Introduction
NOTE: Script has been updated to v2004: https://www.imab.dk/deploy-rsat-remote-server-administration-tools-for-windows-10-v2004-using-configmgr-and-powershell/
Windows 10 v1909 was released to MSDN users last week, and true to tradition, I’m updating my Powershell script, enabling you to install RSAT for Windows 10 1909 automatically and unattended.
I received quite some feedback on my 1903 script, and thanks to that I made some improvements to the 1909 edition. That includes:
- Added test for pending reboots. If reboot is pending, RSAT features might not install successfully
- Added test for configuration of WSUS by Group Policy
- If WSUS is configured by Group Policy, history shows that additional settings might be needed for some environments
Powershell
The script requires administrative rights as well as access to the Internet (RSAT is installed through Microsoft Update).
The script is built around Get-WindowsCapability, Add-WindowsCapability and Remove-WindowsCapability.
Yet again the script comes with 4 options:
- -All (-All is installing ALL the features within the RSAT bundle)
- -Basic (-Basic is only installing AD DS, DHCP, DNS, Group Policy Management and Server Manager)
- -ServerManager (-ServerManager is only installing the Server Manager)
- -Uninstall (-Uninstall removes all RSAT features again)
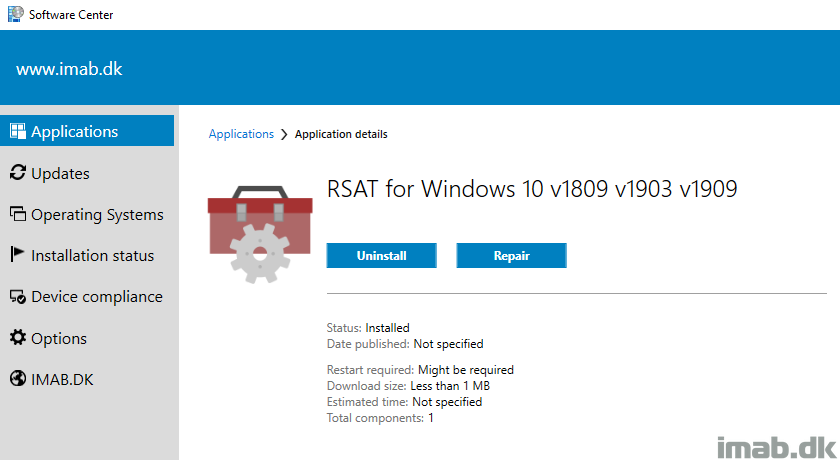
Below an example of running the script manually with the -Basic parameter on Windows 10 1909
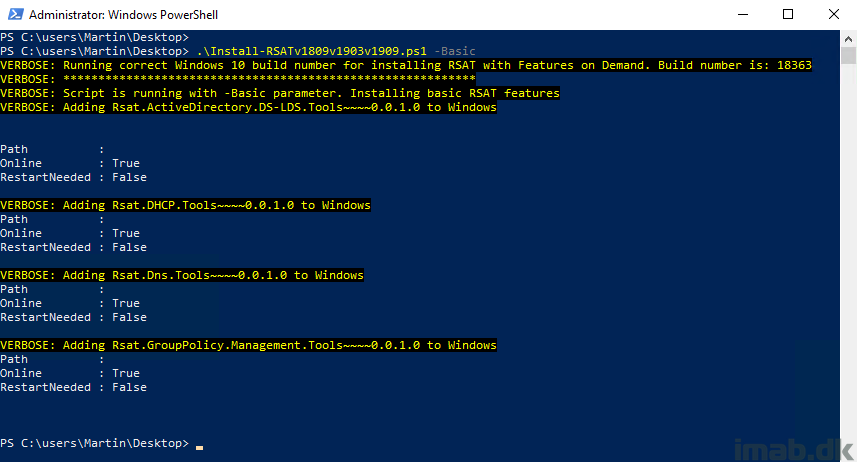
And another example of running the script manually with the -Uninstall parameter on Windows 10 1909
Notice the extra logging if WSUS seems to be configured with Group Policy.
