Introduction
Just a quick blog post, on how to detect and remediate the Lenovo Vantage Vulnerabilities disclosed this week.
- More information here: Lenovo Vantage Component Vulnerabilities – Lenovo Support CY
- And here: Lenovo laptops vulnerable to bug allowing admin privileges (bleepingcomputer.com)
This surely has been an eventful week for most IT professionals, beginning with the #Log4j nightmare, and now ending with some Lenovo Vantage fun. Joking aside, this fix is pretty easy, but making sure and proving the vulnerability has been mitigated throughout your environment, might be something else. This post explains how I did.
PowerShell
This solution consists of 2 PowerShell scripts, intended to be used with Endpoint Analytics Proactive Remediations in Microsoft Endpoint Manager.
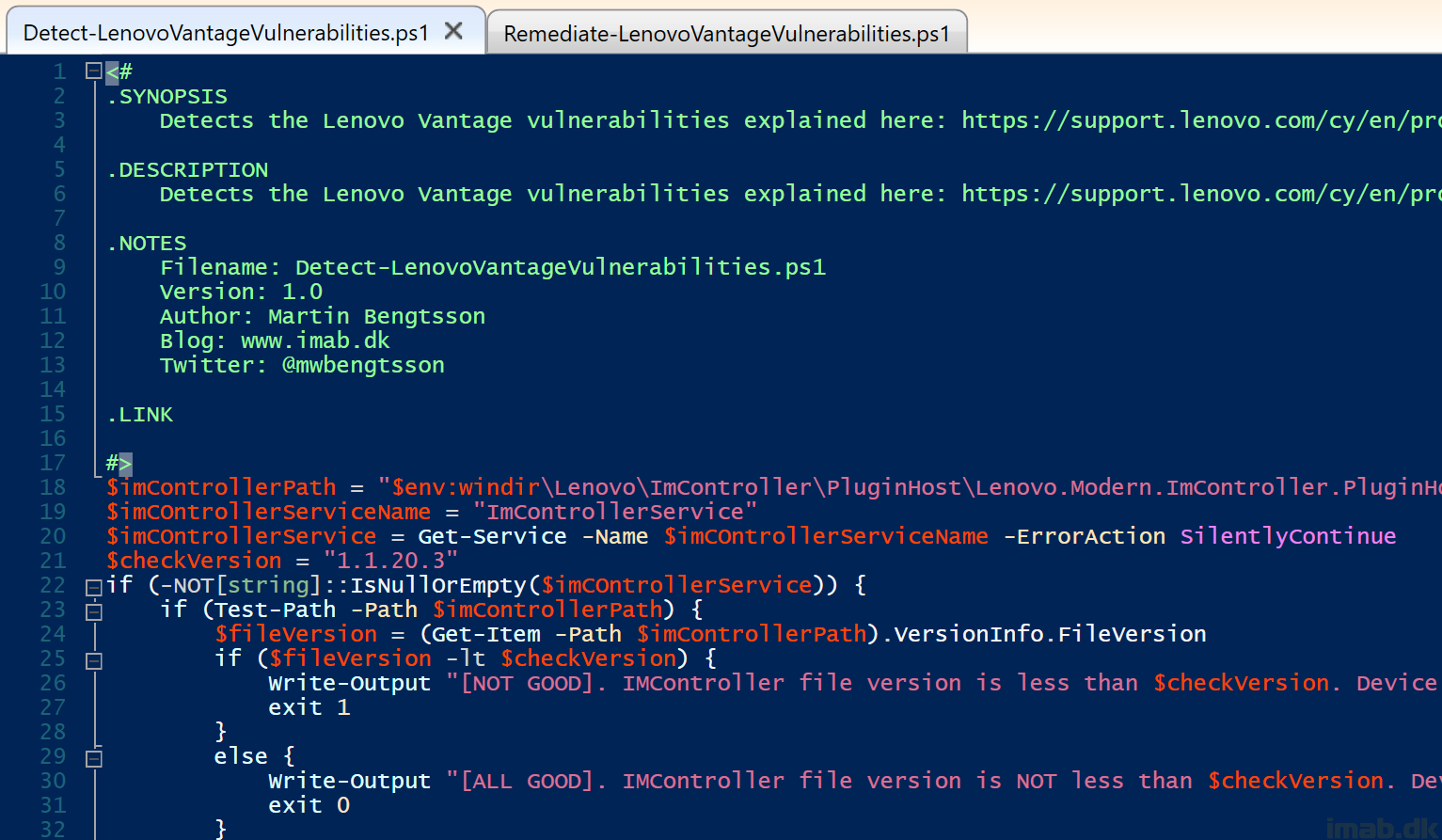
Detect-LenovoVantageVulnerabilities.ps1
Find the Detect-LenovoVantageVulnerabilities.ps1 script on my GitHub page: PowerShell/Detect-LenovoVantageVulnerabilities.ps1 at master · imabdk/PowerShell (github.com)
This script does following in headlines:
- Detect if the Lenovo Vantage service is present
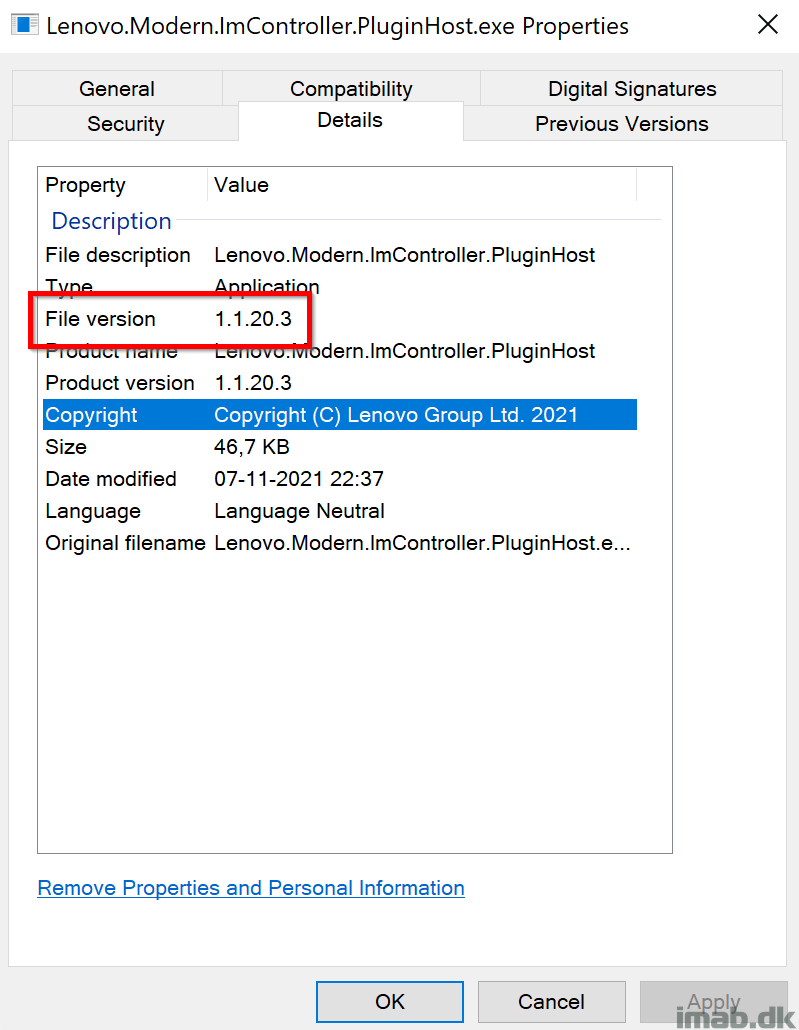
