Introduction
This post is long overdue and something I originally considered doing when I explained my Windows as a Service process.
The story is, that I allow In-Place Upgrades with Configuration Manager to happen over the Internet and over VPN. While I do allow upgrades over VPN, I still prefer them happening on local network and I certainly doesn’t want them to happen over LTE.
I use Powershell App Deployment Toolkit to initiate the Windows 10 In-Place Upgrade Task Sequence, and I wanted to add more user-friendliness to the experience, by notifying the end-user about possible VPN and LTE connections.
Note #1: LTE connectivity can be prevented altogether in the Client Settings, but I’m not doing that for various reasons. 🙂
Note #2: I do precache everything prior to making the upgrade available. Therefore download of binaries should be limited to zero, though the connection to the site server is still needed, as well as connection to the domain (depending on what you are doing throughout your task sequence).
- More WaaS posts: https://www.imab.dk/windows-as-a-service/
Powershell
The magic lies in 2 Powershell functions I created for the purpose.
Note: The functions have only been tested in my own environment, and depending on how you have setup your AlwaysOn VPN profile, you might need to modify the content a bit.
- Test-DomainVPNConnectivity
- Test-LTEConnectivity
Each function outputs the current connectivity to the screen as well as an output to be used later in PSADT.
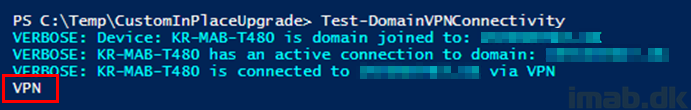
Below is an example of running the Test-DomainVPNConnectivity function manually. My production domain name is obfuscated, but the function recognizes that I’m currently connected through AlwaysOn VPN:
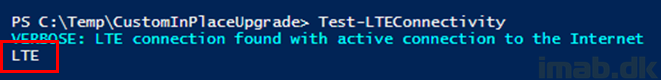
The Test-LTEConnectivity function does the same thing: Outputs the current LTE connectivity to the screen and for later use in PSADT:
function Test-DomainVPNConnectivity {
$computerName = $env:computername
$domainName = $env:userDNSDomain
if ($domainName) {
Write-Verbose -Verbose -Message "Device: $computerName is domain joined to: $domainName"
$domainConnection = Get-NetConnectionProfile | Where-Object {$_.Name -eq $domainName}
if ($domainConnection) {
Write-Verbose -Verbose -Message "$computerName has an active connection to domain: $domainName"
$interfaceAlias = $domainConnection.InterfaceAlias
$domainConnectionName = $domainConnection.Name
$domainConnectionCategory = $DomainConnection.NetworkCategory
if (($domainConnectionName -eq $domainName) -AND ($domainConnectionCategory -eq "DomainAuthenticated")) {
if (($interfaceAlias -like "Wi-Fi*") -OR ($interfaceAlias -like "Ethernet*")) {
Write-Verbose -Verbose -Message "$computerName is connected to $domainName via local network"
Write-Output "LAN"
}
elseif ($interfaceAlias -like "*VPN*") {
Write-Verbose -Verbose -Message "$computerName is connected to $domainName via VPN"
Write-Output "VPN"
}
}
}
else {
Write-Verbose -Verbose -Message "$computerName does not have an active connection to domain: $domainName"
Write-Output "NODOMAIN"
}
}
else {
Write-Verbose -Verbose -Message "Looks like that $computerName is not domain joined"
Write-Output "NOTDOMAINJOINED"
}
}
function Test-LTEConnectivity {
$lteInterface = "Cellular"
$lteDetails = Get-NetConnectionProfile | Where-Object {$_.InterfaceAlias -eq $LTEInterface}
if ($lteDetails) {
if ($lteDetails.IPv4Connectivity -ne "Internet") {
Write-Verbose -Verbose -Message "LTE connection found, but NO access to the Internet"
Write-Output "LTE"
}
elseif ($lteDetails.IPv4Connectivity -eq "Internet") {
Write-Verbose -Verbose -Message "LTE connection found with active connection to the Internet"
Write-Output "LTE"
}
}
else {
Write-Verbose -Verbose -Message "No LTE connection was found"
Write-Output "NOLTE"
}
}
Powershell App Deployment Toolkit
So how do I use that with the Powershell App Deployment Toolkit?
For your downloading pleasure, I have made the entire PSADT project used available for download here: PSADT_TestConnectivity.zip (5632 downloads )
I have made a custom region paragraph within the Deploy-Application.ps1 file which contains the custom code. I hope most of this is self explanatory, assuming you have some sort of experience with PSADT already:
$TestLTEConnectivity = Test-LTEConnectivity
$TestDomainConnectivity = Test-DomainVPNConnectivity
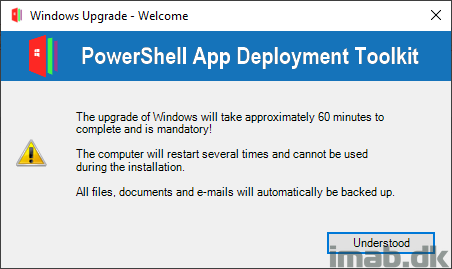
$IPUMessage = "The upgrade of Windows will take approximately 60 minutes to complete and is mandatory!`n`nThe computer will restart several times and cannot be used during the installation.`n`nAll files, documents and e-mails will automatically be backed up."