Configuration Manager
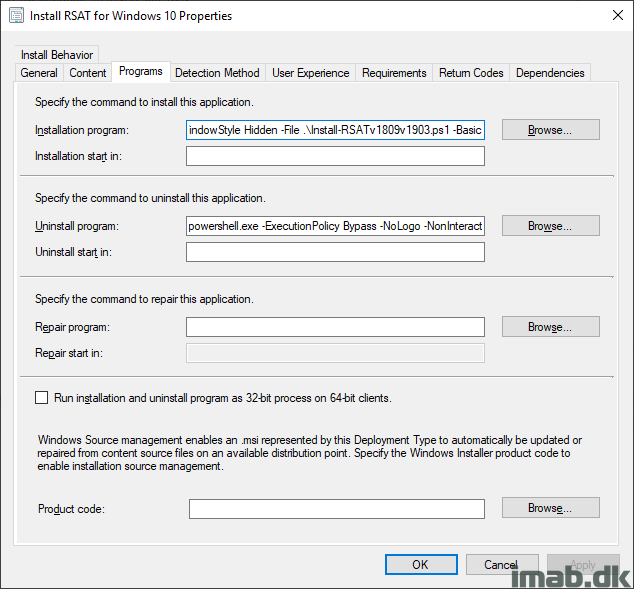
I’m putting the Powershell script to use with an application in SCCM. While this is pretty standard SCCM, I have included a few snippets of the application below.
The installation program:
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -File .\Install-RSATv1809v1903v1909.ps1 -Basic
The uninstall program:
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -File .\Install-RSATv1809v1903v1909.ps1 -Uninstall
Download
https://gallery.technet.microsoft.com/Install-RSAT-for-Windows-75f5f92f
ENJOY 🙂
Can you update this article to include performing this deployment in an environment without access to the internet?
It initially was on my to do. So, I guess I’d bring it back.
Hi Martin,
i have modified your script for our needs to install from FoD media. therefor i modified your param block and also the add -windowscapability part.
My param blocks look like this:
[CmdletBinding()]
param(
[parameter(Mandatory=$false, ParameterSetName = “Install”)]
[ValidateNotNullOrEmpty()]
[switch]$All,
[parameter(Mandatory=$false, ParameterSetName = “Install”)]
[ValidateNotNullOrEmpty()]
[switch]$Basic,
[parameter(Mandatory=$false, ParameterSetName = “Install”)]
[ValidateNotNullOrEmpty()]
[switch]$ServerManager,
[Parameter(ParameterSetName = “Install”, Mandatory=$true)]
[ValidateNotNullOrEmpty()]
[string]$FoDMediaPath,
[parameter(Mandatory=$false, ParameterSetName=”Default”)]
[ValidateNotNullOrEmpty()]
[switch]$Uninstall
)
and the add part:
Add-WindowsCapability -Online -Name $RsatItem -Source $FoDMediaPath -LimitAccess
Through set parameter the param FoDMediaPath is only needed within the installation switch
Install-RSATv1809v1903.ps1 -FoDMediaPath [-All] [-Basic] [-ServerManager] []
Install-RSATv1809v1903.ps1 [-Uninstall] []
Thank you for your great scripts
NICE! Do you mind sending me more details on mab@imab.dk? That’s something I wanted to include myself, seeing not all devices will have access to the Internet.
You got all the informations and testings which i have done
Thanks for this! I was able to get this working after making the Group Policy change. Just curious is you’ve tried this during a Windows 10 Task Sequence upgrade? I can get this to install during a regular Task Sequence just fine, but I get a generic 0X80004005 error during the TS upgrade. I’ll keep digging, but just curious if you’ve had any success with this.
I haven’t tried to run the script during an IPU TS, but if you enable dynamic updates (Dynamically update Windows Setup with Windows Update) for your in-place upgrade, the RSAT tools should be preserved.
