Introduction
This is not exactly an A-Z guide on the topic, but rather a story of my experiences with upgrading Windows 10 over the Internet with In-Place Upgrade (IPU) Task Sequence using ConfigMgr and how it works in my environment.
I’m using a Cloud Management Gateway (CMG) with enhanced HTTP as well as initially being connected to the on-premises infrastructure with Always On VPN. The VPN in this scenario is a user-initiated tunnel and thus obviously disconnects once the upgrade restarts the computer. It’s not completely without challenges and I will try to cover those during this post.
Curious? Read on 🙂
Oh yeah, seeing I now allow IPU to happen over the Internet, I also created something in Powershell App Deployment Toolkit which extraordinarily warns the user if the upgrade is being initiated from outside the office network. A preview of that in the end of the post 🙂
Pre-Cache Content
If precaching content wasn’t considered mandatory already, making in-place upgrades available over the Internet surely does so.
In my opinion there’s absolutely no reason to make IPU available over the Internet, if content isn’t precached already, other than providing the end user with a horrible experience. We don’t want to do that 🙂
I have previously gone into details on the precaching part here: https://www.imab.dk/windows-as-a-service-sharing-my-precache-and-in-place-upgrade-task-sequences-part-1/
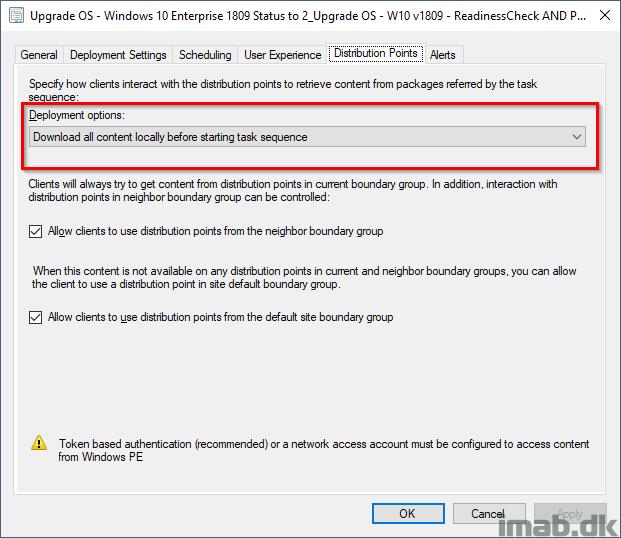
As I said, precaching is MANDATORY. When making IPU available through the Cloud Management Gateway, the task sequence is REQUIRED to be deployed with ‘Download all content locally before starting task sequence’. If content isn’t on the client already, you do the math. The complete download can take hours depending on Internet speed etc.
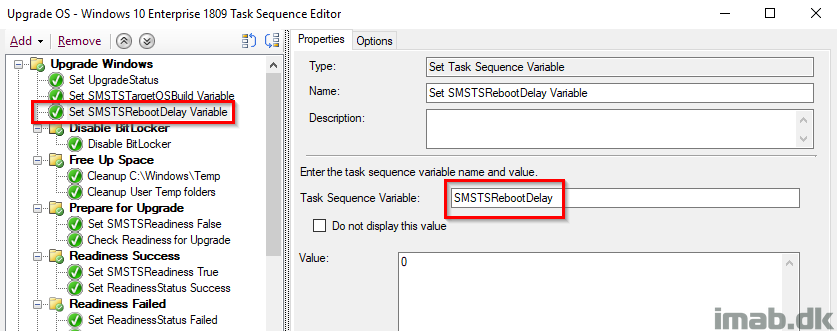
SMSTSRebootDelay
Time is precious. During my testing I realized how much time I spent watching a countdown to complete. The Windows setup still initiates a few reboots and each is being count down from 15-20 seconds.
Prevent that and any delays from any reboot during the task sequence by setting SMSTSRebootDelay to 0 (zero).
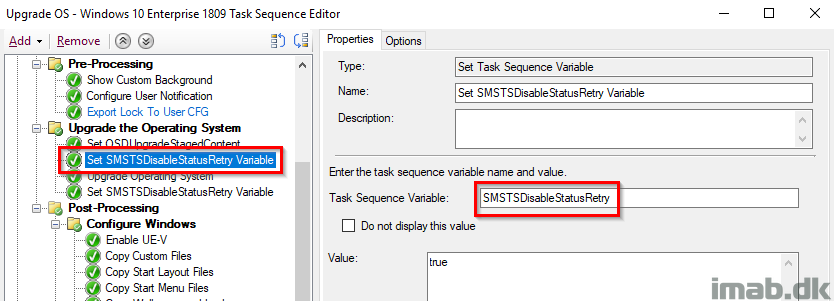
SMSTSDisableStatusRetry
This might cause some wondering for some, but remember that in my scenario I initially have a user-centric Always On VPN tunnel active, which is being disconnected during the first reboot. From there the SCCM client switches to Currently Internet and connects to the Cloud Management Gateway and I’ve seen some waiting here and there for status messages to be sent back to the CMG.
