Introduction
Late last night my time, Tamper Protection in the Microsoft Defender stack went Generally Available.
In short and as the name implies, this is a feature which essentially locks Microsoft Defender and prevents your security settings from being tampered with, including changes made by an administrator.
From a security perspective, this is a great and welcomed addition – let’s take a closer look. 🙂
PS. I did find some oddities in some of the behavior when trying to disable Microsoft Defender through Group Policy. More on that in the end of the post.
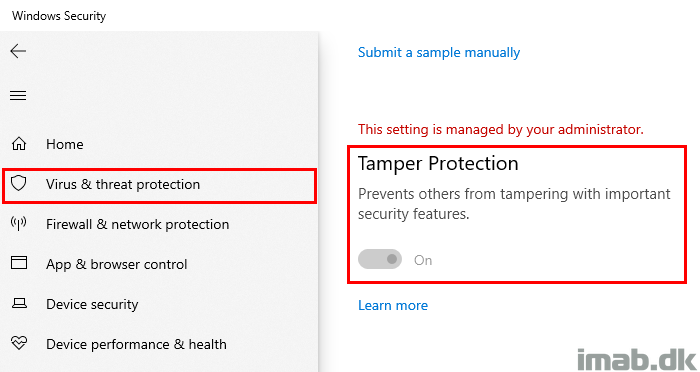
Turn ON Tamper Protection
I’m not going into much details on how to do this, but there’s currently only one option to turn Tamper Protection on or off when considering managing the enterprise, and that’s through Intune.
- Go to the Microsoft 365 Device Management Portal: https://devicemanagement.microsoft.com.
- Create a new Device Configuration Profile similar to below.
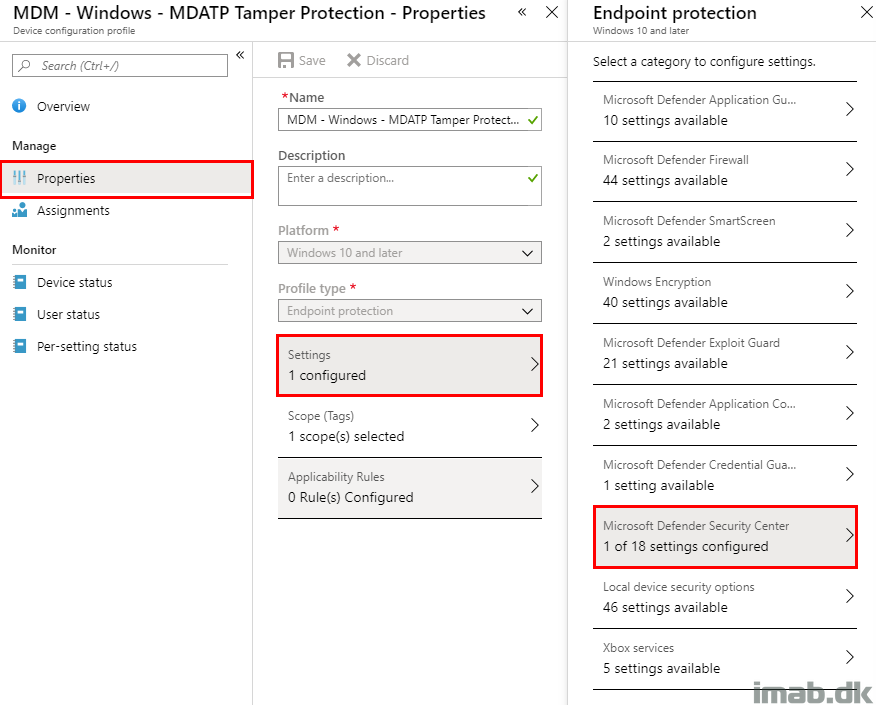
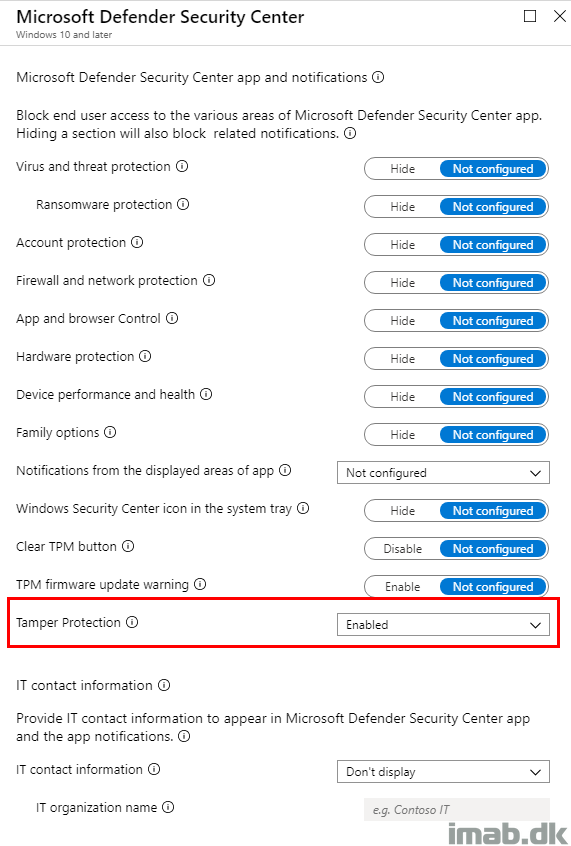
- Configure Tamper Protection to Enabled.
