Introduction
Controlling which and how removable storage devices can be used in your environment, seems to be an increasing demand from new and existing business partners. At least that’s my observation made from within the legal vertical.
It all boils down to preventing data leakage and hardening of your security posture, so I figured showing how this can be achieved with Microsoft Defender for Endpoint Device Control and Microsoft Intune, would make a decent blog post.
Device Control
This part of the Device Control feature can seem daunting at first.
It’s all configured via .xml files that you need to create yourself, and within these .xml files, you reference group and policy IDs based on unique GUIDs you also generate yourself.
Have no fear though. I will explain and give you everything you need, in order to achieve to block write and execute permissions on any non-approved removable storage in your environment.
.XML Files
My current setup consist of 4 .xml files which builds the Device Control groups and policy. I will try to elaborate on each of the xml files function.
- All of the .xml files are available via my Device Control GitHub repository, and is outlined in detail down below: imabdk/Device-Control (github.com)
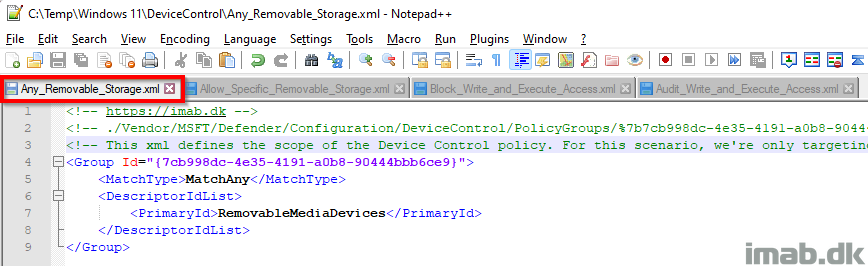
Any_Removable_Storage.xml
GitHub link: Device-Control/Any_Removable_Storage.xml at main · imabdk/Device-Control (github.com)
This xml file defines the scope or group of devices that your Device Control policy is covering.
- Group Id: This is a unique GUID generated using New-Guid
- This GUID is later on referenced in some of the other xml files
- MatchType: MatchAny: This is essentially an Or statement for the defined type of devices
- In this scenario, this doesn’t do much, as I only have 1 type of devices (RemovableMediaDevices)
- DescriptorIdList: PrimaryId: RemovableMediaDevices. This is type of devices that the scope or group is covering
- In my scenario, I’m only interested in removable storage, but other options are CdRomDevices and WpdDevices
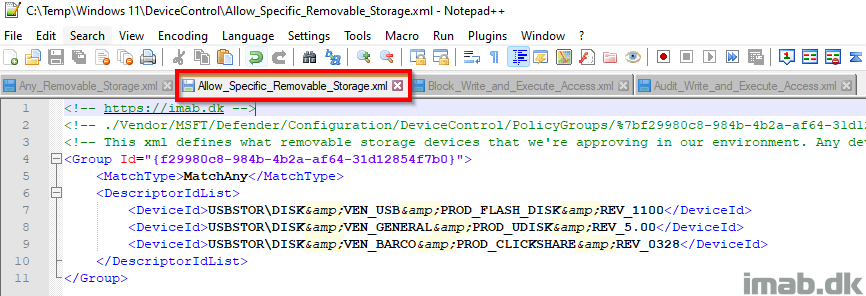
Allow_Specific_Removable_Storage.xml
GitHub link: Device-Control/Allow_Specific_Removable_Storage.xml at main · imabdk/Device-Control (github.com)
This xml defines the scope or group of devices that are approved within the Device Control policy. Any devices that are not defined within this group, are not permitted to write and execute.
