Introduction
Why would you do this, when there’s a built-in option to do so, you may ask?
Well, I needed an alternative, as I kept getting some weird errors when using the built-in configuration profile in Intune. The errors only happens for me on Windows 11, so while I’m investigating these, I wanted to have an alternative in order for us to move on with our Windows 11 process.
- EDIT: I was just made aware in the comment section, that there’s a known issue around this. Granted, this post can obviously serve as a workaround (or permanent solution moving forward) 🙂
Also, there’s still no option to lock the VPN strategy to SSTP-only in the native configuration profile in Intune. For that I used to run another weekly PowerShell script, resetting the strategy from IKEv2 to SSTP-only. Using a solution like this, also removes that requirement.
What errors?
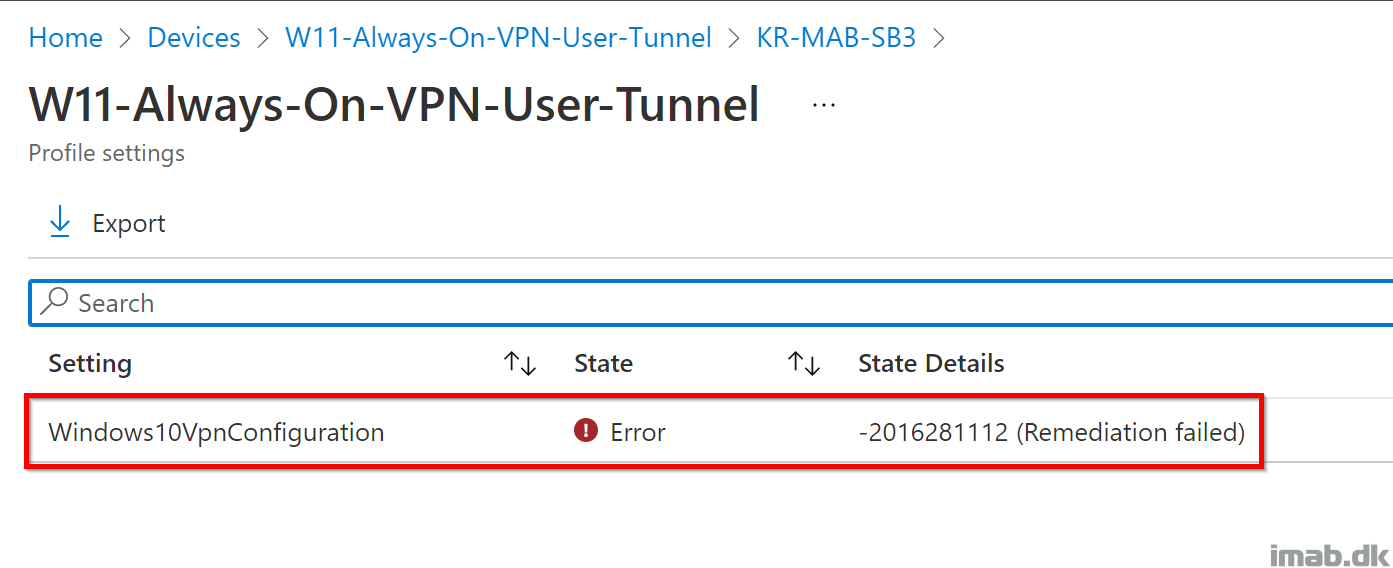
The initial error I get with the usual Always On VPN configuration on Windows 11, is illustrated below:
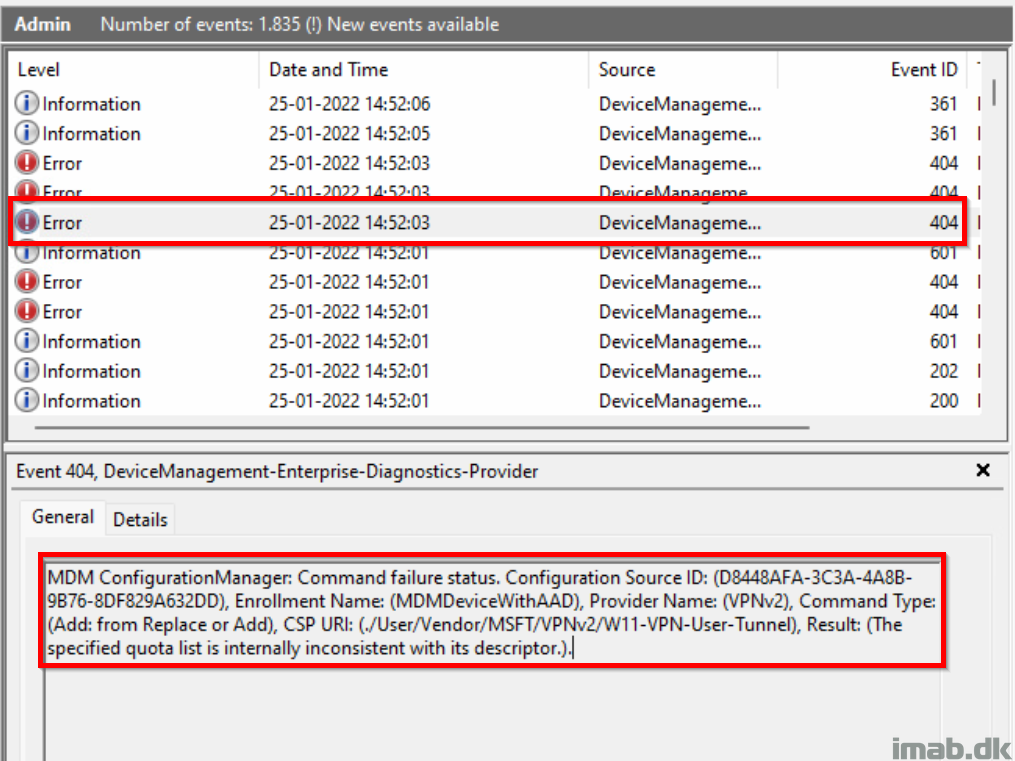
This is also translated into following error in the Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider event log, also as illustrated below:
- MDM ConfigurationManager: Command failure status. Configuration Source ID: (D8448AFA-3C3A-4A8B-9B76-8DF829A632DD), Enrollment Name: (MDMDeviceWithAAD), Provider Name: (VPNv2), Command Type: (Add: from Replace or Add), CSP URI: (./User/Vendor/MSFT/VPNv2/W11-VPN-User-Tunnel), Result: (The specified quota list is internally inconsistent with its descriptor.).
The result on the device is, that the VPN profile comes and goes with each MDM sync, rendering the VPN connection useless.
Root cause?