- If the service is present, the script looks for a certain .exe file
- The script then checks the fileversion, and if less than a specified value, the script will return and exit with 0
- If the service is present, the script looks for a certain .exe file
Remediate-LenovoVantageVulnerabilities.ps1
Find the Remediate-LenovoVantageVulnerabilities.ps1 on my GitHub page: PowerShell/Remediate-LenovoVantageVulnerabilities.ps1 at master · imabdk/PowerShell (github.com)
This script does following in headlines:
- Detects if the Lenovo Vantage service is present
- If present, it will restart the service and Write-Output
Microsoft Endpoint Manager
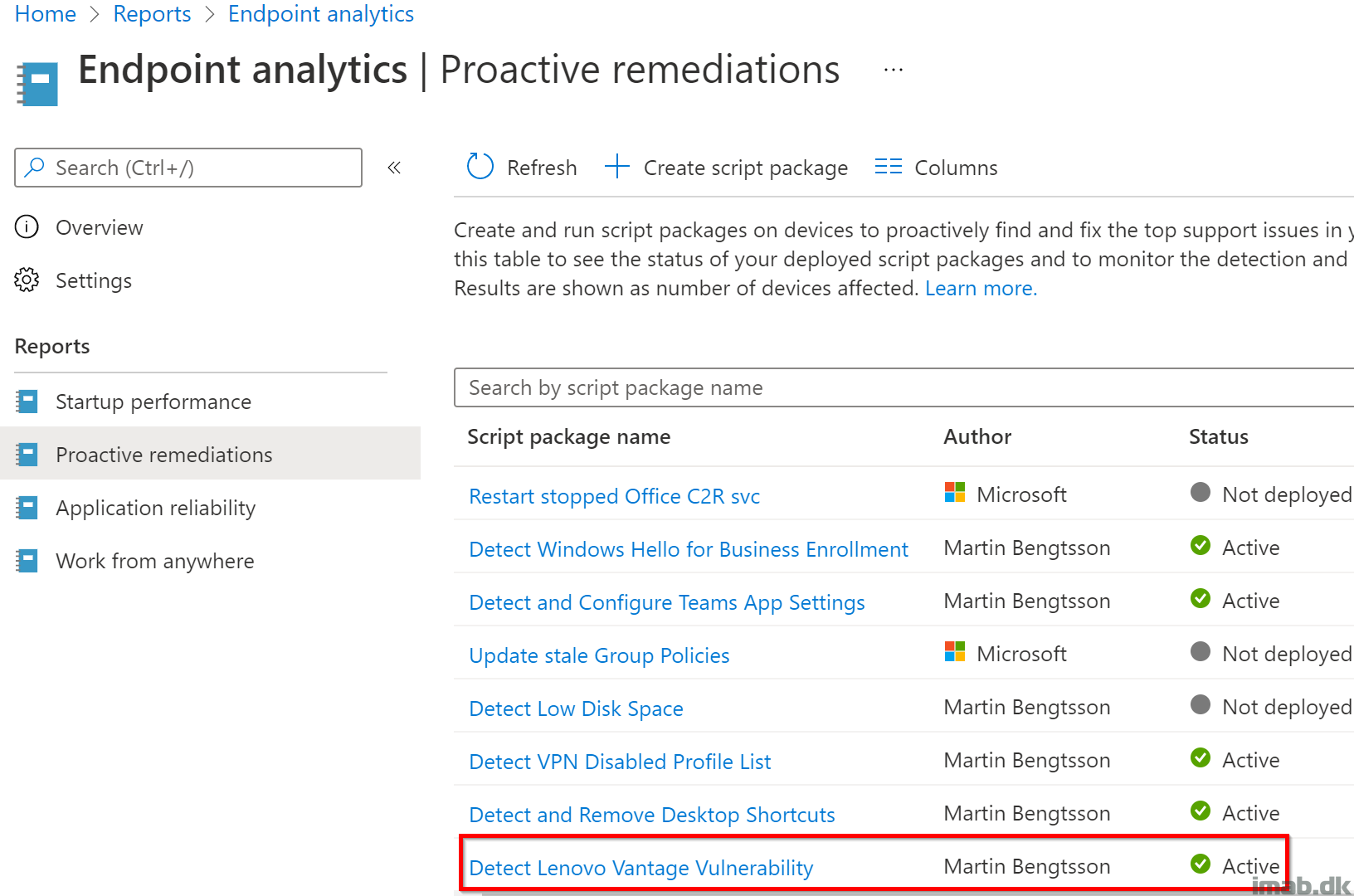
Head into the Microsoft Endpoint Manager admin center: https://endpoint.microsoft.com and locate the Proactive Remediations feature within the Reports -> Endpoint Analytics blade:
