Introduction
I typically blog about topics, that I’m currently addressing in my own daily work, and this time is no different.
Covid-19 surely has a saying on this particular topic as well, and empowering our users to do more, working securely from home and remote, is key.
In that regard, we needed a simple VPN solution for our iOS devices, and while making my way through the setup and configuration of Microsoft Tunnel Gateway, I decided it was worth blogging as well.
This post will walk you through everything you need know, in order to successfully setup Microsoft Tunnel Gateway as a proof of concept.
This includes:
- Creating the VM(s) in Azure
- Assigning static public IP
- Hardening of the inbound traffic
- Configuring public DNS record
- SSH’ing to the Linux server
- Installing Docker on Linux
- Setting up configuration in Microsoft Endpoint Manager
- Installing Microsoft Tunnel on Linux
- Copying down TLS certificate to Linux
- Deploying VPN profile in Microsoft Endpoint Manager
- Verifying connection to VPN on iOS is successful
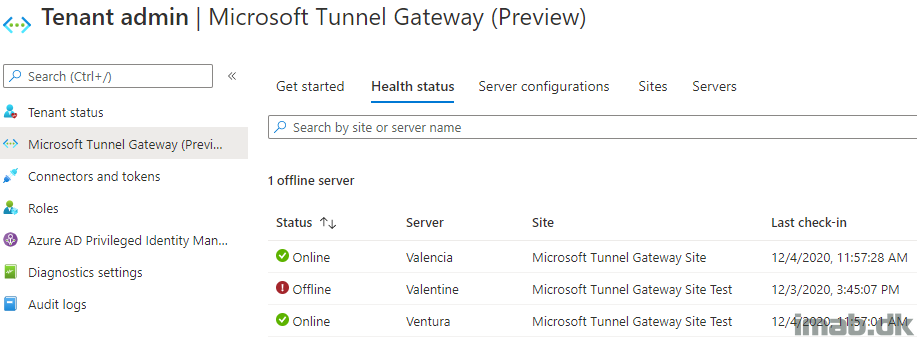
Linux VM in Azure
I won’t go into super details on how the VM(s) in Azure are created, but instead just highlight the important bits and pieces of the setup.
I’m creating the below VM, as I write this post. This is also the VM, which will be proving working with the Microsoft Tunnel Gateway configuration, when you are done reading this post.
A lot of below options will wary depending on your infrastructure. The important parts are to select a supported OS and proper inbound ports. I’m using Ubuntu 18.0.4 and opening port 443 and 22.
- Find details on supported Linux distributions here: Use the Microsoft Tunnel VPN solution for Microsoft Intune – Azure | Microsoft Docs
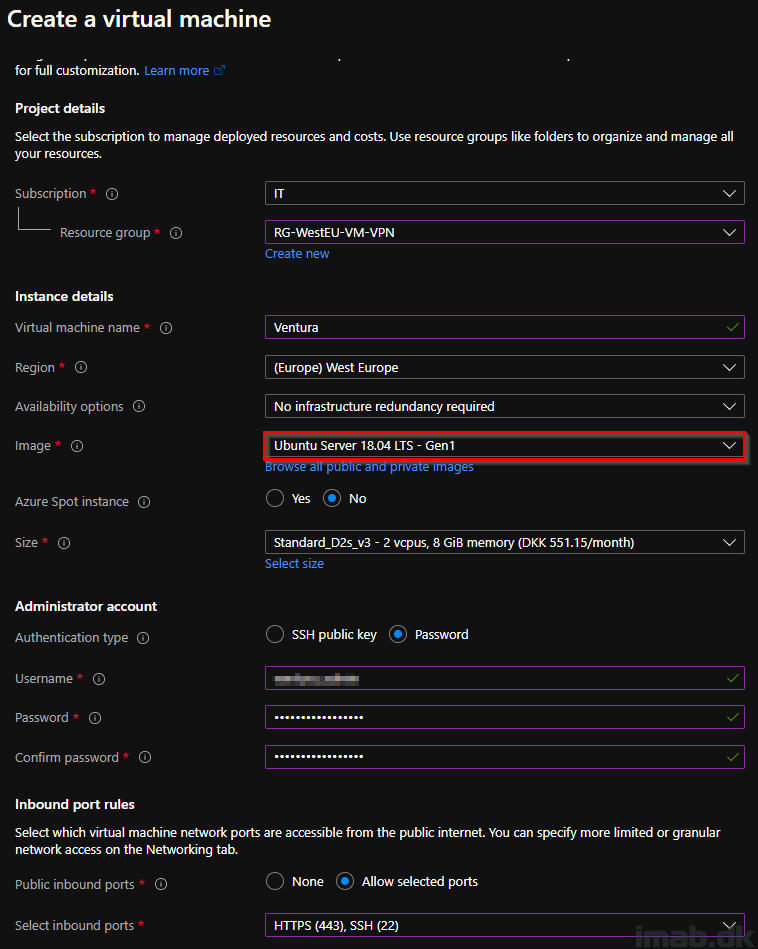
Public IP
Next important options in configuring the Linux VM, is the Networking tab. In this scenario, I create a public IP address in the process, and verify that the required inbound ports are selected.
- NOTE: This is something that will be unique for your environment. It will depend on a lot of factors, like how things in Azure communicates with your on-premises infrastructure etc. If you have a networking team, you should consult with them.
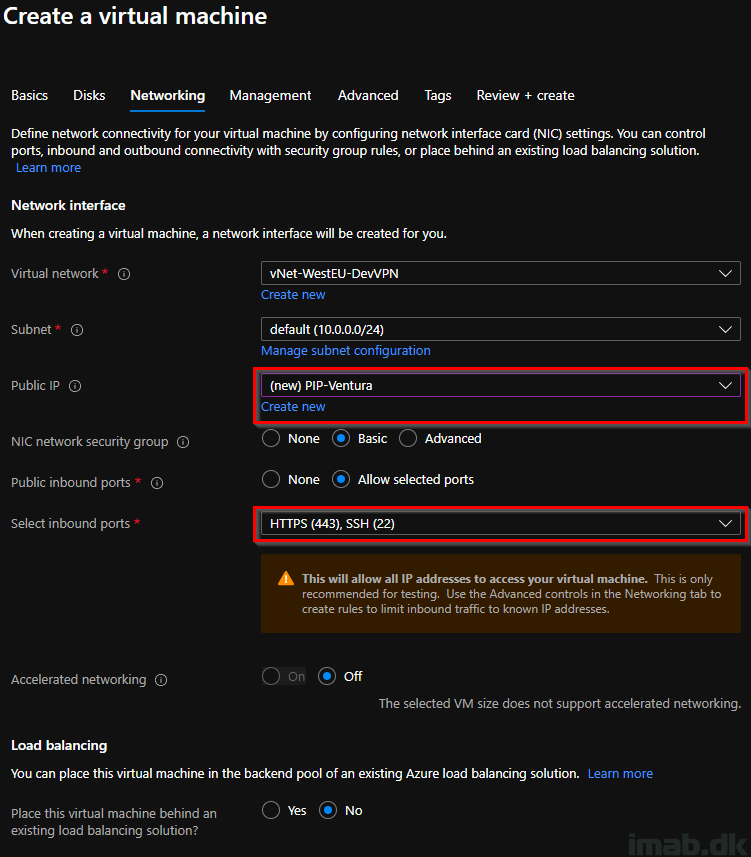
And accepting your choices and creating the Linux VM, will give you a Deployment is in progress screen like shown below:
SSH hardening
SSH is wide open to the Internet at this stage of the Linux VM. What I like to do here, is to lock it down to my own public IP address, making sure that only devices coming from my end, can SSH into the Linux VM.
