Introduction
So, I’m quite far behind in my blogging schedule, and I’m merely picking up on a feature which released in preview back some time in May. Luckily, this doesn’t impact the importance of the topic, and therefore I’m still putting it out there.
A neat example of putting Filters to use with Conditional Access, is by protecting your privileged users, like your Global Administrators, with an additional layer, only allowing access to resources if coming from specific devices.
Curious? This post will walk you through how to achieve just that. 🙂

Configuration
- First things first. Sign into the Microsoft Endpoint Manager admin center and locate the Endpoint security blade followed by the Conditional Access blade: https://endpoint.microsoft.com
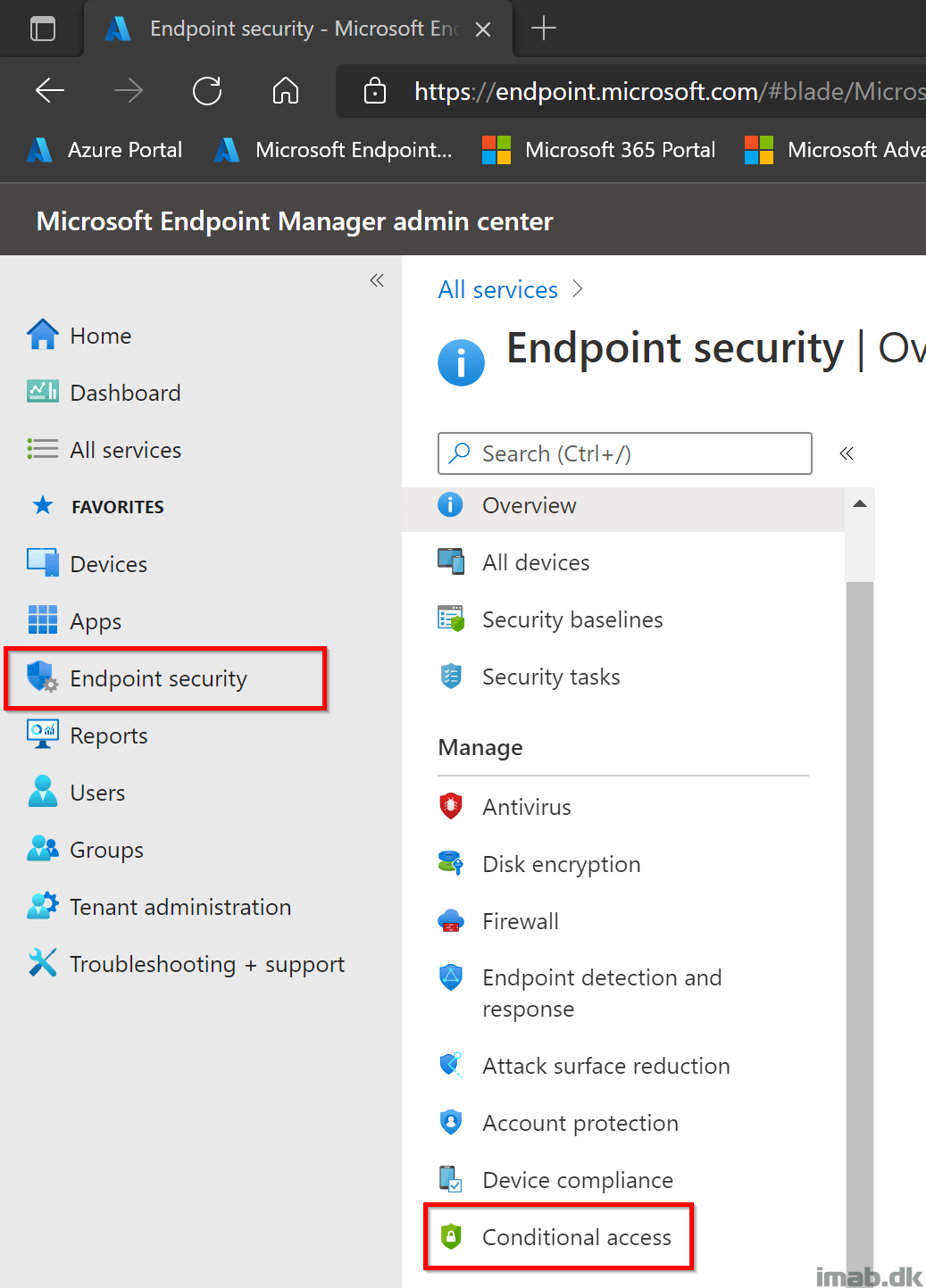
- Create a new policy and give it a relevant name. Mine is called: CA – Global Admins – Block Non-Approved Devices (Filters)
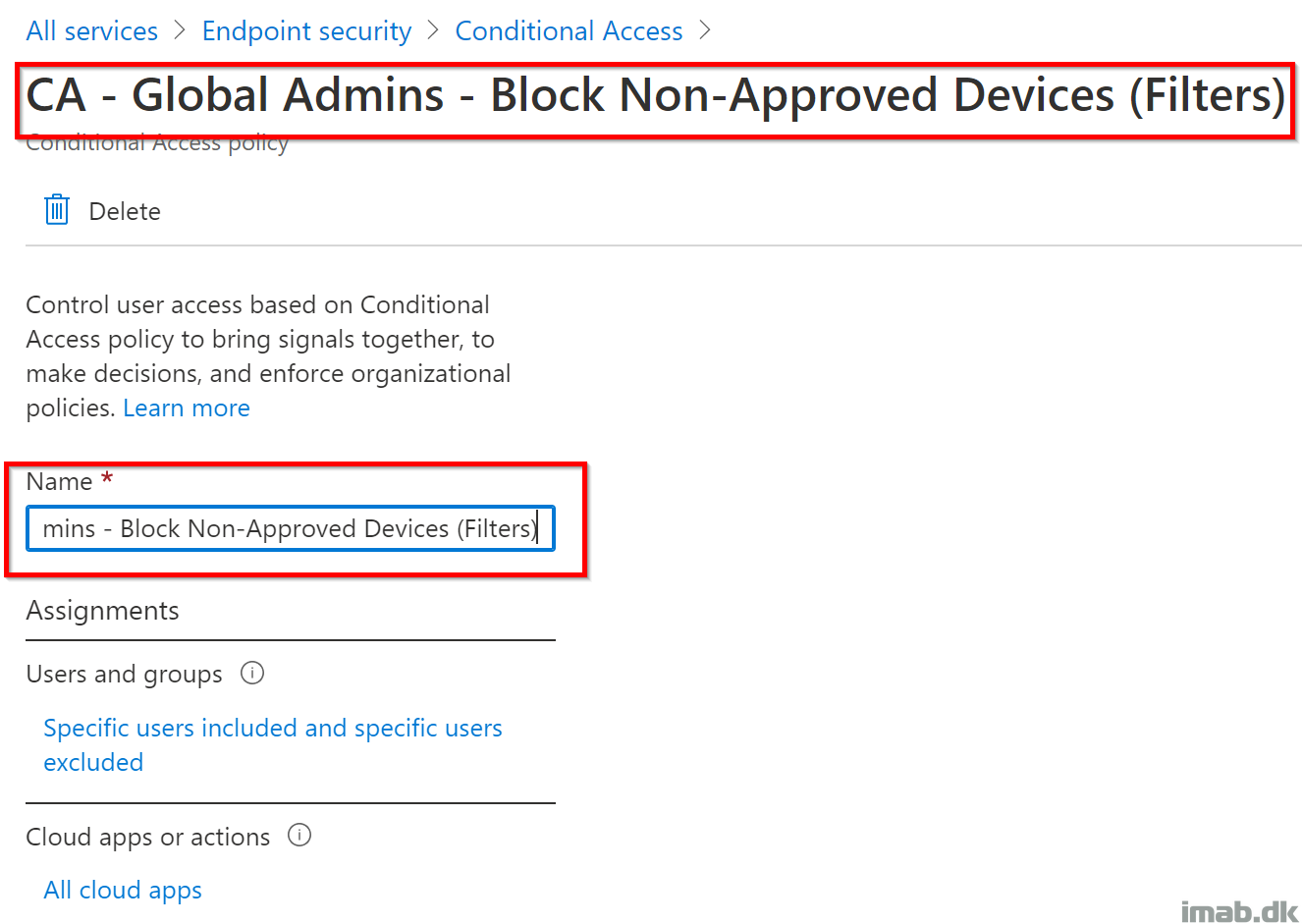
- Select and include the Global administrator role as shown below:
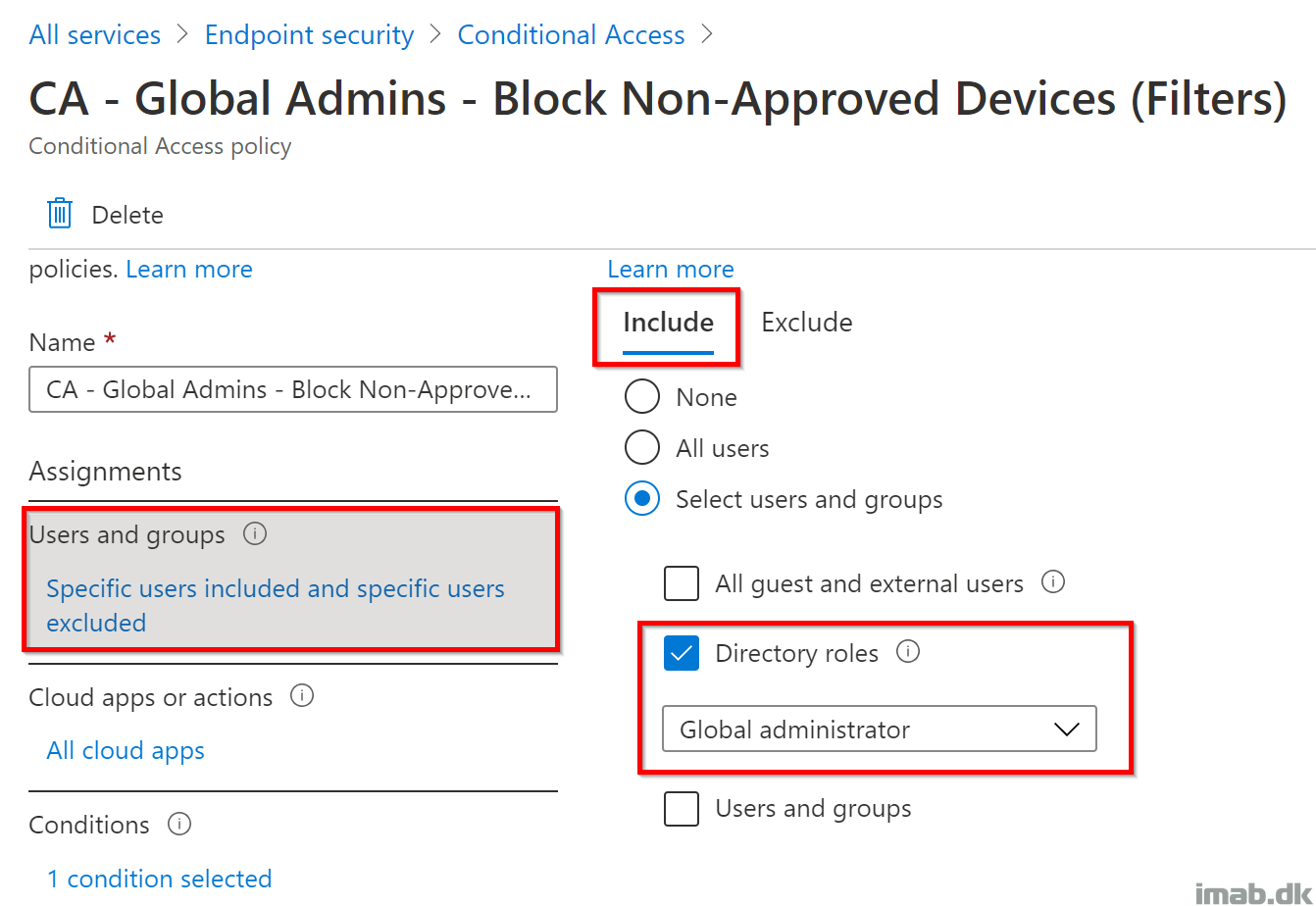
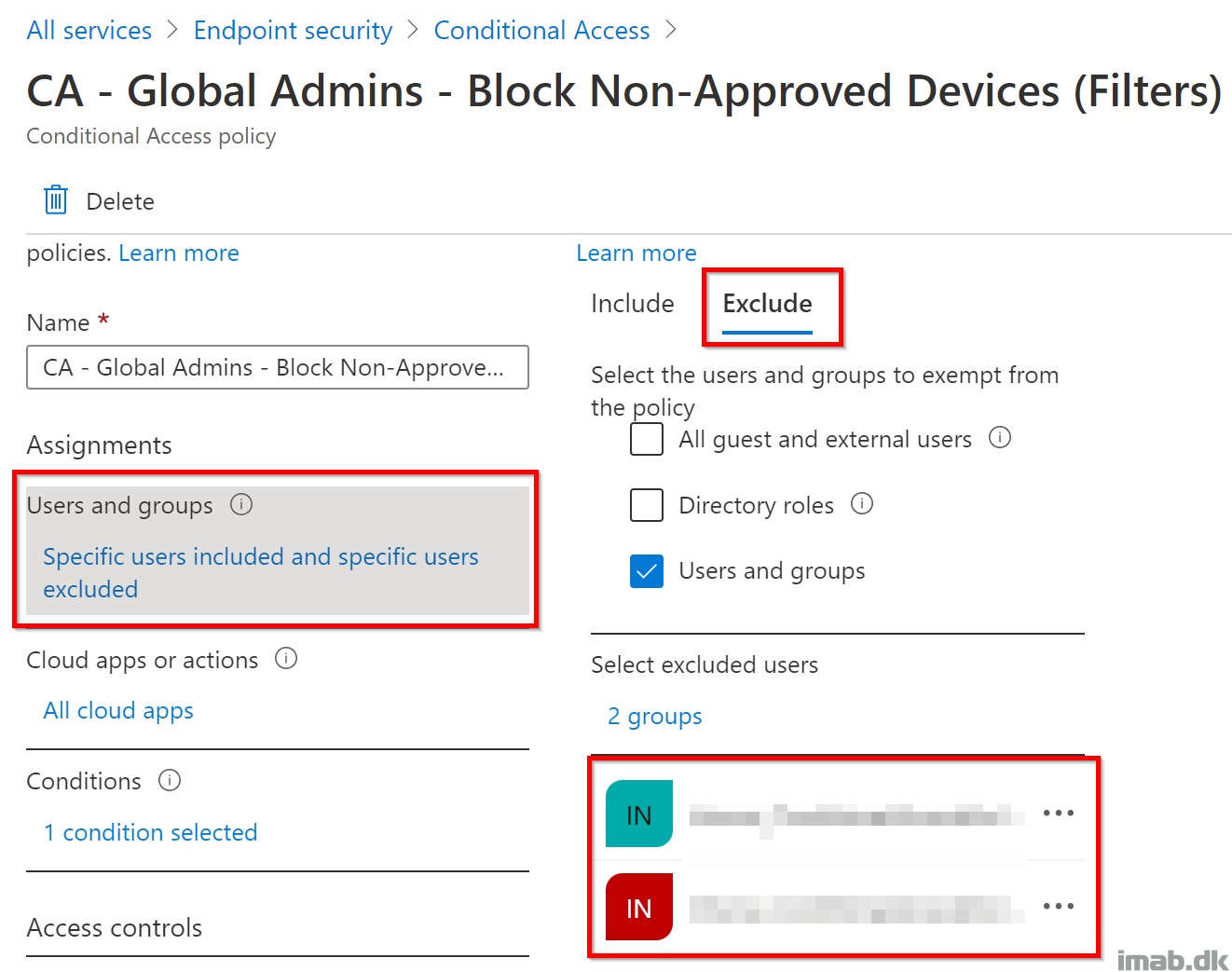
- Remember to configure some default exclusions, in case something is not working as intended. I’ve obfuscated mine for security reasons, but I always leave a backdoor on my CA policies:
- Conditions! This is the interesting part, where you via Filters are configuring which devices that are being allowed access to resources when authenticating as a Global Administrator.
