Introduction
I’m currently working on getting my Windows 11 devices CIS (CIS Center for Internet Security (cisecurity.org) compliant in regards to their benchmark. This takes some effort, especially if you don’t use Group Policy anymore. 🙂
- For those who don’t know CIS benchmarks, get more details here: CIS Benchmarks (cisecurity.org) and here: Center for Internet Security (CIS) Benchmarks – Microsoft Compliance | Microsoft Docs
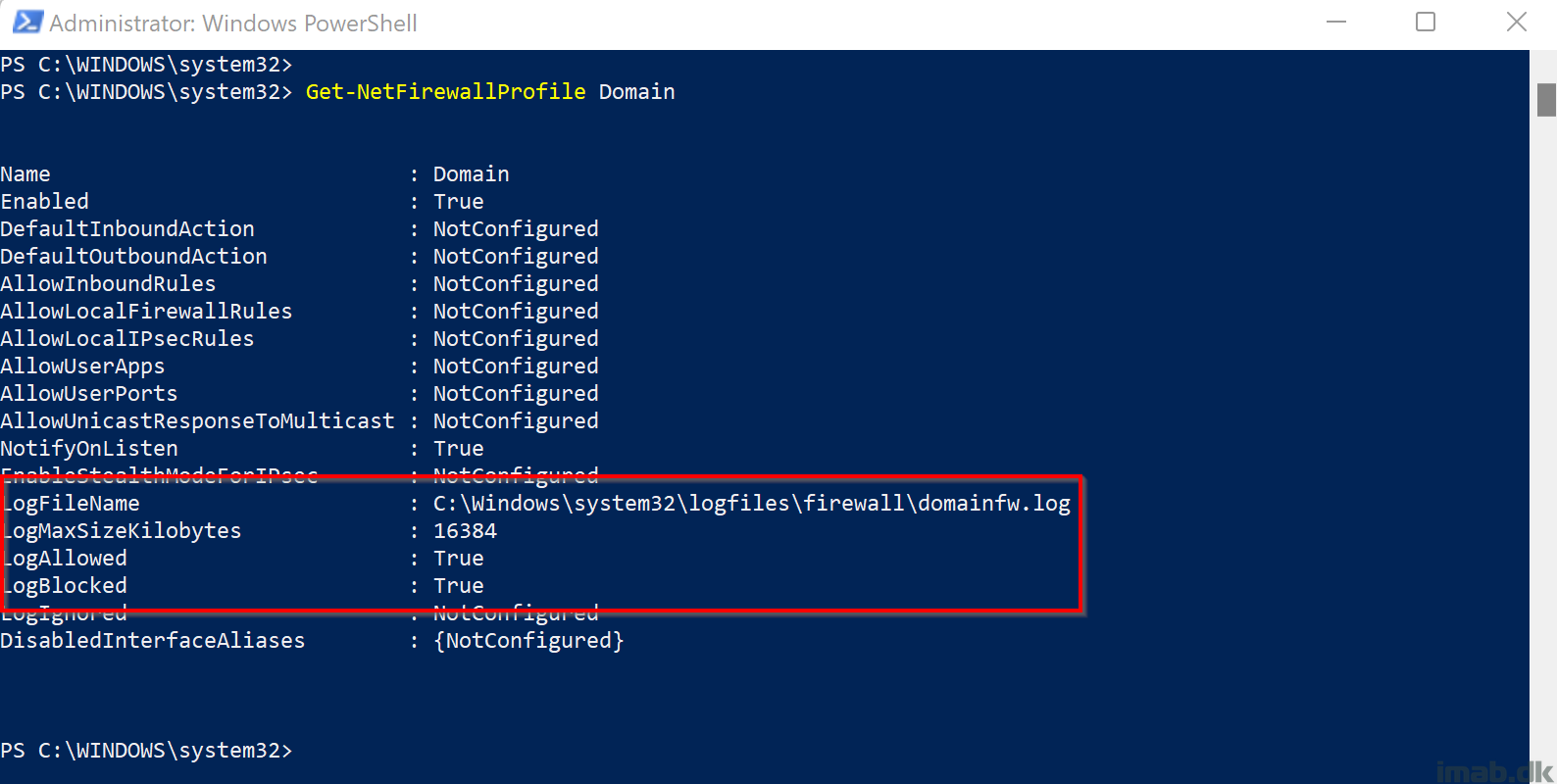
The CIS Benchmark for Microsoft Windows 11 Enterprise dictates that logging for Windows Firewall is enabled, and is configured with certain settings. None of those settings, at the time of writing, are available natively via Intune, so I have chosen to resort to PowerShell and Proactive Remediations.