NOTE: Again, depending on how your network is done, the Linux VM might be reachable from the inside of your network, and opening SSH to the Internet might not be needed at all. Consult with your networking team.

Public DNS
My Linux VM is assigned a static public IP address, and this can be found when browsing the VM in Azure:

This public IP address is used with my DNS provider, to create an A record: tunnelgateway.imab.dk
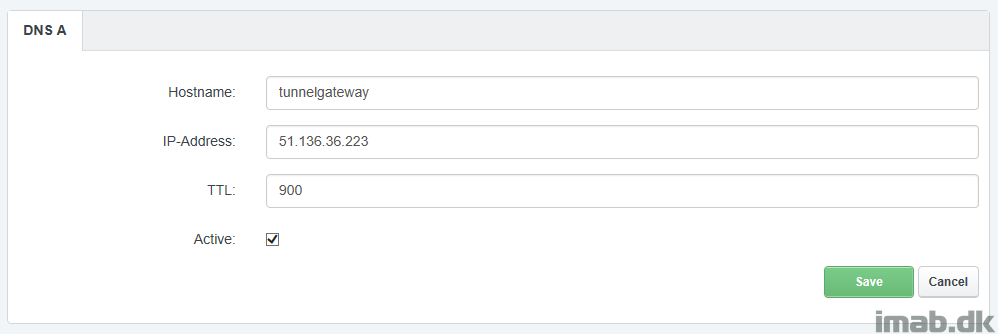
SSH to the Linux VM
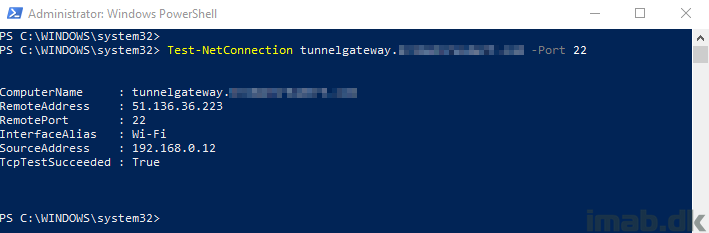
Before attempting to SSH into the Linux VM, I’m testing the newly created A record as well as whether port 22 is open.
The result below is what I wanted to see: My host name is resolving to the public IP of the Linux VM and port 22 is open.
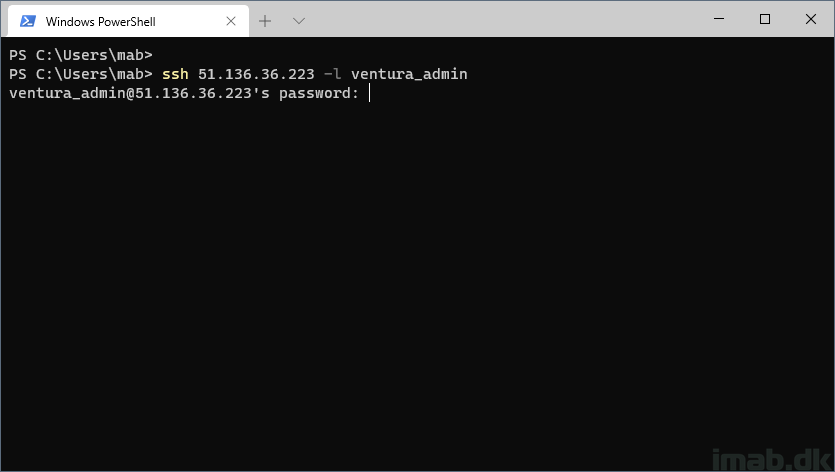
I’m using Windows Terminal as my SSH client. PuttY or whatever you might prefer, will do it as well.
As illustrated in the image of the creation of my VM, I specified an admin user as well as a password.
I’m using this user and password to connect via SSH to the Linux VM in Azure:
ssh 51.136.36.223 -l ventura_admin
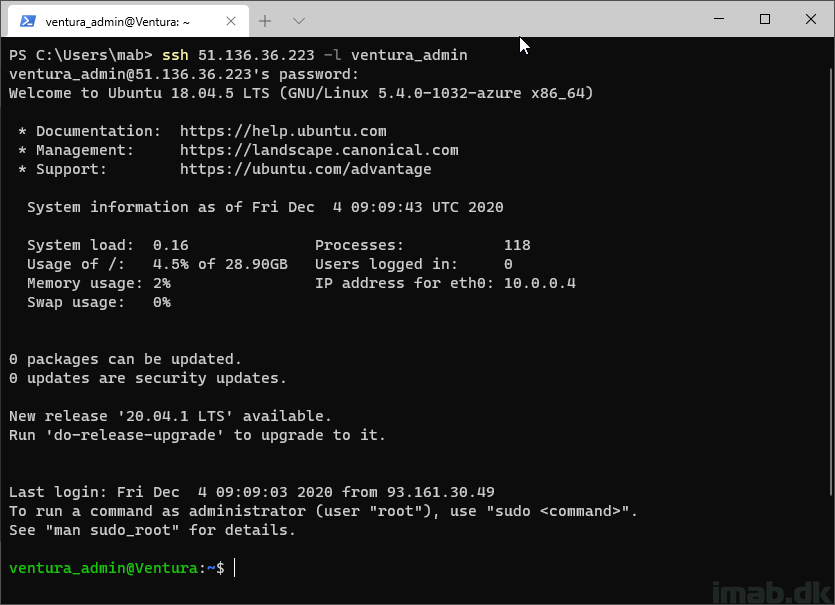
When successfully connected, Windows Terminal will have an appearance similar to below illustration:
Install Docker
The installation of Docker is straightforward and completed in a few steps.