Hi Martin,
the script is running if I run it manually on my machine. But with SCCM Application I get the error message:
Unmatched exit code (4294770688) is considered an execution failure.
in the appenforce.log.
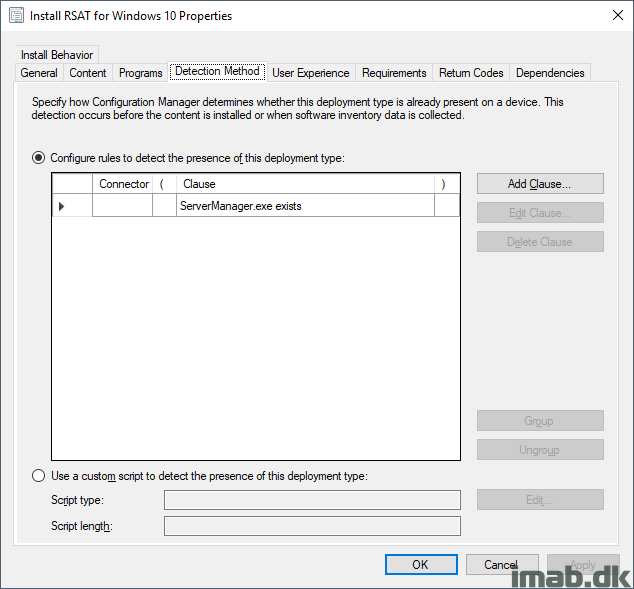
I thing it is the detection method
Path: %windir%\system32\
File or folder name: ServerManager.exe
– Install for system
– Whether or not a user is logged on
– Normal
What is here wrong?
Same here. I tried to install – failed with error code 0x87D00324(-2016410844). Can you share detailed screen shot of your detection method.
Tried manual install – Error info shared for your info.
VERBOSE: Script is running with -Basic parameter. Installing basic RSAT features
VERBOSE: Adding Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0 to Windows
VERBOSE: Failed to add Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x800f0954
VERBOSE: Adding Rsat.DHCP.Tools~~~~0.0.1.0 to Windows
VERBOSE: Failed to add Rsat.DHCP.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x800f0954
VERBOSE: Adding Rsat.Dns.Tools~~~~0.0.1.0 to Windows
VERBOSE: Failed to add Rsat.Dns.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x800f0954
VERBOSE: Adding Rsat.GroupPolicy.Management.Tools~~~~0.0.1.0 to Windows
VERBOSE: Failed to add Rsat.GroupPolicy.Management.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x800f0954
VERBOSE: Adding Rsat.ServerManager.Tools~~~~0.0.1.0 to Windows
VERBOSE: Failed to add Rsat.ServerManager.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x800f0954
I tried both manual and through application package. Both fails for me. Not sure what is wrong. The test was done at home lab.
I can provide error details and other info to help fix the issue. Let me know.
Does anyone know whether this is broken if we have the following Group Policy settings enabled?
-Turn off access to all Windows Update features
-Remove access to use all Windows Update features
I have these enabled from back when there was some weird stuff relating to Dual Scan. I wonder if I need them any longer…..
I would assume the script will fail installing RSAT if those group policies are enabled. I had those too applied to avoid dual scan initially, but I have since made the move to Windows Update for Business and is no longer applying any setting in regards to Windows Update with GPOs 🙂
Unfortunately, I am also receiving error 0x87D00324 in SCCM, and it fails during manual install. The script worked great for v1809 and v1903, but not here unfortunately.
Hmm, can you add the RSAT features manually? Not through the script, but directly in the OS (manage optional features). If that doesn’t work either, something is not right in your OS.
Yes, I add them in manually and it works fine.
Yes, manual works well. This is a clean install – not even using an image, it is using the install media.