$Answer = Show-InstallationPrompt -Title 'Windows Upgrade - Welcome' -Message $IPUMessage -MessageAlignment Left -ButtonRightText 'Understood' -Icon Exclamation
if ($Answer -ne “Understood”) {
Exit-Script -ExitCode 1618
}
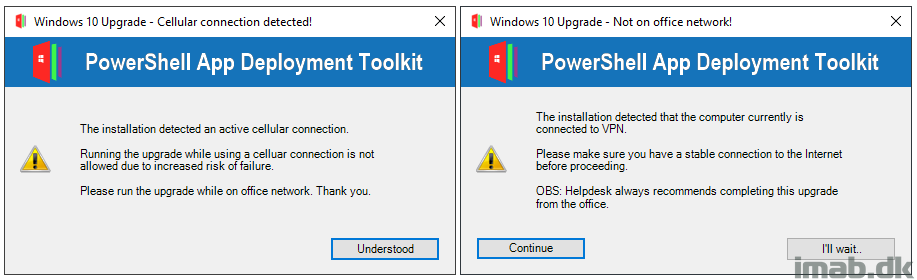
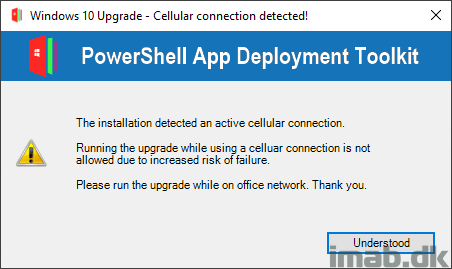
if ($TestLTEConnectivity -eq "LTE") {
$LTEMessage = "The installation detected an active cellular connection.`n`nRunning the upgrade while using a celluar connection is not allowed due to increased risk of failure.`n`nPlease run the upgrade while on office network. Thank you."
$Answer = Show-InstallationPrompt -Title 'Windows 10 Upgrade - Cellular connection detected!' -Message $LTEMessage -Icon ‘Exclamation’ -MessageAlignment Left -ButtonRightText "Understood"
if ($Answer -eq “Understood”) {
Exit-Script -ExitCode 1618
}
}
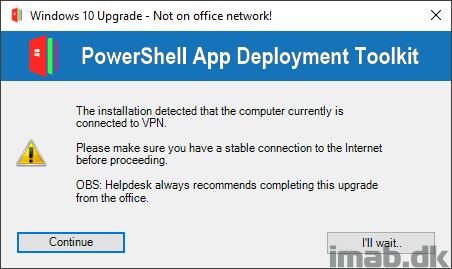
if ($TestDomainConnectivity -eq "VPN") {
$DomainMessage = "The installation detected that the computer currently is connected to VPN.`n`nPlease make sure you have a stable connection to the Internet before proceeding.`n`nOBS: Helpdesk always recommends completing this upgrade from the office."
$Answer = Show-InstallationPrompt -Title 'Windows 10 Upgrade - Not on office network!' -Message $DomainMessage -Icon ‘Exclamation’ -MessageAlignment Left -ButtonLeftText ‘Continue’ -ButtonRightText "I'll wait.."
if ($Answer -eq “I'll wait..”) {
Exit-Script -ExitCode 1618
}
}
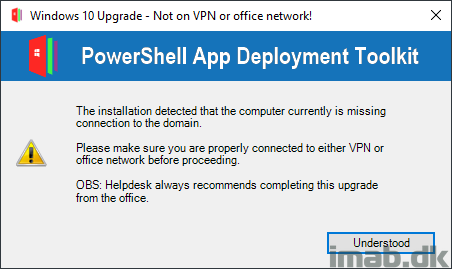
if ($TestDomainConnectivity -eq "NODOMAIN") {
$DomainMessage = "The installation detected that the computer currently is missing connection to the domain.`n`nPlease make sure you are properly connected to either VPN or office network before proceeding.`n`nOBS: Helpdesk always recommends completing this upgrade from the office."
$Answer = Show-InstallationPrompt -Title 'Windows 10 Upgrade - Not on VPN or office network!' -Message $DomainMessage -Icon ‘Exclamation’ -MessageAlignment Left "Understood"
if ($Answer -eq “Understood”) {
Exit-Script -ExitCode 1618
}
}
Results
- Initially when PSADT is run, the user is greeted with this first welcome message:
- If PSADT detects that the user currently is connected through a LTE connection, the user is notified and the installation is prevented:
- If PSADT detects that the user currently is connected through VPN, the user is notified and given the option to wait or continue:
- If PSADT detects that the user currently is not connected to either VPN or office network, the user is notified and the installation is prevented:
- This is a scenario that might turn relevant if one are using a Cloud Management Gateway, and the device is not on VPN and not in the Office.
ENJOY 🙂
Hi! Great work! Is this the same way you prevent precaching via LTE or VPN? Do you run precaching task sequence required and run these PoSh-Script before task sequence is executed?
Dietmar
Hi and thanks! I don’t allow precaching over VPN nor LTE, and I prevent that through the boundaries and boundary groups 🙂
Whaaat? This is what I need too. How to prevent the execution of a task sequence with boundary groups?
It’s not the TS per say you prevent executing, it’s content download which cannot happen when the client falls out of the boundaries configured. When my clients are connected through alwayson vpn, they fall into a specific boundary group with no relationship to a DP and thus the precaching cannot happen 🙂
Thanks for clarification! However, this way your clients will never ever install updates or missing but needed software via memcm? Right?
BTW… Your blog really cool!
The individual deployment options can bypass that, and for instance be allowed to grab content from a neighbor DP or even from the default site boundary group. So by default, clients on VPN is not allowed to download content unless you explicitly allow it on the deployment.
I sense that you have associated a DP or included your VPN client into a boundary group which has a DP associated? 🙂
Ah, now I understand your thoughts. Perfectly fine! This is exactly what we need. We own ~2000 notebook and we currently switch from DirectAccess to AlwaysOn VPN. So this post and your comments come at just the right time. ? There is something to learn every day…
Fortsæt med det store arbejde!
As Always great work Martin!
Thank you! 🙂