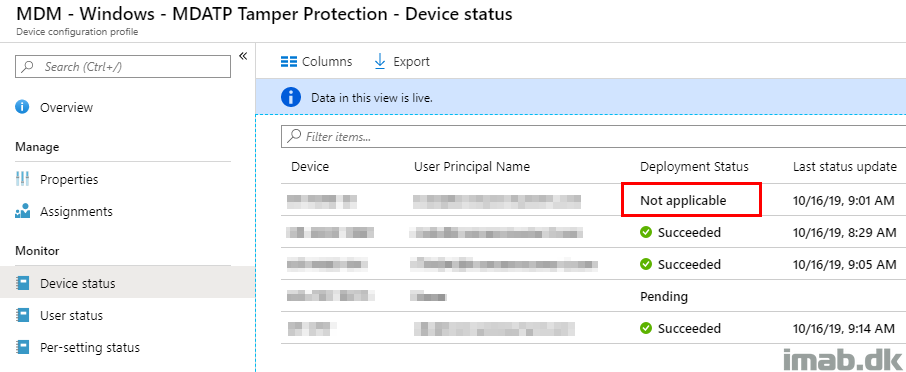
Assignment and Applicability
I’m assigning this to my devices and noticed there’s a device returning Not applicable. This is due to the requirement of Windows 10 1903 as a minimum and the highlighted device running on Windows 10 1809.
Pre-Tamper Protection
So this is the exciting part. Demonstrating what’s possible prior to enabling Tamper Protection (and obviously also what’s not possible after enabling Tamper Protection).
Taking a closer look on the current configuration running Get-MpPreference, you will see that Real Time Monitoring is enabled as expected.
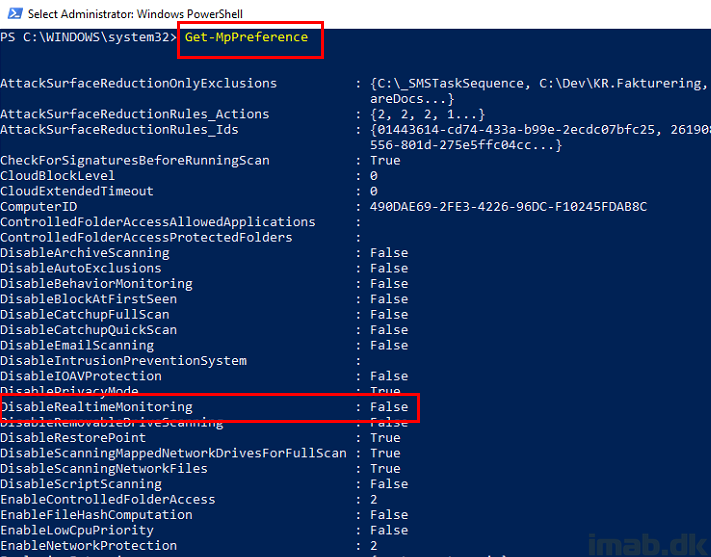
When running Set-MpPreference -DisableRealtimeMonitoring $true as an local administrator, you will find yourself able to disable Real Time Monitoring.