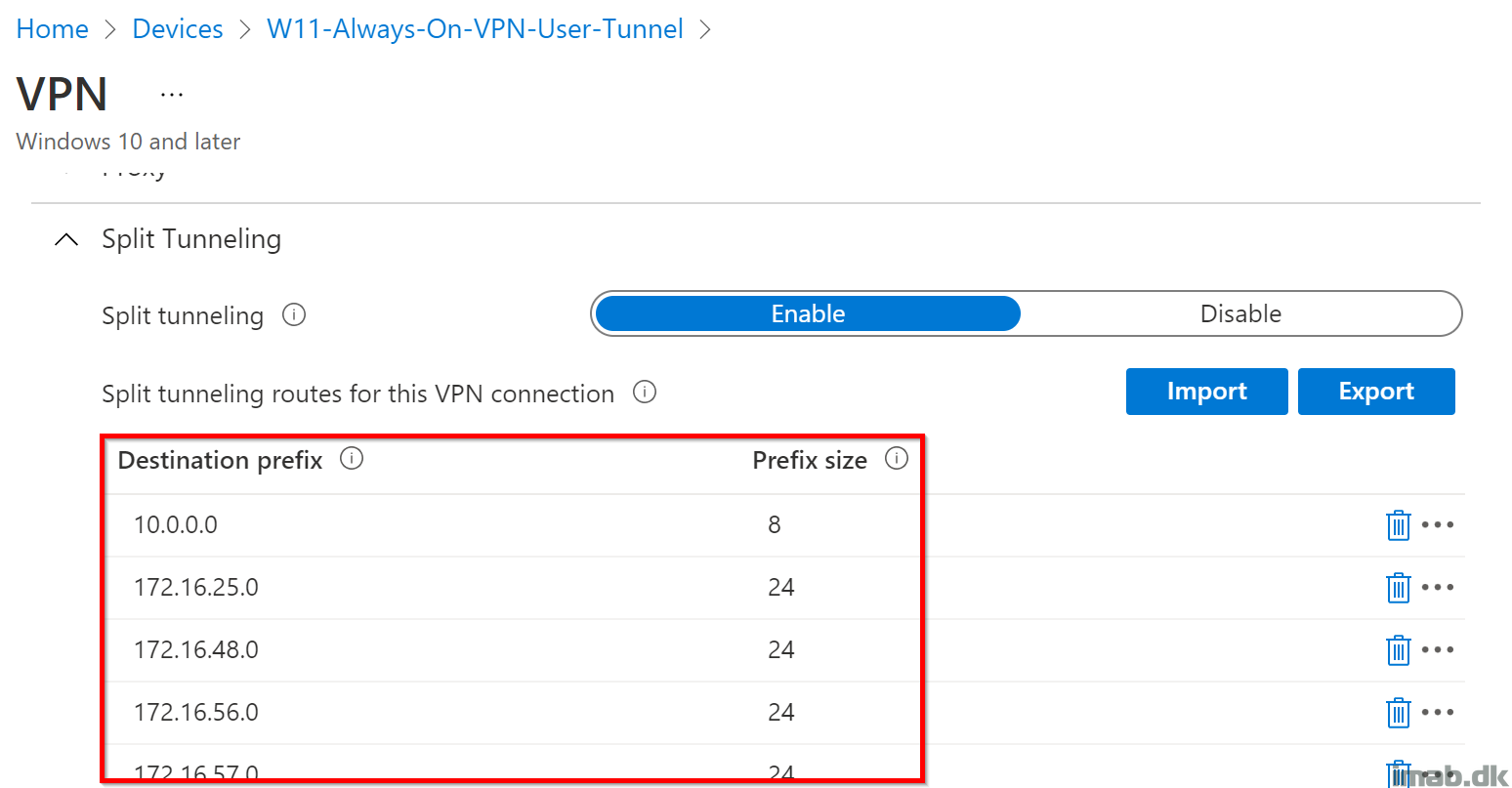
I’ve narrowed it down to be related to the split tunneling routes. If I remove all the routes configured here, the error goes away.
Even configuring a single route, breaks the entire VPN profile and I have no clue why. I also see other people mentioning the same issue, when searching around the Internet.
- EDIT: I was just made aware in the comment section, that there’s a known issue around this. Granted, this post can obviously serve as a workaround (or permanent solution). 🙂
The alternative
My alternative involves using 2 PowerShell scripts with Endpoint Analytics Proactive Remediations in Microsoft Endpoint Manager.
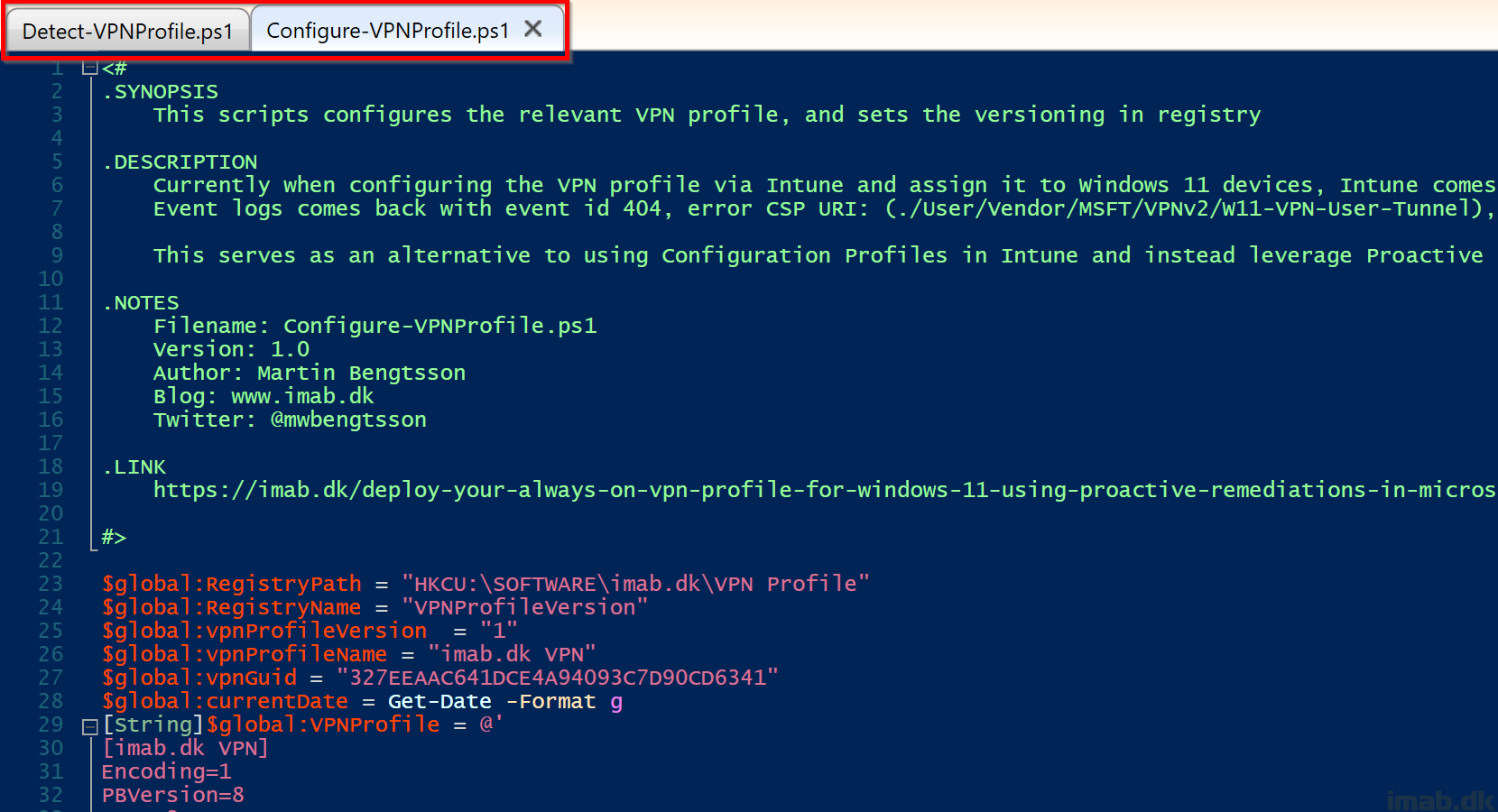