My scripts will create each log file, for each firewall profile: Domain, Private, Public and make sure those log files are configured with the correct permissions (otherwise the Defender engine won’t have permissions to write to the files). Firewall logging will then be enabled with the recommended values.
Defender for Endpoint
Microsoft Defender for Endpoint has a baseline assessment feature, which will ease the work getting compliant with the CIS benchmark.
- The feature is found in the Microsoft 365 Defender portal here: https://security.microsoft.com/baseline-compliance
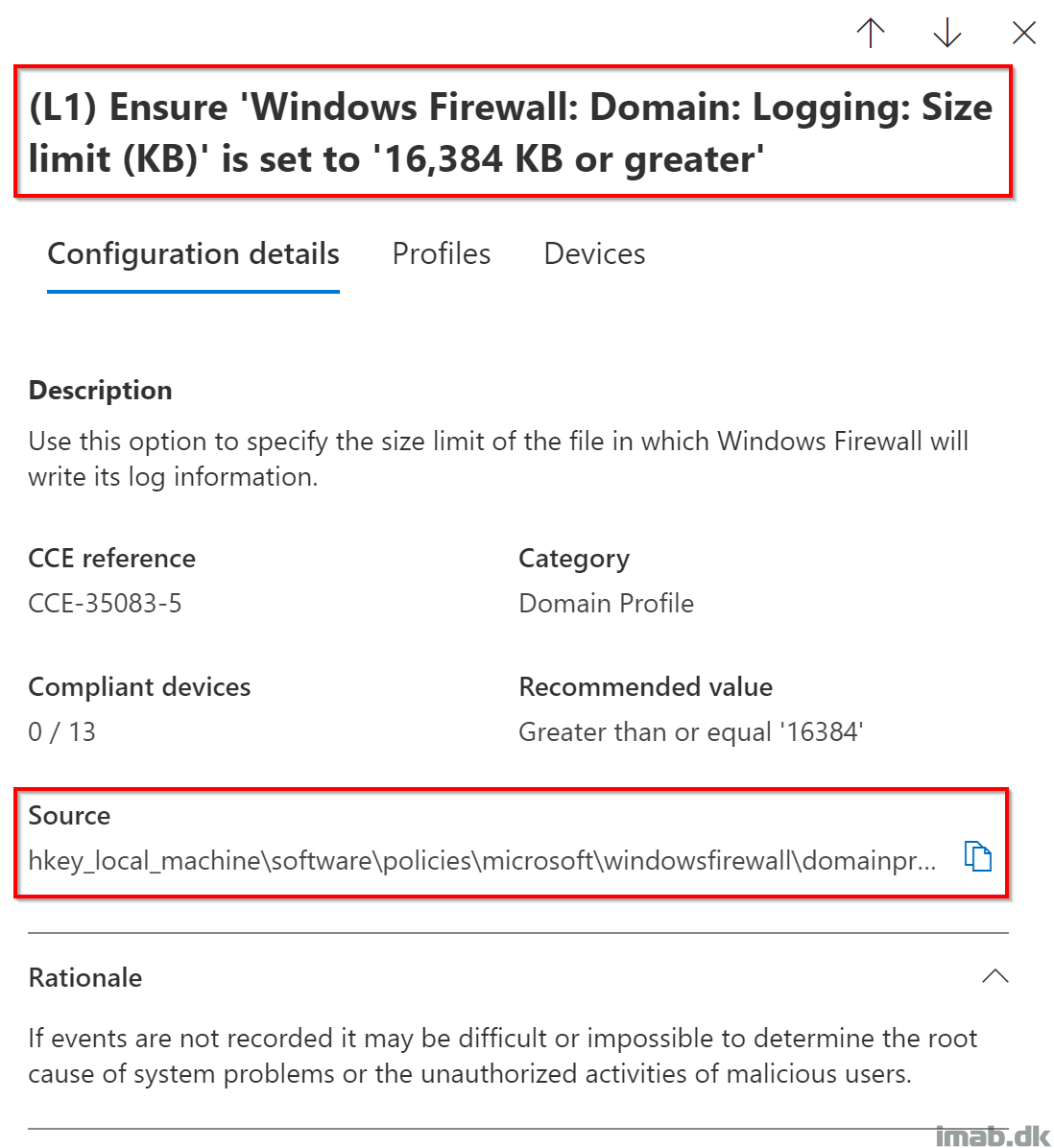
When a baseline assessment profile has been configured, and more specifically the one for Windows 11 based on CIS benchmarks, you will find what settings that the baseline is measuring.