Either follow my outlined steps below, or use the official documentation found here: Install Docker Engine on Ubuntu | Docker Documentation
Step 1
Update the apt package index and install packages to allow apt to use a repository over HTTPS:
-
sudo apt-get update
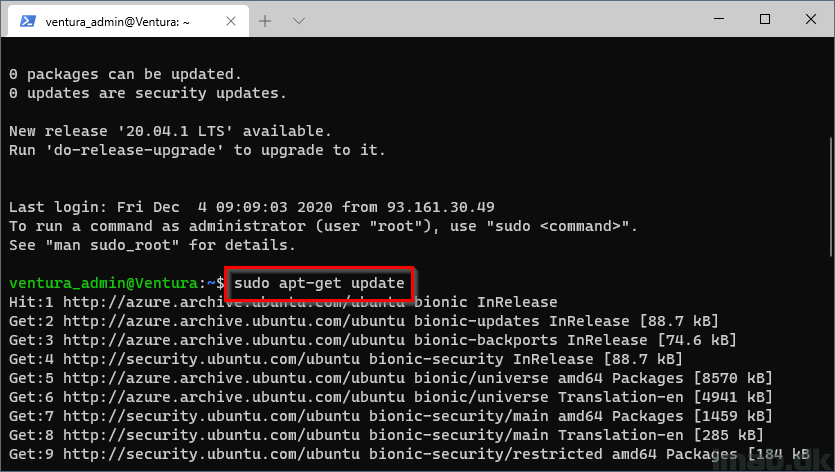
Step 2
-
sudo apt-get install \ apt-transport-https \ ca-certificates \ curl \ gnupg-agent \ software-properties-common
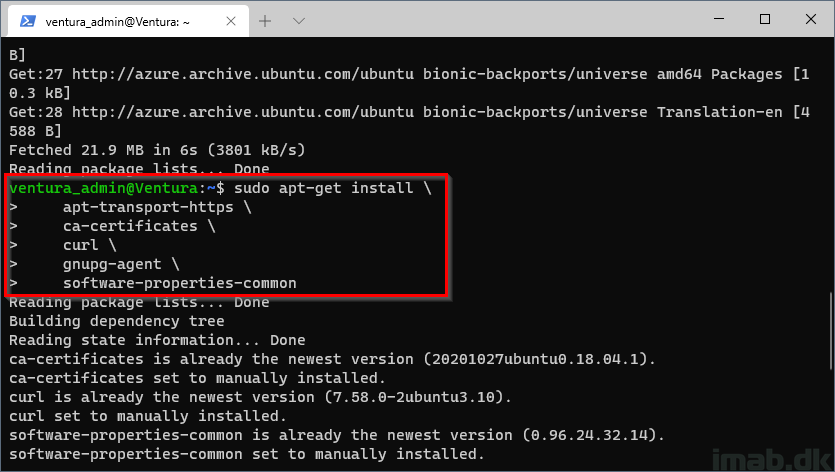
Step 3
Add Docker’s official GPG key:
-
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo apt-key add -
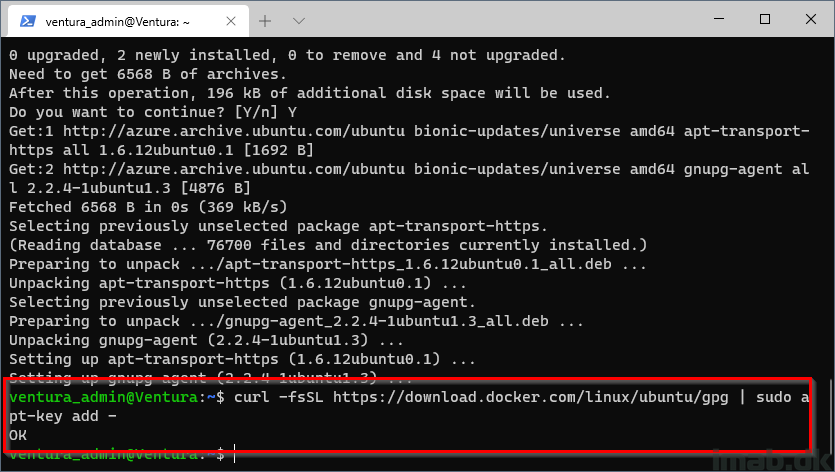
Step 4
Use the following command to set up the stable repository:
-
sudo add-apt-repository \ "deb [arch=amd64] https://download.docker.com/linux/ubuntu \ $(lsb_release -cs) \ stable"
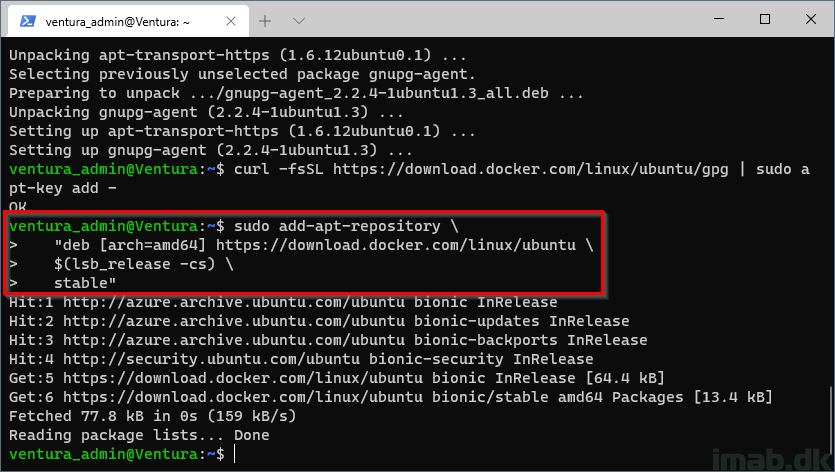
Step 5
Update the apt package index, and install the latest version of Docker Engine and containerd::
-
sudo apt-get update sudo apt-get install docker-ce docker-ce-cli containerd.io
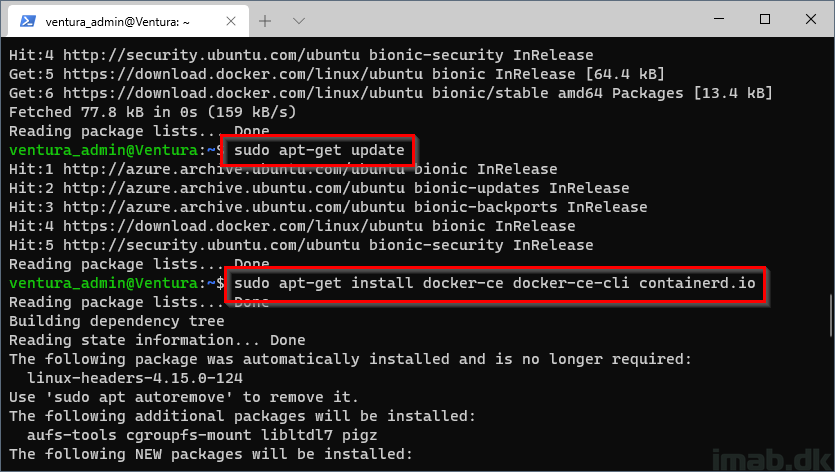
Final step
Verify that Docker Engine is installed correctly by running the hello-world image:
-
sudo docker run hello-world
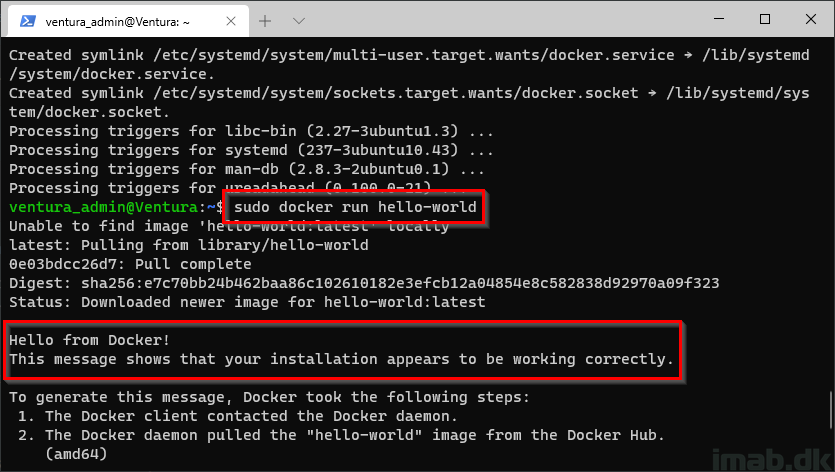
Configuration in Microsoft Intune
Before moving on to the actual installation of the Microsoft Tunnel Gateway, it’s important to complete the configuration in Microsoft Intune first. This is because the installation itself, is pulling the configuration from Microsoft Intune during the installation.
