Introduction
If you are working with Microsoft Intune on a daily basis, chances are that you are familiar with the awesome Powershell Intune Graph script samples over at GitHub: https://github.com/microsoftgraph/powershell-intune-samples.
I have previously blogged specifically about putting 2 of the scripts to use here:
- https://www.imab.dk/remove-inactive-devices-in-intune-automatically-using-microsoft-graph-api-and-powershell-and-a-scheduled-task/
- https://www.imab.dk/changing-device-ownership-in-microsoft-intune-standalone-using-microsoft-graph-api/
If you are less familiar with Powershell, the script samples might seem a bit intimidating and difficult for some to put to use. The new Microsoft.Graph.Intune PowerShell Module to the rescue!
Now, this post is not about using the actual module, but how you with a single click can connect to the Graph API and gain access to all the available cmdlets in a very easy and sufficient way.
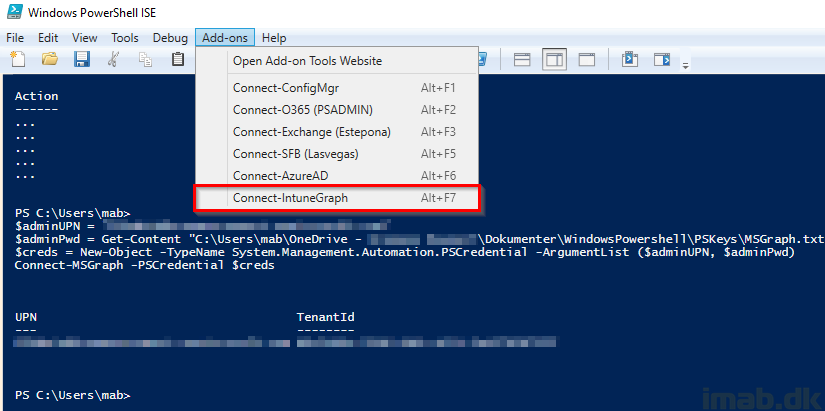
Intune PowerShell SDK
The actual module and manual installation is covered over at the official GitHub page at https://github.com/Microsoft/Intune-PowerShell-SDK. I will cover in basics what I have done, but I recommend that you read through the official guidelines as well.
Install the module
- Fire up an elevated Powershell and run Install-Module -Name Microsoft.Graph.Intune and accept any potential prompts for acceptance.
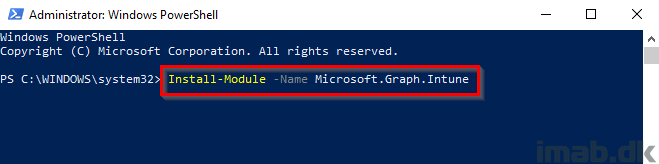
Provide consent
- An admin user must provide consent for this app to be used. This can be done with the following command: Connect-MSGraph -AdminConsent
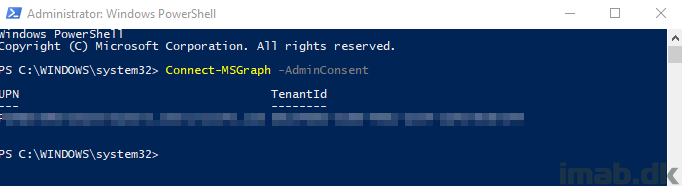
Service Account
- It goes without saying, but in order for you to be able to connect to the MS Graph, you will need to provide authentication. That be an account with the proper permissions and the associated password. No worries – the password is not provided in clear text.
- Create an unique .txt file containing the encrypted password running below snippet of code.
- NOTE: The .txt file created here will be unique for the computer/user creating the .txt file. As of such, the .txt file cannot be copied/moved and used elsewhere.