Alright, I actually don’t know. All my testing is done on a clean installation as well, and I don’t have any issues. The script is not doing anything magically, other than running the proper powershell cmdlets: add-windowscapability, remove-windowscapability. Are you able to run those manually too?
Looking forward to a script that can be used for offline RSAT install. I was able to get hold of FOD package for en-us. Not sure how to use it with PS script.
By the way, if anybody need help with RSAT install using above PS script through CB1906 check below link. I wrote a detailed documentation with all screen shot that worked perfectly when deployed to Win 10 v1909 workstation.
http://www.infotechram.com/index.php/2019/11/20/installing-rsat-tools-on-windows-10-v1909/
Thank you for the detailed guide. I will soon enough modify the script, to also support installing RSAT offline via local FOD binaries 🙂
Any update on support for installing RSAT offline?
Sorry Scott, but I haven’t had time to look into this just yet. It’s on my to-do (which btw is quite lengthy in its own) 🙂
I was able to get it working by modifying the script a bit and downloading the FoD as shown in this blog post: https://www.moderndeployment.com/quick-start-guide-rsat-windows-10-1903-offline-fod-sccm-mdt-osd/
Nice, thanks for letting me know 🙂 I will look into this at some point, and probably around when the release of Windows 10 2004 🙂
During IPU I set the following REG Key before I use this script:
reg add “HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Servicing” /v RepairContentServerSource /d 2 /t REG_DWORD /f
This does the same as the policy setting Specify settings for optional component installation and component repair under Computer Configuration\Administrative Templates\System.
Well documented https://docs.microsoft.com/en-us/windows/deployment/update/fod-and-lang-packs.
Hi Martin, sorry, but why do you start ps1 with .\ ?
Also, this worked for me;
Run “gpedit.msc” to edit your local computer policy The setting in question is: Computer Configuration\Administrative Templates\System\Specify settings for optional component installation and component repair
My local policy seems to have defaulted to “Disabled” – after changing it to “Enabled” and selecting the checkbox labeled “Download repair content and optional features directly from Windows Update instead of Windows Server Update Services (WSUS)” the RSAT tools installed for me.
This does not work with Powershell 7.
.\Install-RSATv1809v1903v1909.ps1 -Uninstall
Get-WmiObject: C:\Users\xxx\Downloads\Install-RSATv1809v1903v1909.ps1:78
Line |
78 | $WindowsBuild = (Get-WmiObject -Class Win32_OperatingSystem).BuildNum …
| ~~~~~~~~~~~~~
| The term ‘Get-WmiObject’ is not recognized as the name of a cmdlet, function, script file, or operable
| program. Check the spelling of the name, or if a path was included, verify that the path is correct
| and try again.
WARNING: Not running correct Windows 10 build:
Get-WmiObject was deprecated in PS Core; use CIM instead.
Thank you! I adjusted the script and uploaded the new version. Thanks again 🙂
You saved me with this!
Many thanks!
Thank you! 🙂
Love this script. Thanks.
Thank you! 🙂
Hello,
I tried on my side to script uninstallation but i can’t uninstall without reboot.
I have this error : “permanent package cannot be uninstall” on W10 1909.
After reboot, this message disappears.
Do you have the same ?
Is your script need reboot during feature uninstall ?
windows 1903 here. Under features, RSAT is not visible. If I run the script, it jumps immediately to the “else” clause:
PS C:\Users\Arne\Desktop> powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -File .\Install-RSATv1809v1903v1909.ps1 -Uninstall
VERBOSE: Running correct Windows 10 build number for installing RSAT with Features on Demand. Build number is: 18362
VERBOSE: ***********************************************************
VERBOSE: Script is running with -Uninstall parameter. Uninstalling all RSAT features
VERBOSE: All RSAT features seems to be uninstalled already
PS C:\Users\Arne\Desktop> powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -File .\Install-RSATv1809v1903v1909.ps1 -Basic
VERBOSE: Running correct Windows 10 build number for installing RSAT with Features on Demand. Build number is: 18362
VERBOSE: ***********************************************************
VERBOSE: Script is running with -Basic parameter. Installing basic RSAT features
VERBOSE: The basic features of RSAT seems to be installed already
what about win 10 2004?