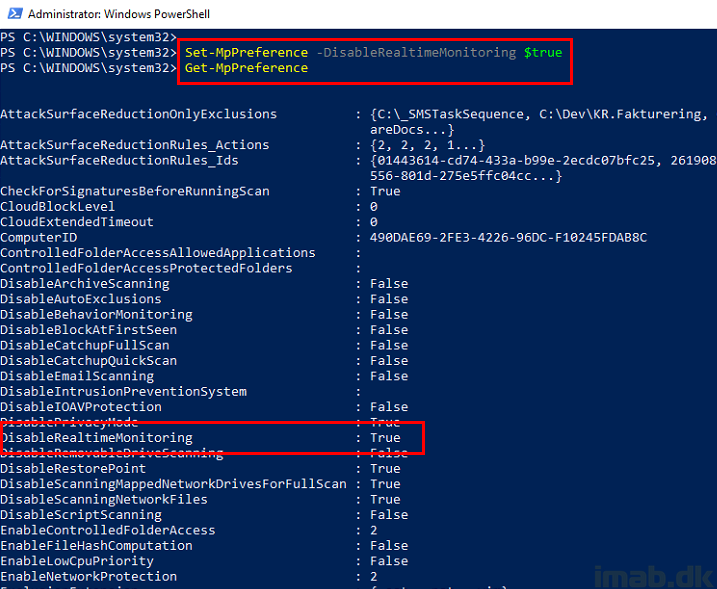
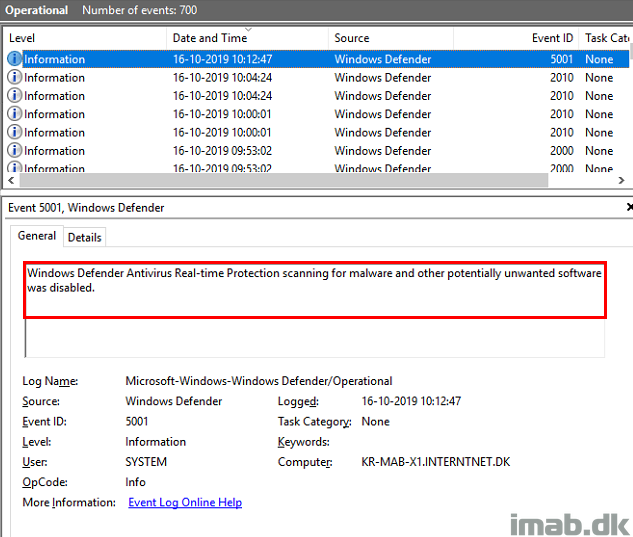
Everything is logged into the Windows Defender event log, where your actions are confirmed; Real-time Protection is now disabled.
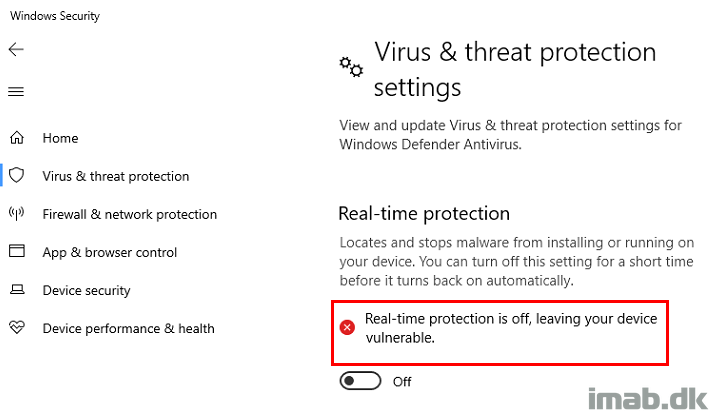
Eventually leaving your device vulnerable, which you also are made aware of in the Windows Security Center.
Post-Tamper Protection
So what happens when you try to carry out some of those actions after you enabled Tamper Protection?
First off, confirming that Tamper Protection indeed is enabled. This can be done running Get-MpComputerStatus. IsTamperProtected needs to return True.
