Introduction
Similar to when Windows 10 v1809 was released back in October 2018 and RSAT debuted as “Features on Demand”, the way of installing RSAT continues with the v1903 release.
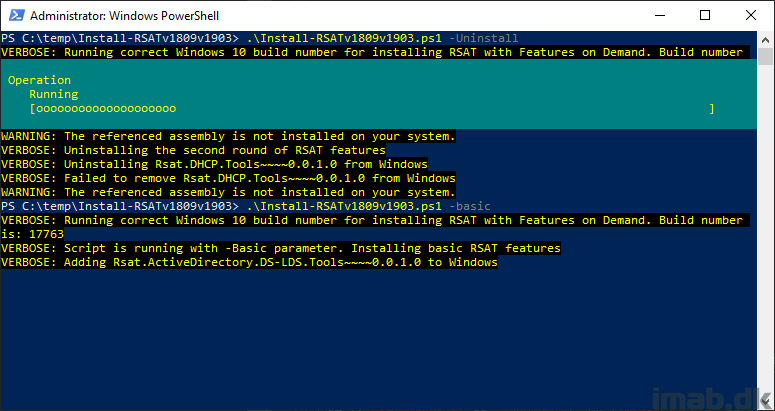
Back then I did a Powershell script which is able to install and uninstall the RSAT features. I have now rewritten the script to also include Windows 10 v1903.
Find my 1809 post here: https://www.imab.dk/deploy-rsat-remote-server-administration-tools-for-windows-10-v1809-using-sccm-system-center-configuration-manager/
Powershell
The script requires administrative rights as well as access to the Internet (RSAT is installed through Microsoft Update).
The script is built around Get-WindowsCapability, Add-WindowsCapability and Remove-WindowsCapability.
Yet again the script comes with 4 options:
- -All (-All is installing ALL the features within the RSAT bundle)
- -Basic (-Basic is only installing AD DS, DHCP, DNS, Group Policy Management and Server Manager)
- -ServerManager (-ServerManager is only installing the Server Manager)
- -Uninstall (-Uninstall removes all RSAT features again)
Configuration Manager
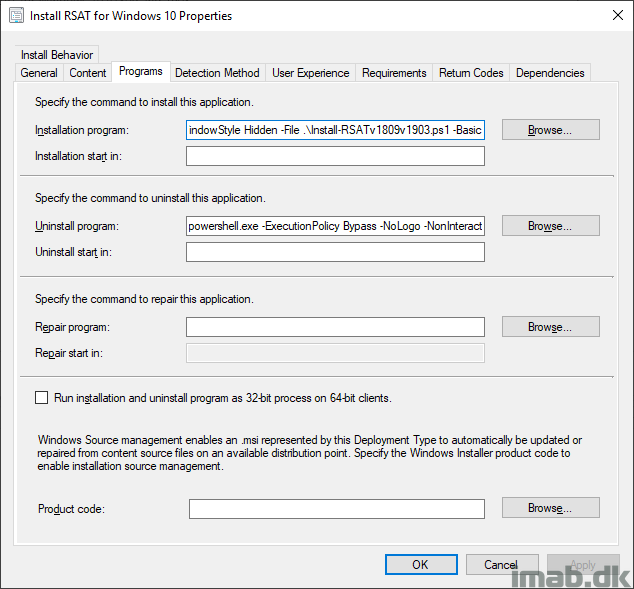
I’m putting the Powershell script to use with an application in SCCM. While this is pretty standard SCCM, I have included a few snippets of the application below.