This is also to cater for poor private wifi connections. I want the highest chance of success, regardless of Internet connection.
Important: For now I set it twice. Once before the Upgrade OS step and once after. The first because this is where my VPN disconnects and the SCCM client doesn’t switch to the CMG instantly. The second due to the nature of the step, where the variable will be ignored after a reboot in case a status message is sent successfully. Read more here: https://docs.microsoft.com/en-us/sccm/osd/understand/task-sequence-variables#SMSTSDisableStatusRetry
Now, the second time is being set conditionally if the current Management Point is the Cloud Management Gateway. This is done to only skip status messages if the client indeed is being upgraded from the Internet and possibly will be done so from a crappy connection.
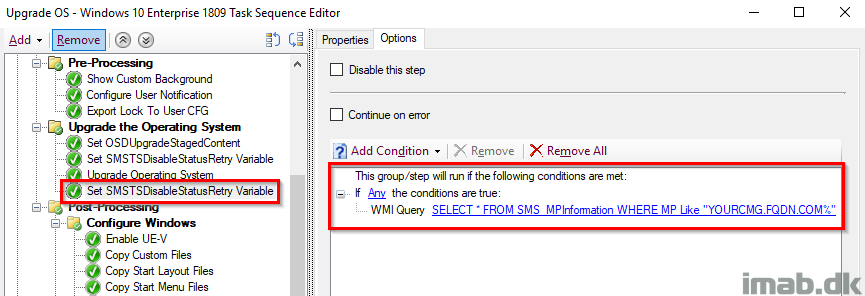
Additional Steps
This is more of a inspirational section, and will vary a lot depending on what your task sequence looks like.
During my usual IPU task sequence, I do stuff which is only possible if the client is inside local LAN/or have an active VPN tunnel. For one I manage groups in the local Active Directory through a web service. That is not possible for a Internet client through the Cloud Management Gateway without exposing the web service to the Internet, so that’s something to consider as well.
I have solved that by running steps conditionally and only manage AD groups if the current Management Point is my local Management Point.
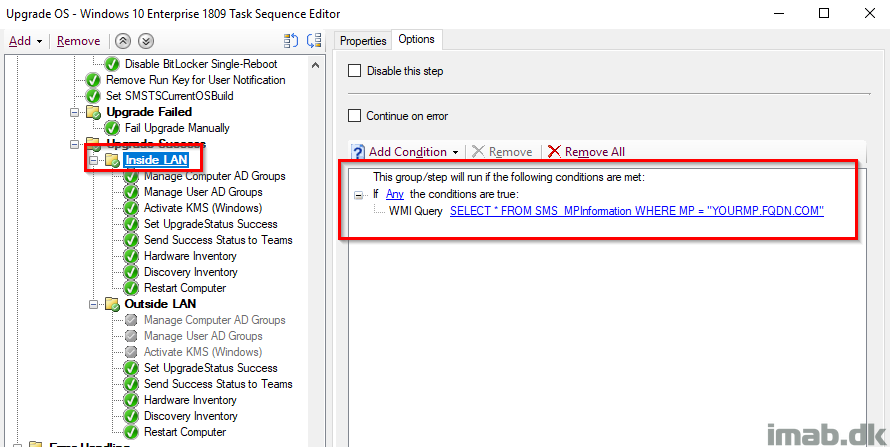
And another step conditionally to only run if the CMG is acting as Management Point and the client thus is being considered on the Internet.