- Group Id: This is a unique GUID generated using New-Guid
- This GUID is later on referenced in some of the other xml files
- MatchType: MatchAny: This is essentially an Or statement for the defined type of devices. This is required for the policy to evaluate all the defined DeviceIds
- DescriptorIdList: DeviceId: I chose to use the DeviceId to permit an entire generation of removable storage that we use internally
- This can also be other options, such as HardwareId, InstancePathId, FriendlyNameId etc.
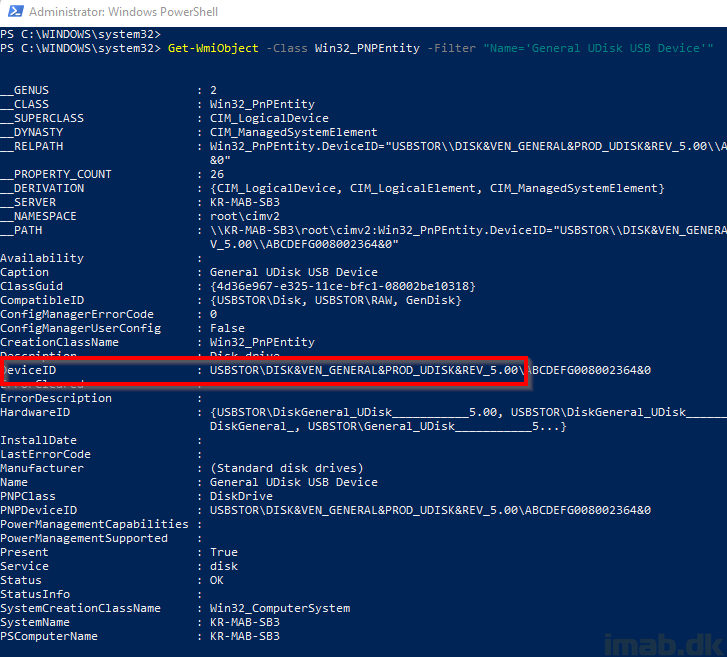
You can retrieve the DeviceID of your removable storage, by running following. Replace ‘General UDisk USB Device’ with the name of your removable storage:
Get-WmiObject -Class Win32_PNPEntity -Filter "Name='General UDisk USB Device'"
- NOTE: The character ‘&’ needs to be escaped when used in XML. Replace ‘&’ with ‘&’, as illustrated in my XML files already
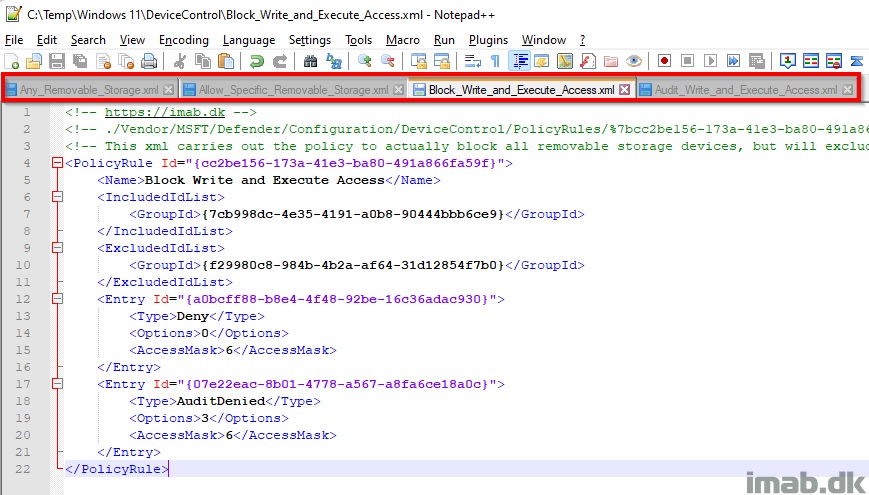
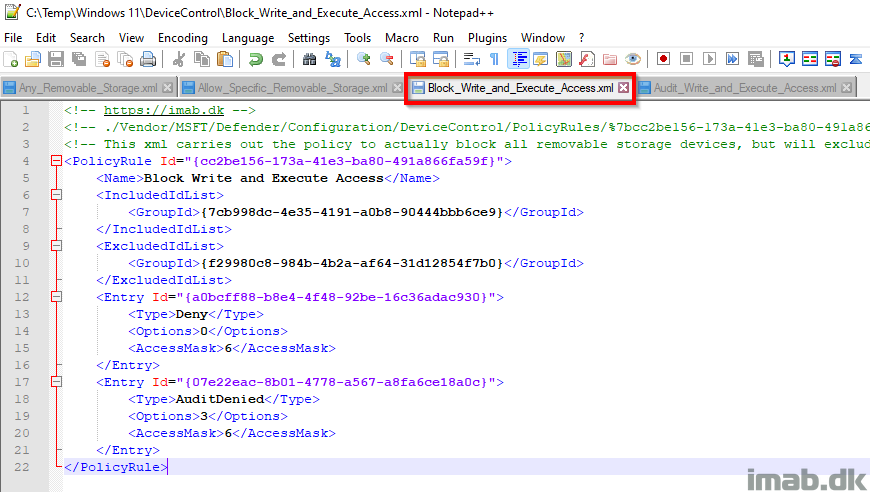
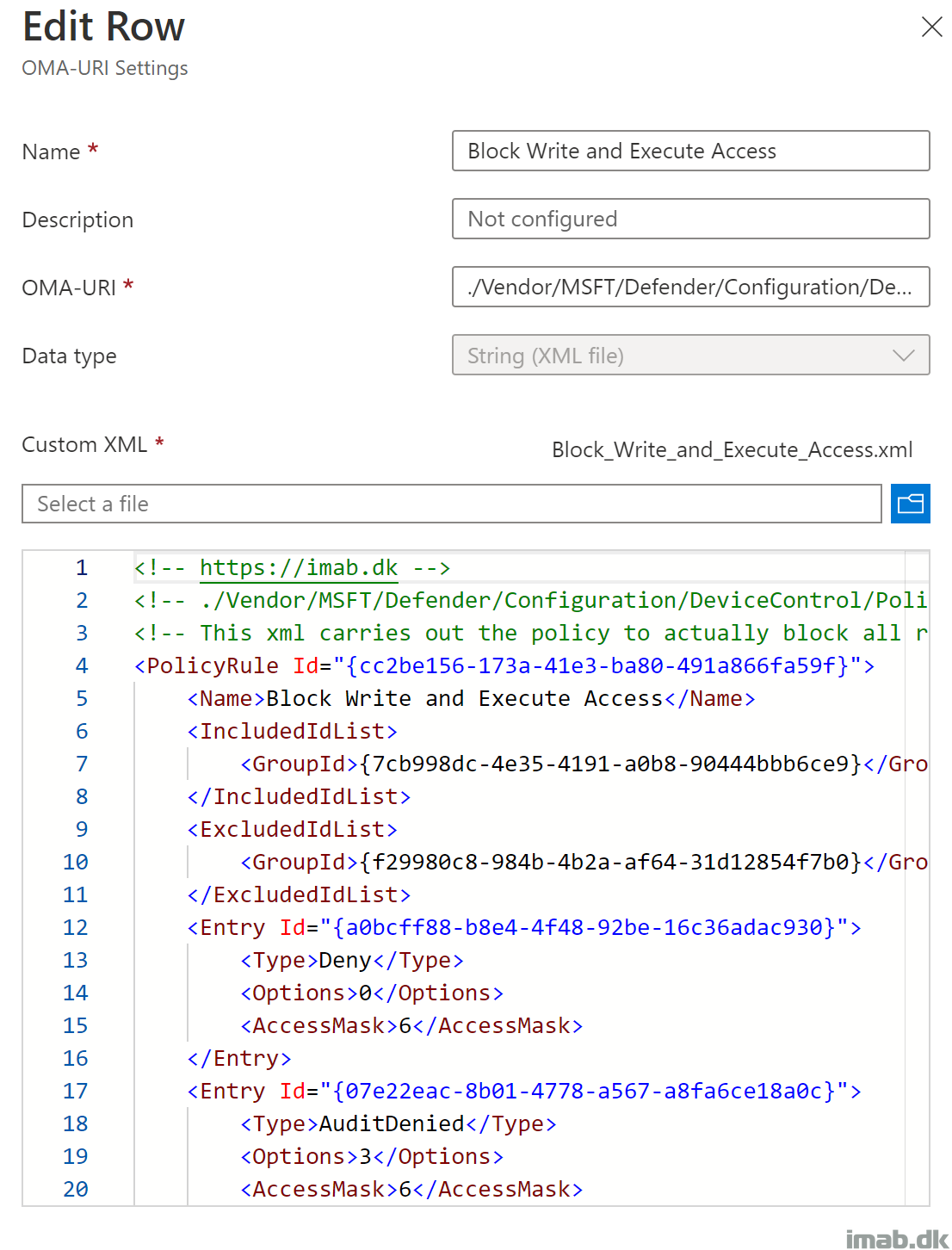
Block_Write_and_Execute_Access.xml
GitHub link: Device-Control/Block_Write_and_Execute_Access.xml at main · imabdk/Device-Control (github.com)