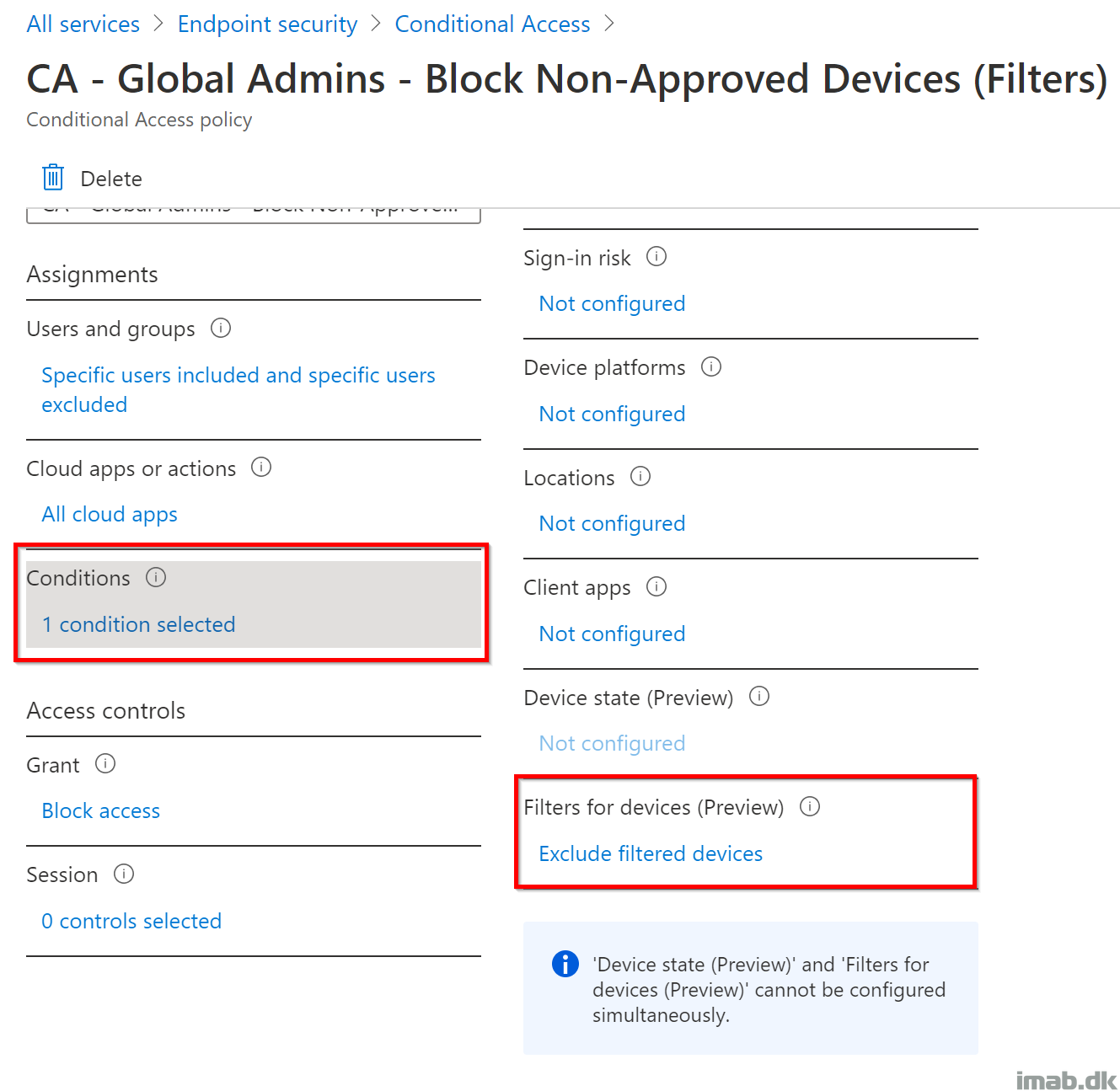
- Within the Filter for devices option, you have the option to configure a rule syntax, either including or excluding very specific devices, based on the selected property. In my scenario, it made the most sense to do so based on the name of the computer.