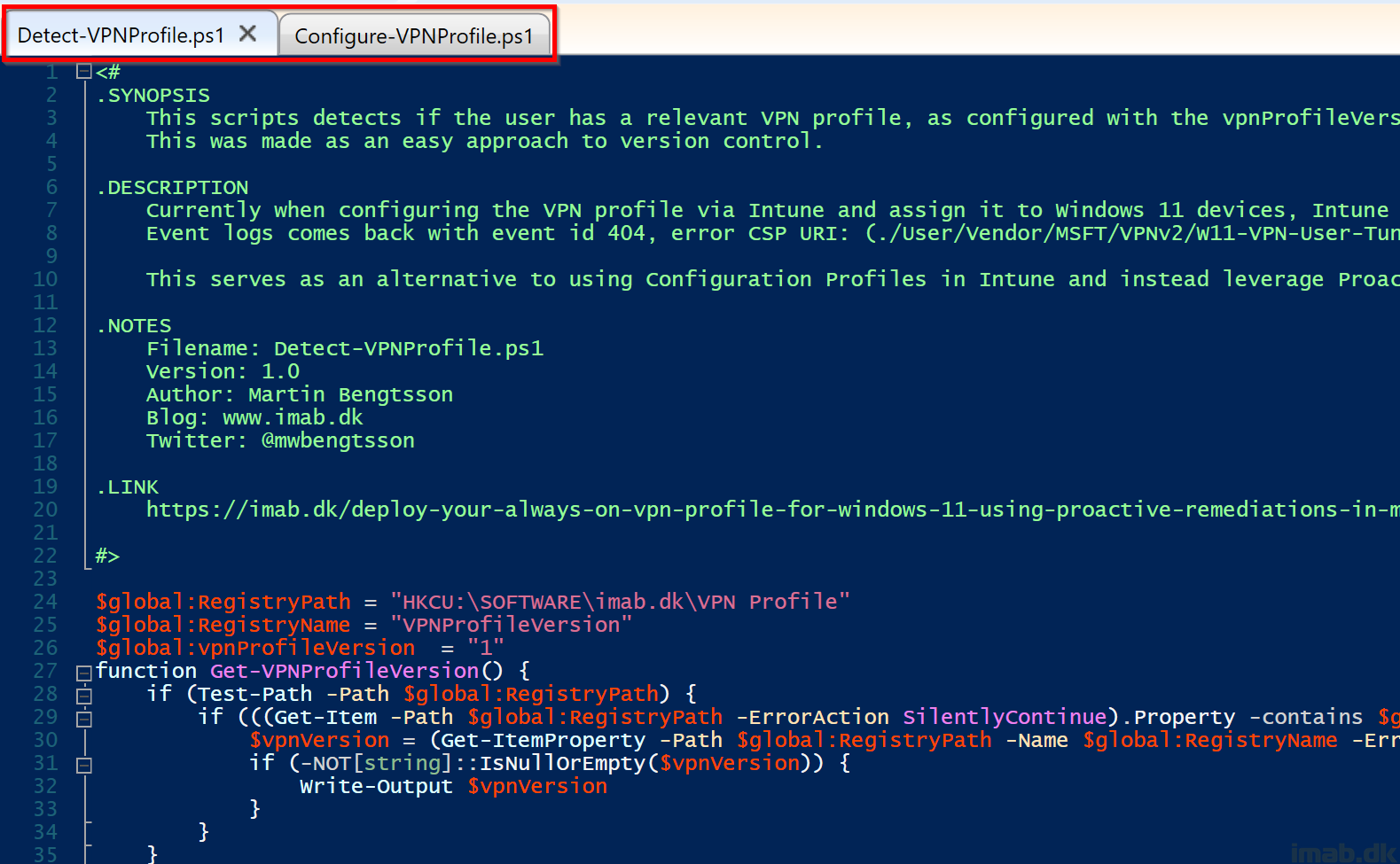
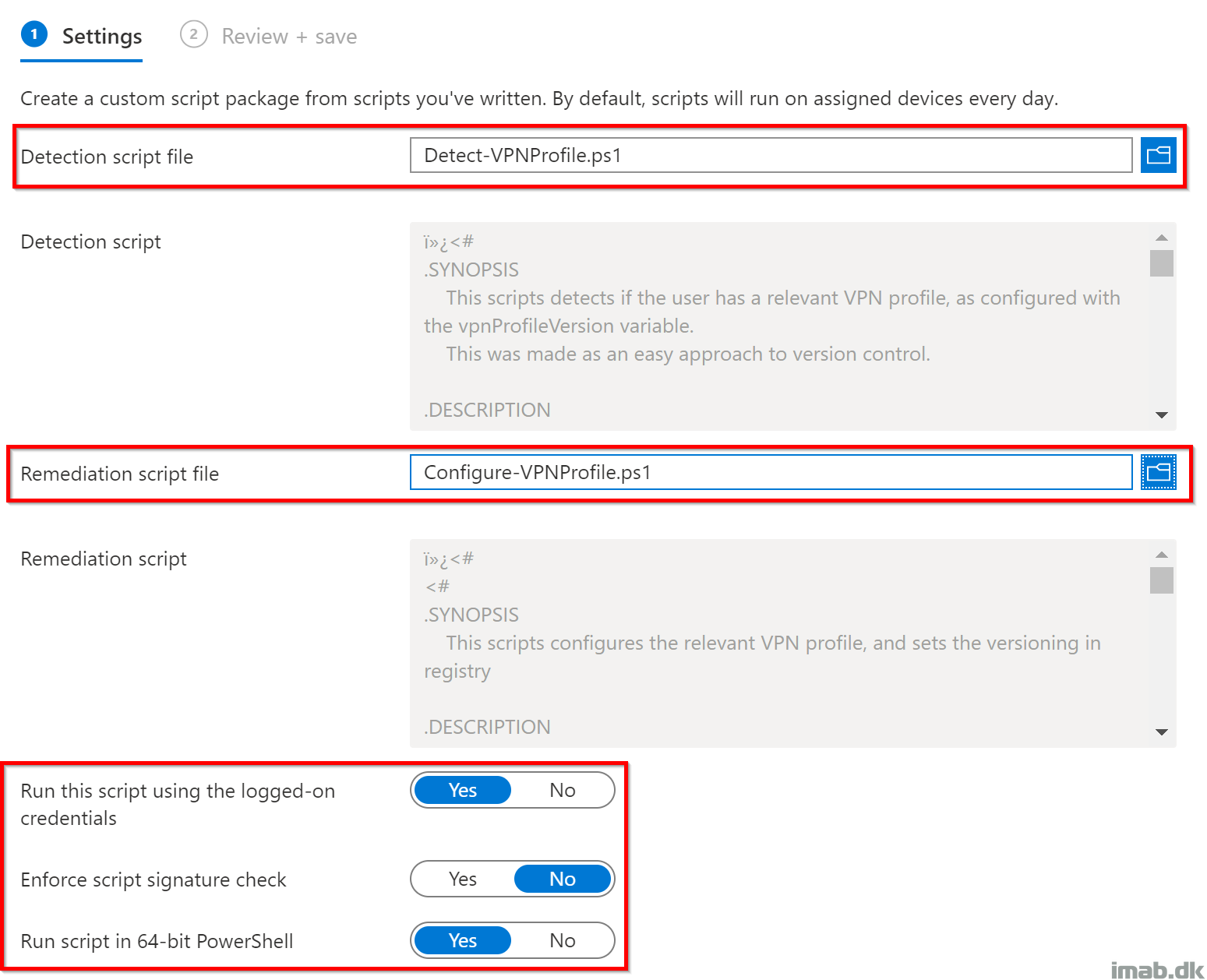
Detect-VPNProfile.ps1
Find the Detect-VPNProfile.ps1 script over at my GitHub repository: PowerShell/Detect-VPNProfile.ps1 at master · imabdk/PowerShell (github.com)
This script does following in headlines:
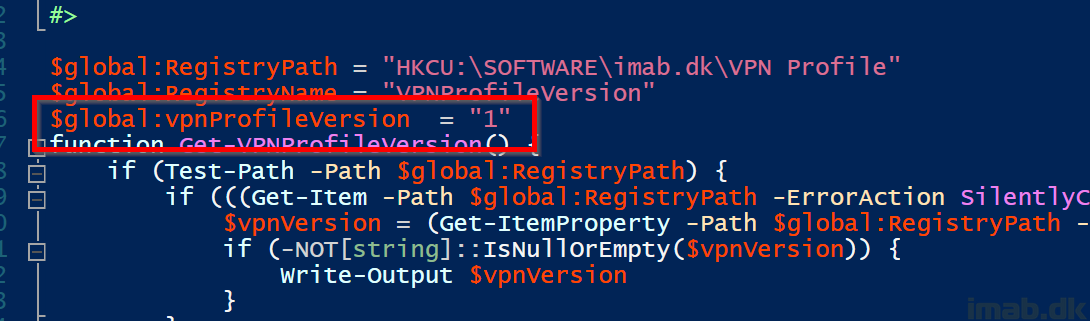
- This script queries the registry for values related to the Configure-VPNProfile.ps1 script
- These values are used as a sort of detection method, as well as version control
- If the relevant version is found in registry, the script will exit with error code 0
- If the relevant version is not found or is in mismatch, the script will exit with error code 1