In this scenario, the settings related to the Windows Firewall is of interest, and in order to get compliant, you will have to – among other settings – configure the log size to greater than or equal to 16,384KB.
PowerShell
I have split the scripts into 2 categories; one for creating the log files with the correct permissions, and another for enabling the actual logging on each firewall profile; domain, private and public.
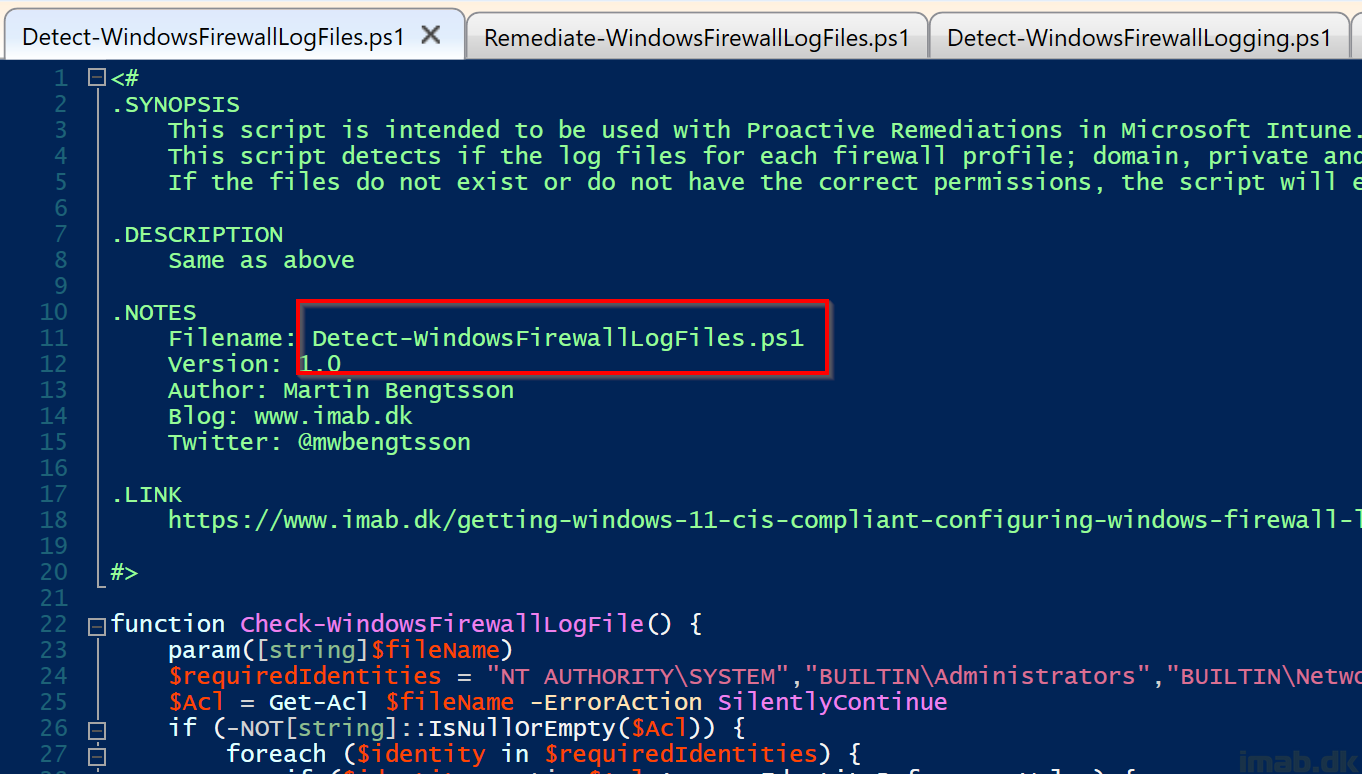
