Introduction
This is a little something on the new option with Conditional Access, where you can specify restrictions for registering the end users security information used with Multi-Factor Authentication.
This is a nifty addition, enabling you to control when and where the security information can be added or changed, making sure it’s not an attacker who’s messing with the details.
In this post i’m trying to put this into the context of enrolling a new device, in this example an iOS device, where MFA is required for enrollment.
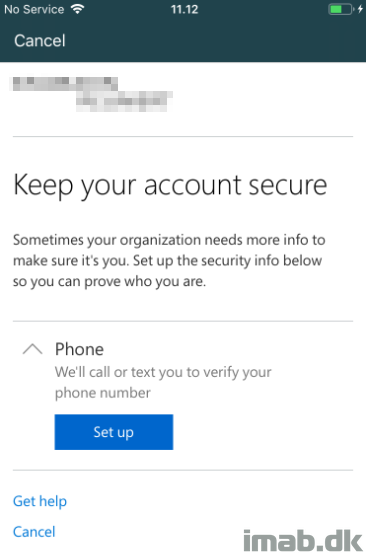
If the enrollment is being done by a user who’s without security information (imagine a newly hired employee), the user is initially prompted to register the security information. Now also imagine this being done by an attacker instead. Not good. Therefore it’s desirable to control from where the registering of the security information can be done. Curious? Read on 🙂
