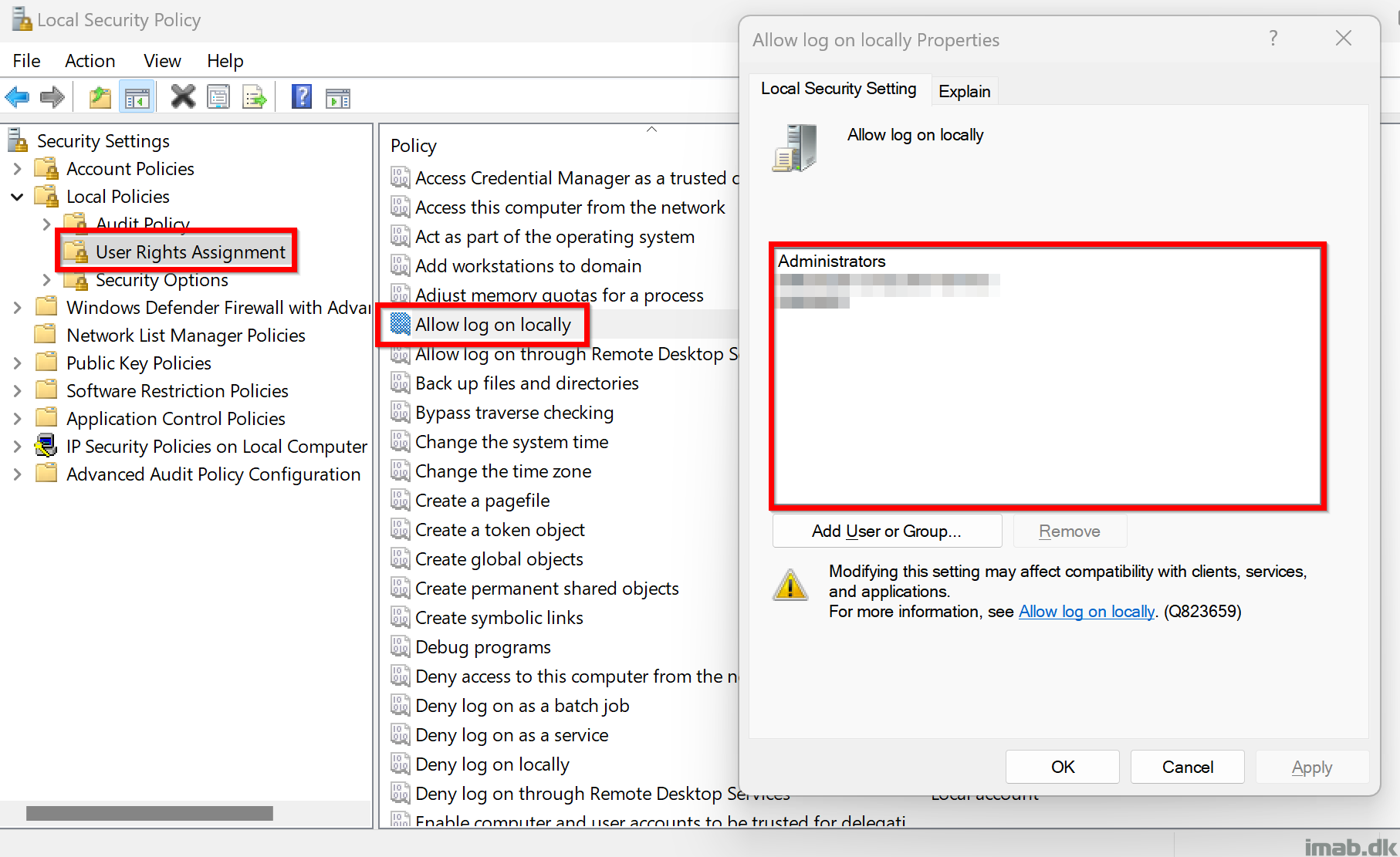
I know Microsoft Intune has the ability to configure this particular user rights assignment natively already. At time of writing, the new security baseline for Windows 11 23H2 in Intune configure this as well, restricting local logons to the built-in groups: Users and Administrators.