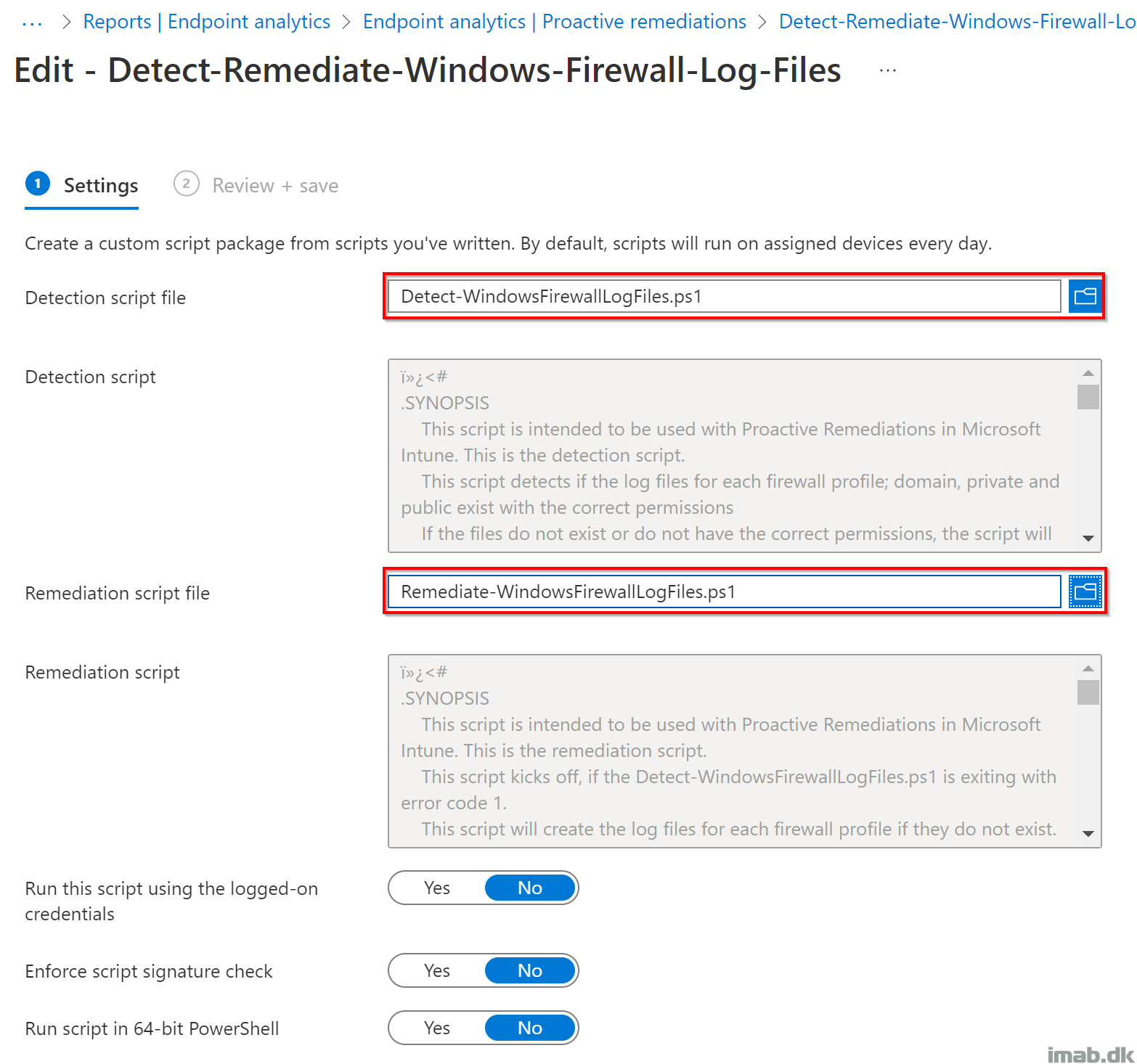
Detect-WindowsFirewallLogFiles.ps1
Find this script on my GitHub: Proactive-Remediations/Detect-WindowsFirewallLogFiles.ps1 at main · imabdk/Proactive-Remediations (github.com)
This script detects if the log files for each firewall profile exist. If they do not exist or do not have the correct permissions applied, the script will exit with error code 1, instructing the Intune Management Extension to kick off the remediation script.