Good point. I will update the script asap 🙂 Thank you for the reminder.
Great Script, Thank you.
Would there be any issues with adding the information required for the newly released Windows 10 2004 (Build 19041)?
Unfortunately I do encounter an issue related to WSUS and the script stops for me. That is an issue I will work on. But for others, maybe add:
# Windows 10 2004 build
$2004Build = “19041”
.
.
.
and then
if (($WindowsBuild -eq $1809Build) -OR ($WindowsBuild -eq $1903Build) -OR ($WindowsBuild -eq $1909Build)-OR ($WindowsBuild -eq $2004Build)) {
Write-Verbose -Verbose “Running correct Windows 10 build number for installing RSAT with Features on Demand. Build number is: $WindowsBuild”
Write-Verbose -Verbose “***********************************************************”
.
.
.
What else needs to change?
Thanks again.
Hello Warren, I just updated the script to support for 2004. Sorry for being a tad late on this one 🙂
Hello, where is the updates script for download? thanks
Hey, see my latest post on Windows 10 v2004. I moved the script to GitHub 🙂
SORRY didn’t realize you already modified..
No worries 🙂
I’ve been trying this script and another one to try to turn this into an application deployment through Software Center and I’m running into the 0x87D00324 error in my detection method. My settings are as follows:
Type: File System
Path: %windir\System32
File or Folder: ServerManager.exe
I’ve both tried checking and unchecking the box for “This file or folder is associated with a 32-bit application on 64-bit systems” and each one fails.
The radio button next to “The file system setting must exist on the target system…” is also selected.
What am I doing wrong? Is there another way to do the detection?
This might come out as a silly question, but do you see the servermanager.exe file when browsing windir\system32? The error you see indeed translates into The application was not detected after installation completed.
Small bug — in your if statements, the $null side of the comparison should be first.
So instead of:
if ($Install -ne $null)…
it should be:
if ($null -ne $Install)
Alrighty! Care to explain the reason before I correct it? I might learn something new, which I appreciate! 🙂
I did a search for ServerManager.exe and found it here:
C:\Windows\WinSxS\msil_microsoft-windows-servermanager-shell_31bf3856ad364e35_10.0.10585.0_none_34dafa55f3cf30d2
Is this the right location for detection? or is this for only rsat 1909? do we need to specify detection for all 3 build numbers?
Hi Martin, many thanks for Your script! I modified it a little and works on Buils 2004 also:
# Windows 10 1809 build
$1809Build = “17763”
# Windows 10 1903 build
$1903Build = “18362”
# Windows 10 1909 build
$1909Build = “18363”
# Windows 10 2004 build
$2004Build = “19041”
# Get running Windows build
$WindowsBuild = (Get-CimInstance -Class Win32_OperatingSystem).BuildNumber
# Get information about local WSUS server
$WUServer = (Get-ItemProperty “HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate” -Name WUServer -ErrorAction Ignore).WUServer
#$DualScan = (Get-ItemProperty “HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate” -Name DisableDualScan -ErrorAction Ignore).DisableDualScan
$TestPendingRebootRegistry = Test-PendingRebootRegistry
if (($WindowsBuild -eq $1809Build) -OR ($WindowsBuild -eq $1903Build) -OR ($WindowsBuild -eq $1909Build) -OR ($WindowsBuild -eq $2004Build)) {
Write-Verbose -Verbose “Running correct Windows 10 build number for installing RSAT with Features on Demand. Build number is: $WindowsBuild”
Write-Verbose -Verbose “***********************************************************”
Sorry for my poor english, but I must thank.
Laci
Martin, many thanks for sript!!!