Read-Host -Prompt "Enter the password for your service account" -AsSecureString | ConvertFrom-SecureString | Out-File "<Enter File Path>\MSGraph.txt"
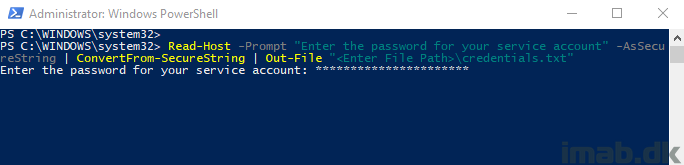
Powershell ISE
- Create a new sub-folder in your Documents folder. Rename this folder to WindowsPowershell. Similar to below illustration (don’t mind the other non-default folders):
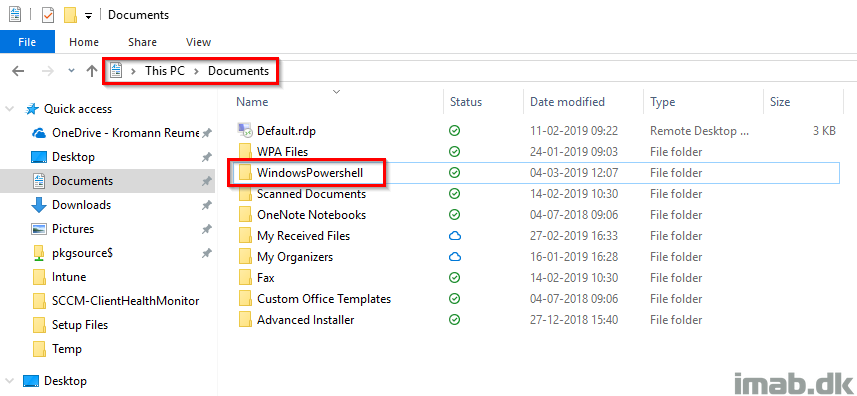
- Copy/paste below Powershell snippet into a new script. Save this script as Microsoft.PowerShellISE_profile.ps1 into the WindowsPowershell folder created in the previous step.
$psISE.CurrentPowerShellTab.AddOnsMenu.Submenus.Add("Connect-IntuneGraph",
{
# Replace with your service account
$adminUPN = "YourSA@YourTenant.com"
# Replace with path for your secure crendentials .txt file
$adminPwd = Get-Content "C:\Path to your credentials file\PSKeys\MSGraph.txt" | ConvertTo-SecureString
$creds = New-Object -TypeName System.Management.Automation.PSCredential -ArgumentList ($adminUPN, $adminPwd)
Connect-MSGraph -PSCredential $creds
},"ALT+F2")
- The end result will be similar to this:
- Note that I have a sub folder here called PSKeys. For your inspiration, you can create a similar sub folder and store your MSGraph.txt file here.
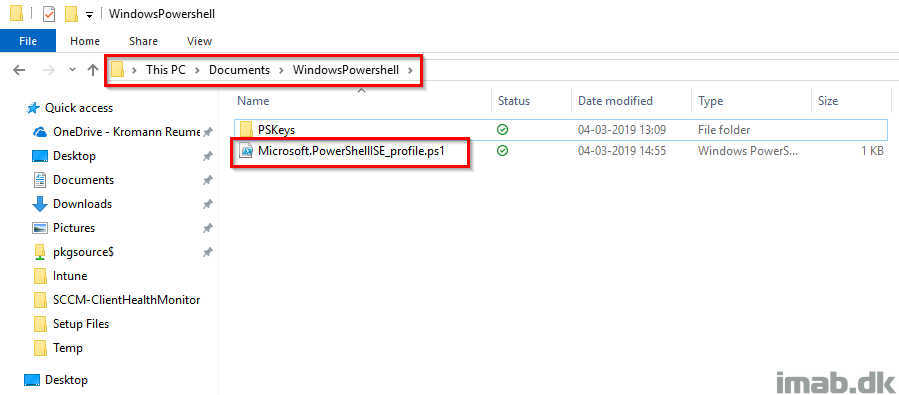
End result
You now have the option to connect to the Microsoft Graph for Intune with a single click. Hell yeah! Notice I have other services added in there as well, such as ConfigMgr, Office 365, Azure AD etc.