The installation program:
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -File .\Install-RSATv1809v1903.ps1 -Basic
The uninstall program:
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -File .\Install-RSATv1809v1903.ps1 -Uninstall
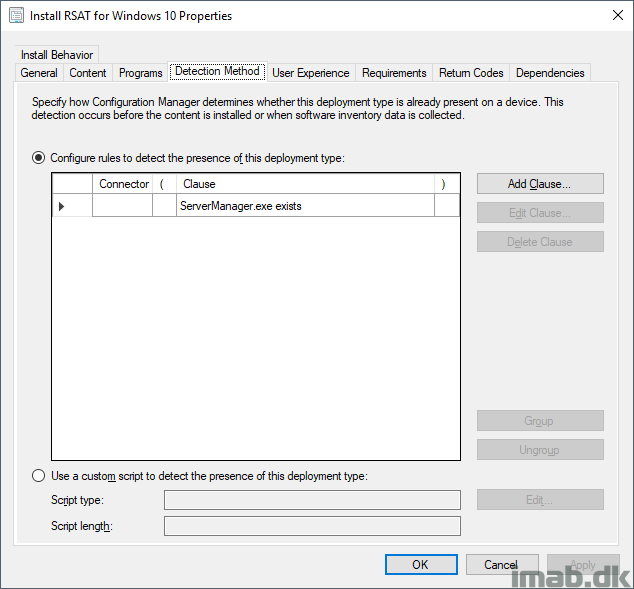
In my previous script I created registry keys for detection. I’m unsure if that’s an approach I fancy anymore, so for now I’ve removed it and instead detect on ServerManager.exe, as that always gets installed with RSAT.
Download
https://gallery.technet.microsoft.com/Install-RSAT-for-Windows-75f5f92f
ENJOY 🙂
Windows 10 Pro, 1903, OS Build 18362.86
Installing RSAT using your script and the -Basic option causes Windows 10 Restart or Shutdown hang issues. Verified this on two different systems. Uninstalling RSAT corrects the issue.
Thanks for letting me know. I’m almost certain that it’s not the script itself but the presence of RSAT which is creating the issue. The script does nothing fancy other than run Add-WindowsCapability. I have tested the script on 1903 Enterprise and I initially didn’t see any issues. I will test again 🙂
So, I took a look at the script and this will attempt to install features even if the feature is already installed. You’ve got the logic of, if ($Install -ne $null), as your check. $Install will never not equal $null. You have to check for install like this: if ($Install.state -ne ‘Installed’).
I appreciate the feedback, but that’s simply not true. I filter on $_.State -eq “NotPresent” as well, so I only pick up features which are not installed already 🙂
Thank you man, very appreciate.
I tried installing RSAT features on my Dell Precision 7920 running Windows 10 Pro for Workstations build 1903 two ways. First using the interactive Features submenu in the Apps and Features module. Installs fail. Then tried using your script. Script ran fine but the installs failed. So I guess this may be a problem with the RSAT packages (perhaps only on my particular machine type).
You are right, that sounds like a problemer with your OS itself rather than my script 🙂
am getting the following trying to install RSAT please can you help
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Try the new cross-platform PowerShell https://aka.ms/pscore6 PS C:\WINDOWS\system32> cd.. PS C:\WINDOWS> cd.. PS C:\> cd certs
PS C:\certs> Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass
Execution Policy Change
The execution policy helps protect you from scripts that you do not trust. Changing the execution policy might expose
you to the security risks described in the about_Execution_Policies help topic at
https:/go.microsoft.com/fwlink/?LinkID=135170. Do you want to change the execution policy?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is “N”): a
PS C:\certs> ./Install-RSATv1809v1903.ps1 -Basic
VERBOSE: Running correct Windows 10 build number for installing RSAT with Features on Demand. Build number is: 18362
VERBOSE: Script is running with -Basic parameter. Installing basic RSAT features
VERBOSE: Adding Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0 to Windows
VERBOSE: Failed to add Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x80240438
VERBOSE: Adding Rsat.DHCP.Tools~~~~0.0.1.0 to Windows
VERBOSE: Failed to add Rsat.DHCP.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x80240438
VERBOSE: Adding Rsat.Dns.Tools~~~~0.0.1.0 to Windows
VERBOSE: Failed to add Rsat.Dns.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x80240438
VERBOSE: Adding Rsat.GroupPolicy.Management.Tools~~~~0.0.1.0 to Windows
I’m sorry, but I don’t know what would cause Error code = 0x80240438 to happen. It’s not related to the script, but something in your OS 🙂
Same error, as I have it …
How can I modify this script so that it looks locally for the install files? I’d like for the source to be “c:\temp”.
Script fails for me as well but I expected it to.
GPO’s direct all computers to use WSUS, not Windows update. (the norm in a business enviroment)
VERBOSE: Failed to add Rsat.WSUS.Tools~~~~0.0.1.0 to Windows
WARNING: Add-WindowsCapability failed. Error code = 0x800f0954
I’m thinking the pass of least resistance is to add a line to the beginning of the script to edit the following registry key.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU\UseWUServer = 0 (not 1)
Manually editing the registry key and then running the script yields success.