This xml file defines the policy to block write and execute permissions on all removable storage, but will exclude those devices defined in the Allow_Specific_Removable_Storage.xml
- PolicyRule Id: This is a unique GUID generated using New-Guid
- This GUID is later on referenced in Microsoft Intune when creating the OMA-URI
- IncludedIdList: {7cb998dc-4e35-4191-a0b8-90444bbb6ce9}. This is the unique GUID created for the group defined within Any_Removable_Storage.xml
- ExcludedIdList: {f29980c8-984b-4b2a-af64-31d12854f7b0}. This is the unique GUID created for the group defined within Allow_Specific_Removable_Storage.xml
- Entry Id: Another unique GUID for each restriction defined
- Type: Deny. Defines the action for the removable storage groups in IncludedIDList
- Options: 0. Defines whether to display notification or not
- AccessMask: 6. Defines the permissions. 6 = Write + Execute
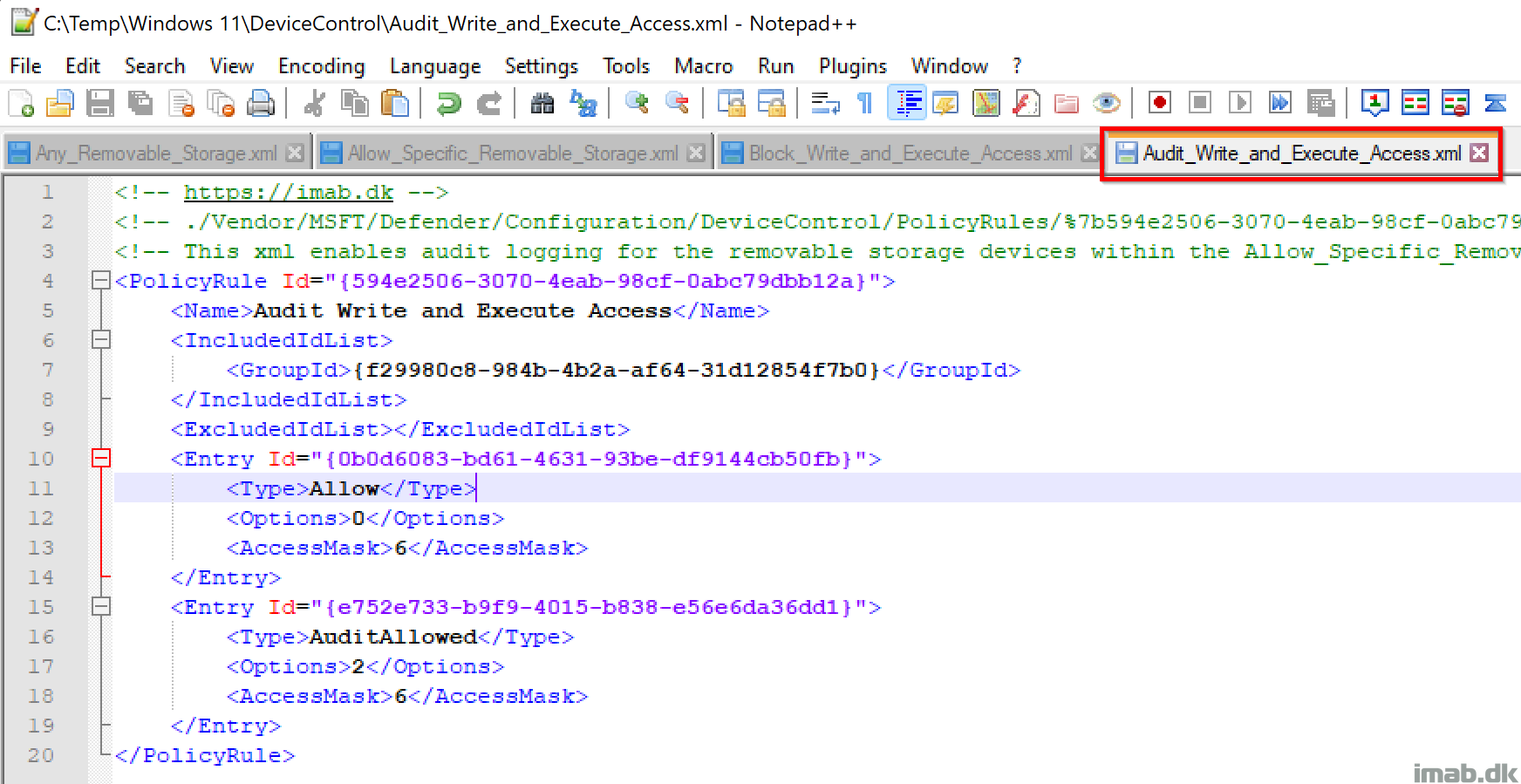
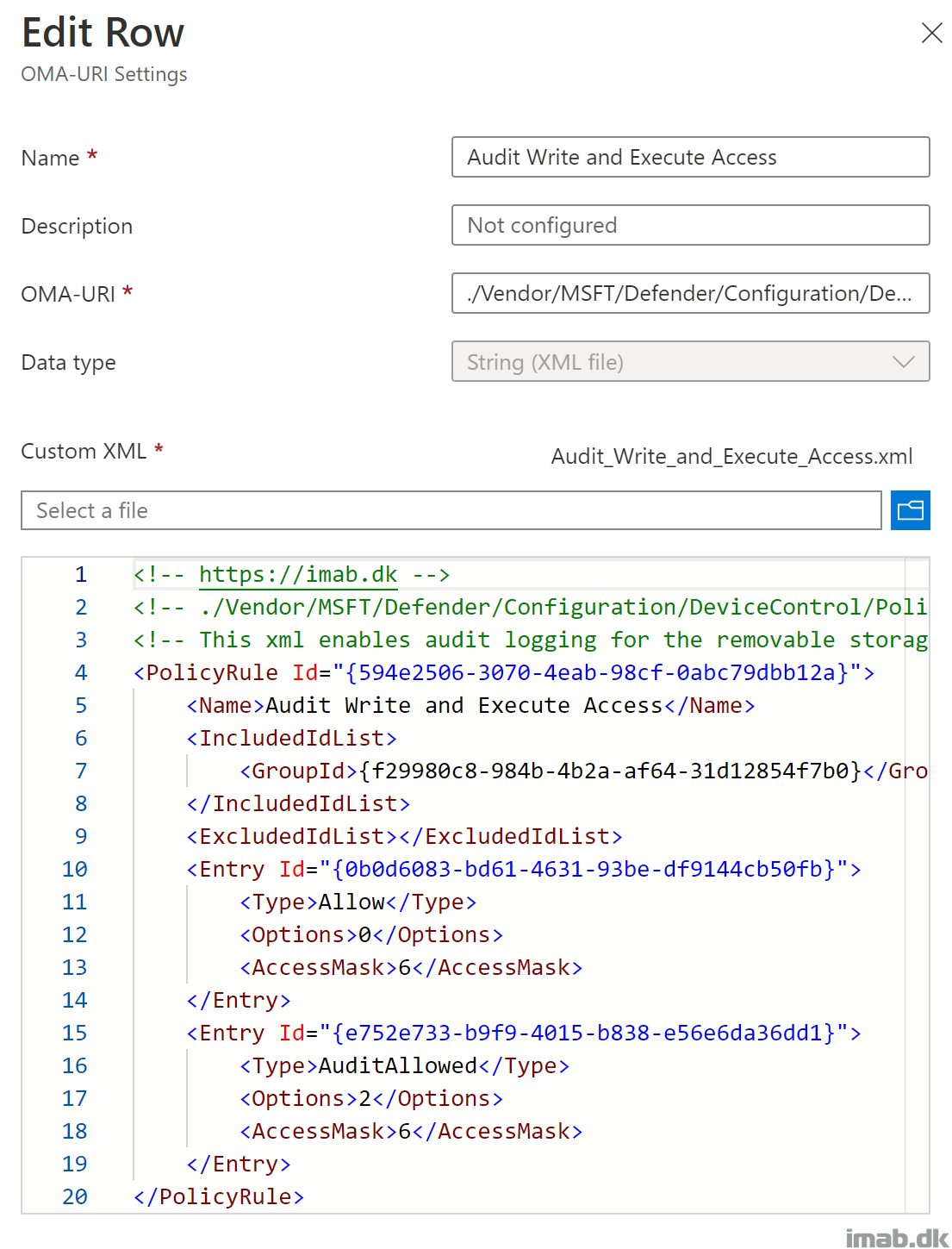
Audit_Write_and_Execute_Access.xml
GitHub link: Device-Control/Audit_Write_and_Execute_Access.xml at main · imabdk/Device-Control (github.com)
- PolicyRule Id: This is a unique GUID generated using New-Guid