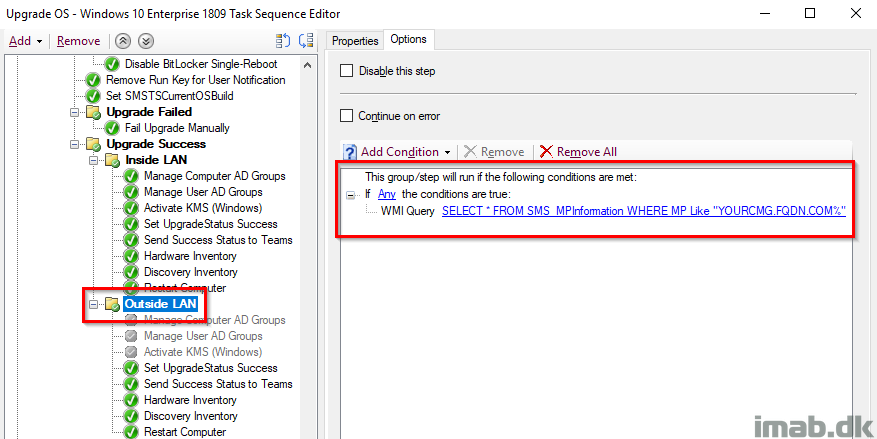
Deployment
The task sequence is being deployed with the option ‘Allow task sequence to run for client on the Internet‘, allowing the TS to actually run regardless of my VPN connection being active or not.
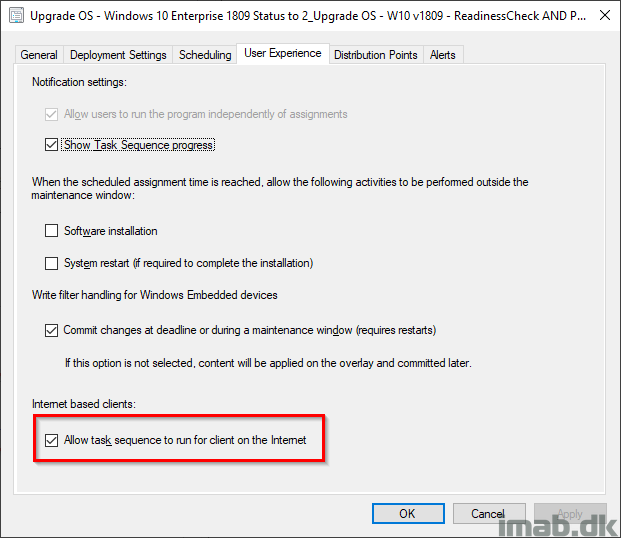
More details
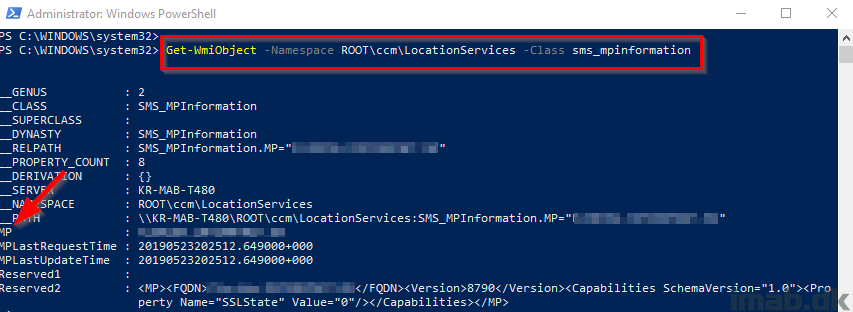
You can get the Management Point details from WMI running following Powershell:
Get-WmiObject -Namespace ROOT\ccm\LocationServices -Class sms_mpinformation
Get-WmiObject -Namespace ROOT\ccm\LocationServices -Class sms_activempcandidate
Logging
While working through all of this, there are a bunch of useful logs to investigate:
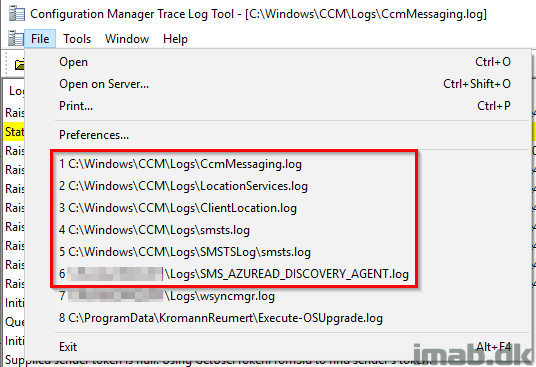
CcmMessaging.log
LocationServices.log
ClientLocation.log
smsts.log
Powershell App Deployment Toolkit preview
I use PSADT with an application to initiate the In-Place Upgrade task sequence. Though my content have changed slightly since then, you can find more on that here: https://www.imab.dk/how-can-i-in-place-upgrade-to-windows-10-1803-using-powershell-app-deployment-toolkit-and-sccm-system-center-configuration-manager-part-2/
- The initial welcome message.