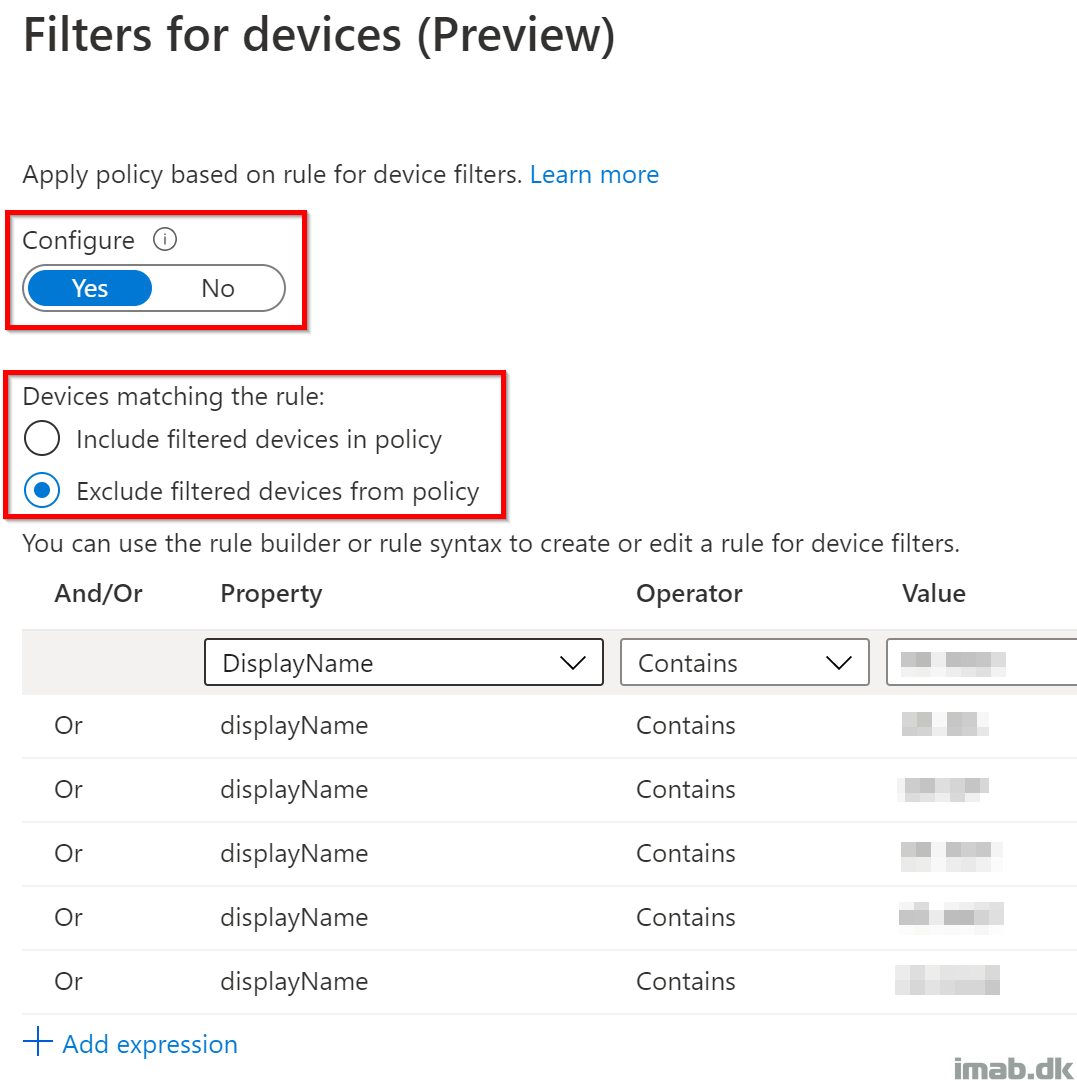
- In the Access controls option, you select Block access. This will essentially block the access for any Global Administrators, if not coming from any of the devices configured in the Filters rule syntax.