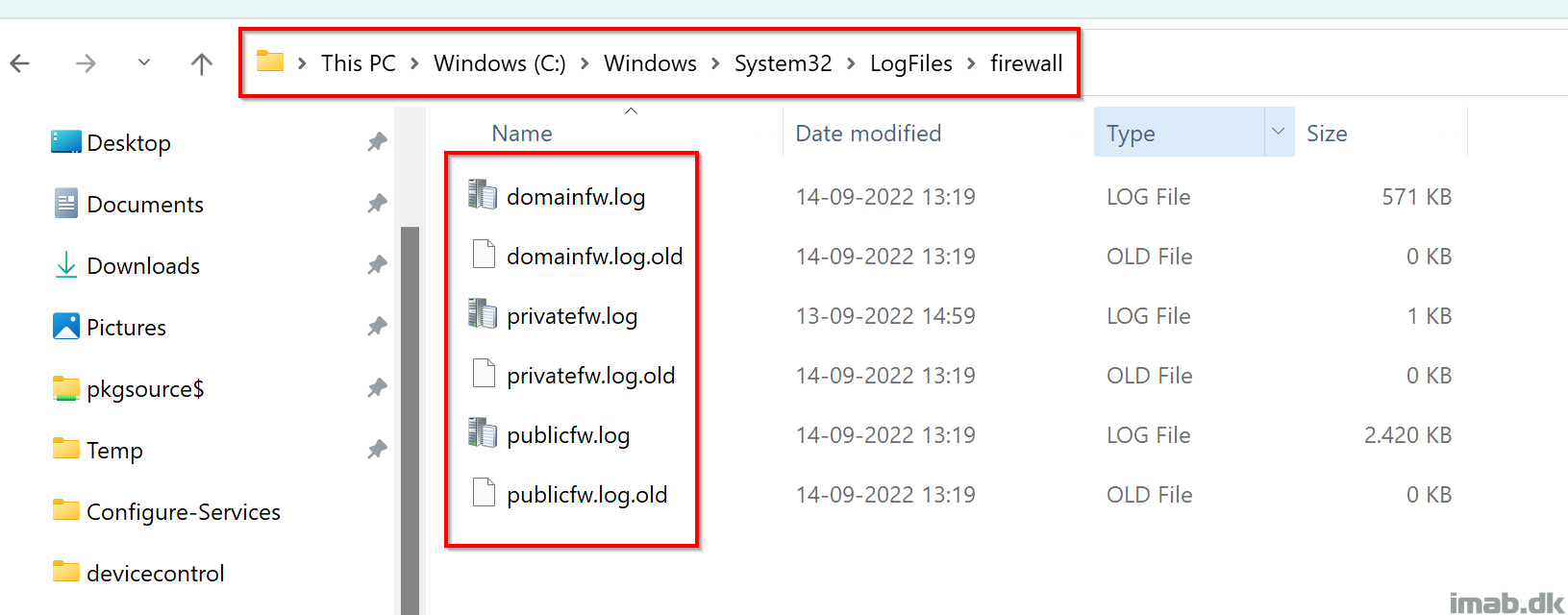
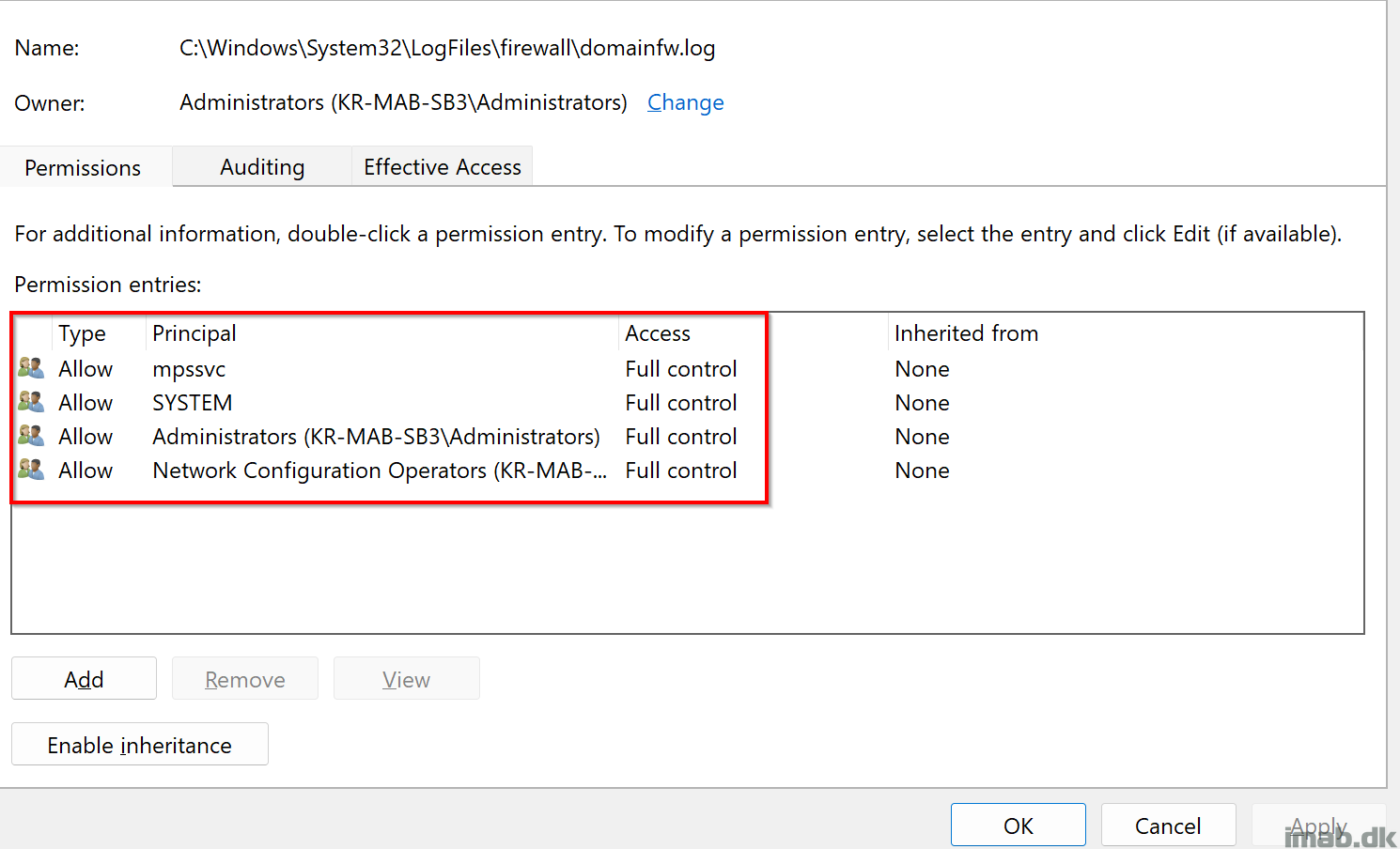
The log files in question are these:
And the correct permissions are as following:
Remediate-WindowsFirewallLogFiles.ps1
Find this script on my GitHub: Proactive-Remediations/Remediate-WindowsFirewallLogFiles.ps1 at main · imabdk/Proactive-Remediations (github.com)
This script will create each log file for each Windows Firewall profile; domain, private, and public with the correct permissions.
Detect-WindowsFirewallLogging.ps1
Find this script on my GitHub: Proactive-Remediations/Detect-WindowsFirewallLogging.ps1 at main · imabdk/Proactive-Remediations (github.com)
This script detects if each firewall profile is configured to enable logging according to CIS recommendations.
If any of the 3 profiles is not configured accordingly, the script will exit with error code 1, instructing the remediation script to kick off.
Remediate-WindowsFirewallLogging.ps1
Find this script on my GitHub: Proactive-Remediations/Remediate-WindowsFirewallLogging.ps1 at main · imabdk/Proactive-Remediations (github.com)
This script will configure logging for all 3 Windows Firewall profiles according to CIS recommendations. The logging path will be set to a specific path, the log size to 16384KB and enable logging for allowed and blocked connections.