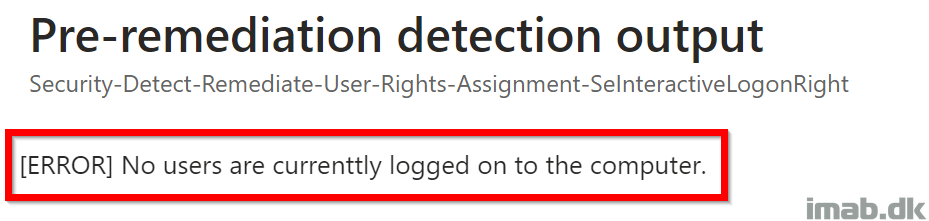
This solution does something else. This solution grabs the currently logged on user and configures the ‘Allow logon locally‘ policy to ONLY allow this very user as well as Administrators to be able to log on locally. A custom group is added as well for backup reasons. If no user is logged on, the script does nothing. More details down below.
The solution is made to prevent ‘stealing’ credentials from one user/device and be able to use it on another device within the same environment.
PowerShell
The script is located here on my GitHub repository: Proactive-Remediations/Detect-Remediate-LockToUser.ps1 at main · imabdk/Proactive-Remediations (github.com)
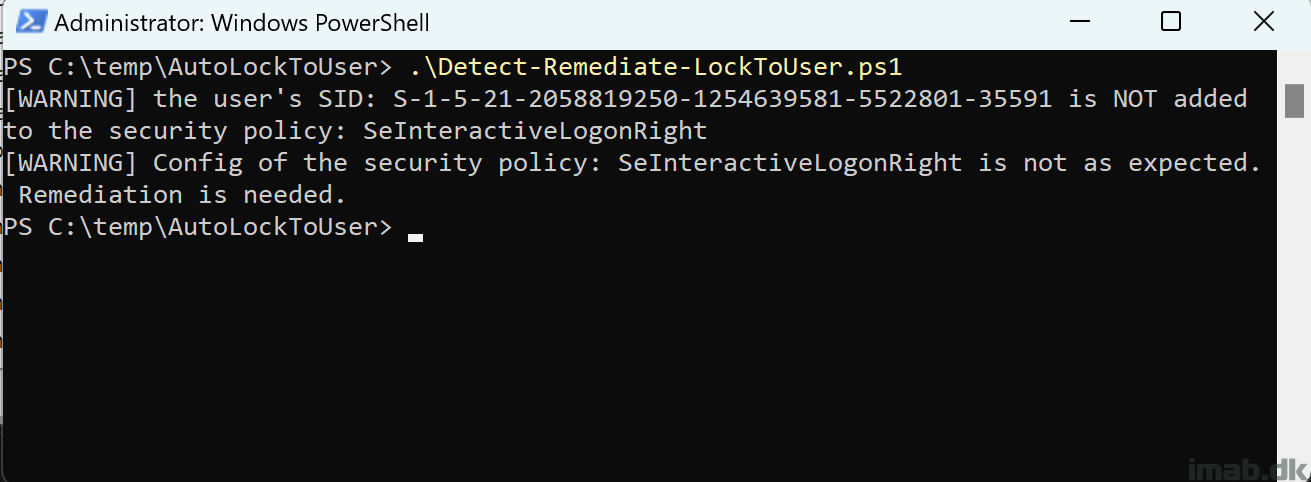
The script accepts 2 parameters: -runDetection and -runRemediation.
-runDetection
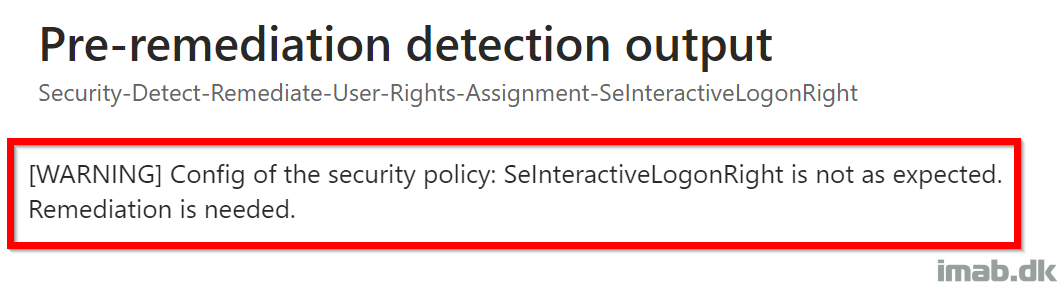
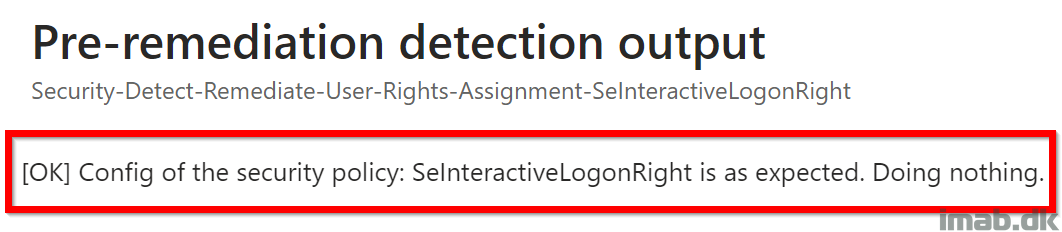
This portion of the script is detecting whether the logged on user is added to the ‘Allow logon locally‘ policy. If the user is not added, the script will exit with exit code 1, instructing Microsoft Intune to kick off the remediation script.