Thanks for the added details. In regards to “the norm in a business environment” comment, I tend to disagree and that really depends on a lot of factors. If you are using SCCM (which this blog mostly is about), you don’t redirect clients to WSUS using GPOs 🙂
I’m probably gonna extend the script to be able to take care of the various errors mentioned in here soon 🙂
Thanks again.
Thank you Martin,
I guess I’m not aware of your configuration. I’ve been directing clients to WSUS for many years. I started using SCCM 4 years ago and now use a combination of WSUS and Automatic Deployment Rules in SCCM for all of my patching.
Nevertheless, in every organization I’ve been a part of, they use WSUS and a GPO to point to WSUS but I’d love to learn a better way.
Jon
If you use software updates with ConfigMgr, the configmgr client will create a local WUServer policy telling the client about your WSUS. What GPO are you using? I’m curious, as it obviously have an effect on how RSAT is being installed with add-windowscapability 🙂
Add to your GPO the option to “Contact Windows Update directly to download repair content instead of WSUS”
It’s found under “Computer Configuration > Policies > Administrative > System > Specify settings for optional component installation and component repair” oddly enough it’s not in the Windows Updates category where you would think this option would be.
It’s not odd to have a GPO pointing the WSUS settings to your SCCM SUP. Doing this gives you an alternate method to install the SCCM client on your machines rather than pushing them from your server
https://docs.microsoft.com/en-us/sccm/core/clients/deploy/deploy-clients-to-windows-computers#configure-a-group-policy-object-to-specify-the-software-update-point
Good knowledge. Thanks for sharing that 🙂
Thank you for the script and than you John P for the tip on GPO to contact Windows Update directly. That worked a treat.
For anyone with the error..
Run “gpedit.msc” to edit your local computer policy The setting in question is: Computer Configuration\Administrative Templates\System\Specify settings for optional component installation and component repair
My local policy seems to have defaulted to “Disabled” – after changing it to “Enabled” and selecting the checkbox labeled “Download repair content and optional features directly from Windows Update instead of Windows Server Update Services (WSUS)” the RSAT tools installed for me.
From https://social.technet.microsoft.com/Forums/en-US/42bfdd6e-f191-4813-9142-5c86a2797c53/windows-10-1809-rsat-toolset-error-code-of-0x800f0954
Regarding the error 0x800f0954… setting the ‘Optional component for installation’ does not give us a solution. Instead it throws another error which is 0x8024002e. Some people mentioned setting HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU\UseWUServer = 0 but in an environment where the clients get their updates through SCCM this value is always set to 1. This has nothing to do with a GPO, it’s just the way SCCM sets it for its clients.
In the end we found out that setting another key from 1 to 0 is the solution. The key is HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\DisableWindowsUpdateAccess and you should set it to 0.
Unfortunately this is not a real solution for us since we don’t want our users to have direct control over the Windows Update settings so next thing to do is find a way to place the RSAT tools inside a package and deploy it through SCCM.
I am continuing to return a CmdletBinding error
PS C:\temp> .\Install-RSATv1809v1903.ps1 -Basic
At C:\temp\Install-RSATv1809v1903.ps1:31 char:1
+ [CmdletBinding()]
+ ~~~~~~~~~~~~~~~~~
Unexpected attribute ‘CmdletBinding’.
At C:\temp\Install-RSATv1809v1903.ps1:33 char:1
+ param(
+ ~~~~~
Unexpected token ‘param’ in expression or statement.
+ CategoryInfo : ParserError: (:) [], ParseException
+ FullyQualifiedErrorId : UnexpectedAttribute
Adarst22, Thanks that worked!
@Marcel Moerings “next thing to do is find a way to place the RSAT tools inside a package and deploy it through SCCM.”
> Did you figure out how to realize that package ?
Hi Martin,
I have a question about detection method. What should I select as setting Type for “ServerManager.exe exists”
Regards
I got all of this to work. The next step is… how can I query everything with rsat installed that’s already on 1809? Because when doing the upgrade from 1809 to 1909 it removes those features. So in theory if I could query what PC has rsat on 1809 I could make this deployment depends on 1909 and stick those systems out there that have it into a collection and as they migrate to 1909 RSAT will install automatically for them.
Finding the query logic has proved challenging for the windows features.