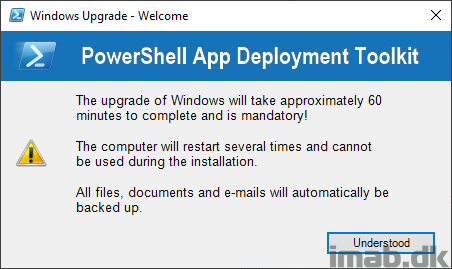
- If installation is initiated outside of office network, below message is shown, allowing the user to continue or wait.
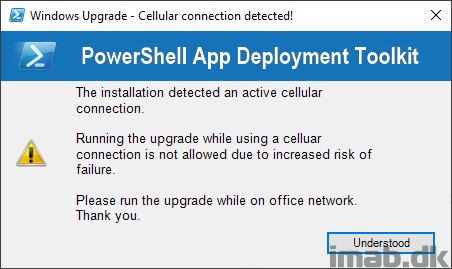
- If the installation is initiated from a cellular/LTE connection, I currently prevent that with below message.
Hit me up if you need something elaborated – enjoy 🙂
How do you detect the LTE connection in your PSADT?
Hey Bo, I created my own Powershell function to detect that using Get-NetConnectionProfile 🙂
hi Martin,
can you please share a short guide on how did you create the function Get-NetConnectionProfile and how did you use it in PSADT?
i am not an expert in powershell 🙂 but i am using PSADT for my deployments and this is very useful to use it with windows 10 feature upgrades.
thank you
Thank you very much for the article. Is it possible for you to share your task sequence? We are about to push out the in-place upgrade where most users will be on VPN because of COVID-19. Our Windows 10 1709 will be out of support in April. Also, is your CMG configured with HTTPS?
Will it be possible to have the script you are using to send messages to Teams?
Absolutely. I will share it with you as a reply to your e-mail regarding bitlocker 🙂
Hi Martin,
I’m so happy I’m not the only one struggling with this scenario. I have AOVPN and have been testing IPU with CMG. My biggest struggle has been reporting. I’m confident that IPU works properly with the pre-cache and that the upgrade will complete correctly but how do I prove it? I’ve been messing with setting a custom regkey that I extended hardware inventory to capture but have mixed results with that. I’ve got over 5000 endpoints, all off site, that I need to upgrade and a good report will make everyone feel better. Any sort of guidance would be greatly appreciated!
Hello, Thank you very much for this article ! do you know if the status messages are well sent through the CMG ?
I have tested a task sequence on CMG but there is an error in the log file saying :
Failed to send status message (80004005)
When checking on google, i’m not the first :
https://twitter.com/PaulWetter/status/1138847751205281795
Thank you
Can you provide the the script or command to send success status messages to teams.
Thanks in advance.
Hi,
It is very inspiring article.
I’m not in a comfortable situation as I cannot use MP on DMZ nor the CMG.
Once the device is disconnected the TS is running fine, but of course the status is not being updated in SCCM.
To workaround it I have made quite complex script that checks the result of the TS, as well as remediate some possible problems. It is scheduled to run after the user logs in for the first time when upgrade is ready, or failed, and the VPN connection is established. My problem is still the TS result in SCCM is “In progress”.
I was looking for a solution to that but I cannot find any.
I was thinking about following:
1. Start the TS again from my script, after user logs in and bypass all the steps based on the condition that the system is already running new version, exiting it with a success (or failure depending what is the real output from the real run).
2. Pausing somehow the TS at the last step and wait for the user to log in (have no idea how to do that, how to display the logon page). But what I have noticed is that once the McAfee encryption is on, and the PIN requirement doesn’t allow the device to finish the TS, the status messages are delivered. How to get the logon screen without finishing the last step of the TS?
We have followed your articles regarding WaaS while configuring our task sequences and they have been a tremendous help, thank you. We are getting prepared to leverage our CMG for our PreCache TS. Now that we are all working from home, we realize the importance of leveraging the CMG and would like to put it to good use.
My question is regarding the content in our PreCache TS on the CMG. Am I correct in understanding that once we distribute our PreCache TS to the CMG, it will also distribute all content within the TS to the CMG? All packages and OS upgrade packages will reside in the CMG as well, correct? You can’t pick and choose what goes to the CMG for the precache, can you? I figure that would defeat the purpose of leveraging the CMG for our PreCache TS.
We will be deploying our precache silently and hidden, so the users won’t be aware. Our concern is if we do not leverage the CMG and users happens to disconnect from VPN while the TS is downloading or running, the precache TS would end up failing.
Currently our TS is roughly 15 GB of data and we are concerned about the cost. I’m just trying to understand the process better so that we know how to go to our manager with this particular ask.
I’m still trying to wrap my head around determining the cost which doesn’t appear to be an easy task. 🙂
Thanks so much!