Introduction
Configuring the BIOS password on a Lenovo device for the first time, requires manual labor. Either by you or by the OEM before shipping. For security reasons, this cannot be done remotely.
So, what if the idea of having a supervisor password on your devices is relatively new, and you have thousands of devices out there without?
Then you’ll have to come up with a process on getting to them manually, and in this process, knowing exactly which devices that needs attention is key.
PowerShell
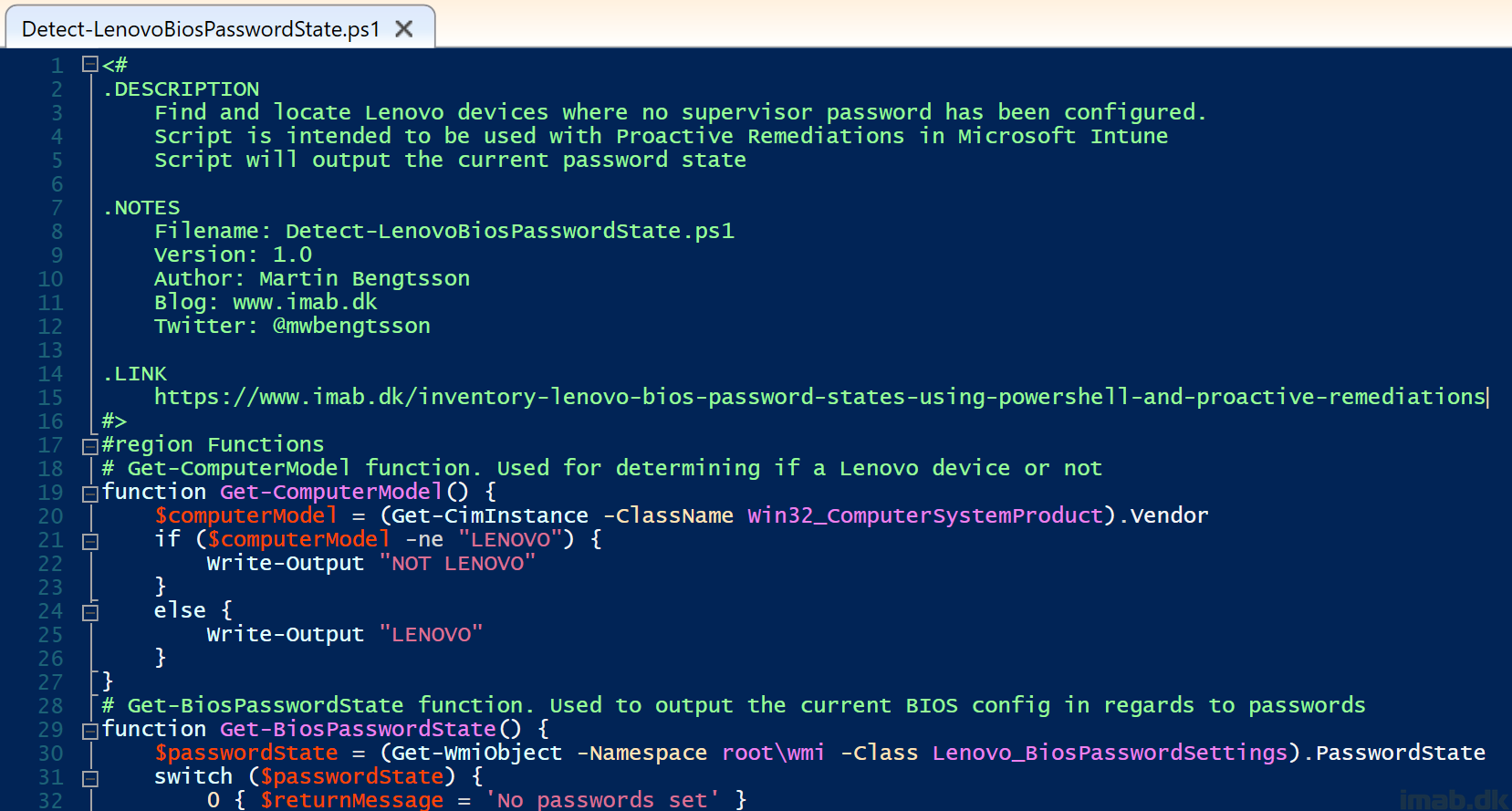
With the intentions of configuring a supervisor password on all Lenovo devices in the environment, as well as having a complete overview during the process, I wrote following PowerShell script.
