Introduction
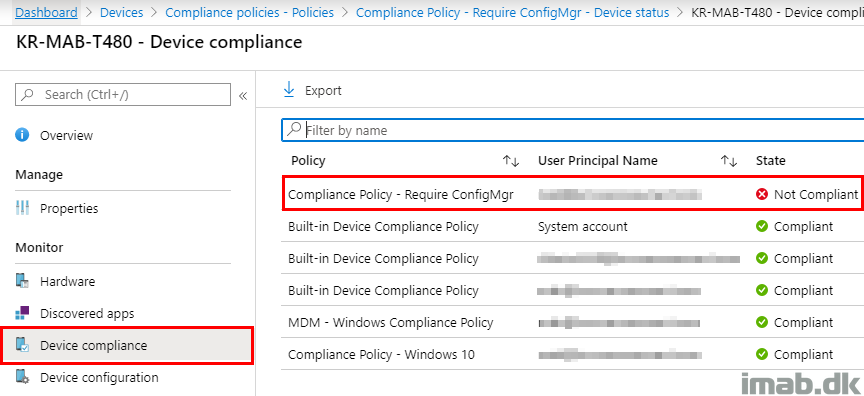
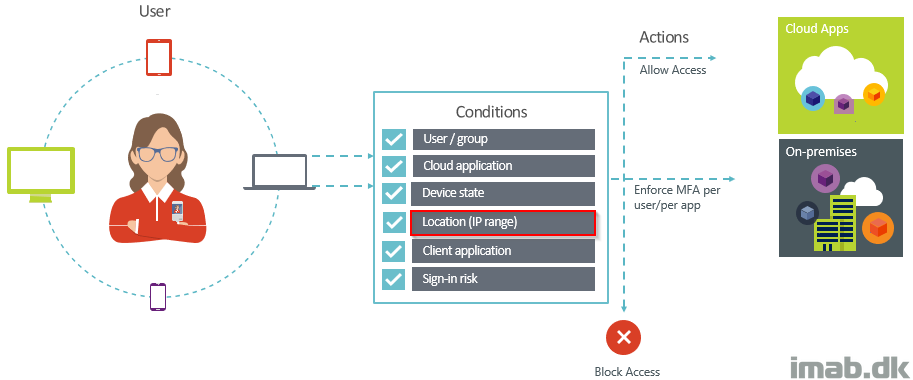
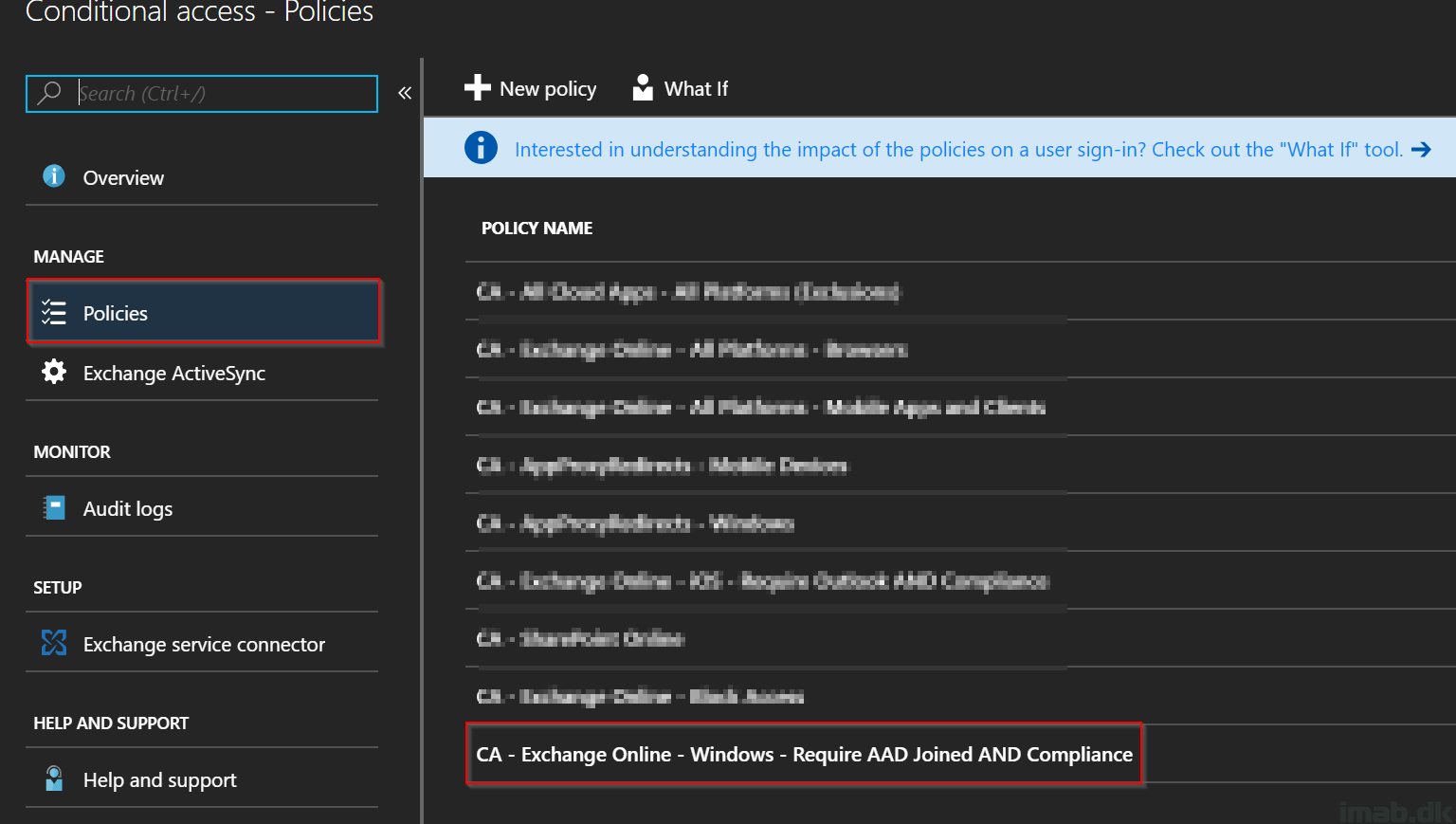
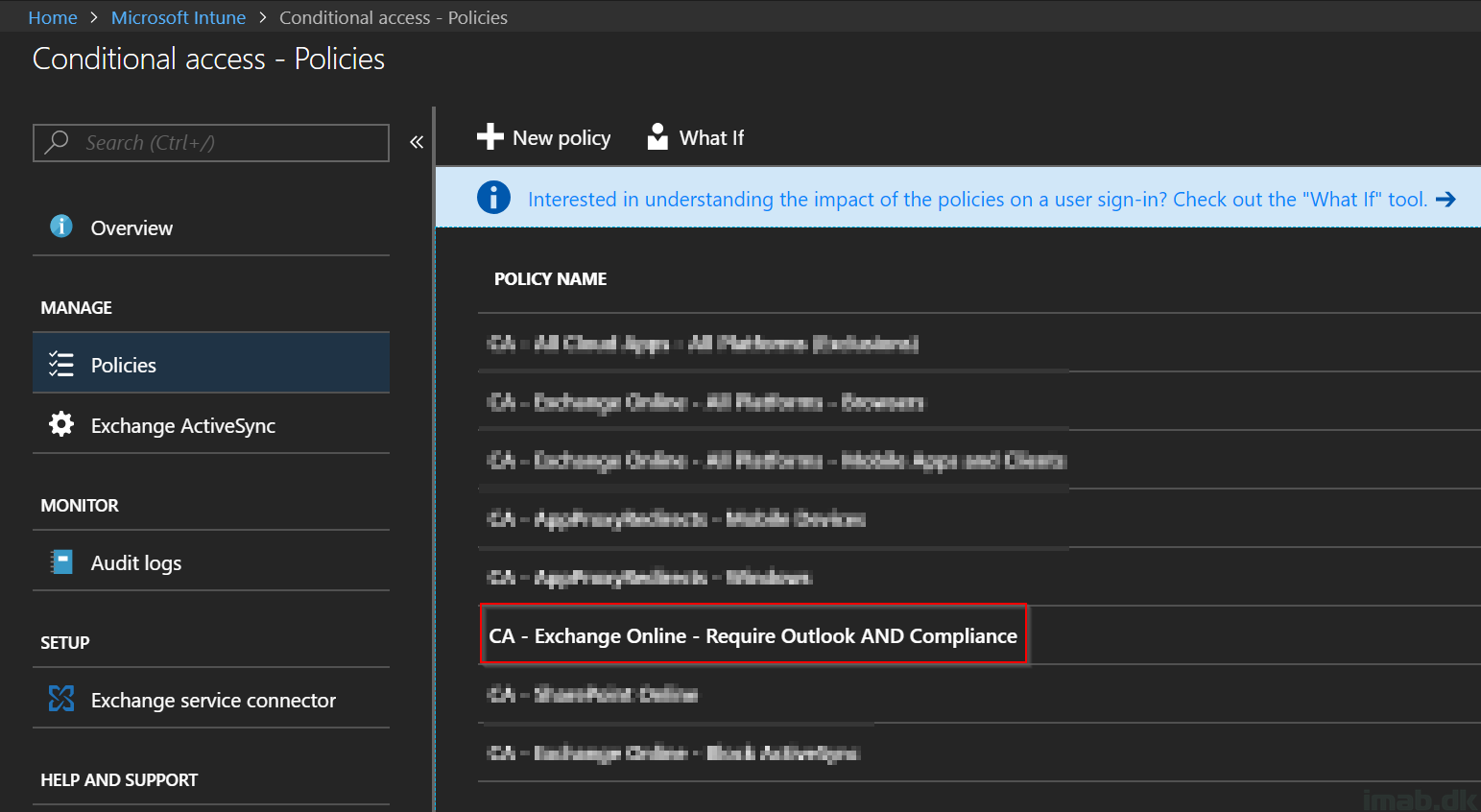
This must be one of my favorite features of Configuration Manager version 1910: Include custom configuration baselines as part of compliance policy assessment.
For a detailed description of the feature, I suggest you read the What’s new article.
In short, this enables us to assess device compliance based on almost anything and really extends the possibilities.
I will walk through the setup required and give you a quick and easy example on how to use this new awesome feature in a co-management scenario.