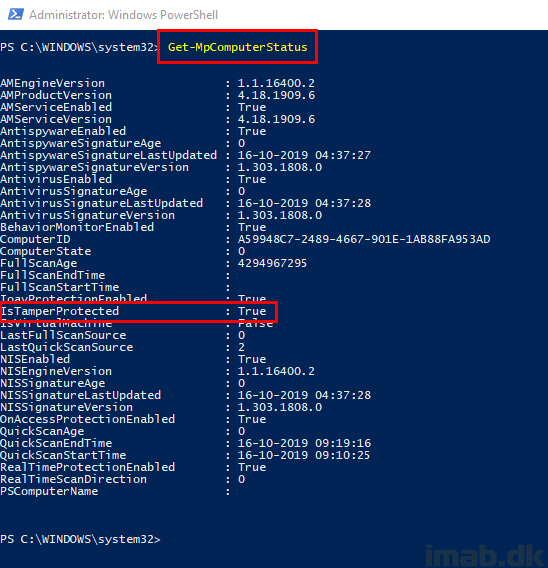
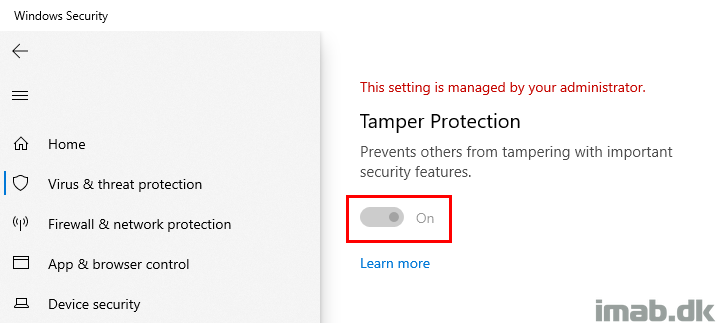
Or you can view the setting in the Windows Security Center.
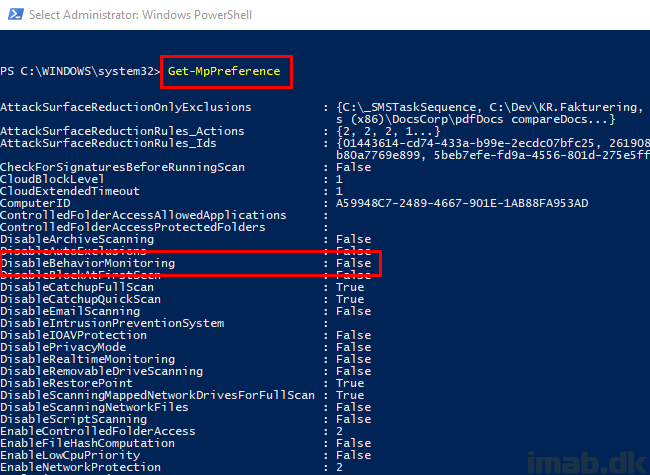
Yet again, I’m confirming that the setting I’m about to change is enabled. For sake of the example, I’m trying to disable BehaviorMonitoring. This is the setting I highlighted below.
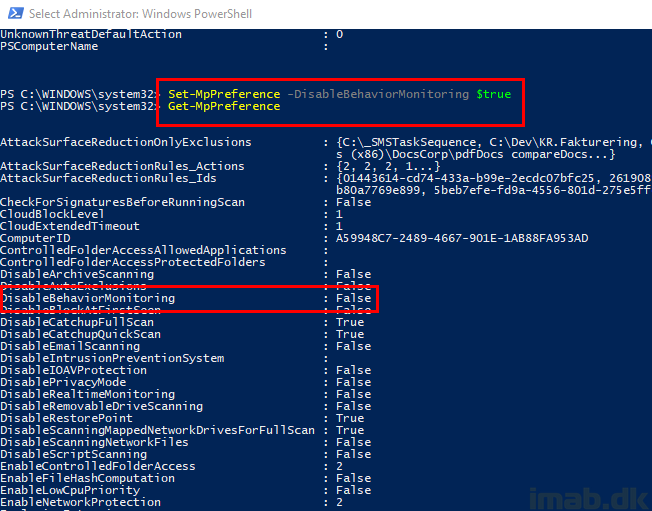
This is usually achieved by running Set-MpPreference -DisableBehaviorMonitoring $true, also as illustrated below.
But as you see when running Get-MpPreference immediately thereafter, you will find that BehaviorMonitoring is still set to False and therefore still enabled.
The attempt to disable BehaviorMonitoring is also logged into the Windows Defender event log, but is done a tad differently than without Tamper Protection.
This time the change is picked up, but the value is never updated to something new.