- This will trigger the Configure-VPNProfile.ps1 script to run
- These values are used as a sort of detection method, as well as version control
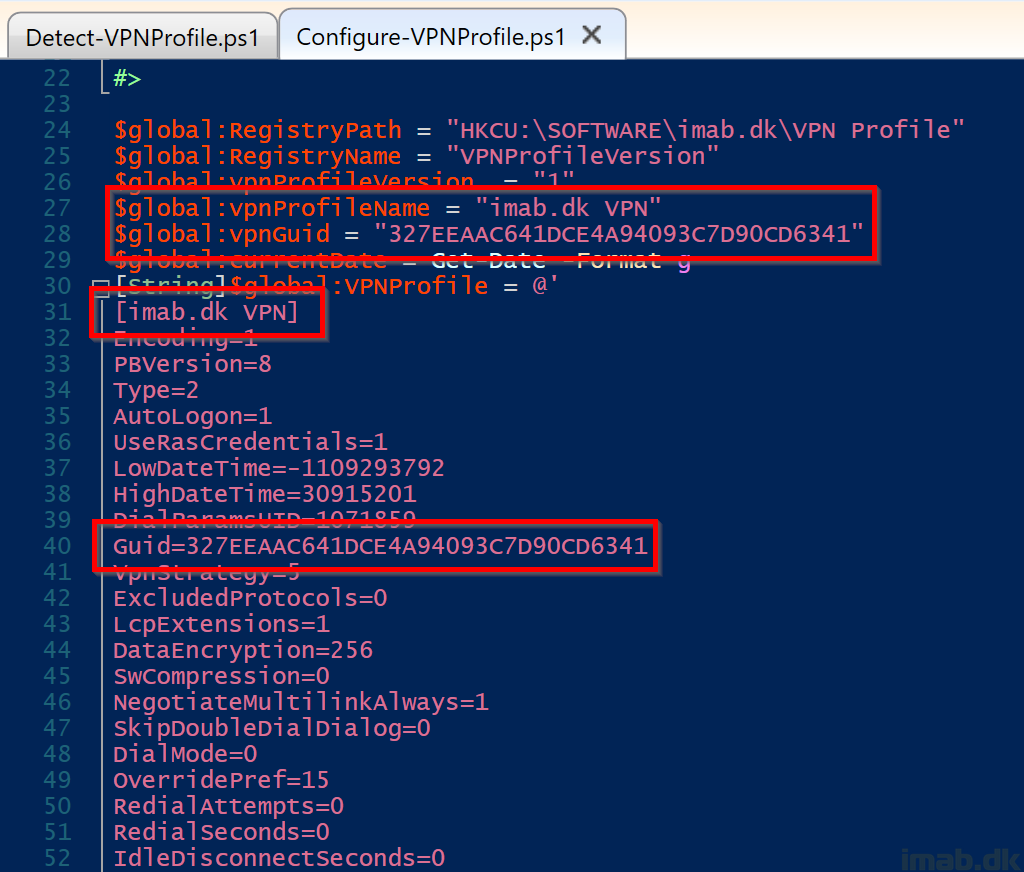
Configure-VPNProfile.ps1
Find the Configure-VPNProfile.ps1 script over at my GitHub repository: PowerShell/Configure-VPNProfile.ps1 at master · imabdk/PowerShell (github.com)
This script does following in headlines:
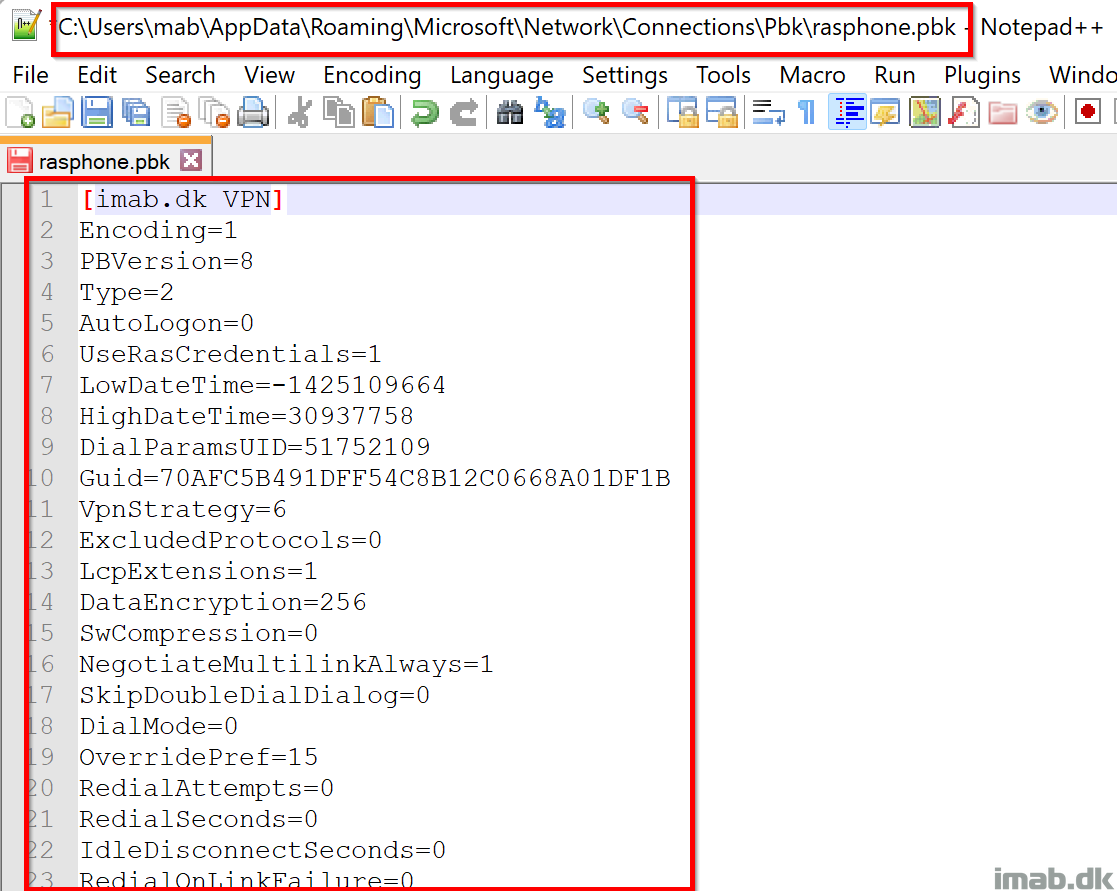
- This script looks for a rasphone.pbk file in the users profile
- If found, it looks to see if a current VPN profiles matches the name or guid
- If either matches, the script will replace the entire rasphone.pbk file essentially updating the entire VPN profile