The configuration in Microsoft Intune is close to self-explanatory, and does not require much explaining in details.
I will give you screenshot of my configuration, and explain where needed. I think seeing real screenshots, paired with this guide, where the Linux VM ends up in the shown configuration, is sufficient for the understanding.
- Start off by creating a new Server configuration. This is done in Microsoft Endpoint Manager admin center, in Tenant administration and Microsoft Tunnel Gateway (Preview) as shown below:
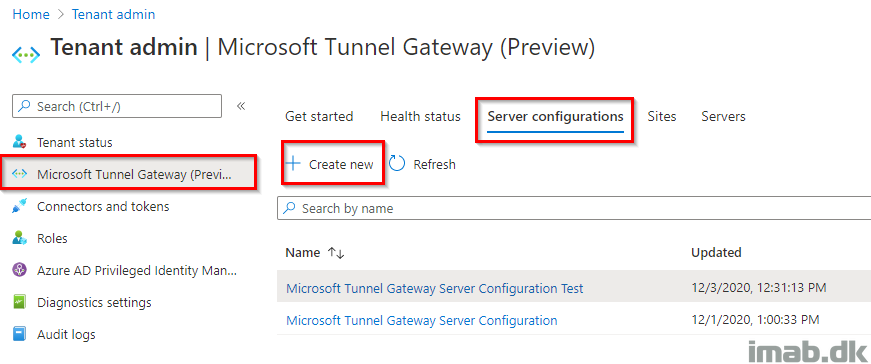
Again, this cannot be done properly without involving your networking team or at least knowing ups and downs in your network and infrastructure.
- IP address range: Which IP addresses should be assigned to your devices connected to Microsoft Tunnel
- DNS servers: Which DNS servers will handle DNS request from your devices connected to Microsoft Tunnel
- DNS suffix: What domain will be provided to your devices connected to Microsoft Tunnel
- Split tunneling: Which IP ranges should go via the Microsoft Tunnel, and which should not
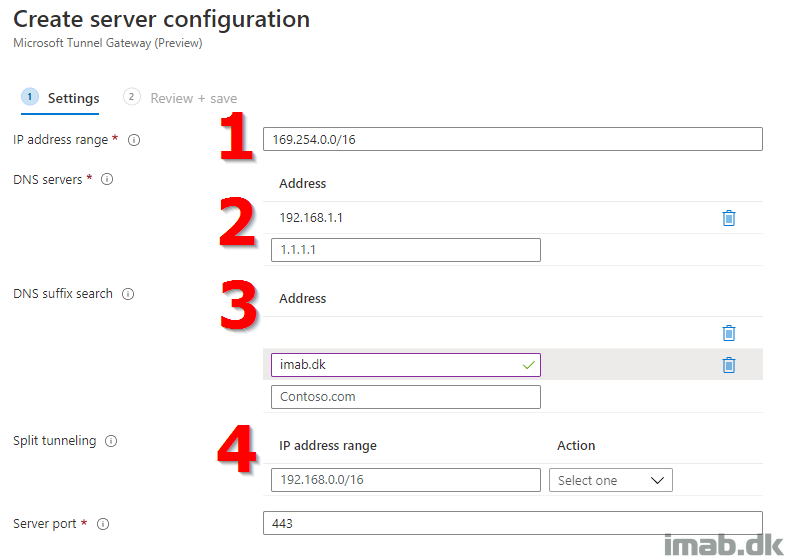
- Next, create a new Site
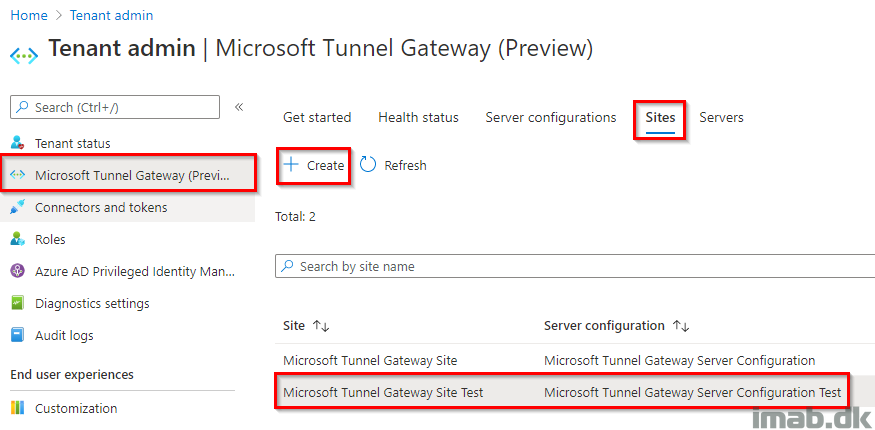
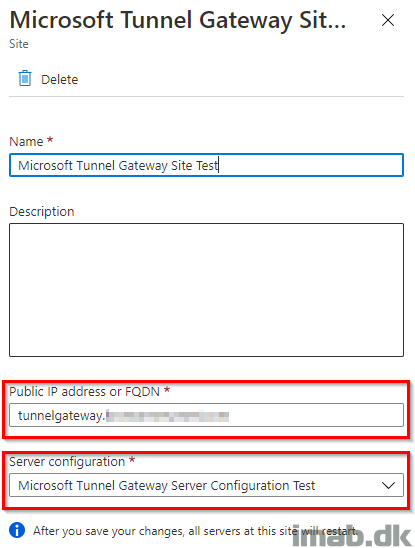
The site is associated with your server configuration. The site also determines which public IP address or FQDN that your devices are connecting to.