Require MFA for enrollment
For the completeness of this example, let’s begin with how you require MFA for enrolling devices into Intune using Conditional Access. This is quite easy:
- Log into the Microsoft 365 Device Management Portal: https://devicemanagement.microsoft.com
- Locate Conditional Access -> Policies and create a New policy:
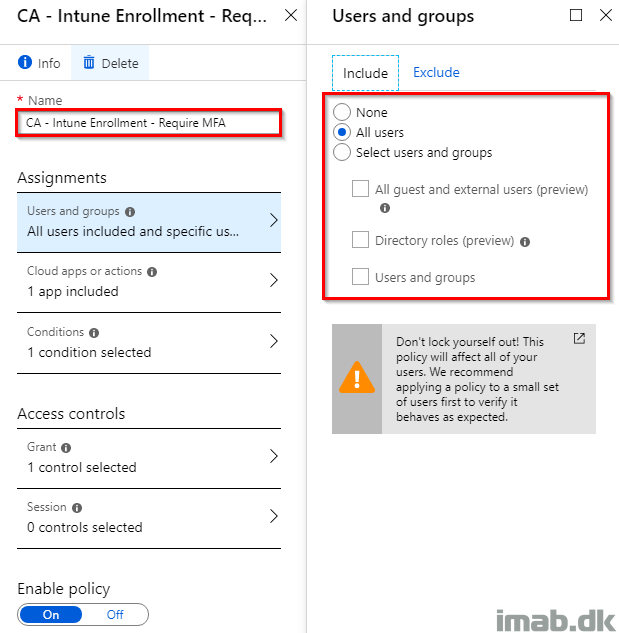
- Give the new Conditional Access policy a suitable name and assign it to the desired users:
- Select the Microsoft Intune Enrollment app in Cloud apps or actions:
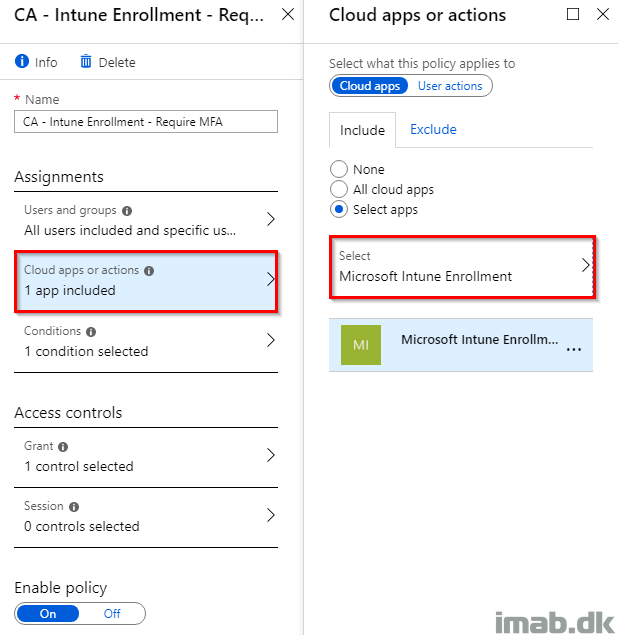
- In this example, I want to target all device platforms except Windows. Therefore I select Any device on the include tab:
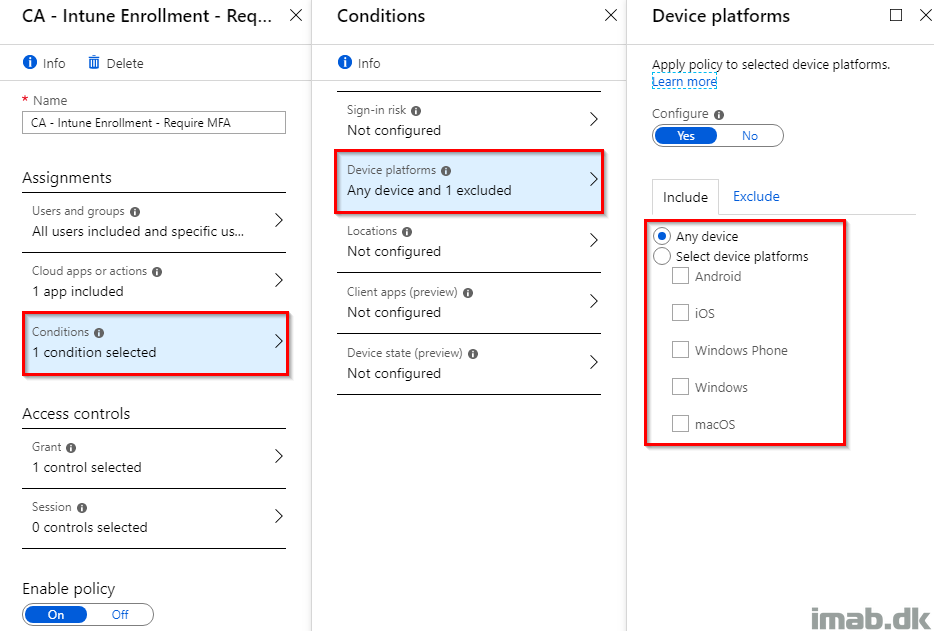
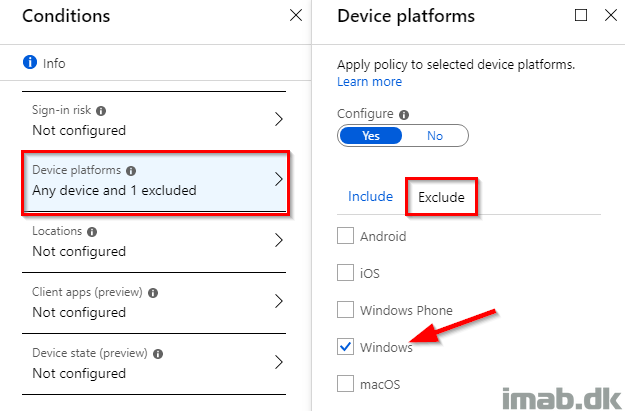
- And exclude Windows on the Exclude tab:
- I don’t want MFA when enrolling Windows devices into Intune, as this is already restricted to corporate devices (enrollment restrictions).