-runRemediation
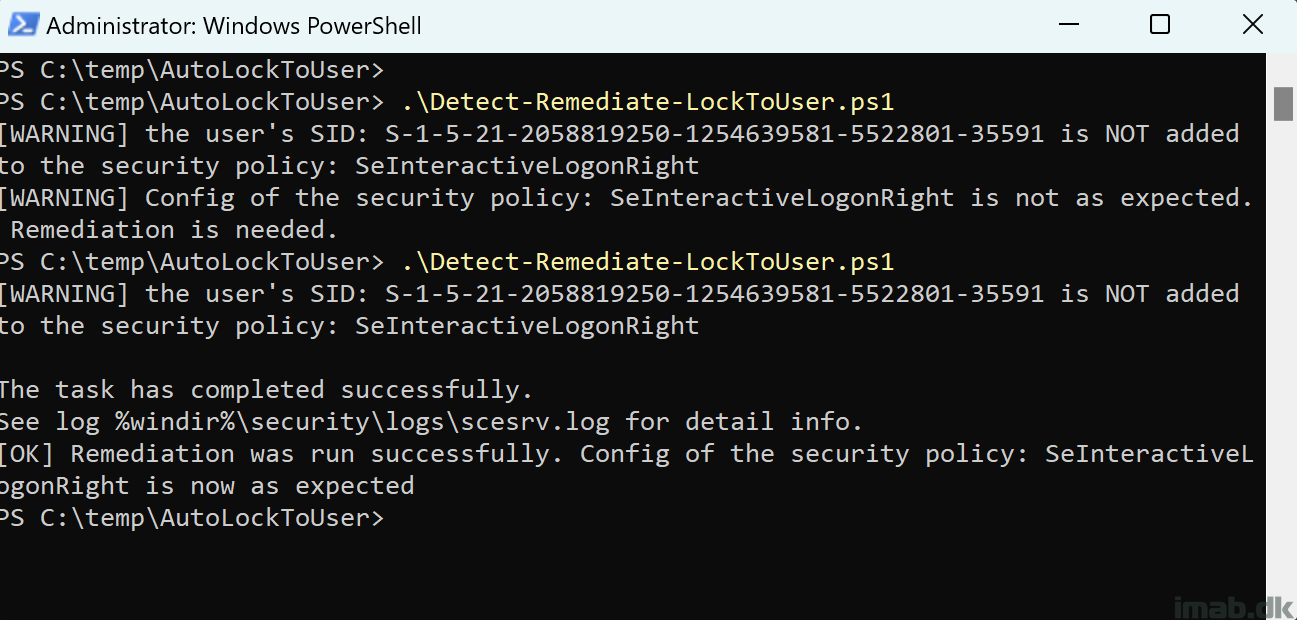
This portion of the script will add the currently logged on user to the ‘Allow logon locally‘ policy, add the additional $trustedGroup as well as remove the built-in group Users.
- Edit the $trustedGroup variable to suit your needs. Again, this is done in a hybrid environment with an on-premises AD. I haven’t tested this with Entra ID identities or groups.