The FQDN is going to match the A record you created in your public DNS earlier (and also match the TLS certificate you are going to use later in the setup).
Installing Microsoft Tunnel Gateway
With the configuration in Microsoft Intune in place, we can move on with the installation of the Microsoft Tunnel Gateway.
Either follow my outlined steps below, or use the public documentation found here: Install and configure the Microsoft Tunnel VPN solution for Microsoft Intune – Azure | Microsoft Docs
Step 1
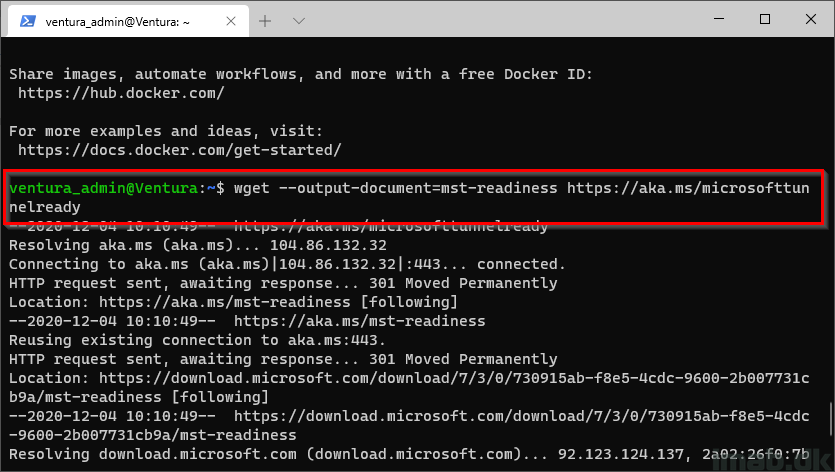
Download the readiness script from Microsoft:
-
wget --output-document=mst-readiness https://aka.ms/microsofttunnelready
Step 2
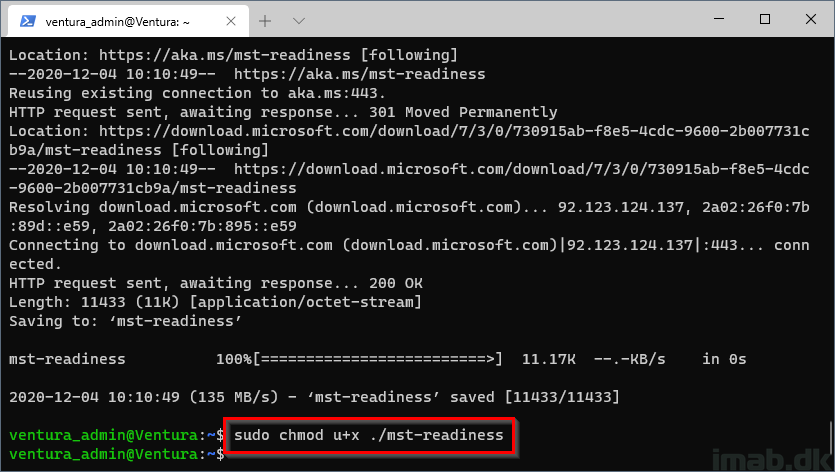
Allow the readiness script to be run:
-
sudo chmod u+x ./mst-readiness
Step 3
Run the readiness script:
-
sudo ./mst-readiness network
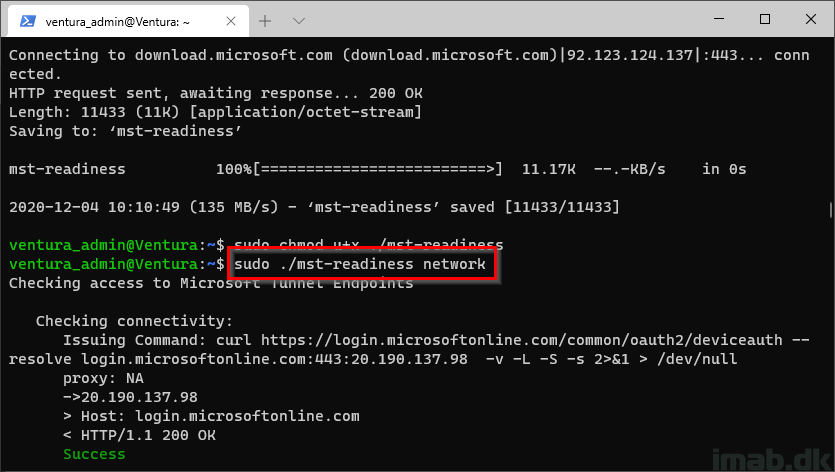
Step 4
Download the Microsoft Tunnel setup script:
-
wget --output-document=mstunnel-setup https://aka.ms/microsofttunneldownload