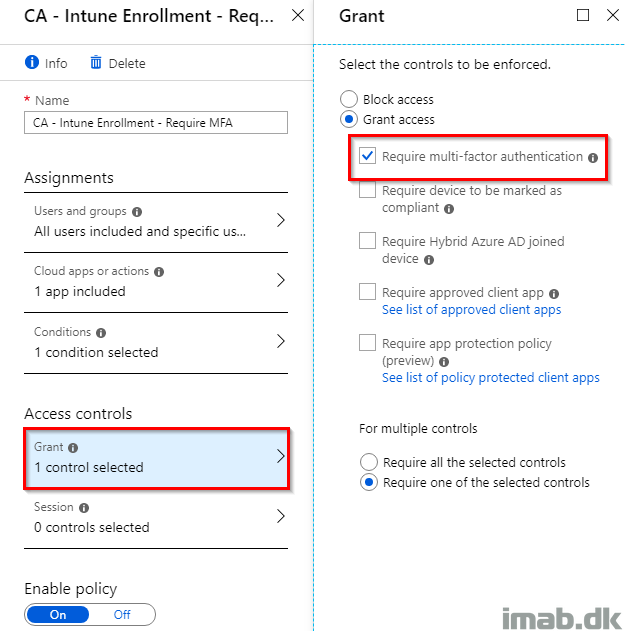
- Select to grant access and Require multi-factor authentication and enable the policy once ready:
Security Information
- Next, create another Conditional Access policy for the registering of security information:
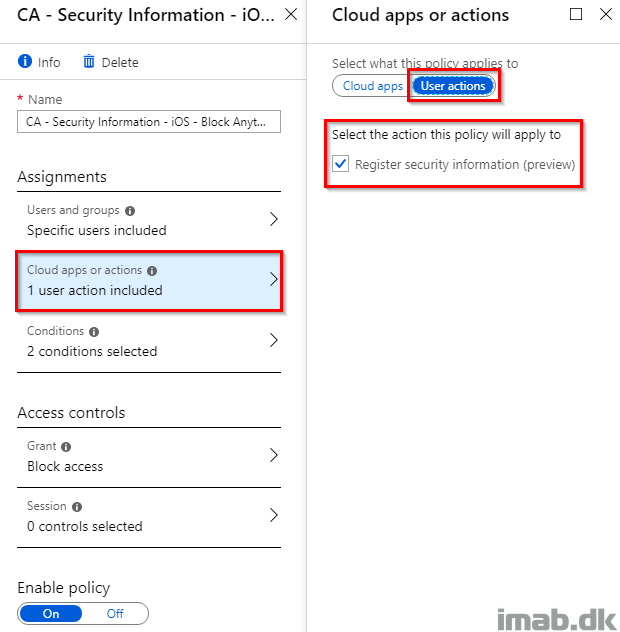
- In the Conditions section, I limit the policy to iOS only (remember the explained scenario in the introduction?)
- This can obviously be done to suit any specific needs, but the case here is that I never want anyone to be able to register security information from iOS devices unless it’s done from corporate network.