- This GUID is later on referenced in Microsoft Intune when creating the OMA-URI
- IncludedIdList: {f29980c8-984b-4b2a-af64-31d12854f7b0}. This is the unique GUID created for the group defined within Allow_Specific_Removable_Storage.xml
- Entry Id: Another unique GUID for each restriction defined
- Type: Allow. Defines the action for the removable storage group in IncludedIDList
- Options: 2. Will generate audit event
- AccessMask: 6. Defines the permissions. 6 = Write + Execute
Microsoft Intune
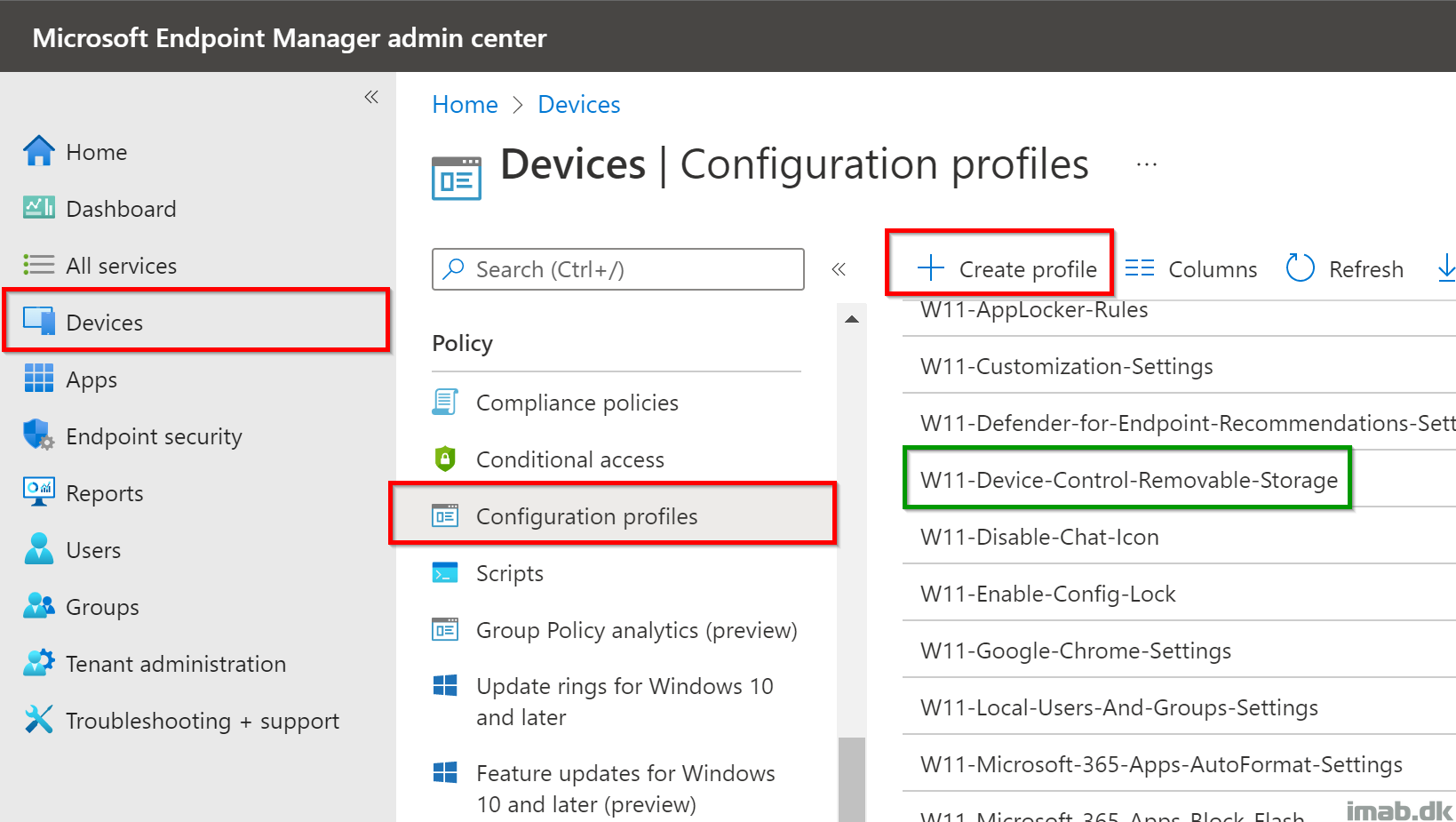
When having the xml files put together and understanding the content of those, the next steps are within Microsoft Intune.
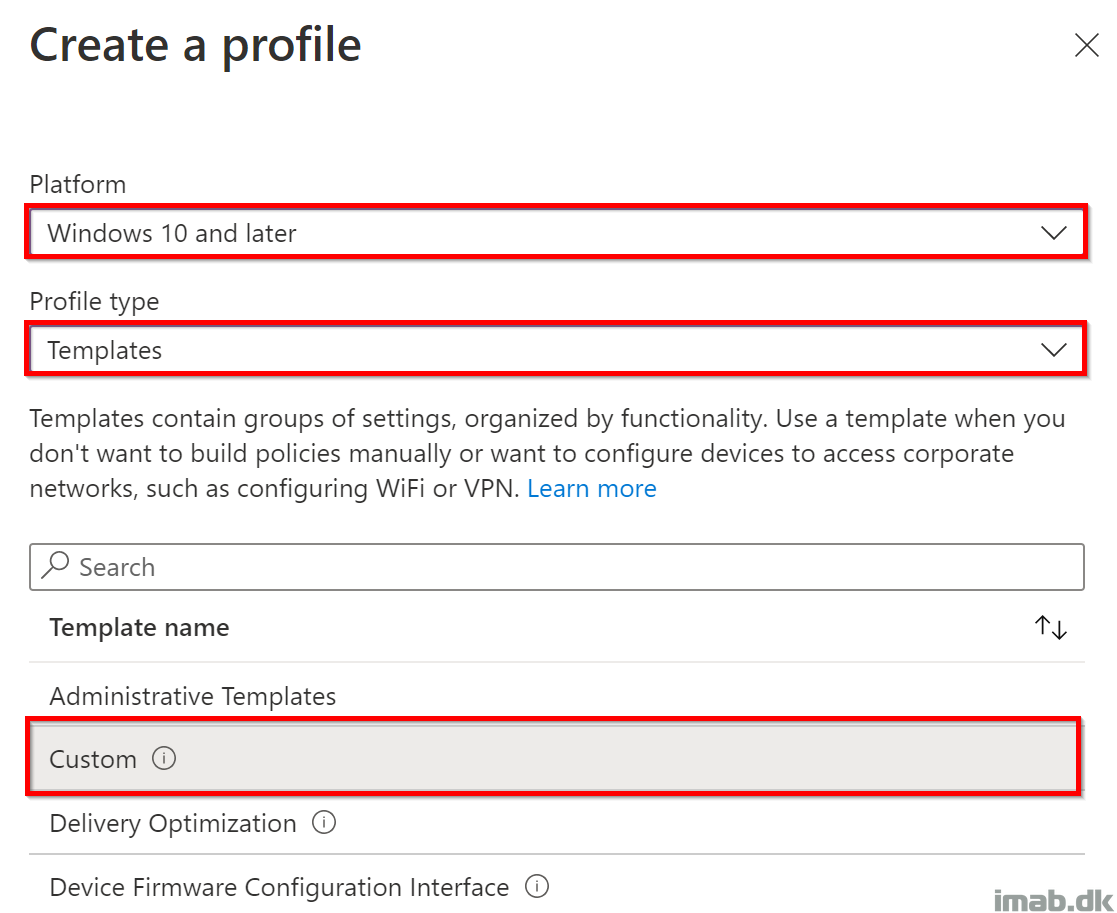
- Head into https://endpoint.microsoft.com per usual, and create a new Configuration profile as shown below:
- Platform: Windows 10 and later
- Profile type: Templates
- Template name: Custom
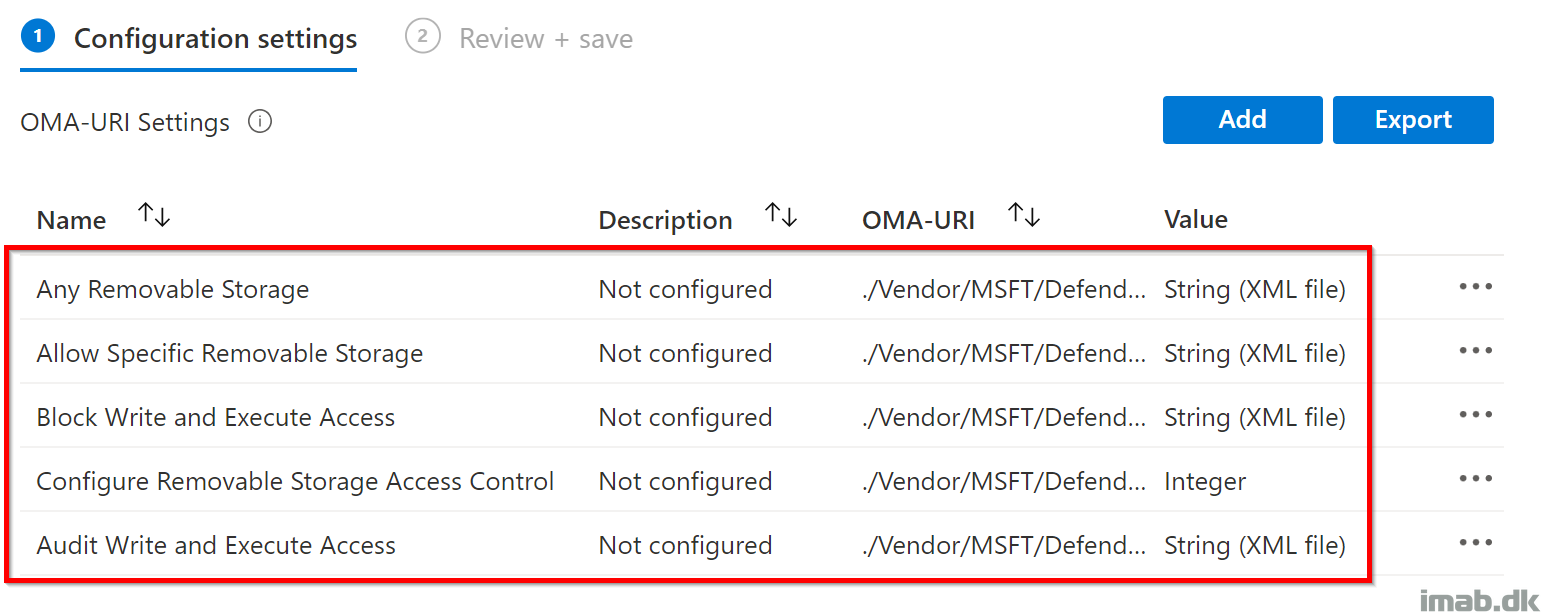
The entire configuration profile, will look similar to below once properly configured:
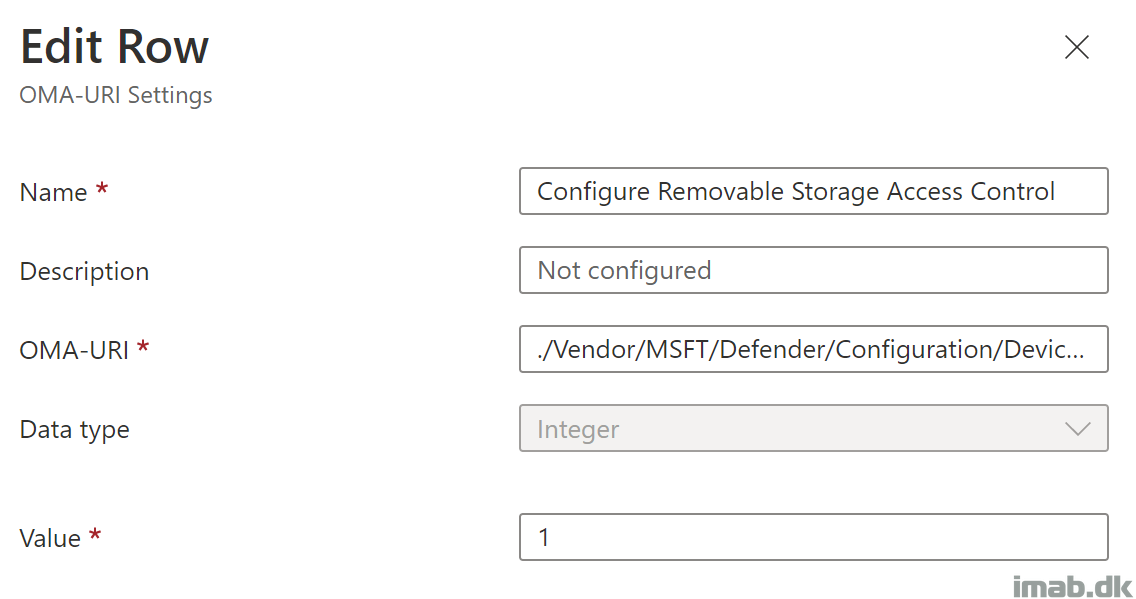
Configure Removable Storage Access Control
This will simply enable Device Control on your devices.