- If rasphone.pbk is found, but no VPN profile matching the name or guid, the profile defined in the $global:VPNProfile will be added to the existing rasphone.pbk file
- If found, it looks to see if a current VPN profiles matches the name or guid
- If no rasphone.pbk is found, a new file is created containing the VPN profile defined in $global:VPNProfile
IMPORTANT!
Make sure that you edit this portion, to suit your rasphone.pbk file:
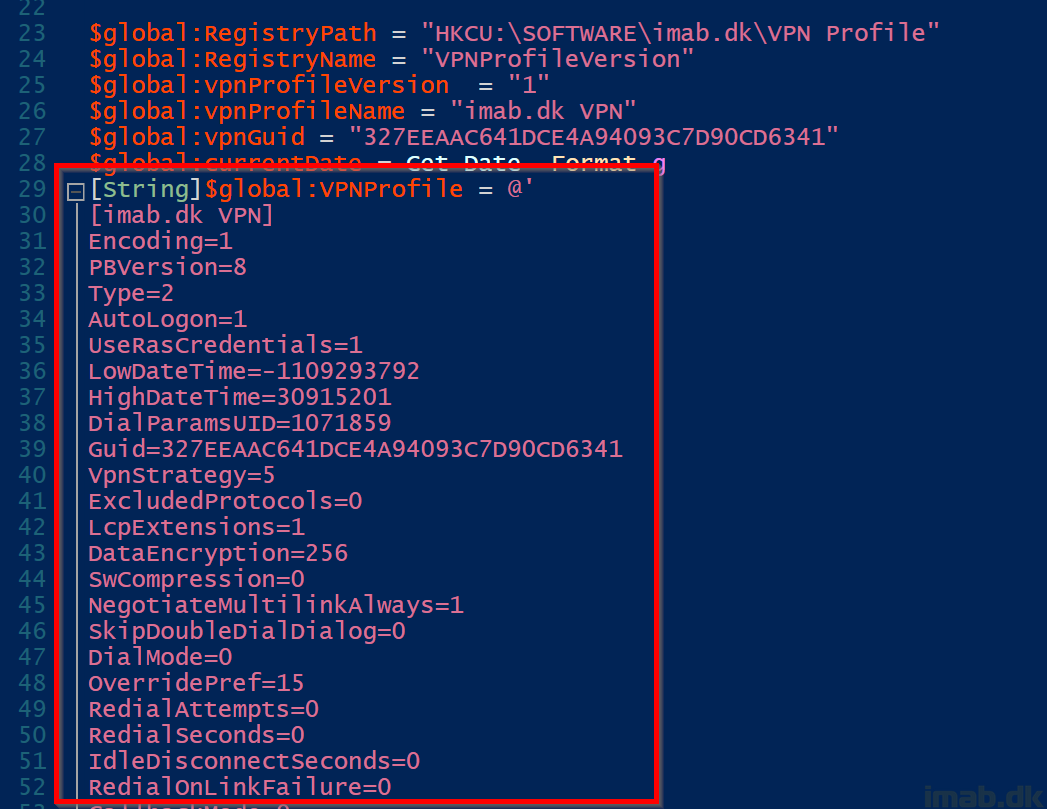
MORE IMPORTANT!’
The entire $global:VPNProfile variable needs to be replaced with your own content. That be the content of a rasphone.pbk file you created yourself or Intune created for you.