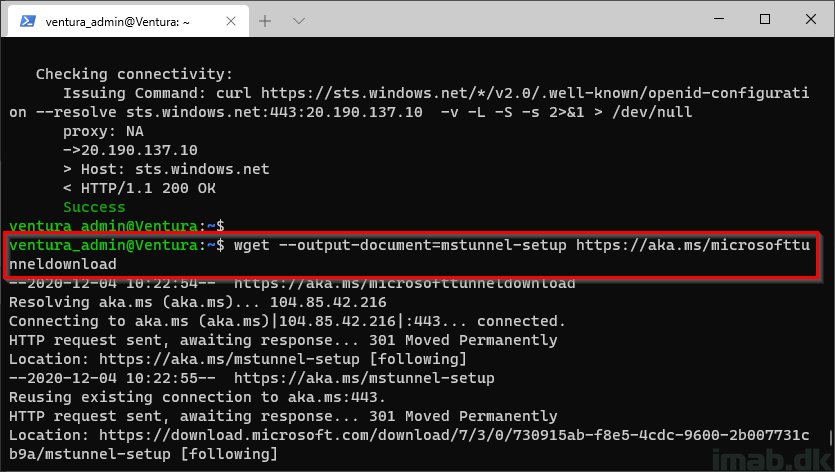
Step 5
Allow the Microsoft Tunnel setup script to be run:
-
sudo chmod u+x ./mstunnel-setup
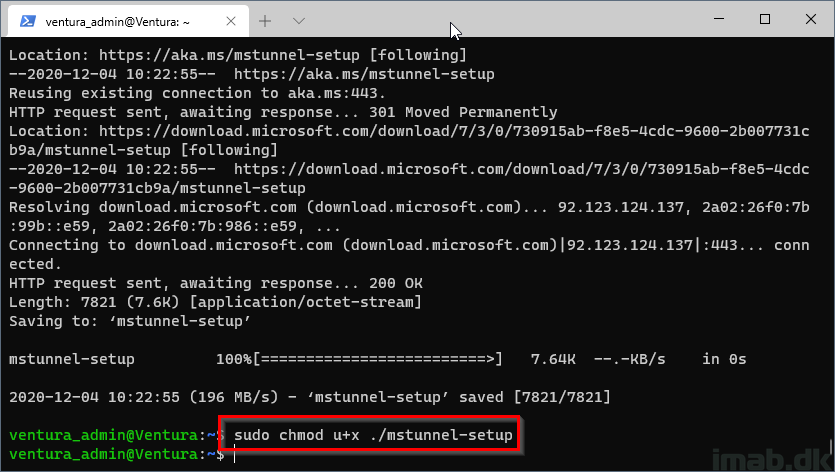
Step 6
Run the Microsoft Tunnel setup script:
-
sudo ./mstunnel-setup
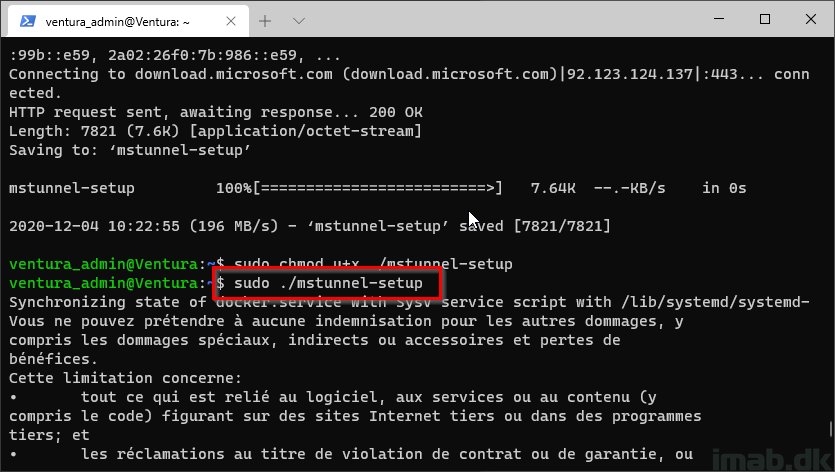
Step 7
Accept the Microsoft license terms (EULA):
Step 8
These following steps are particular interesting, as this is where you need to copy down your TLS certificate used for the FQDN specified in the configuration in Microsoft Intune.
- When presented with this dialog, type yes
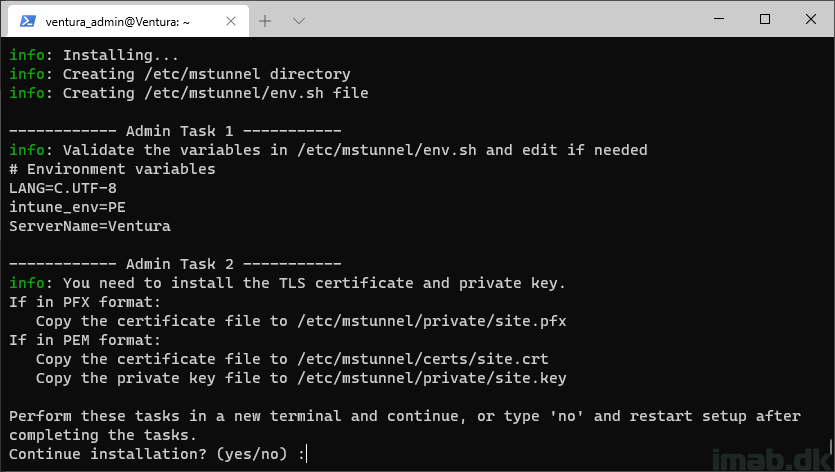
Step 9
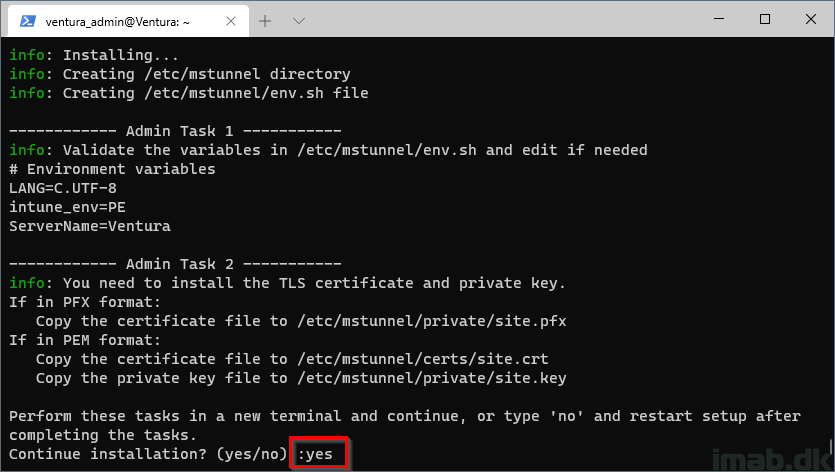
The setup will continue, and this is important, because the folder structure for where the SSL certificate are going. will be created for us in the process.
However, the setup will pause and ask you to install a certificate before continuing.
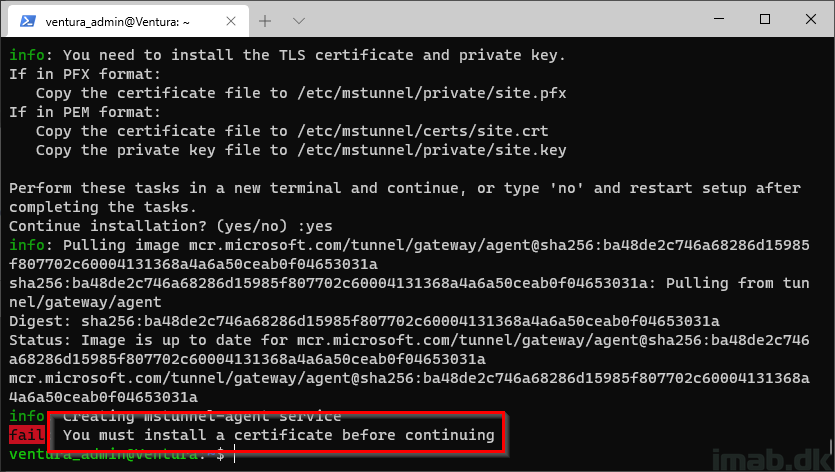
Step 10
What I did here, was to upload my certificate in .pfx format and use wget to download it directly onto the Linux VM.