User experience
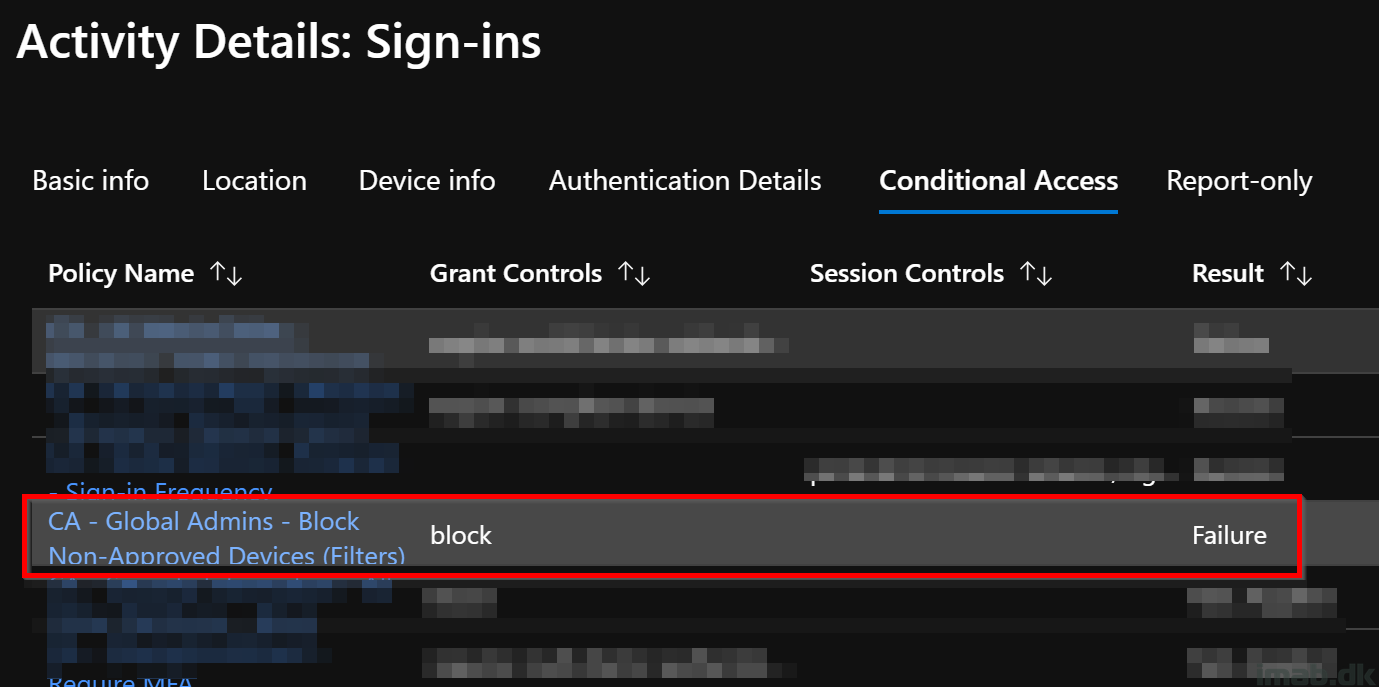
Now, when trying to sign into any cloud resources coming from a Global Administrator and a non-approved device, Conditional Access will prevent you from getting any further:

Taking a closer look in Azure AD on the sign-in in question, you will also see which Conditional Access policy that caused the behavior. As expected, this is the newly created policy based on Filters.
ENJOY 🙂