Detect-LenovoBiosPasswordState.ps1
Find the script on my GitHub page: Proactive-Remediations/Detect-LenovoBiosPasswordState.ps1 at main · imabdk/Proactive-Remediations (github.com)
The script does following in headlines:
- Tests if the device in question is a Lenovo device
- If not, doing nothing
- If a Lenovo device, continues to query WMI looking for a BIOS password
- If no BIOS password is configured, returning that message as output to Intune: No passwords set
- If a BIOS password is configured, returning that message as output to Intune:
- 2 { $returnMessage = ‘Supervisor password set’ }
3 { $returnMessage = ‘Power on and supervisor passwords set’ }
4 { $returnMessage = ‘Hard drive password(s) set’ }
5 { $returnMessage = ‘Power on and hard drive passwords set’ }
6 { $returnMessage = ‘Supervisor and hard drive passwords set’ }
7 { $returnMessage = ‘Supervisor, power on, and hard drive passwords set’ }
- 2 { $returnMessage = ‘Supervisor password set’ }
Proactive Remediations
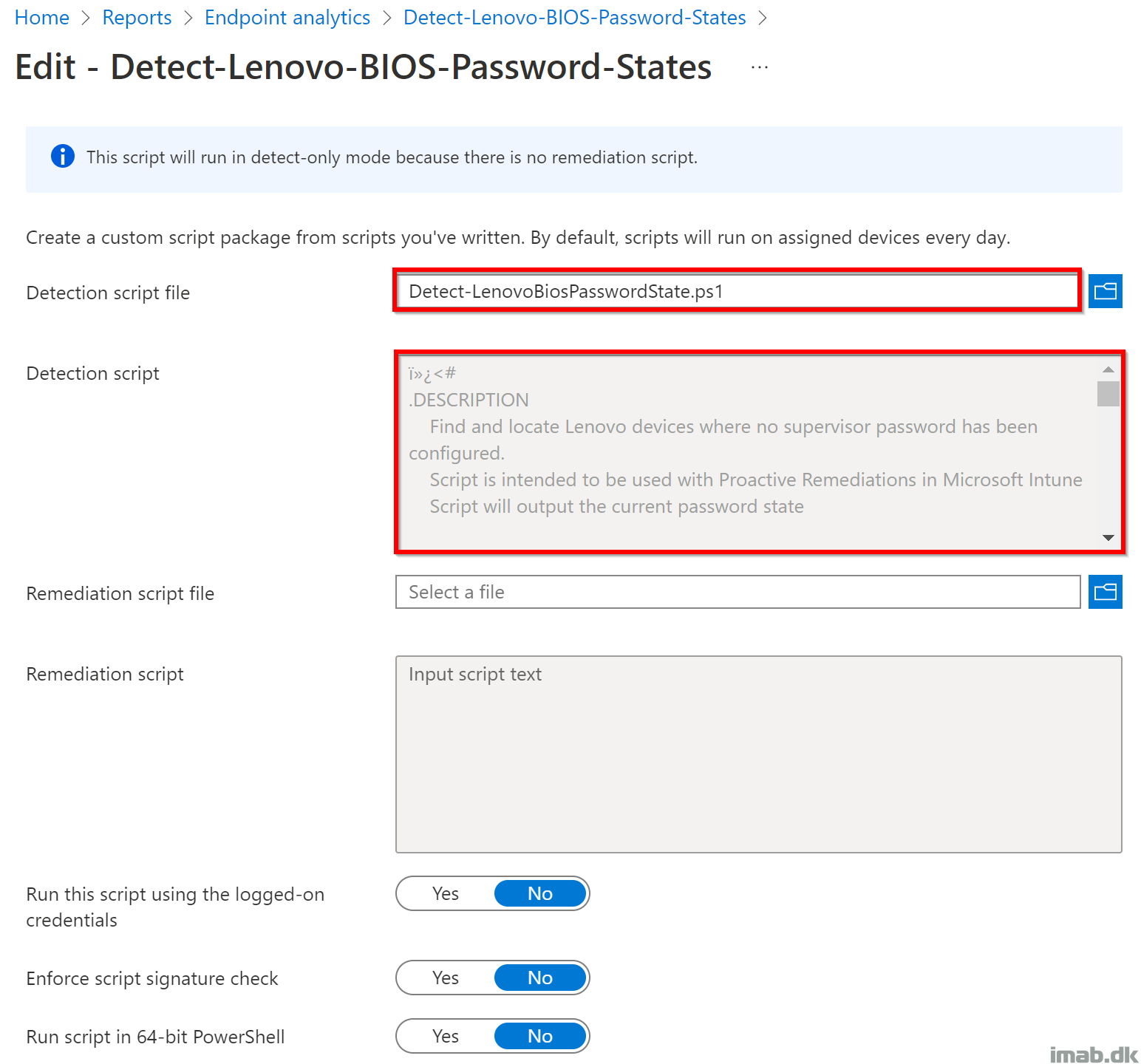
Put the script to use in Microsoft Intune with Proactive Remediations.
