Introduction
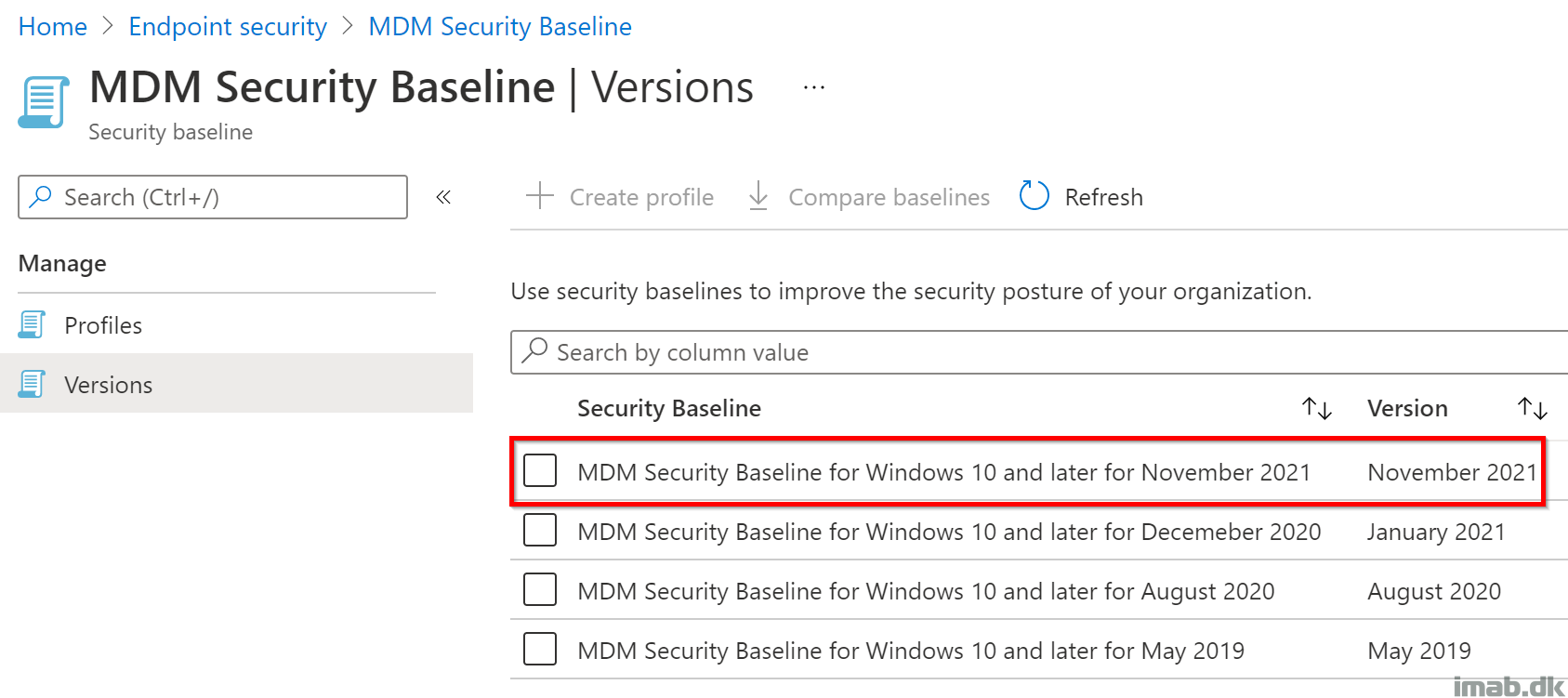
A new version of Microsoft 365 Apps for enterprise security baseline was released last week, delivering the latest recommended security configuration for the included applications.
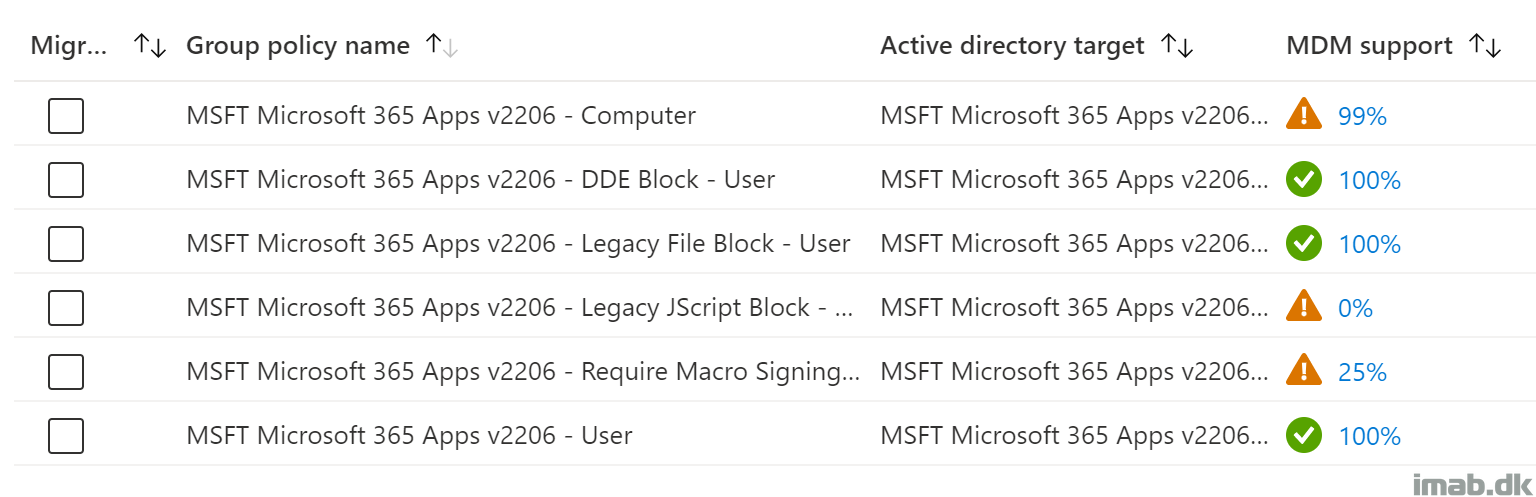
Now, by the time of writing, not everything can be transitioned into Microsoft Intune natively. There are simply not MDM support for each and every setting. So for those settings without MDM support, you will have to leverage ADMX ingestion or PowerShell.
This post will give you insight on using Group Policy Analytics, as well as how to use ADMX ingestion and PowerShell to completely transition management of the security baseline into the cloud.