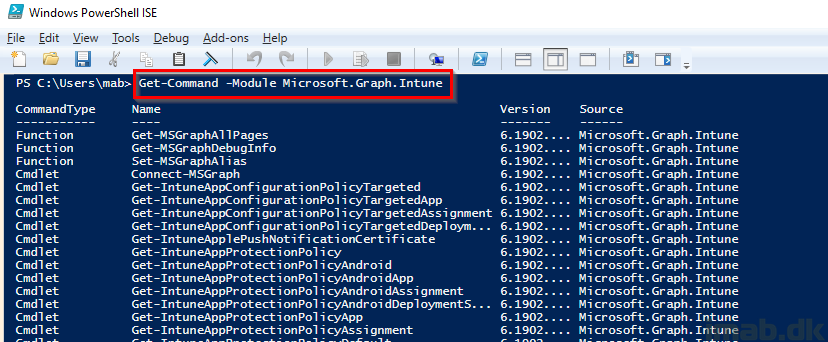
And when running Get-Command -Module Microsoft.Graph.Intune you will get a list of all the available cmdlets:
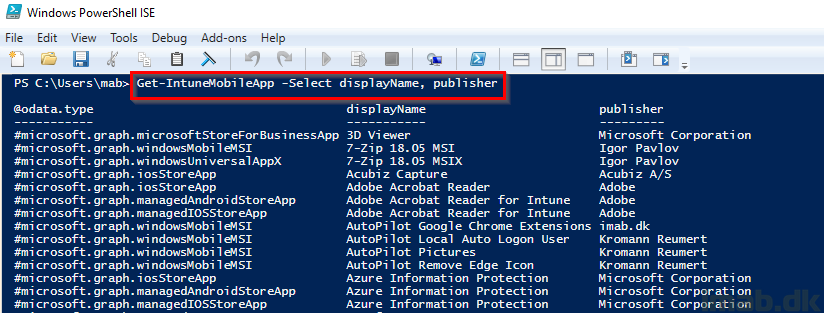
Where one example is Get-IntuneMobileApp -Select displayName, publisher displaying all the apps I currently have created in Intune.
MFA considerations
At the time of writing, I actually don’t know if the module supports MFA in any way. Other services, such as Exchange Online do support this when running automated tasks with Powershell. See this post for more details: https://blogs.technet.microsoft.com/solutions_advisory_board/2017/04/27/connect-to-office-365-services-with-multifactor-authentication-mfa-and-powershell/
However, there are possibilites around this if using Conditional Access. For example to only enforce MFA if the account is used on non-domain joined devices and/or non-compliant devices or even restrict the account to only run when on trusted IPs (this is how I prefer MFA being used).
ENJOY 🙂
Thanks for the write-up Martin!
I have MFA configured for my tenant. When I try to connect, I get the following message:
“Connect-MSGraph : AADSTS50076: Due to a configuration change made by your administrator, or because you moved to a new location, you must use multi-factor authentication to access ‘00000003-0000-0000-c000-000000000000’.”
Any way around this without disabling MFA?
Good question. I actually don’t know. I have made a “MFA considerations” paragraph in the very end of the post. Thanks for the headsup 🙂
Nice article. I am doing the exact same thing, but the connect call returns with a ‘unknown_user_type’. I have a function that takes a username and checks to see if I have a secure string password for that user. If not, it prompts for the password and saves that to a secure file. If it does exist, it creates a PSCredential object exactly like your example. However, when I pass that to Connect-MSGraph -PSCredential $myCreds I get the above error. I also seem to have two versions of the graph module, the later one uses a -Credential parameter instead of -PSCredential. Any thoughts?
you can do this :
#(enter the email and password of your account in popup)
$cred = get-credential
Connect-MSGraph -PSCredential $cred
(if you have signed in at least one time with just connect-msgraph , you should have cookies or saved informations on your machine so the previous commands will allow you to sign in automatically)