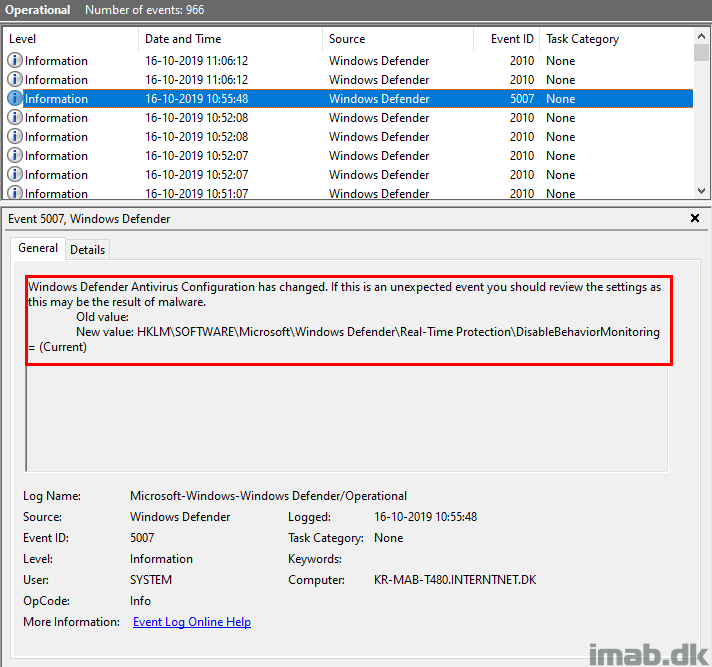
Oddity?
I don’t know if this is expected, but I managed to get the UI to indicate that Tamper Protection all of a sudden was off.
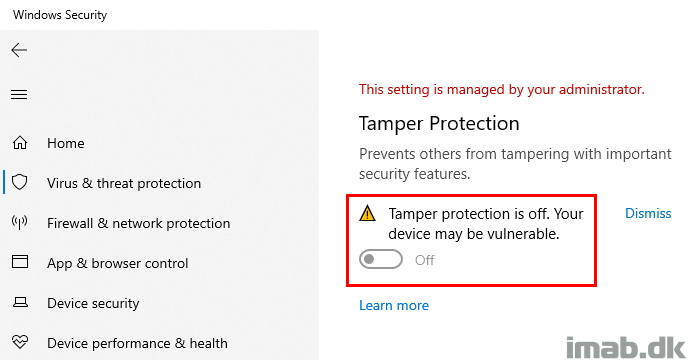
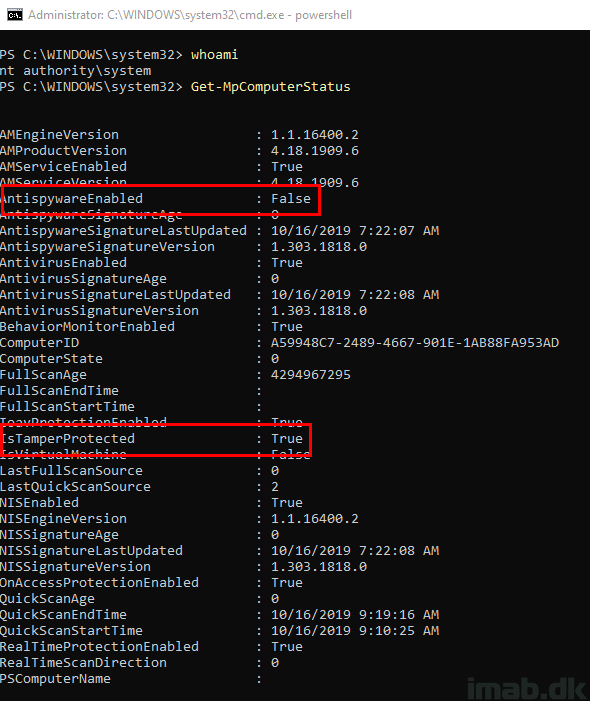
I also ended up having AntispywareEnabled set to False. I would say this is unexpected and this is something that should be prevented by Tamper Protection.
Notice that IsTamperProtected still comes out as True.