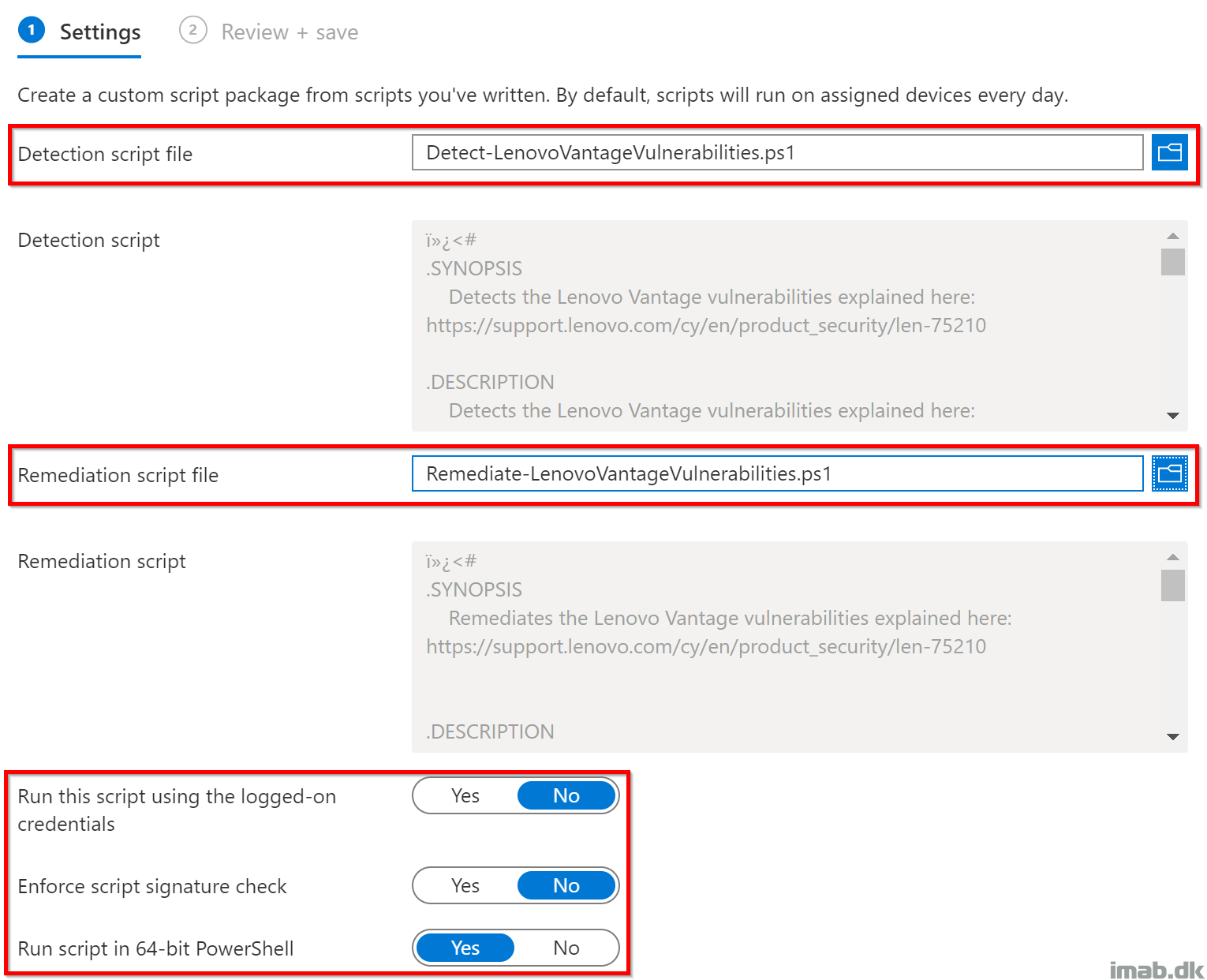
Settings
Use the 2 scripts explained above as illustrated below:
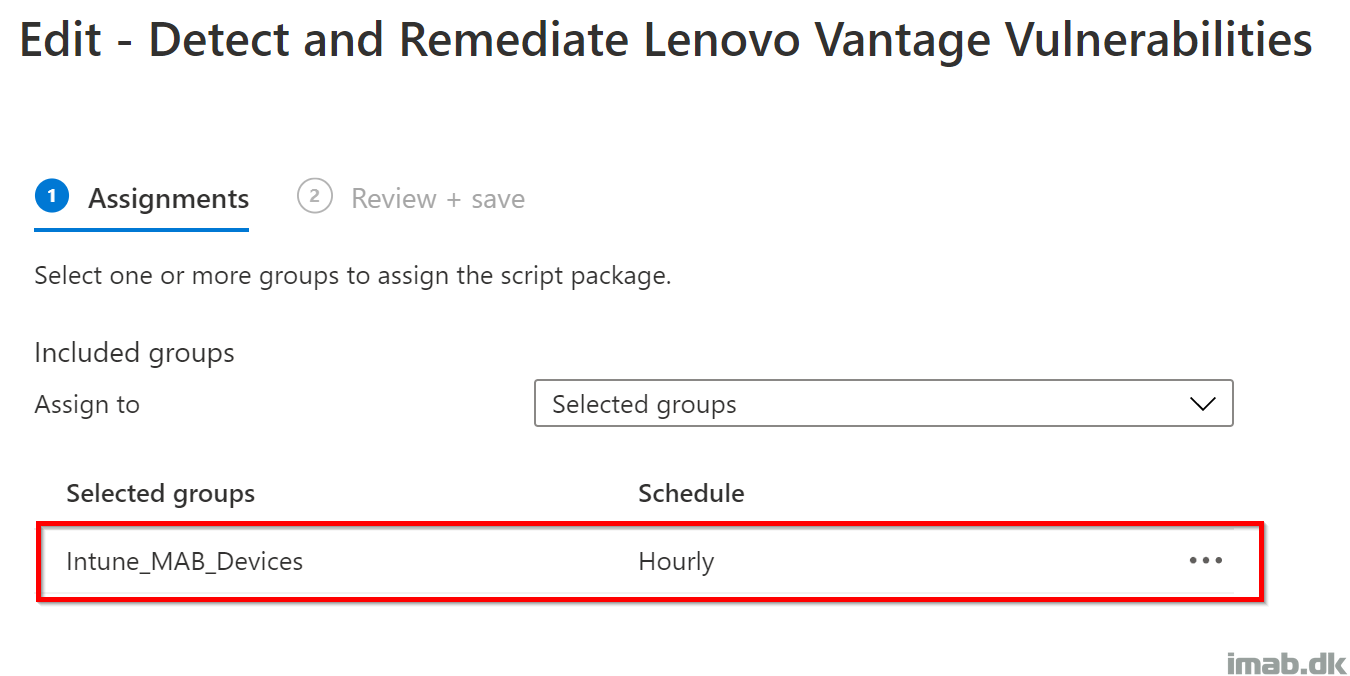
Assignments
Assign the scripts to run on a group consisting of devices or users. In this scenario, I’m running the scripts Hourly on a group containing my own devices:
In Action
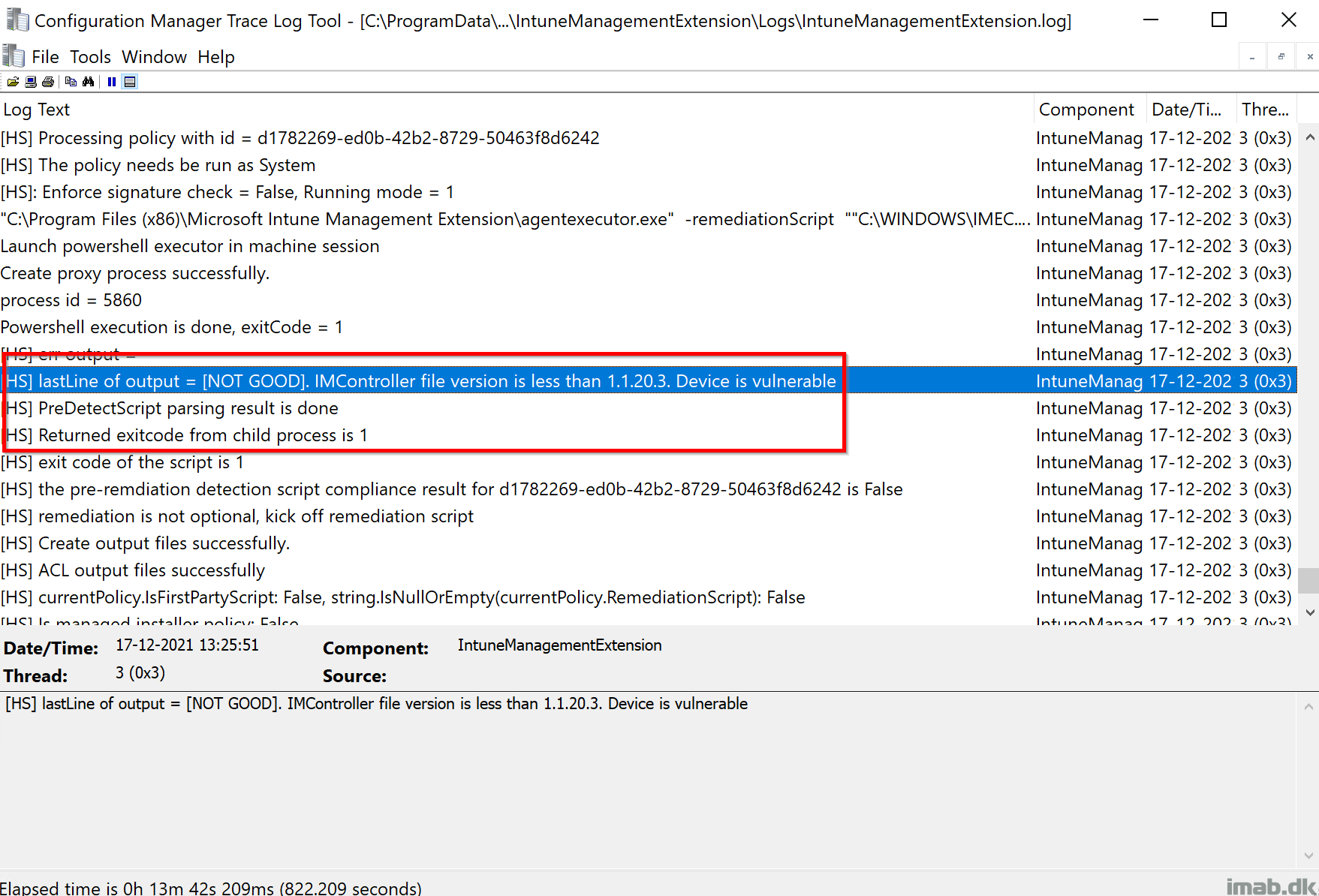