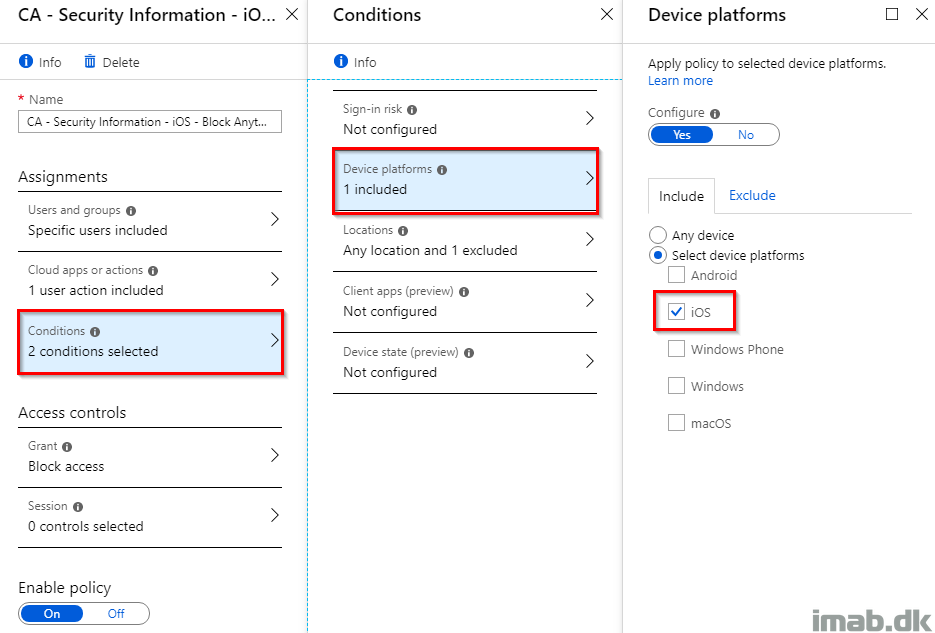
- Also in the Conditions section, configure this to target Any location as shown below:
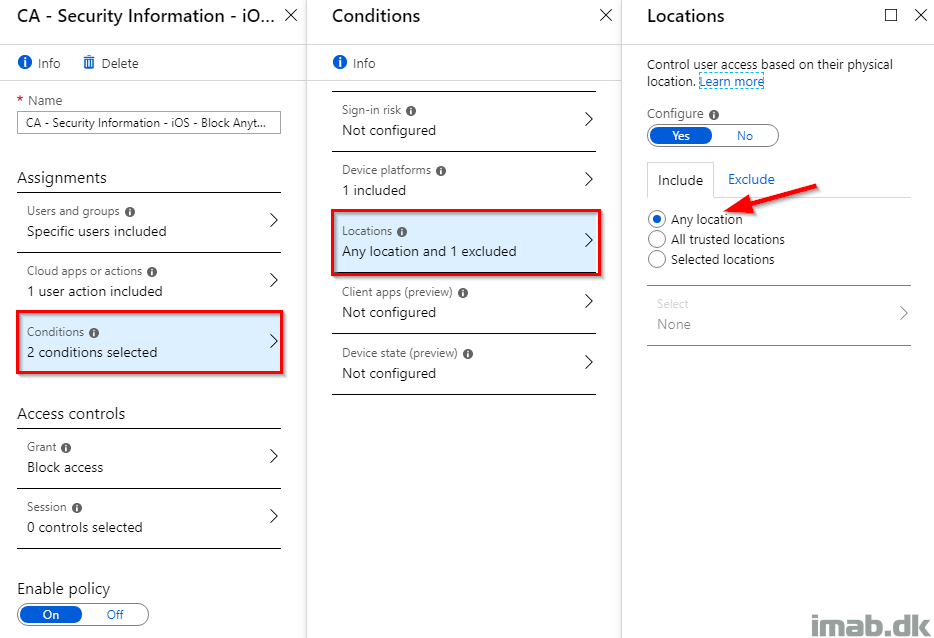
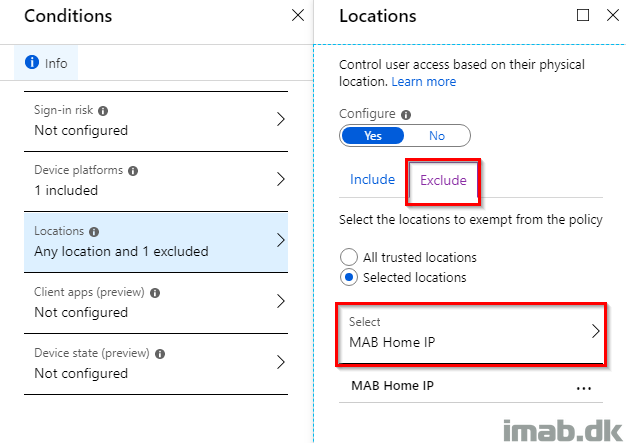
- And remember to exclude the trusted location(s). In this scenario, I want to be able to register and change my security information from home (this is a named location also found in Conditional Access)
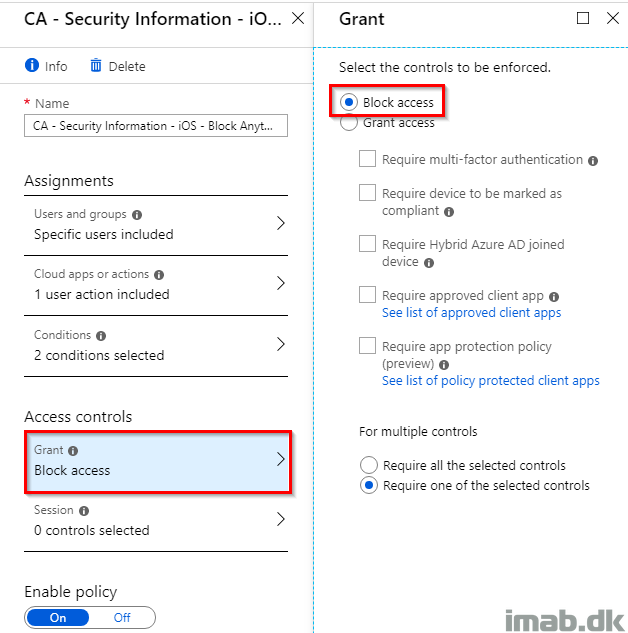
- Finally, select to Block access and enable the policy once ready:
End-user Experience
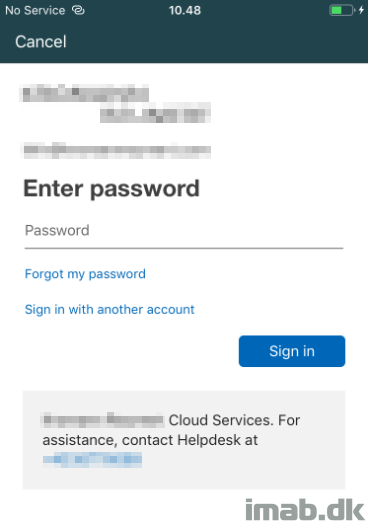
