Introduction
My Windows 10 Toast Notification Script has received another update, now being on version 1.4. What’s new and delicious are mentioned in details below.
Note: I know that expiring passwords are not ideal, but reality is that many still have them configured like so while trying to find their way out with Windows Hello for Business, Password-Less etc.
The toast notification might even serve as a good entry point into enrolling into WhFB when one are ready to do so. I’ll make an example of such in the future 🙂
- Find the original page for the Windows 10 Toast Notification Script here: https://www.imab.dk/windows-10-toast-notification-script/
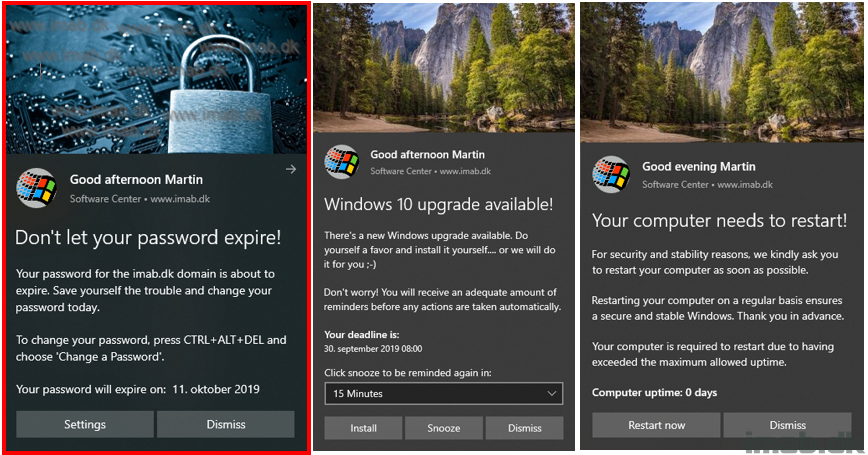
What’s New
- 1.4 – Added new feature for checking for local active directory password expiration
- If the password is about to expire (days configured in config.xml), the toast notification will display reminding the users to change their password
- Using this feature requires the ActiveDirectory powershell module. Note: This might not be allowed everywhere. Working on alternatives 🙂
- The function will try to import the AD powershell module, look up the user’s SamAccountName and use that with the Get-ADUser cmdlet
- If the password is about to expire (days configured in config.xml), the toast notification will display reminding the users to change their password
- 1.4.1 – Get-ADPasswordExpiration function modified to not requiring the AD Powershell module. Thank you @ Andrew Wells
- Improved logging for when no toast notifications are displayed
- More commenting
- 1.4.2 – Bug fixes to the date formatting of ADPasswordExpiration now correctly supporting different cultures
Config.xml
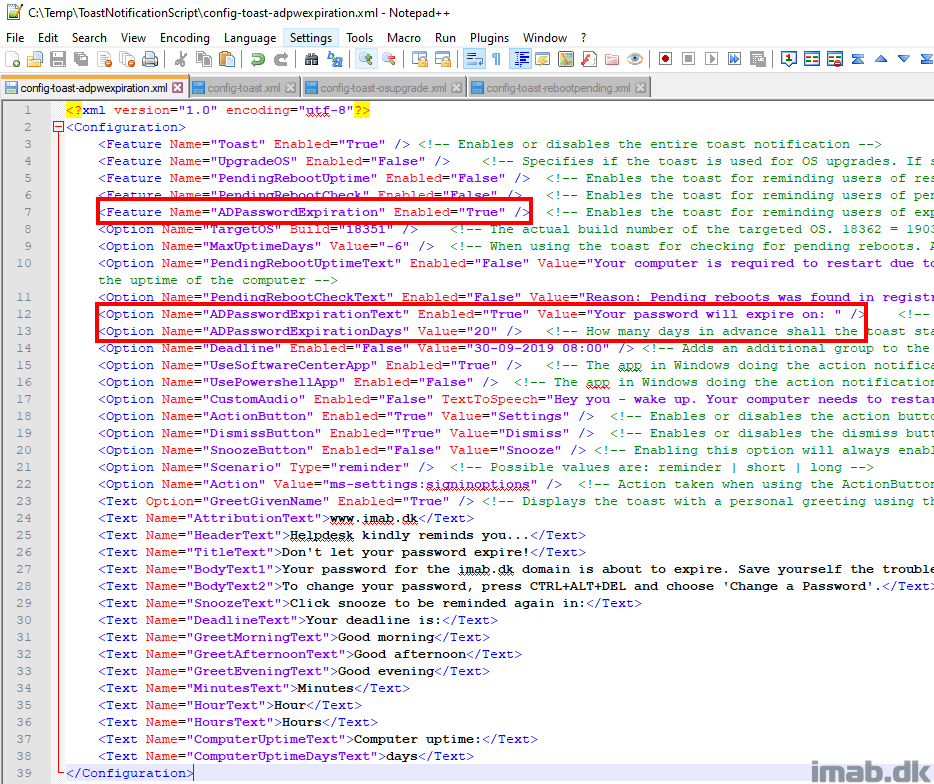
I have highlighted the new additions to the config.xml file in below illustration.