The official documentation here is somewhat lacking, and has no information on how to do this. I came up with this approach, as the readiness script and installation script is downloaded in same fashion.
NOTE: The certificate.pfx MUST be named site.pfx
-
wget --output-document=site.pfx https://imab.dk/mab/site.pfx
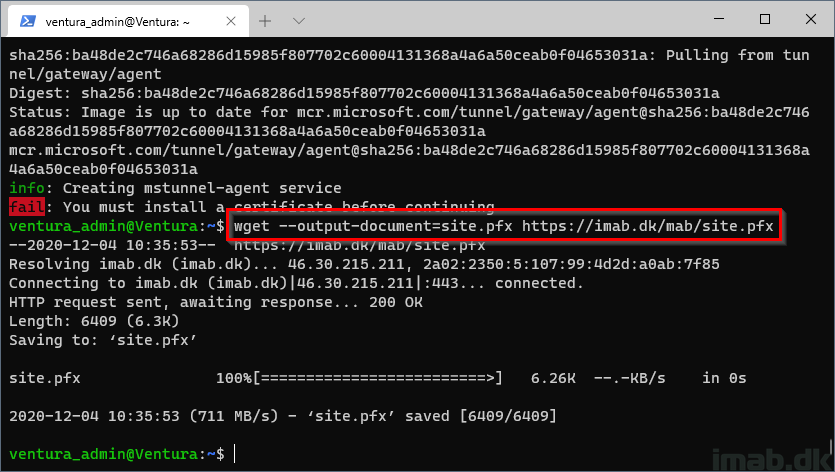
Step 11
Now we need to copy the certificate over to the correct location:
-
sudo cp /home/ventura_admin/site.pfx /etc/mstunnel/private/site.pfx
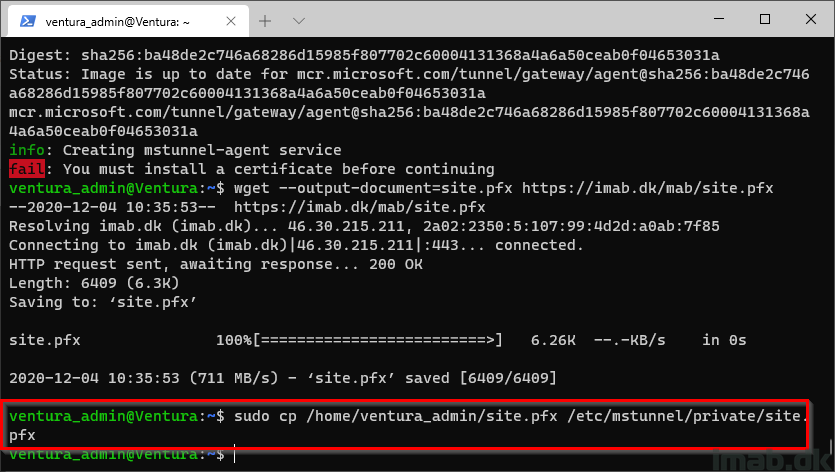
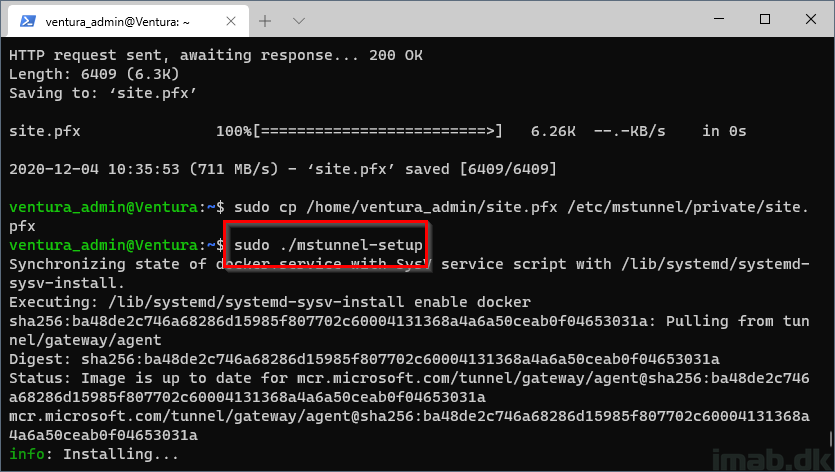
Step 12
Restart and continue the Microsoft Tunnel Gateway installation:
-
sudo ./mstunnel-setup
Step 13
- When prompted again to perform admin tasks, type yes:
Step 14
This time the installation recognizes that we put a TLS certificate in the correct location and prompts us for the import password:
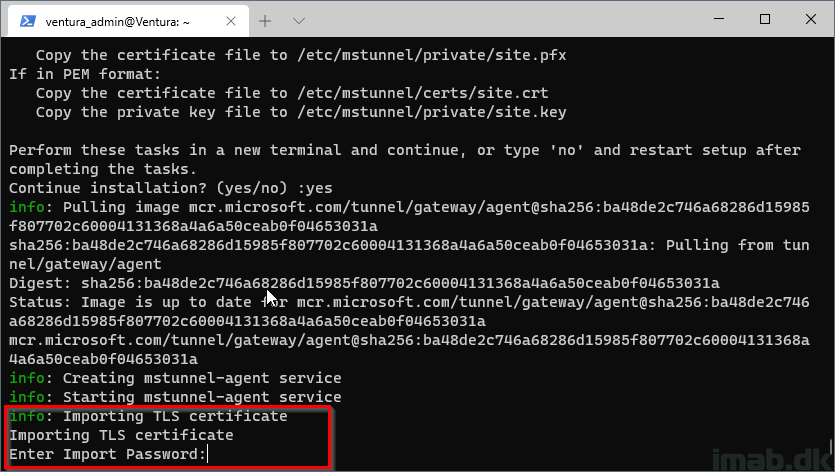
Step 15
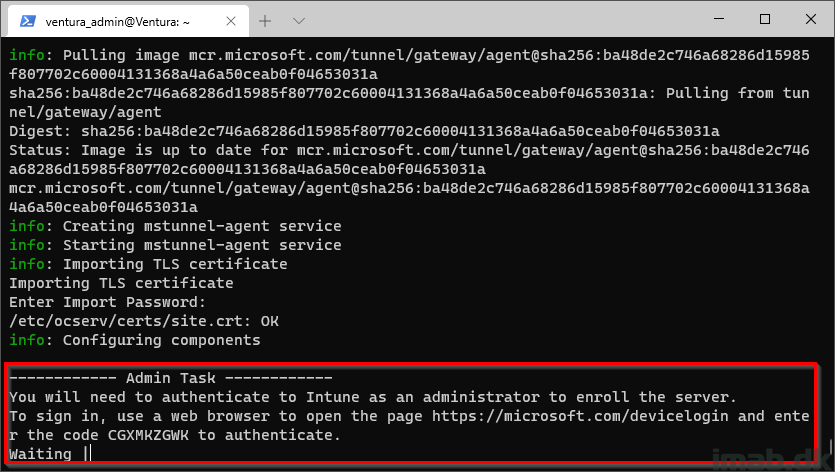
Now it’s time to allow enrollment of the server into your tenant.