- Now, enrolling a device prompts for credentials as usual:
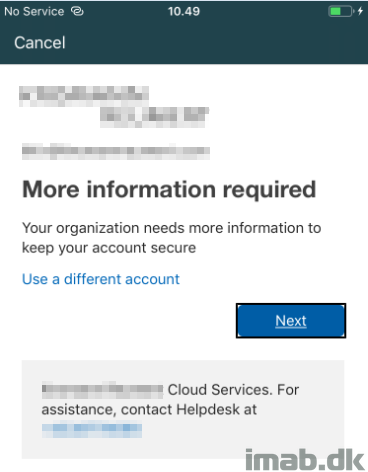
- Seeing we require MFA in the process and the user currently doesn’t have any security information registered, the user is also prompted to provide additional information:
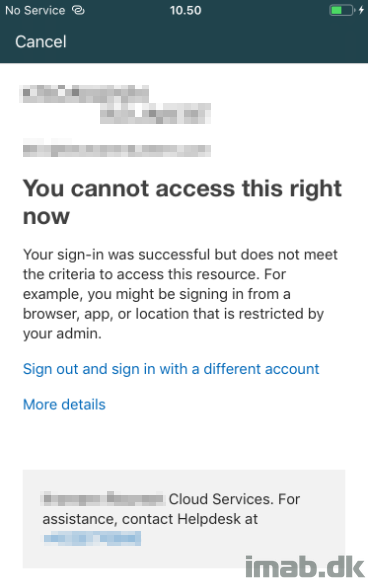
- Now, this is not allowed unless coming from my trusted location, so this is prevented as expected:
- Instead bringing the device online from my trusted location and running through the enrollment process once again, I’m now allowed to register my security information. Awesome!