- Name: Configure Removable Storage Access Control
- OMA-URI: ./Vendor/MSFT/Defender/Configuration/DeviceControlEnabled
- Data type: Integer
- Value: 1
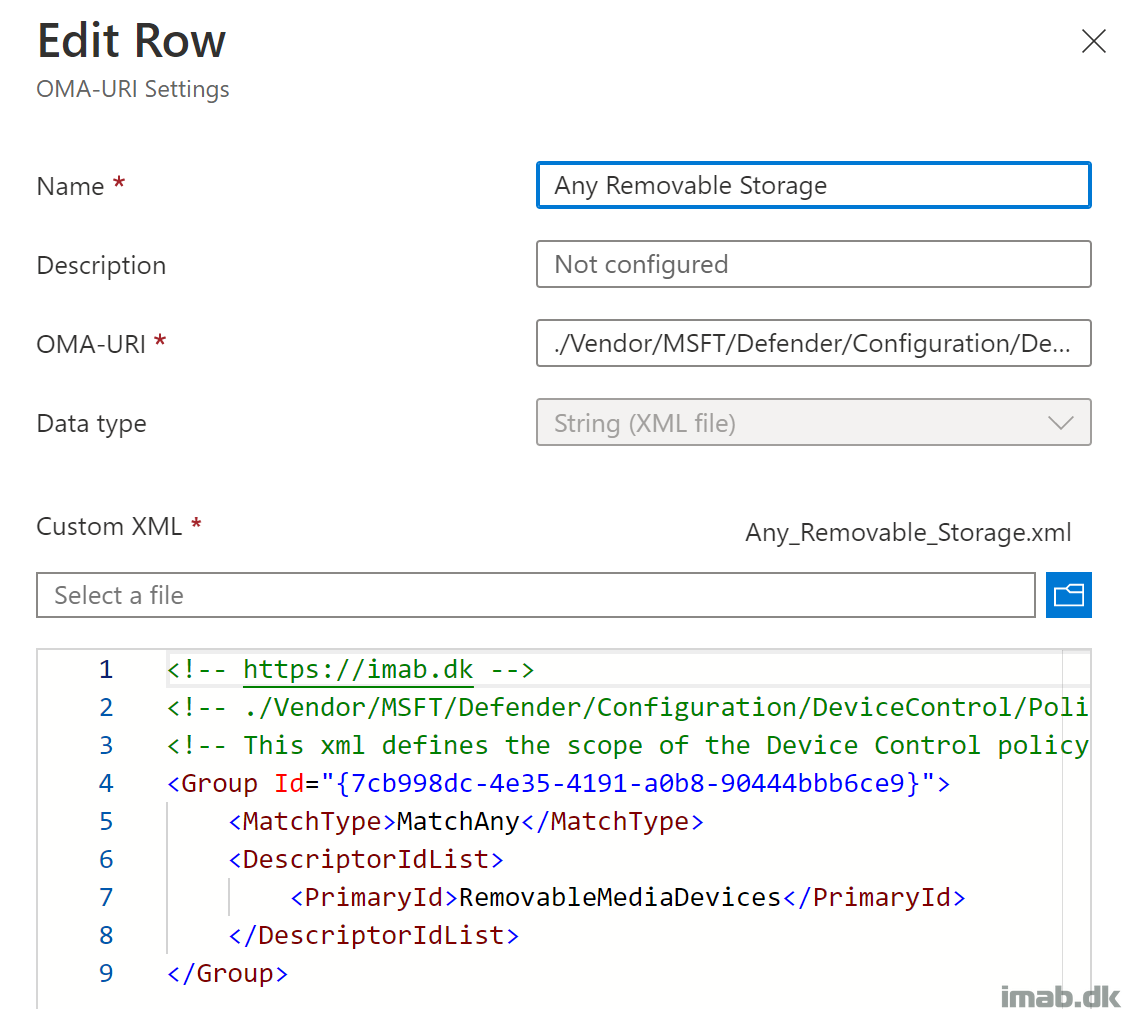
Any Removable Storage
This will configure the Any Removable Storage group. Notice the reference in the OMA-URI to the unique group GUID.
NOTE: ‘%7b’ and ‘%7d’ translates into ‘{‘ and ‘}’
- Name: Any Removable Storage
- OMA-URI: ./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyGroups/%7b7cb998dc-4e35-4191-a0b8-90444bbb6ce9%7d/GroupData
- Data type: String (XML file)
- Custom XML: Any_Removable_Storage.xml
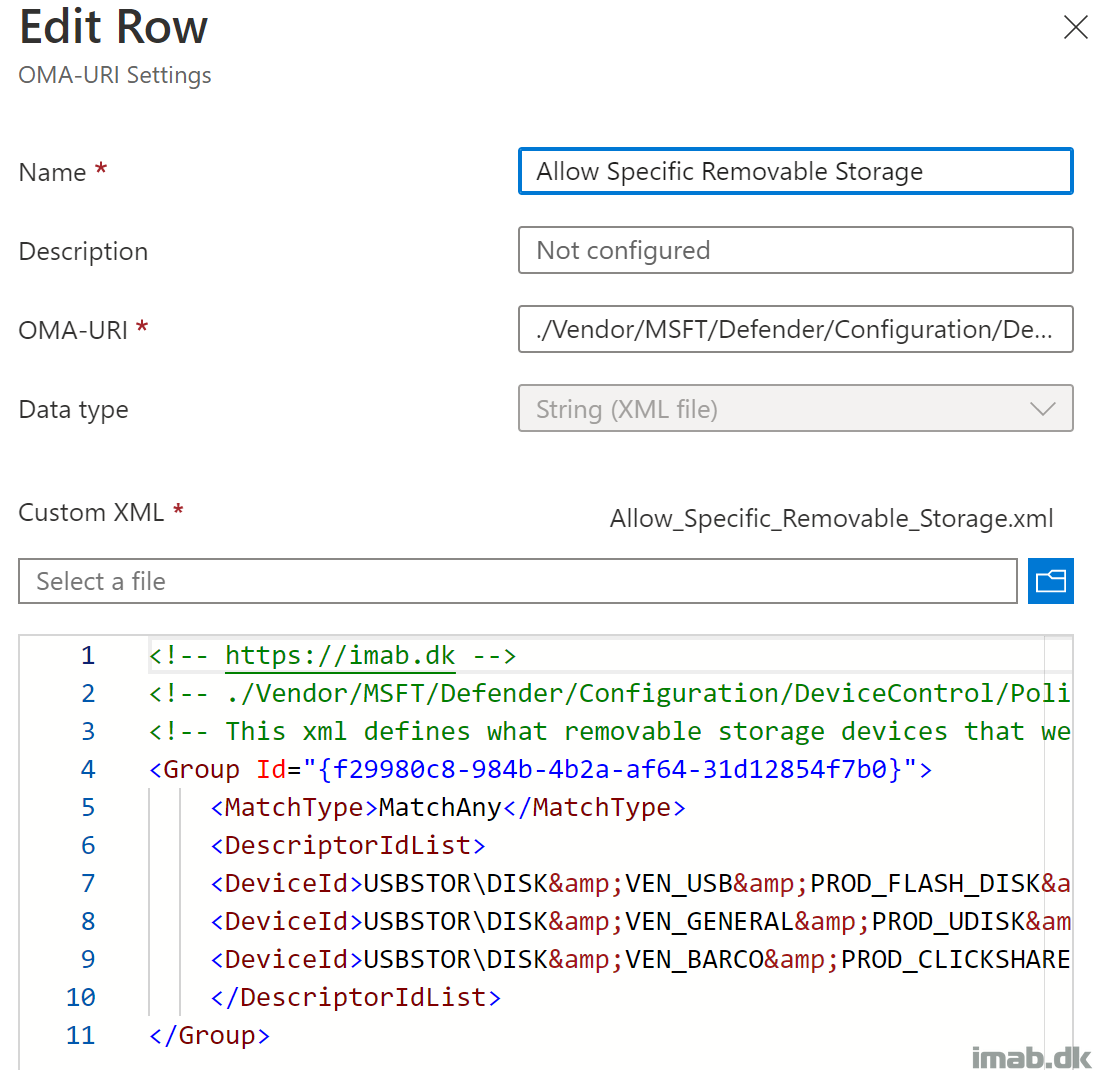
Allow Specific Removable Storage
This will configure the Allow Specific Removable Storage group. Notice the reference in the OMA-URI to the unique group GUID.
NOTE: ‘%7b’ and ‘%7d’ translates into ‘{‘ and ‘}’
Also, this xml contains the approved storage from my environment. Replace with your own!
- Name: Allow Specific Removable Storage
- OMA-URI: ./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyGroups/%7bf29980c8-984b-4b2a-af64-31d12854f7b0%7d/GroupData
- Data type: String (XML file)
- Custom XML: Allow_Specific_Removable_Storage.xml
Block Write and Execute Access
This will configure the Block Write and Execute Access policy. Notice the reference in the OMA-URI to the unique policy GUID.
NOTE: ‘%7b’ and ‘%7d’ translates into ‘{‘ and ‘}’
- Name: Block Write and Execute Access
- OMA-URI: ./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyRules/%7bcc2be156-173a-41e3-ba80-491a866fa59f%7d/RuleData
- Data type: String (XML file)
- Custom XML: Block_Write_and_Execute_Access.xml
Audit Write and Execute Access
This will configure the Audit Write and Execute Access policy. Notice the reference in the OMA-URI to the unique policy GUID.