Proactive Remediations
Put all of this to use with Proactive Remediation within Microsoft Intune: https://endpoint.microsoft.com
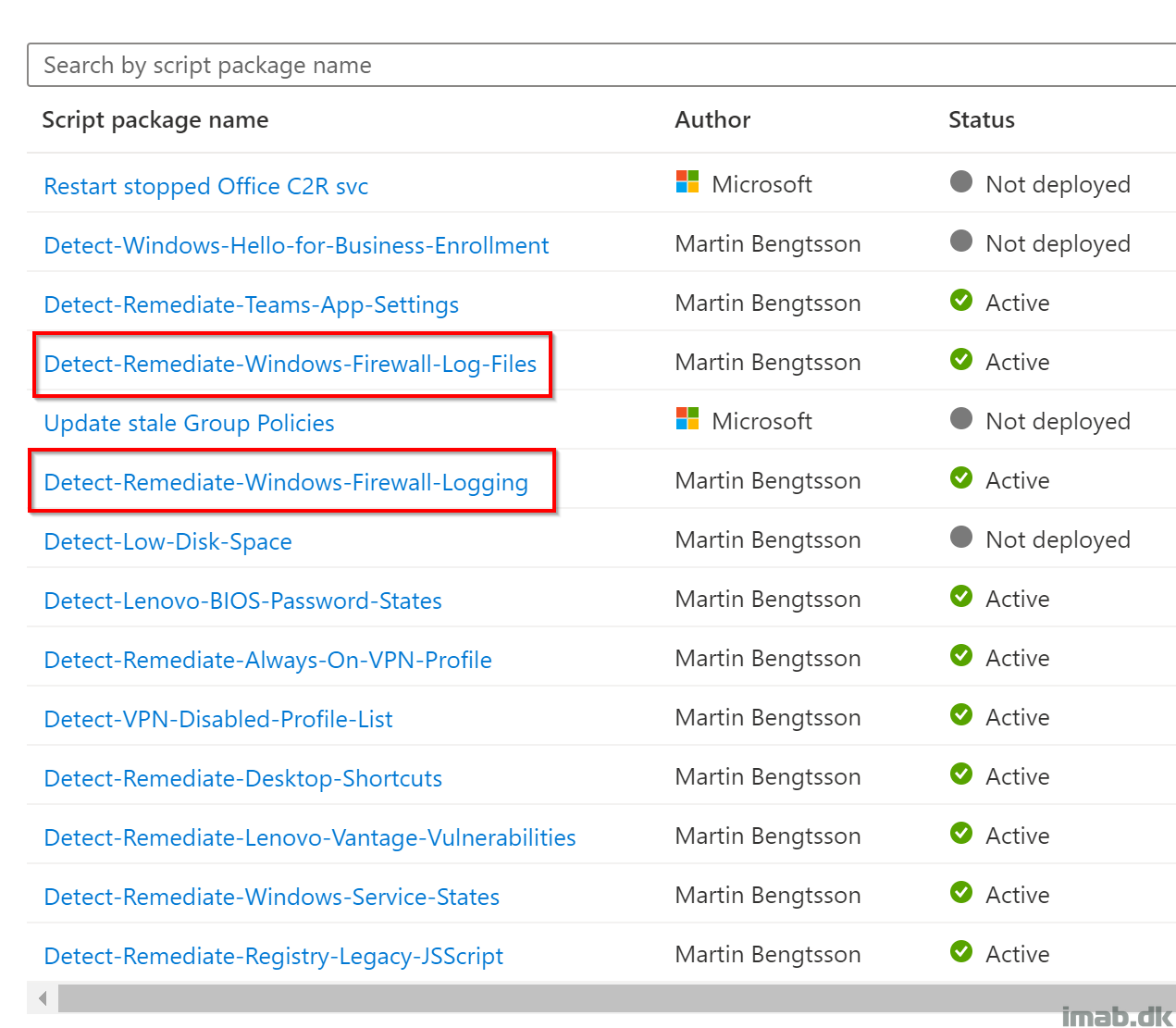
For your inspiration, below is a snippet of the 2 script packages running in my environment.