Taking a closer look on IntuneManagementExtension.log (C:\ProgramData\Microsoft\IntuneManagementExtension\Logs) you will see if the detection script finds the device to be vulnerable or not:
- [NOT GOOD]. IMController file version is less than 1.1.20.3. Device is vulnerable
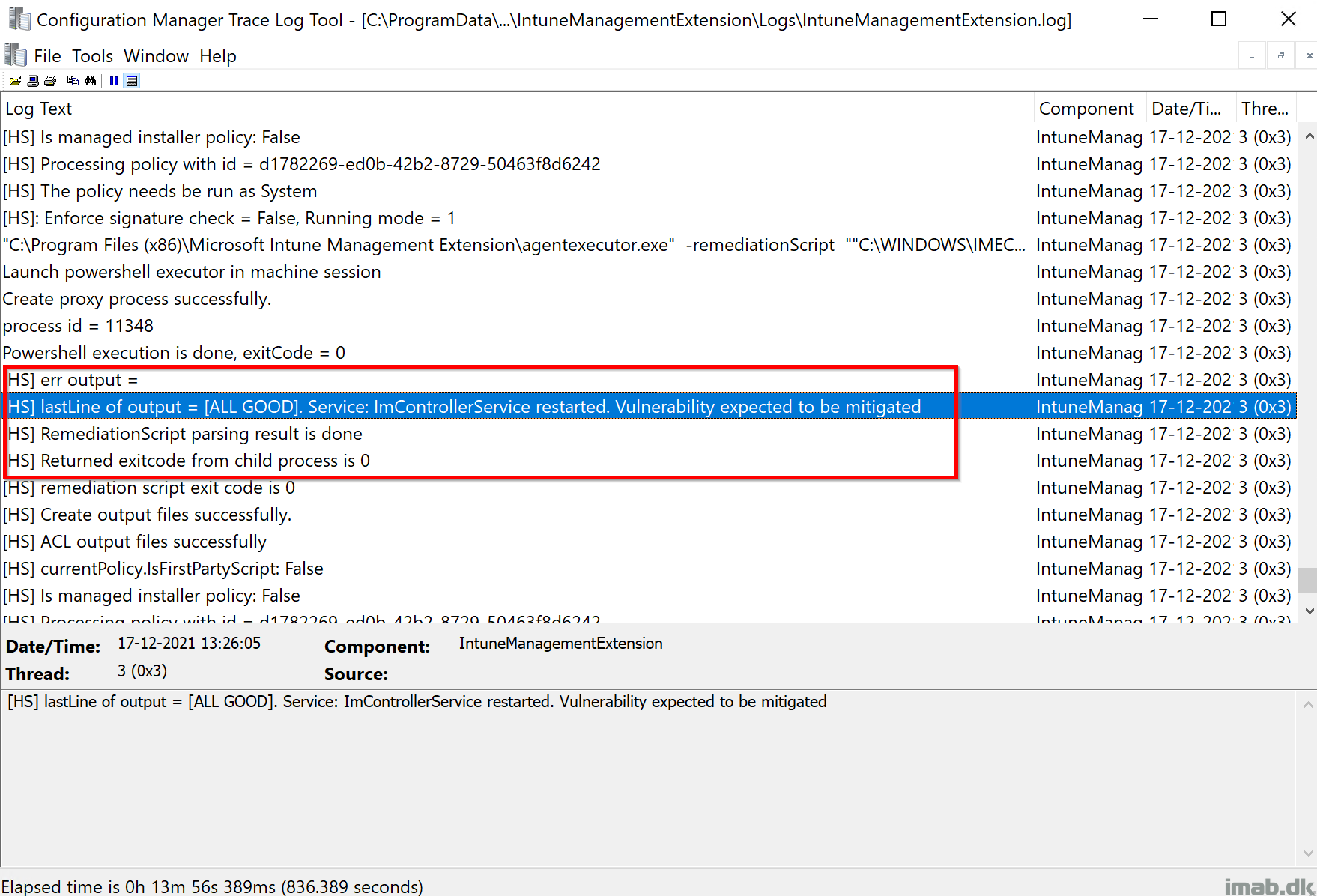
And when the remediation script kicks off, the same log will tell you if the service was restarted or not:
- [ALL GOOD]. Service: ImControllerService restarted. Vulnerability expected to be mitigated
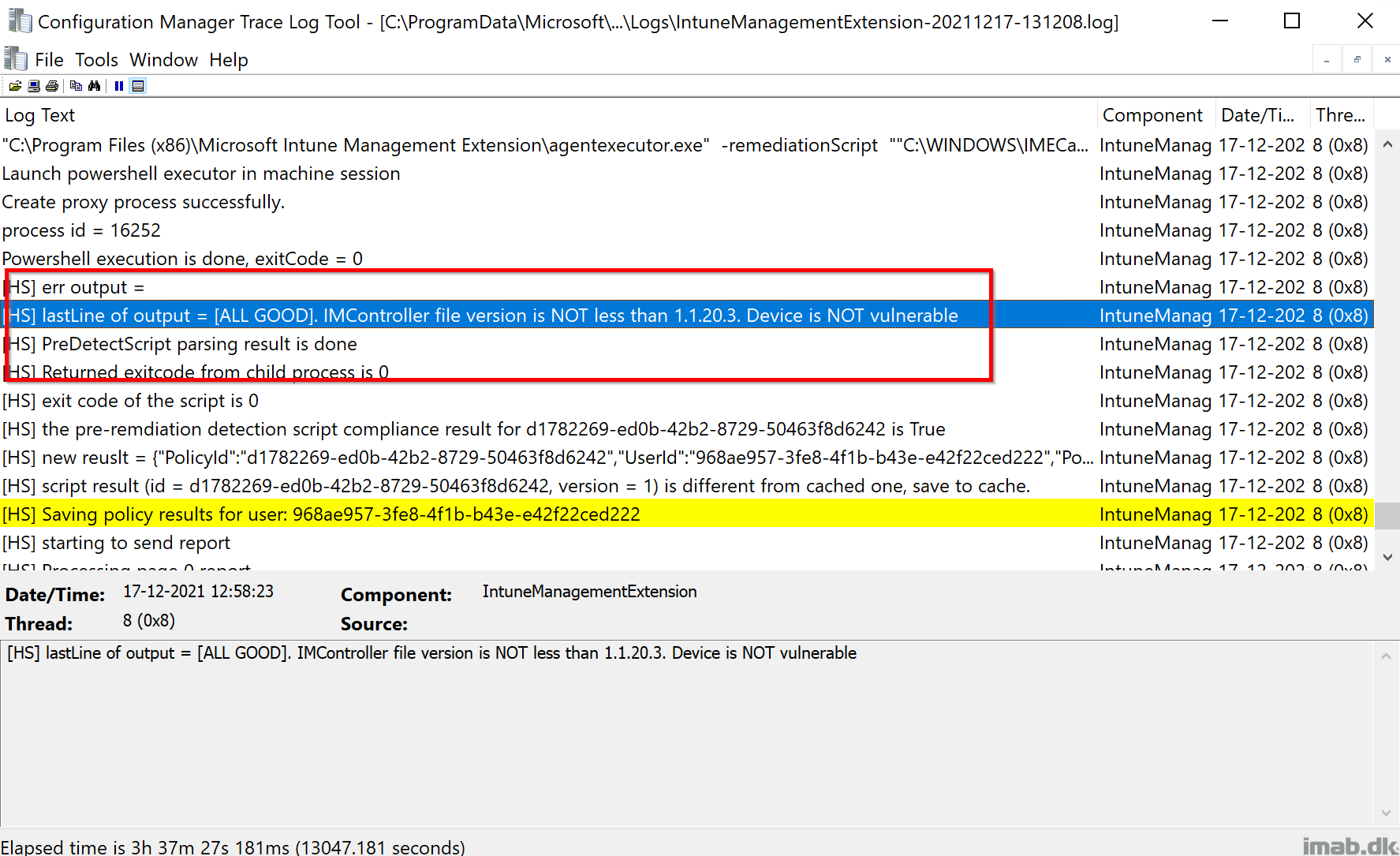
If the vulnerabilities never existed or is not mitigated, the script will return following to the log file:
- [ALL GOOD]. IMController file version is NOT less than 1.1.20.3. Device is NOT vulnerable
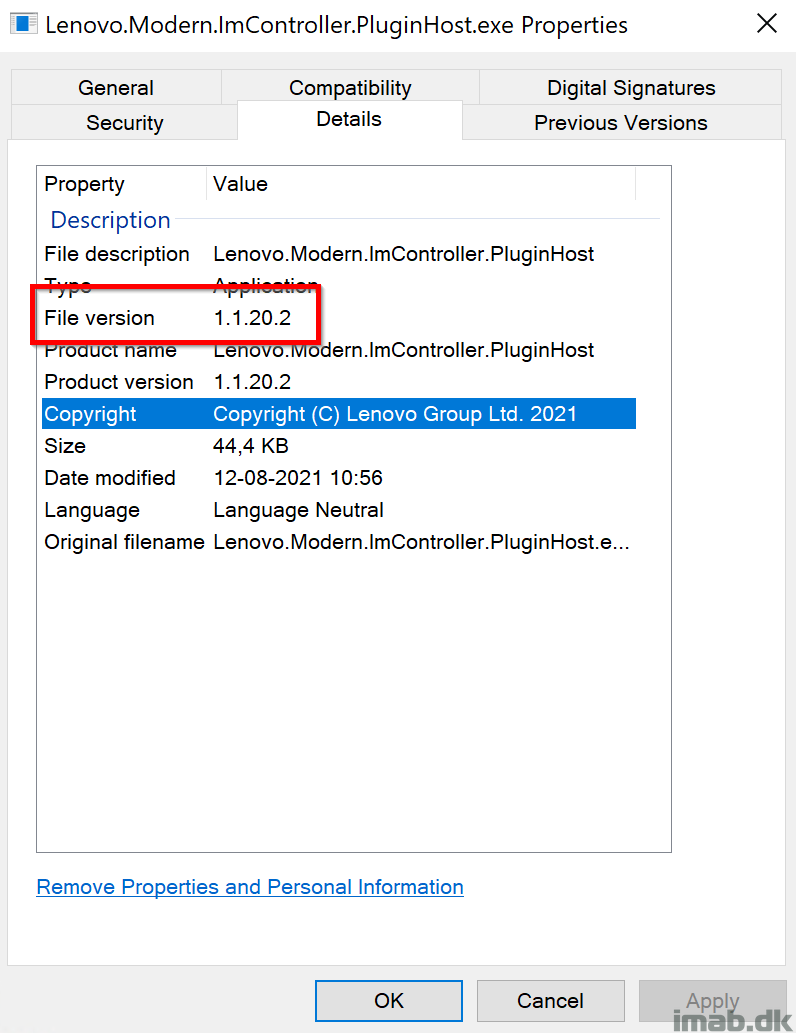
Before and After
ENJOY 🙂