Detect-Remediate-LockToUser.ps1
In headlines, the script does following:
- Queries the explorer.exe for the logged on user(s)
- Exports the current SecPol configuration to C:\Windows\Temp\secedit.tmp
- Translates the logged on user(s) common name to the corresponding SID
- Looks for the logged on user’s SID in the exported configuration
- If SID is not found and runRemediation is set to $true a new SecPol configuration will be written to C:\Windows\Temp\secedit.tmp and imported
- Exit script gracefully to signal either success or failure to Intune
Microsoft Intune
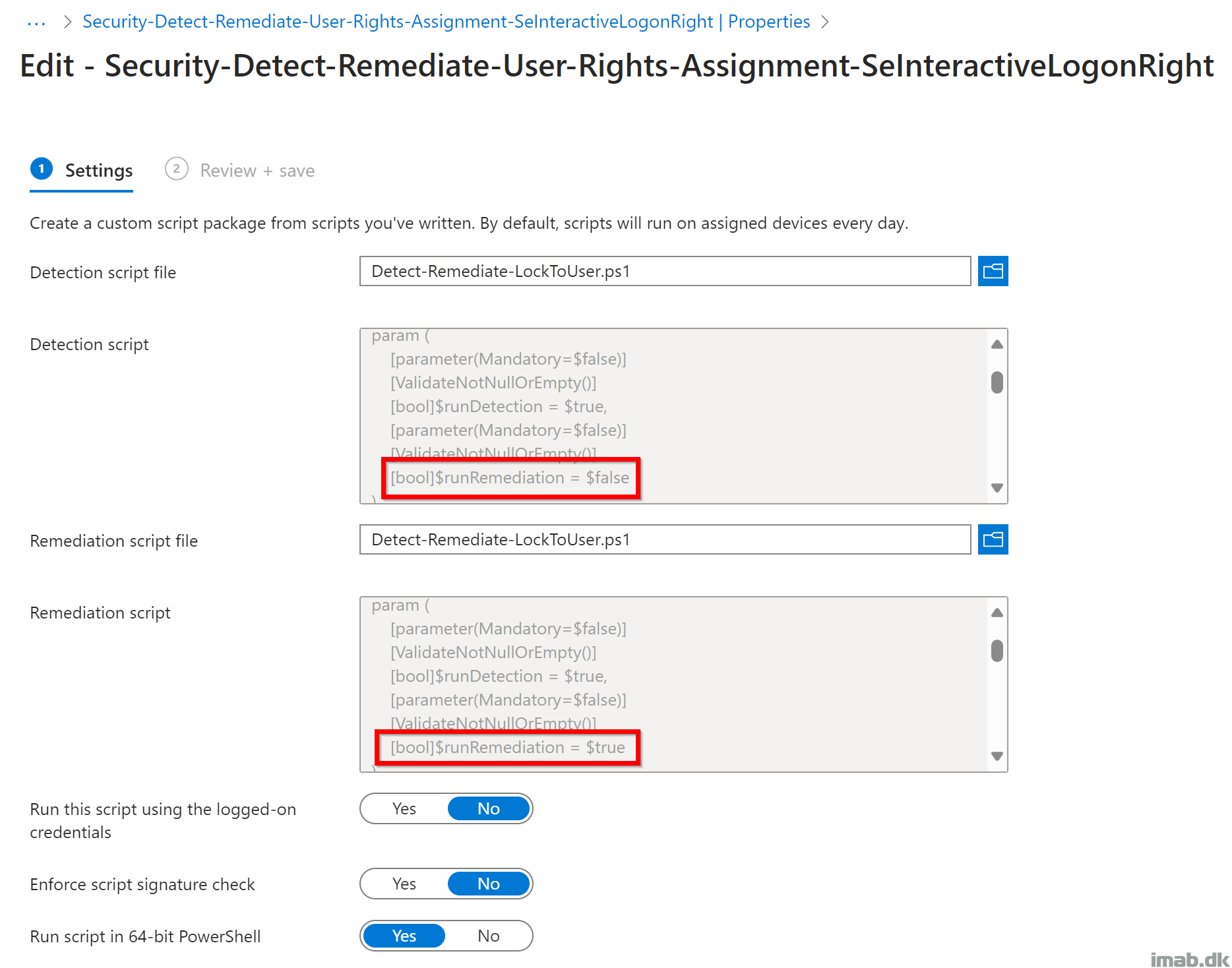
Put the script to use with Microsoft Intune and the Remediation feature. The script comes a standalone script, but running this with Microsoft Intune and Remediation, requires 2 scripts.
The first script where -runDetection is set to $true and -runRemediation is to $false. The second script where both are set to $true.
Device status
The script will output various status messages to Intune. This is useful when setting this up initially or troubleshooting.
The scripts are also logging their actions into C:\ProgramData\Microsoft\IntuneManagementExtension\Logs\HealthScripts.log
Final words
Disclaimer: Test this thoroughly! I have only tested this with on-premises active directory identities. I cannot stress this enough. If something is acting up, you will not be able to logon to the device where this script has been run on. 🙂