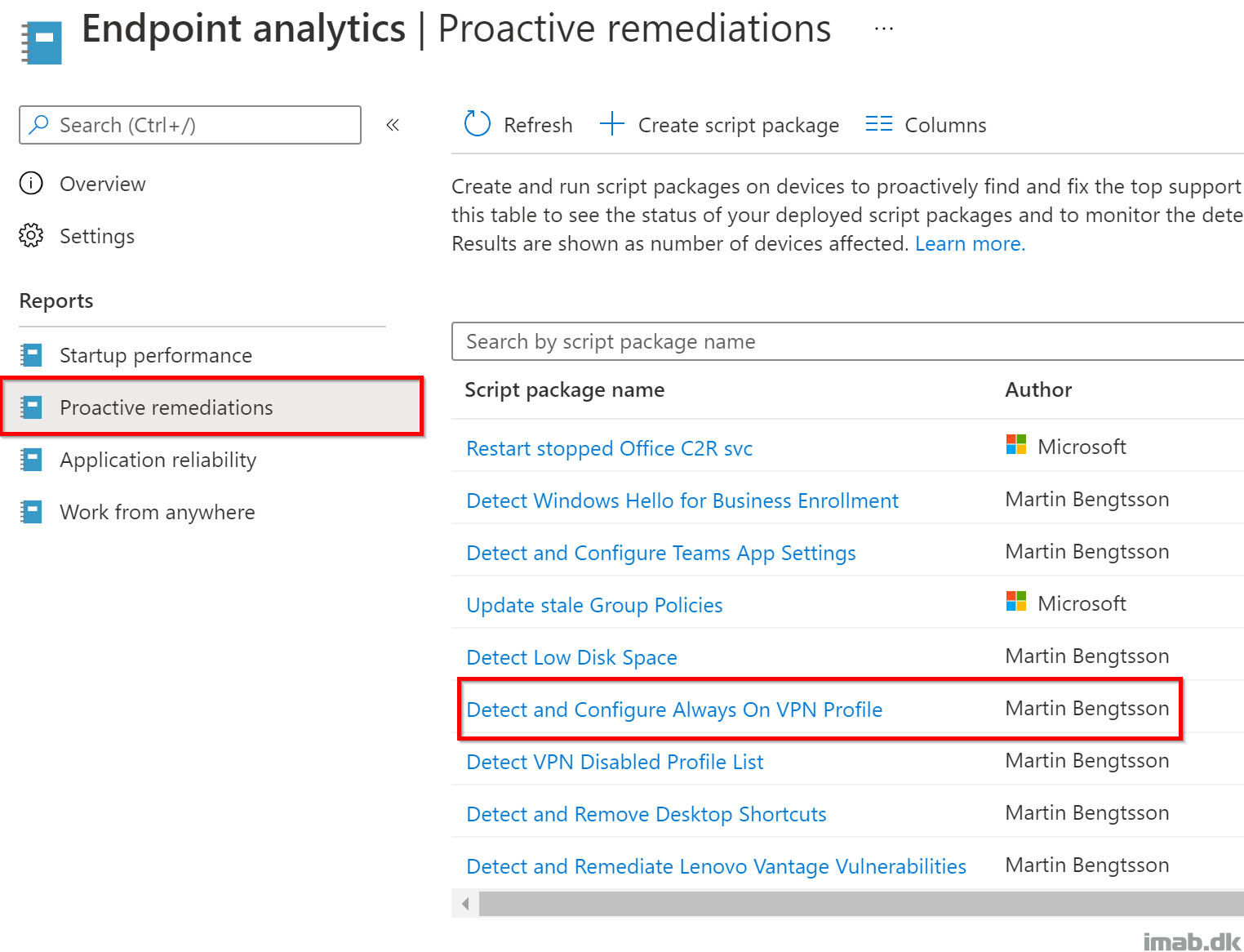
Proactive Remediations
Head into the Microsoft Endpoint Manager admin center: https://endpoint.microsoft.com and locate the Proactive Remediations feature within the Reports -> Endpoint Analytics blade:
Settings
Use the 2 scripts explained above as illustrated below:
In Action
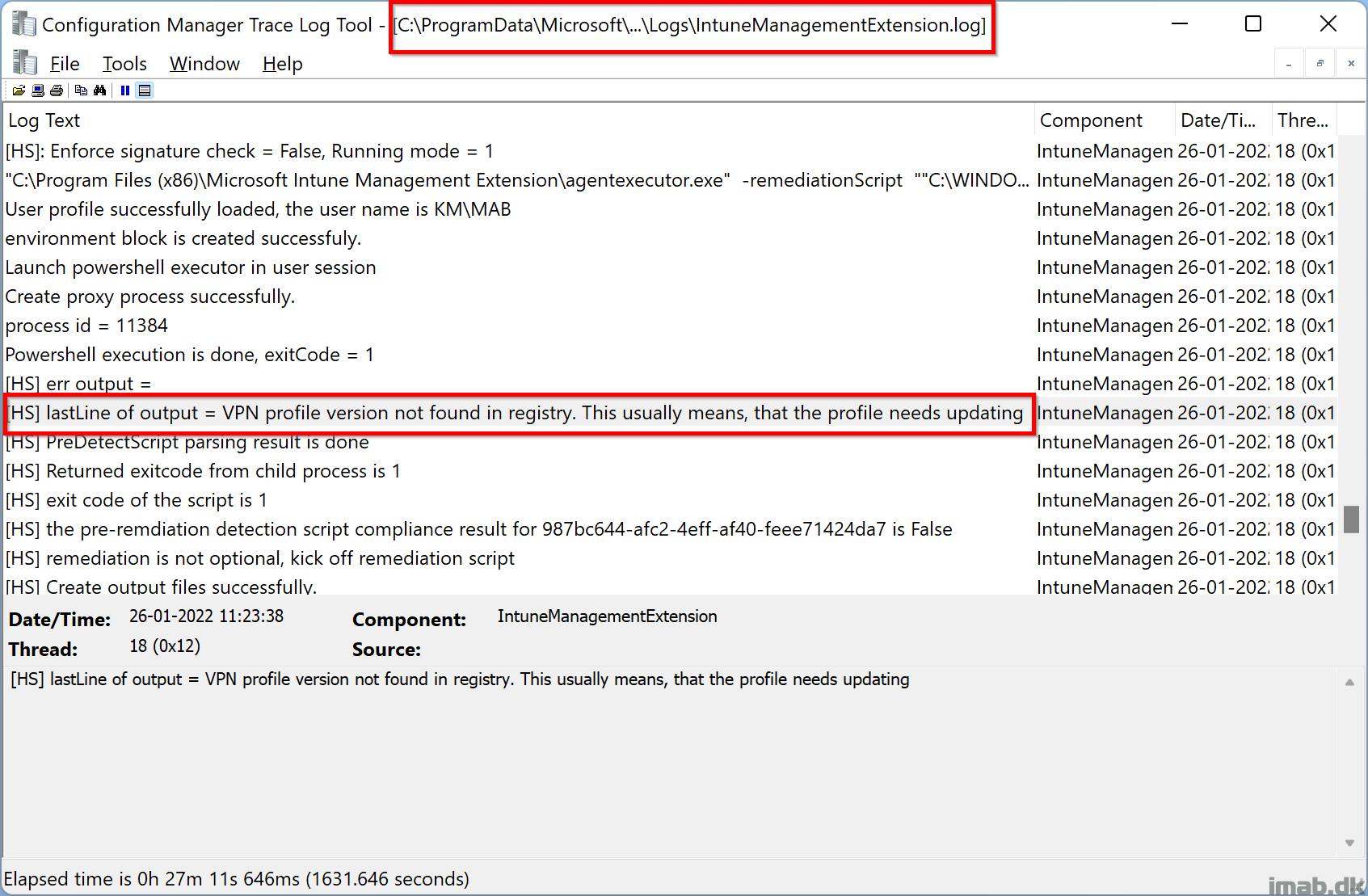
Taking a closer look on IntuneManagementExtension.log (C:\ProgramData\Microsoft\IntuneManagementExtension\Logs) you will see if the Detect-VPNProfile.ps1 finds it relevant to apply a new VPN profile:
- [HS] lastLine of output = VPN profile version not found in registry. This usually means, that the profile needs updating
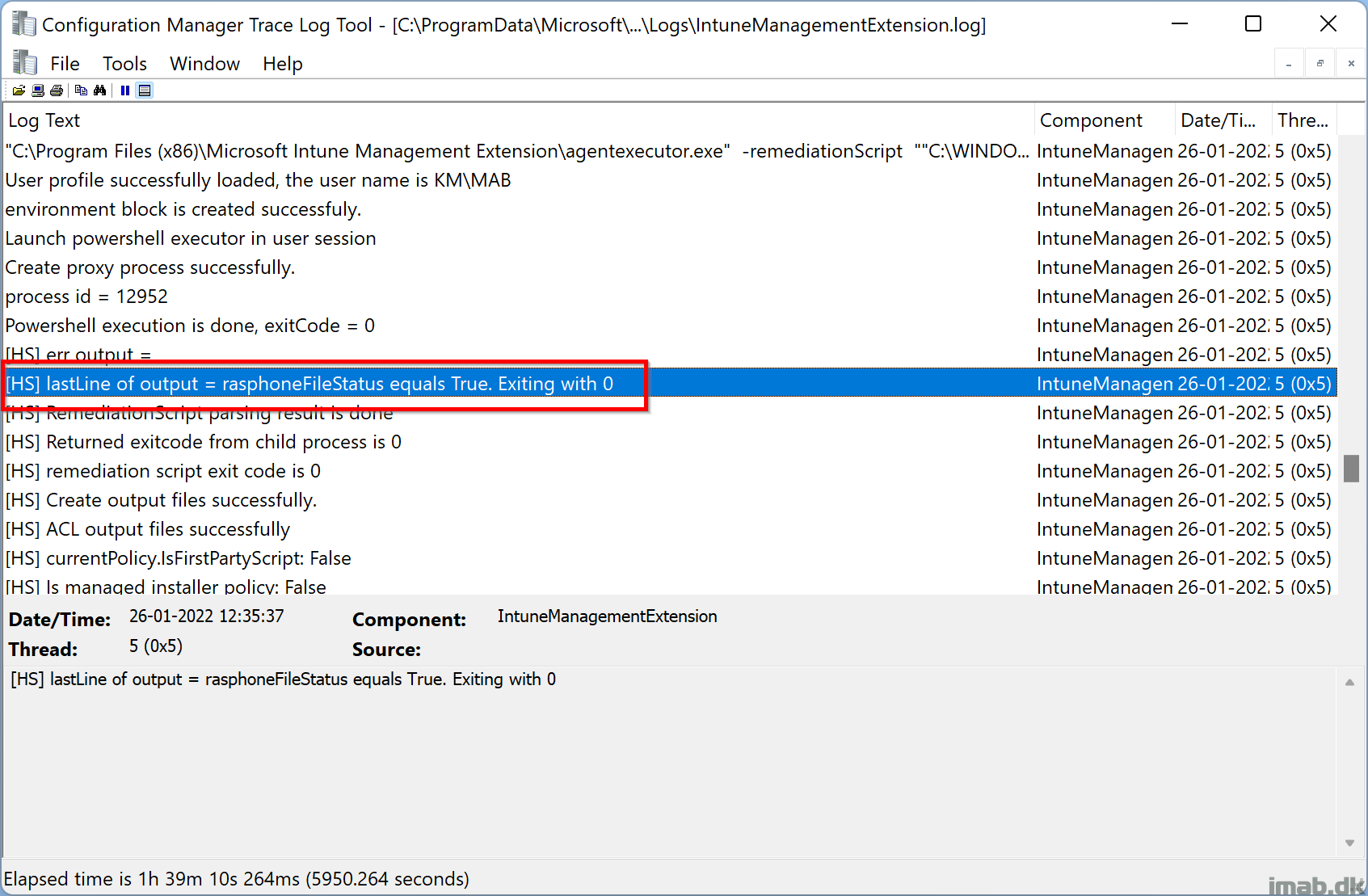
When the Configure-VPNProfile.ps1 kicks off and finishes, the IntuneManagementExtension.log will yield following:
- [HS] lastLine of output = rasphoneFileStatus equals True. Exiting with 0
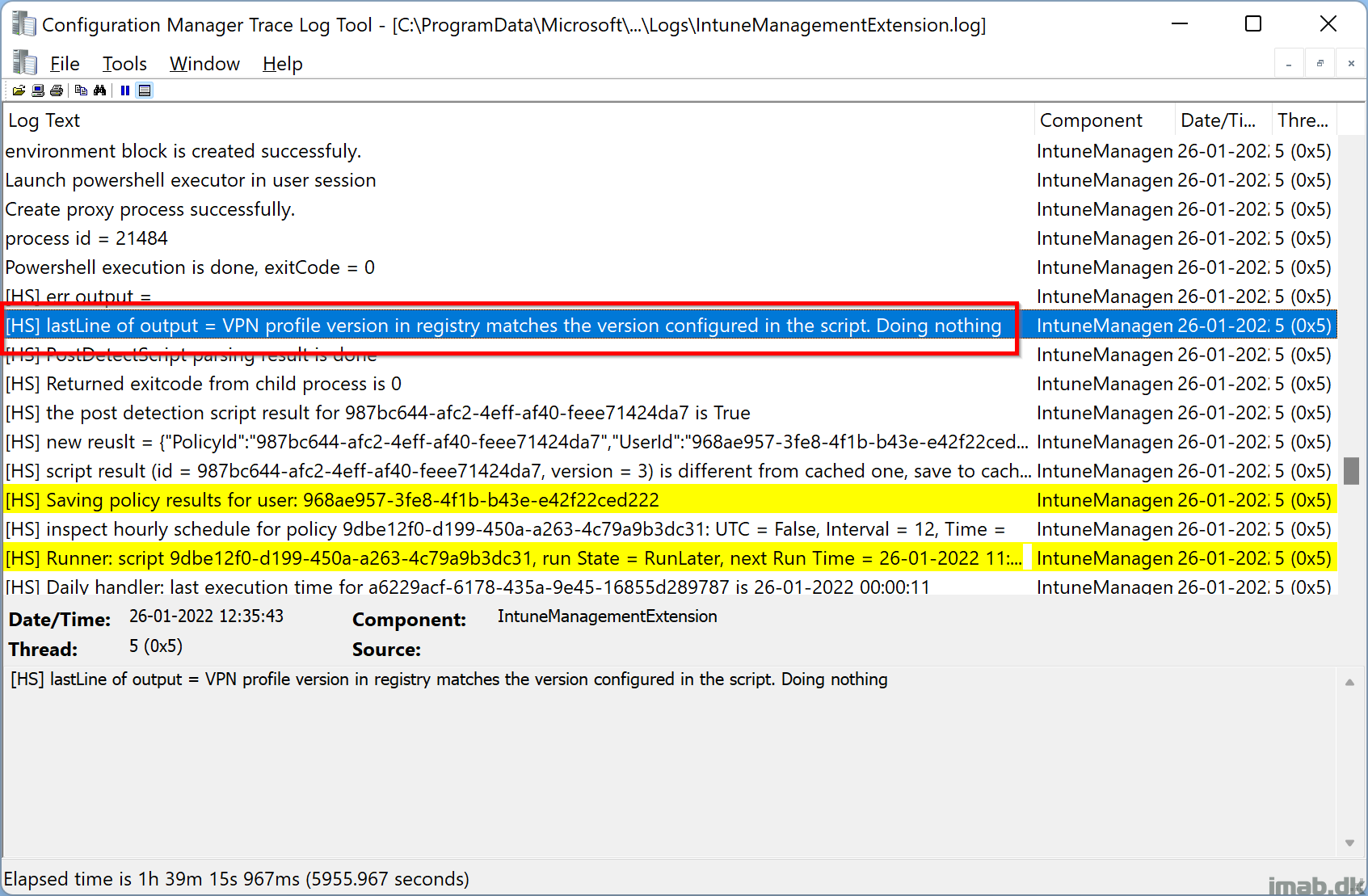
When the Detect-VPNProfile.ps1 script finds that no new version is available (comparing registry with the version defined in the scripts), the IntuneManagementExtension.log will yield following:
- [HS] lastLine of output = VPN profile version in registry matches the version configured in the script. Doing nothing