NOTE: ‘%7b’ and ‘%7d’ translates into ‘{‘ and ‘}’
- Name: Block Write and Execute Access
- OMA-URI: ./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyRules/%7b594e2506-3070-4eab-98cf-0abc79dbb12a%7d/RuleData
- Data type: String (XML file)
- Custom XML: Audit_Write_and_Execute_Access.xml
Additional details
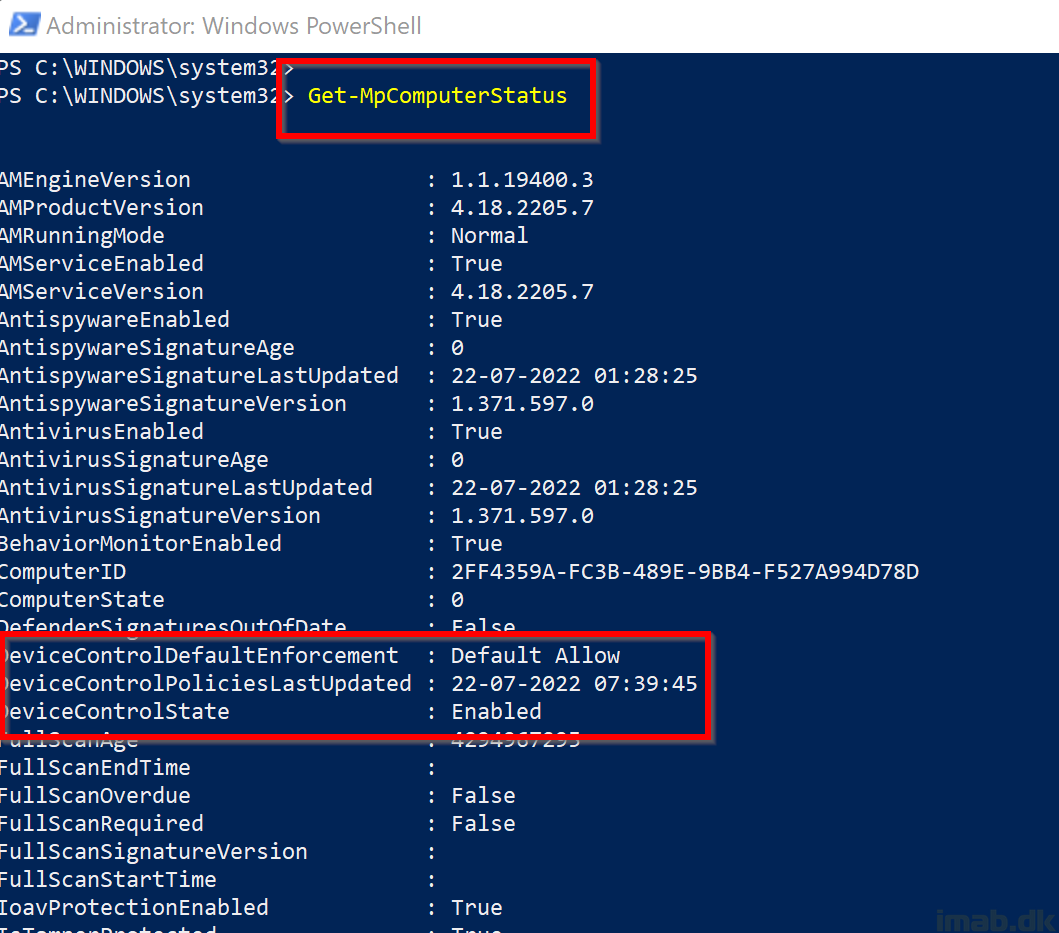
Running Get-MpComputerStatus will tell you if you got Device Control enabled, and when the last policy update occurred:
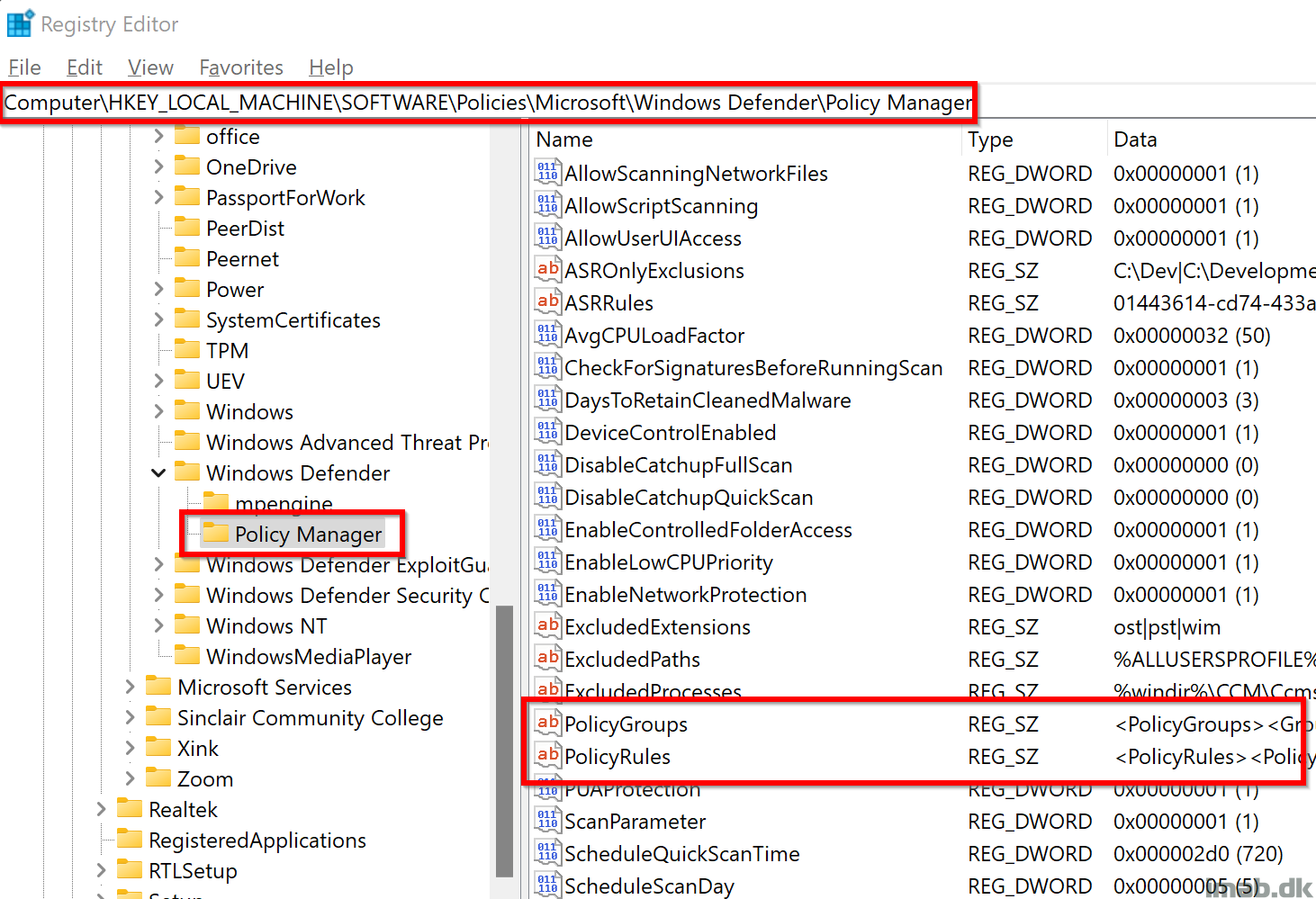
The Device Control groups and policies, once configured correctly, will also be written into registry here:
- Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager
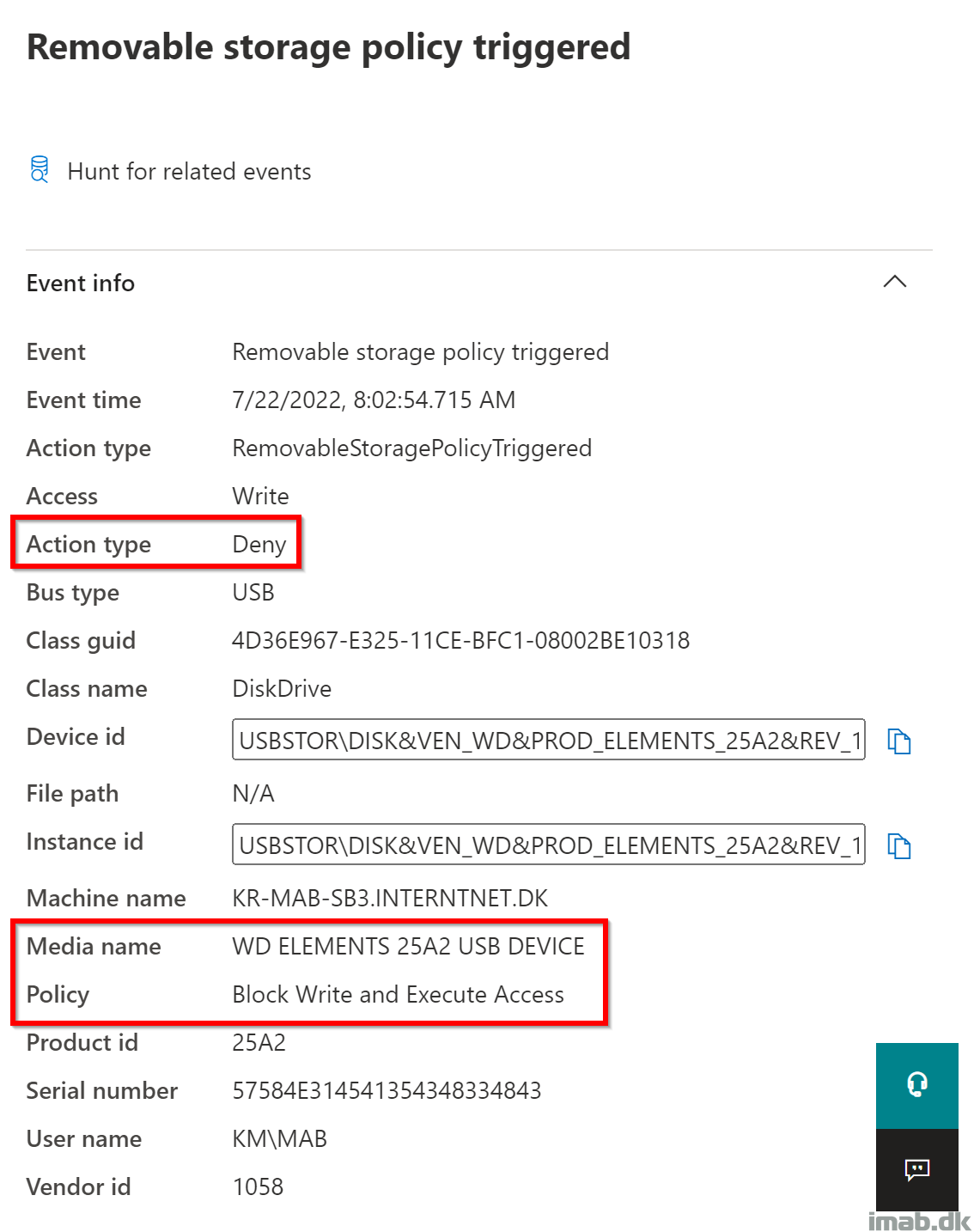
Over in the Defender for Endpoint portal (https://security.microsoft.com), you will be able to query for events related to removable storage. An example of me being denied to write to a personal USB hard drive down below:
- More on hunting for these events here: Microsoft Defender for Endpoint Device Control Removable Storage Access Control, removable storage media | Microsoft Docs
Hello Martin, first of all thank you very much for the great solution. Unfortunately, I get an error on the client and don’t get it solved. Maybe you can help me further?
RuleData [./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyRules/%7bc978cc84-1bf0-4c50-81ef-e7cbec07b739%7d/RuleData]
Error
-2016345612
GroupData [./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyGroups/%7bf8ed3166-9535-4e01-a620-1100178b85d3%7d/GroupData]
Error
-2016345612
GroupData [./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyGroups/%7b09341d64-14b8-42e6-a197-a16bb910cca8%7d/GroupData]
Error
-2016345612
RuleData [./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyRules/%7b2aad0681-5be0-4608-9355-95edfabf42b3%7d/RuleData]
Error
-2016345612
One of the Eventlog Errors:
MDM-ConfigurationManager: Befehlsfehlerstatus. ID der Konfigurationsquelle (26AF168C-0BFD-481E-A107-A563989BCD47). Registrierungsname (MDMDeviceWithAAD). Anbietername (Defender). Befehlstyp (Add: from Replace or Add). CSP-URI (./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyRules/{2aad0681-5be0-4608-9355-95edfabf42b3}/RuleData). Ergebnis (Unbekannter Fehler).
Thank youand best regards
Hi,
Thanks a lot for this clear and detailed post, unfortunately when applying I get error on all PolicyGroups and PolicyRoles, neither are they created in my registry. How can I troubleshoot this?
Errorcode -2016345612
and
SETTING
GroupData [./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyGroups/%7b4afab9a0-92e9-431b-9f18-0442eeaa66b8%7d/GroupData]
STATE
Error
ERROR CODE
0x87d101f4
Thanks for this! Microsoft were supposed to make this easy and use Device Control for these options , however deploying this just comes up with ” (./vendor/msft/defender/configuration/devicecontrol/policyrules/6520d3b6-bb95-4d1d-9b97-5d42ac0f5faf), Result: (Invalid class string).”
When I first tried to deploy this I got the error
“MDM ConfigurationManager: Command failure status. Configuration Source ID: (CDA5B110-73DB-4492-BDE0-AE0D38AB3672), Enrollment Name: (MDMDeviceWithAAD), Provider Name: (Defender), Command Type: (Add: from Replace or Add), CSP URI: (./Vendor/MSFT/Defender/Configuration/DeviceControl/PolicyRules/{cc2be156-173a-41e3-ba80-491a866fa59f}/RuleData), Result: (Unspecified error).”
I switched over the String(XML) to String , removed the XML comments and added new GUID’s ( , maybe it was conflicting with yours? ) for the GroupID’s ( and referenced these in the ExcludedIdList and IncludedIdList and it works!
Yeah, something seems to have changed or be conflicting. I see some errors in my end too now. I’ll take a look asap.
Turns out that the comments are evil all of a sudden. They weren’t initially when I wrote the post. Thanks for making me aware 🙂