Introduction
Short and sweet: Back in May 2019, Administrative Templates in Intune went from preview to General Availability. Back then the feature was released with a list of 277 settings. Not much, huh?
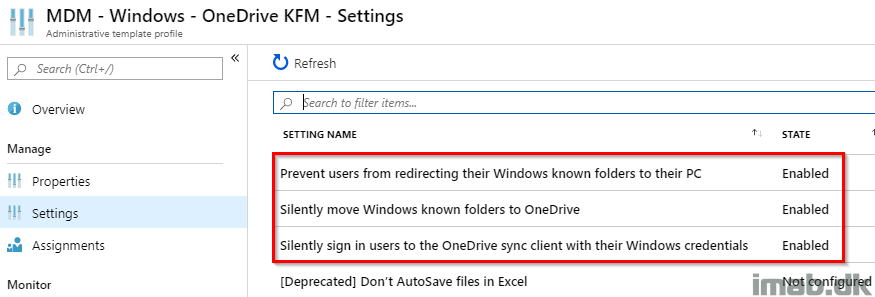
Today this will be extended by additional 2500 settings and among these will be the ability to configure OneDrive Known Folder Move. Exciting!
While the configuration of OneDrive Known Folder Move using Administrative Templates in Intune is pretty easy and straightforward, I figured it deserved a post here as well.
Also, initially when OneDrive Known Folder Move was introduced, I did this post on the topic: https://www.imab.dk/how-to-enable-onedrive-known-folder-move-using-sccm-system-center-configuration-manager/