After a minimal modyfy the script run as well on Build 2004:
# Windows 10 1809 build
$1809Build = “17763”
# Windows 10 1903 build
$1903Build = “18362”
# Windows 10 1909 build
$1909Build = “18363”
# * * * Added next 2 lines * * *
# Windows 10 2004 build
$2004Build = “19041”
# Get running Windows build
$WindowsBuild = (Get-CimInstance -Class Win32_OperatingSystem).BuildNumber
# Get information about local WSUS server
$WUServer = (Get-ItemProperty “HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate” -Name WUServer -ErrorAction Ignore).WUServer
#$DualScan = (Get-ItemProperty “HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate” -Name DisableDualScan -ErrorAction Ignore).DisableDualScan
$TestPendingRebootRegistry = Test-PendingRebootRegistry
# * * * Modified line with ” -OR ($WindowsBuild -eq $2004Build)” * * *
if (($WindowsBuild -eq $1809Build) -OR ($WindowsBuild -eq $1903Build) -OR ($WindowsBuild -eq $1909Build) -OR ($WindowsBuild -eq $2004Build)) {
Sorry for my very poor english.
Thanks!
Laci
I have SCCM configured as my WSUS server. I receive the error code = 0x800f09954 because I do not have “Specify settings for optional component installation and component repair” GPO enabled. Is this a requirement to enable this GPO to install RSAT when you have WSUS server set? Is there no other way to resolve?
Hi I keep getting this error
0x8024402c
PS C:\Users\rmuhammad\Downloads> .\Install-RSATv1809v1903v1909.ps1 -Basic
VERBOSE: Running correct Windows 10 build number for installing RSAT with Features on Demand. Build number is: 18363
VERBOSE: ***********************************************************
VERBOSE: A local WSUS server was found configured by group policy: http://USRNOPSCCM02.MYIGT.com:8530
VERBOSE: You might need to configure additional setting by GPO if things are not working
VERBOSE: The GPO of interest is following: Specify settings for optional component installation and component repair
VERBOSE: Check ON: Download repair content and optional features directly from Windows Update…
VERBOSE: ***********************************************************
VERBOSE: Script is running with -Basic parameter. Installing basic RSAT features
VERBOSE: Adding Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0 to Windows
VERBOSE: Failed to add Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x8024402c
VERBOSE: Adding Rsat.DHCP.Tools~~~~0.0.1.0 to Windows
VERBOSE: Failed to add Rsat.DHCP.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x8024402c
VERBOSE: Adding Rsat.Dns.Tools~~~~0.0.1.0 to Windows
VERBOSE: Failed to add Rsat.Dns.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x8024402c
VERBOSE: Adding Rsat.GroupPolicy.Management.Tools~~~~0.0.1.0 to Windows
VERBOSE: Failed to add Rsat.GroupPolicy.Management.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x8024402c
VERBOSE: Adding Rsat.ServerManager.Tools~~~~0.0.1.0 to Windows
VERBOSE: Failed to add Rsat.ServerManager.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x8024402c
Thank you
You may be succesful in disabling your WSUS. I have an update for the script just coming up which enables you to do that automatically.
Have you tried using my recent release where you can disable wsus in the process?
Howdy from Texas. Could you possibly update the script to work with Windows 10 21H1 and then 21H2? How about for Windows 11 21H2? Is it the same kind of process?
I’m not even close to a powershell or programming type of tech, so any help you can provide, I would appreciate.
Thanks.
-matt
The latest version should be able to install RSAT for you coming from those versions of Windows 10: https://www.imab.dk/deploy-rsat-remote-server-administration-tools-for-windows-10-v20h2-using-configmgr-and-powershell/
Hello Martin,
You post is super awesome. Really thanks for that, it worked as independent application for me wherein I just had to modify the detection with Servermanager.exe version, But when I am calling same application in feature update TS 20h2 its failing and getting successful if I rerun the same tasksequnce . your insight will be very much helpful. I have tried using “windows-10-in-place-upgrade-task-sequence-auto-re-install-rsat” by Gary Town. But result is same.