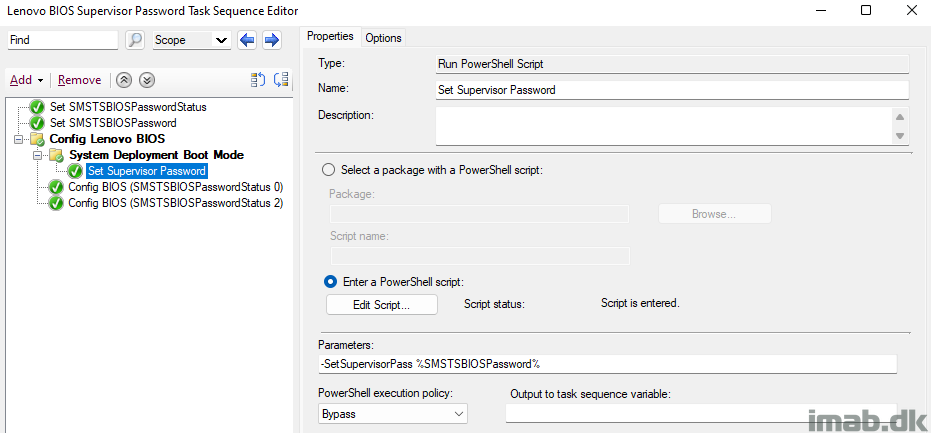
Approximately two years ago, I authored a blog post detailing how to customize the taskbar in Windows 11. You can find that post here: Customize your Windows 11 taskbar during OSD with ConfigMgr using just PowerShell – imab.dk
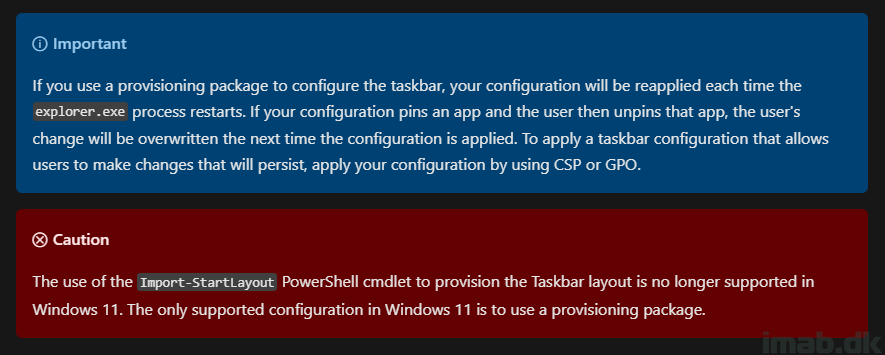
Since then, there have been some changes from Microsoft, and the method I previously described is no longer supported. For more information on these changes, please refer to: Configure the applications pinned to the taskbar | Microsoft Learn
In summary, the cmdlet Import-StartLayout is no longer supported and does not accept the .xml file, resulting in the following error: Import-StartLayout : The file C:\WINDOWS\Taskbar.xml is not a valid layout file
To address this, I have modified the solution I used back then, and the new approach is outlined in this blog post.