- Detect-Remediate-Windows-Firewall-Log-Files
- This is the job creating the log files with the correct permissions
- Detect-Remediate-Windows-Firewall-Logging
- This is the job configuring the logging on each firewall profile
Each script package should be configured similar to below:
Additional details
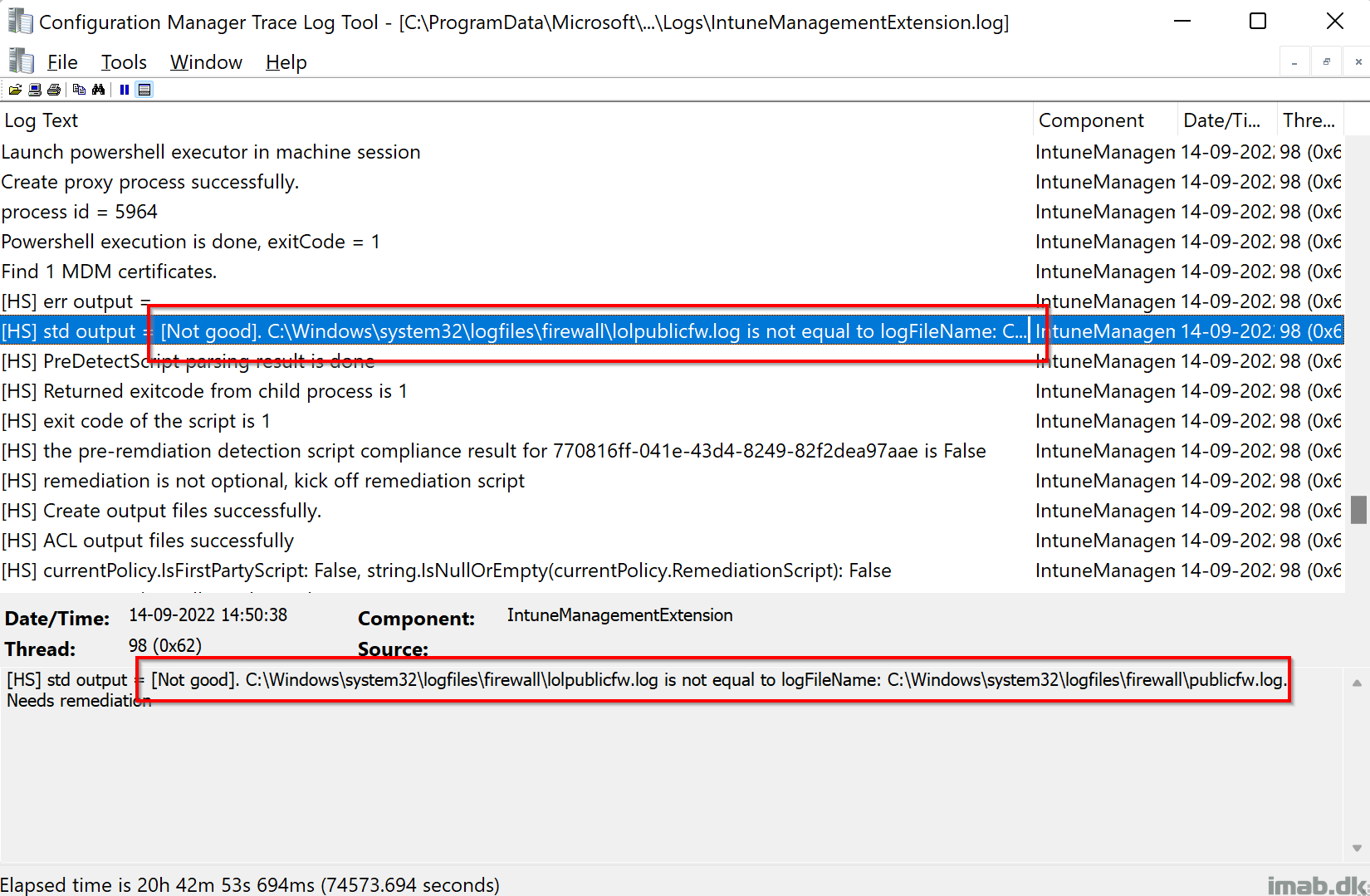
The scripts are returning their outputs to the C:\ProgramData\Microsoft\IntuneManagementExtension\Logs\IntuneManagementExtension.log:
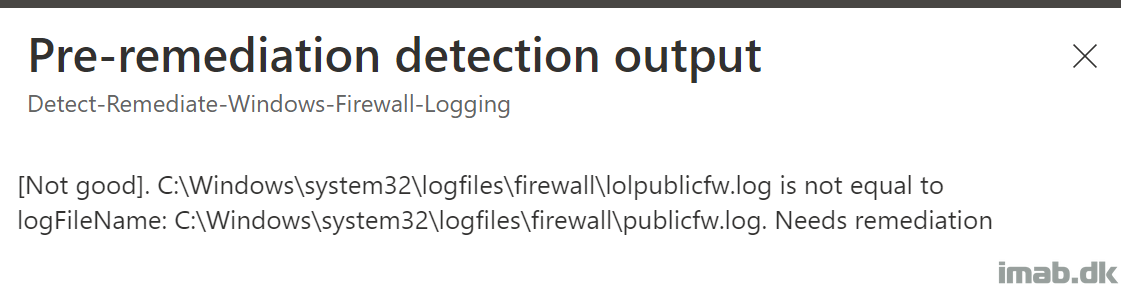
The same information can be seen in Microsoft Intune, within Proactive Remediations for each script package:
ENJOY 🙂
1 thought on “Getting Windows 11 CIS compliant: Configuring Windows Firewall Logging using PowerShell and Microsoft Intune”