- You will be prompted to open a browser and go to: https://microsoft.com/devicelogin and enter the supplied code:
Step 16
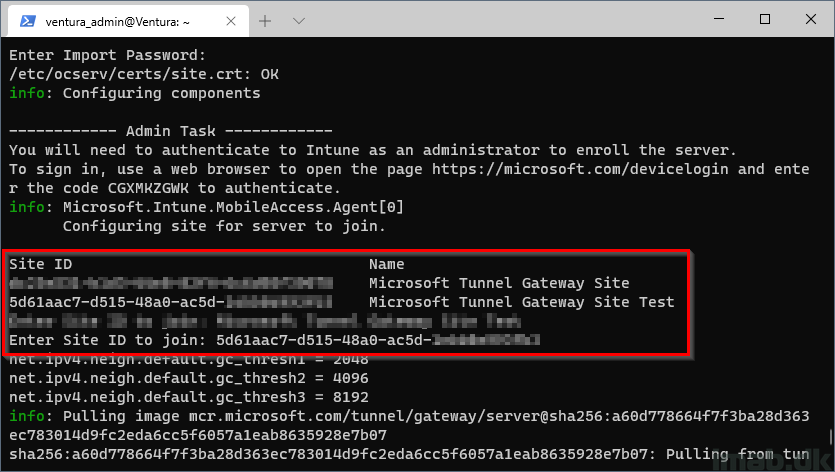
If you have multiple Microsoft Tunnel Gateway sites, the installation will prompt you to enter the ID of the site you wish to join the server into:
Final step
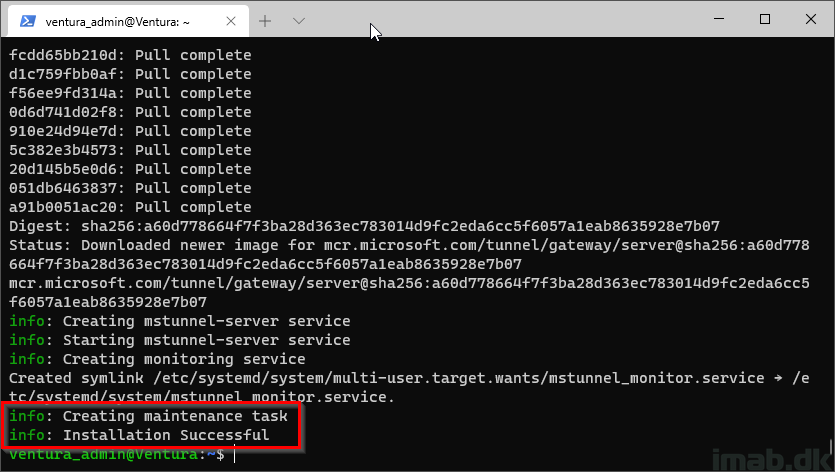
And the installation is complete when below information is being displayed:
Microsoft Endpoint Manager
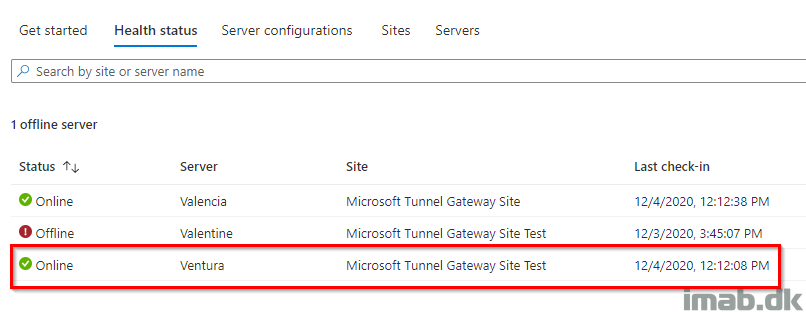
Taking a peek in the Microsoft Endpoint Manager admin center, you will now see your server on the list when browsing the health status, as well as the servers tab:
VPN Profile
Create a VPN configuration for iOS in the Microsoft Endpoint Manager admin center and select the Microsoft Tunnel Gateway site you created during this post.
The rest of the options in the iOS VPN configuration are optional, and I have left them out on purpose.
Assign the configuration to a group consisting of users or devices. I assigned this to a group consisting of test users.

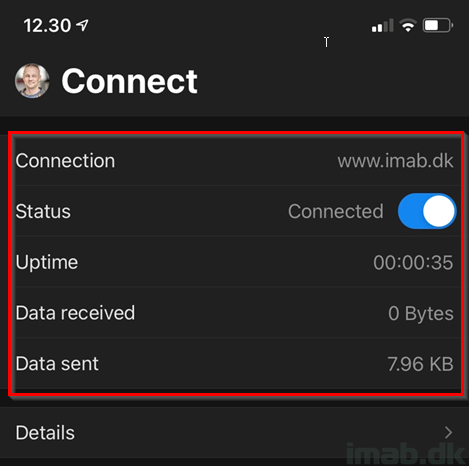
Results on iOS
And finally, I’m now connected to the delicious Microsoft Tunnel Gateway VPN.
Below illustration is taken from the Microsoft Tunnel app, which is available in the Apple App Store: Microsoft Tunnel on the App Store (apple.com)
The Microsoft Tunnel App is required in order to have the Microsoft Tunnel working, and the app can preferably be deployed from Microsoft Intune as well.
ENJOY 🙂
Hi Really useful document and served us well setting up our tunnel. Our TLS certificate is about to expire and we cant find any documentation on the process to renew this. Any advice or instructions on this process?
Hey Andy, wonder if the the certificate will be overwritten if you simply upload and configure a new one? Mine is yet to expire in 2022, so I haven’t been there just yet.