Introduction
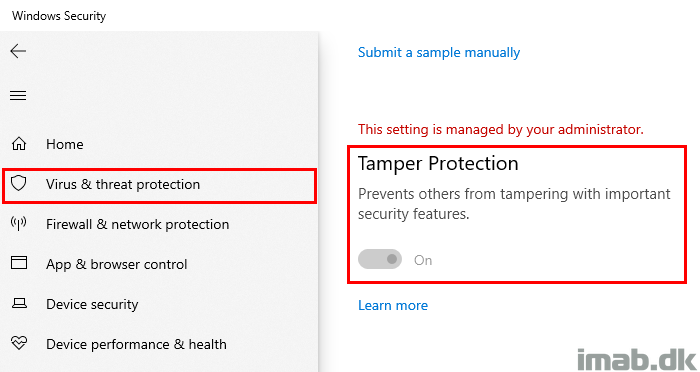
Late last night my time, Tamper Protection in the Microsoft Defender stack went Generally Available.
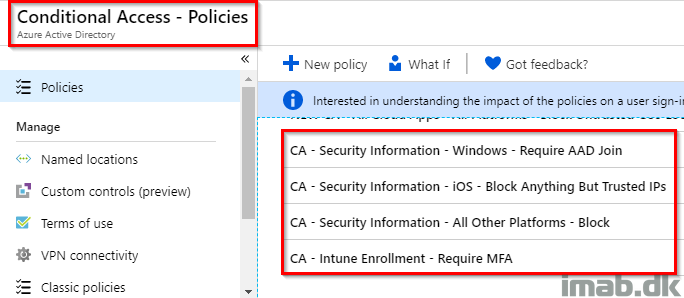
In short and as the name implies, this is a feature which essentially locks Microsoft Defender and prevents your security settings from being tampered with, including changes made by an administrator.
From a security perspective, this is a great and welcomed addition – let’s take a closer look. 🙂
PS. I did find some oddities in some of the behavior when trying to disable Microsoft Defender through Group Policy. More on that in the end of the post.