Additional details
When you want to deploy a new version of the VPN profile, simply do following:
- Update the $global:vpnProfileVersion variables in both scripts to a higher number:
- Replace the $global:VPNProfile variable in the Configure-VPNProfile.ps1 script with the updated and fresh rasphone.pbk configuration:
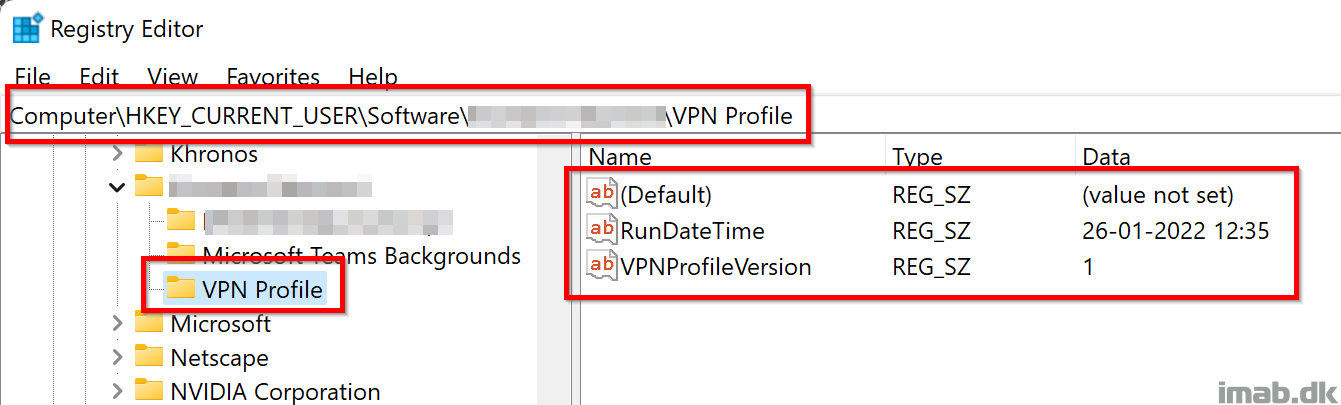
For your convenience, this is an illustration of the area in registry, which is used for version control of the deployed VPN profile:
ENJOY 🙂
Thank you very much! It is good to have a workaround.
The AOVPN issue with Windows 11 is a known issue, and it seems you described the root cause 🙂
https://docs.microsoft.com/en-us/mem/intune/configuration/vpn-settings-configure
Also I didn’t suffer the issue since yesterday… perhaps MS fixed the bug?
Wow, thank you for letting me know. That knowledge is new to me. I’ve had this issue since day 1, and back then there was no news about the cause.
Hi all,
Firstly – thanks for this great gudie Martin! 🙂
I have as of today, the same issues with Windows 11, things come and go 🙁
Luckily your solution works as a workaround 🙂
Ps. deployed as device, my PBK file is not in the path in your script but in a subfolder called “_hiddenPbk” ?!
I also stumbled up onto issues with removing VPN profiles in Win11. Seems also related to some vpn csp as per
https://directaccess.richardhicks.com/2020/08/24/removing-always-on-vpn-connections/
Also sometimes the EAP config is not applied when installing vpn with powershell, but not sure if thats related to this, but never had this issue with w10.
I thought it was meant to be fixed but still seeing the same issue on dev build Version 10.0.22538.1010
Multiple profiles deployed to W11 all show remediation failed yet they install and connect fine.
I opened a ticket Friday because according to Richard Hicks blog it was meant to be fixed in a previous build to the latest dev version and I still have issues.
Thanks for another great article.
The following registry key can be set to prevent Windows from overwriting the value of VpnStrategy.
HKLM\SYSTEM\CurrentControlSet\Services\RasMan\Parameters\VPNStrategyUsageDisabled DWORD = 1
Enjoy! 🙂
Any news or updates on this issue? When will MS fix this? We are still struggling with W11 autopilot machines that use always-on vpn.
The issue is still a thing, but should not cause any issue if delivering a VPN profile once and for the first time. See the note on the docs here: https://docs.microsoft.com/en-us/mem/intune/configuration/vpn-settings-configure