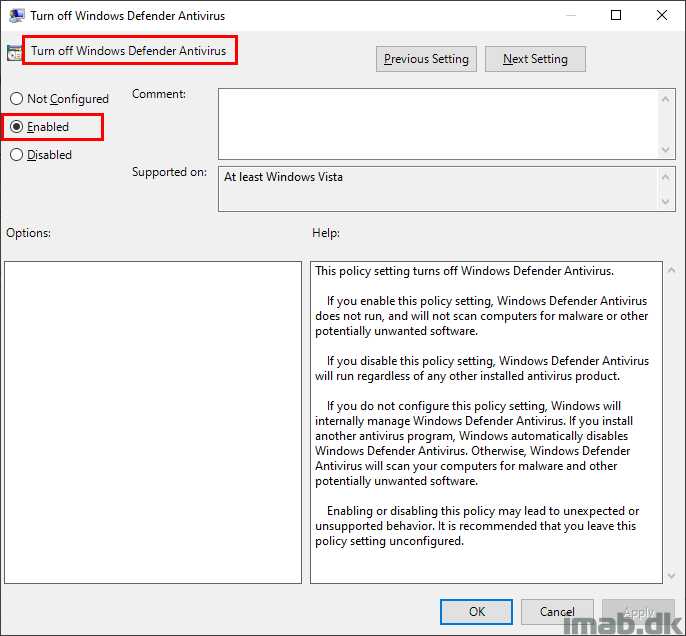
I managed to do so by setting this Group Policy locally via gpedit.msc and running a gpupdate: Turn off Windows Defender Antivirus
Looking in the Windows Defender event log also indicates that I managed to disable some parts of Windows Defender.
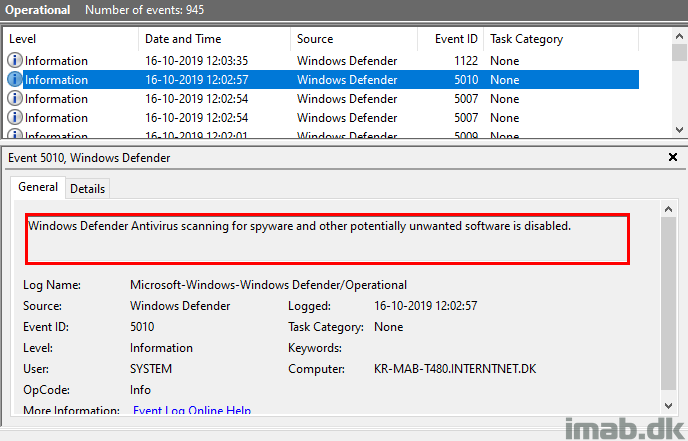
However, running another sync with Microsoft Intune changed the Tamper Protection slider back to On, though still leaving me with the warning about the setting being off. See below illustrations.
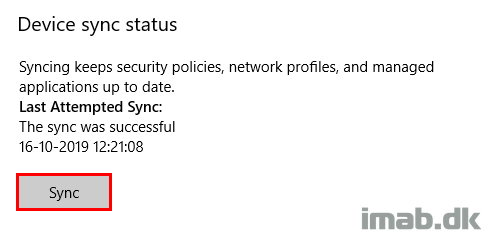
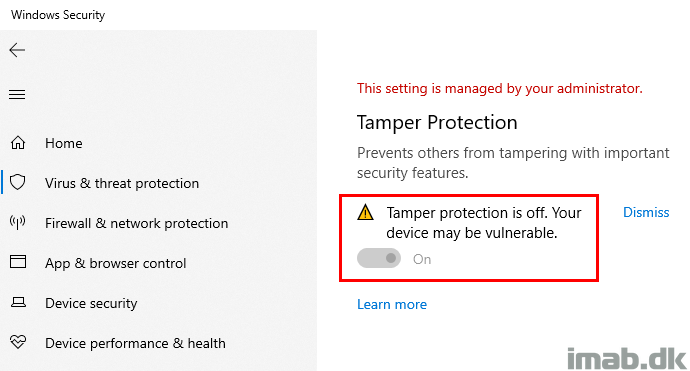
More Information
- https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-antivirus/prevent-changes-to-security-settings-with-tamper-protection#turn-tamper-protection-on-or-off-for-your-organization-using-intune
- https://techcommunity.microsoft.com/t5/Microsoft-Defender-ATP/Tamper-protection-now-generally-available-for-Microsoft-Defender/ba-p/911482