- This is done per usual, via the Microsoft Endpoint Manager admin center: https://endpoint.microsoft.com. Browse to the location shown below:
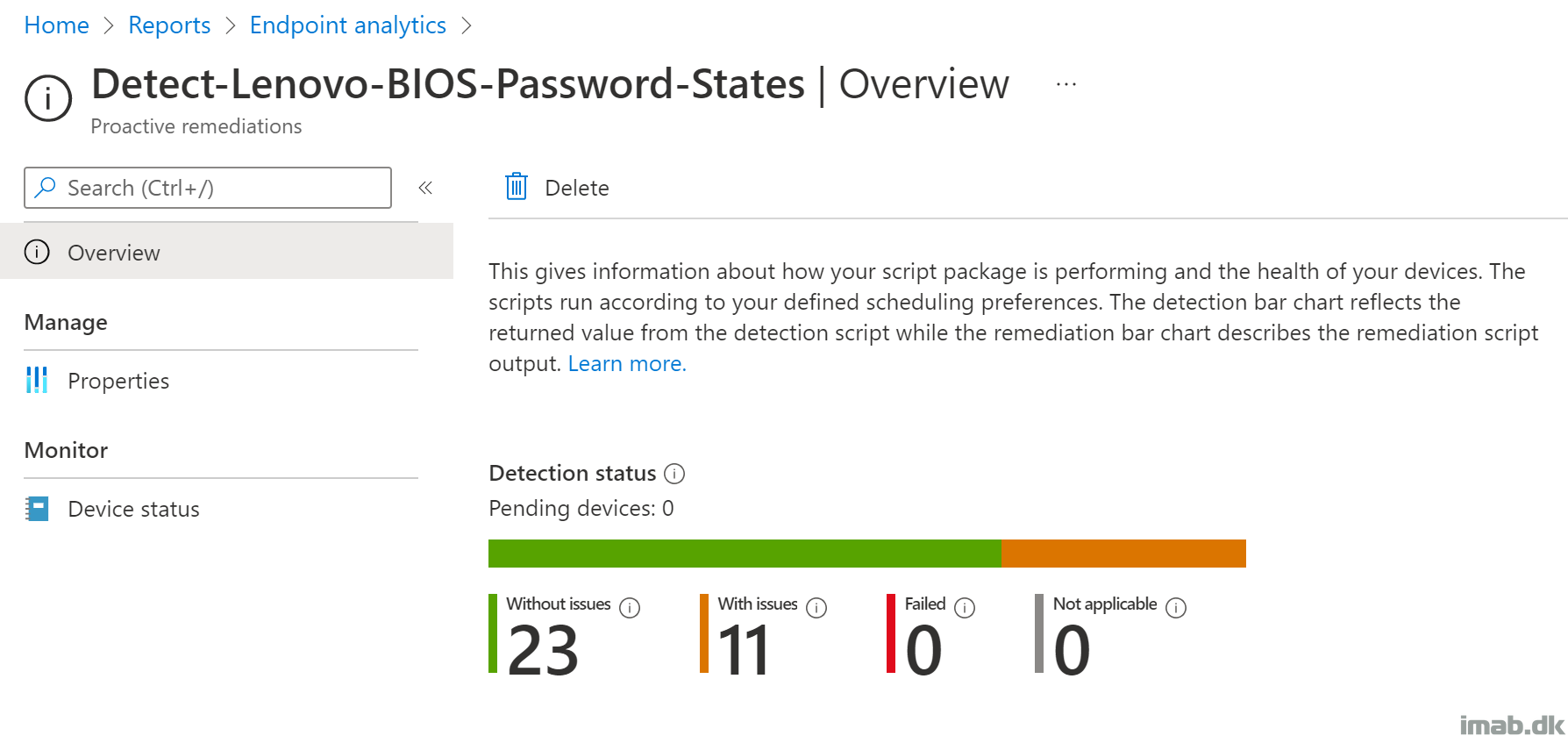
- Once the script has been deployed and run on your devices, you will have a quick overview of the status:
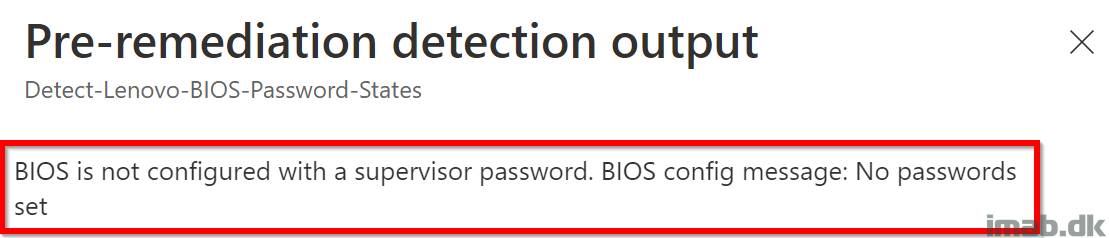
- Digging further into the status of each device, you are able to browse the output of the script directly in the MEM admin center:
- All of this can exported to .csv as well if needed
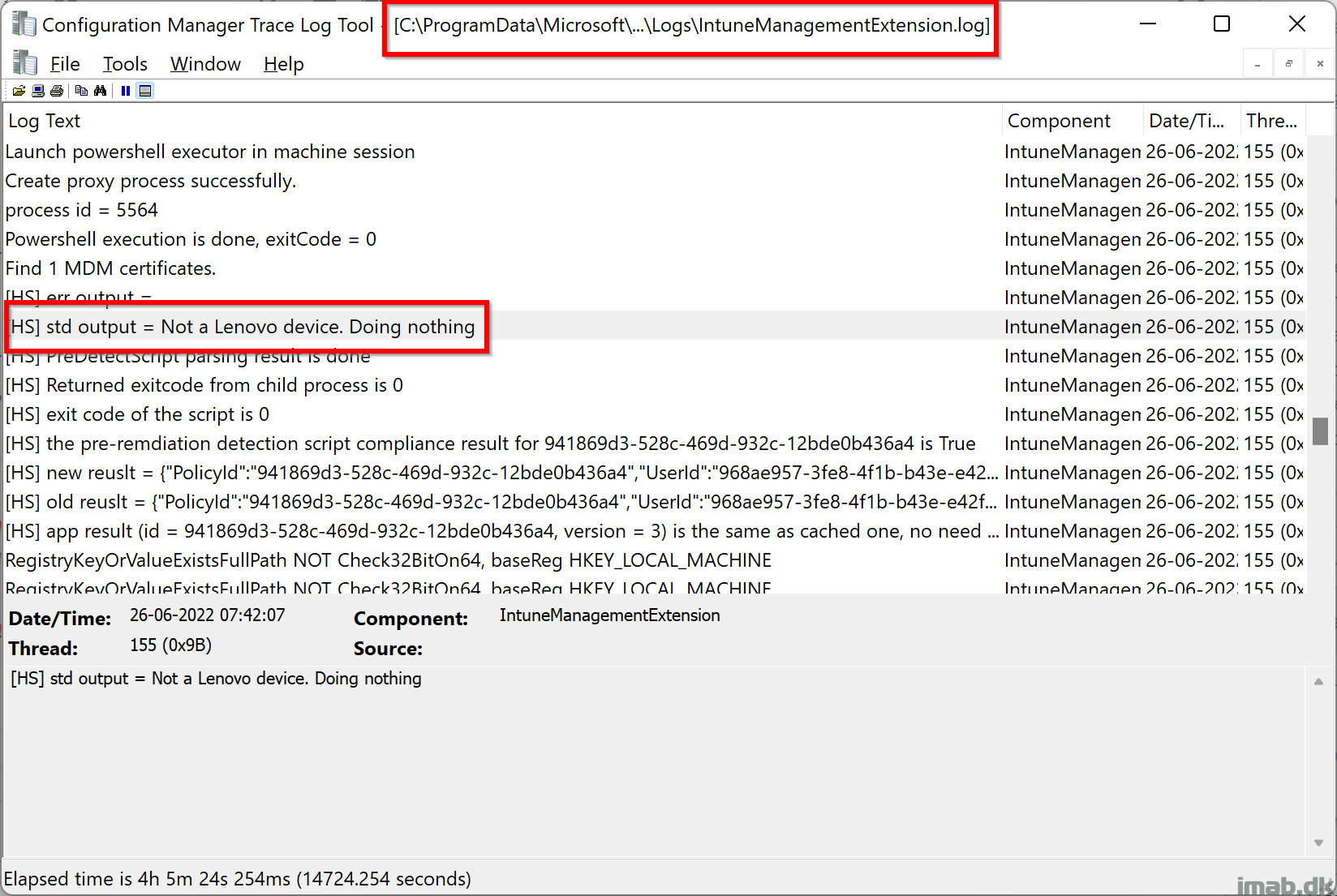
- The output of the script is also written to the IntuneManagmentExtension.log
- Below example is taken from my Surface device, which obviously is not made by Lenovo why the ‘Not a Lenovo device’ entry
ENJOY 🙂
1 thought on “Inventory Lenovo BIOS password states using PowerShell and Proactive Remediations”