To enable the new feature, simply configure ADPasswordExpiration to Enabled=”True” as shown below.
ADPasswordExpirationText enables an extra text element displaying when the password is set to expire.
ADPasswordExpirationDays is the amount of days before expiration that the toast notification will start displaying for the user.
Perhaps use: net user USERNAME /domain to grab the password expiration date, for those that can’t use powershell for each client.
Great content.
Yeah, I considered that, but took the choice of sticking with pure powershell. Imma work something out 🙂
Is it possible to prevent clearing the notification, I removed the dismiss button but you can still click the notification and it disappears.
Great Tool
thank you
Hey, no I’m afraid that’s the nature of Windows and is not related to the script 🙂
How about an option for a “More Info” button, that would open a web page to an intranet knowledge base.
Ye that’s doable. Configure the action button like this: Option Name=”Action” Value=”microsoft-edge:https://yourwebpage.com“
Will this work for cloud managed win 10 devices…ie not adds joined?
We have adds synced to aad and all user objects are there but no computer objects are in adds.
All managed out of intune
This part of the script requires a regular on-premises Active Directory 🙂
Hey, was wondering if there was an easy way to modify the script to show the exact password expiration date/time in the toast instead of just the date. I see that you display it in the log using $ExpiryDate, but I tried to replace that in the toast notification and it doesn’t display. Thoughts?
Hey John, that should be possible I’m sure. My password doesn’t have an expiration date, so I don’t have a quick way of testing without creating a test user. If I have some spare minutes tomorrow, I will try and remember to have a look. 🙂
Amazing Job man 🙂
It seems like the toast only shows once, right? If so, is it possible to configure to show the toast every other day or during every login?
Thanks 🙂
That depends on how you run the script. If run with configmgr, your schedule decides how often the toast is shown. So yeah, it’s definitely possible to have it to display whenever you want 🙂
hi there,
When the toast notification shows up, I see there’s a button available for users to turn off software center notifications. Is there a way to disable that?
Yes, issue is that, that setting is stored in AppData\Local\Microsoft\Windows\Notifications\wpndatabase.db.
If a notification hasn’t been sent (since the user disabled it), there’s maybe a (of course not supported) way: stop the service WpnUserService, delete/rename the wpndatabase.db file, delete the regkey “HKCU:Software\Microsoft\Windows\CurrentVersion\Notifications\Settings\Powershell” and restart the service again – a new db file is created and afterwards the notification can be sent successfully. Disadvantage of course: most of the notification settings are lost. Basically the old/renamed db file could be written back to get the settings back.
Is there a way to tweak this script to work with AD Account Expiration Date rather than AD Password Expiration date?
We have users that do not often connect to VPN. Is is possible to get this working with AAD?
At least to check the password age and possibly notify them to connect to VPN?
The password expiration function only works with onprem AD. The assumption and recommendation is, that password never expires. You can create something with either Intune or ConfigMgr, that finds devices where VPN is disconnected and display them a toast notification instructing them in using VPN more often. Let me know if you need some inspiration on the latter. 🙂
Yes we are struggling with some users not connecting to the VPN often enough and as such the user and computer account passwords are not updated before they expire. In the case of either the user can no longer VPN in if the account password has expired. The systems are all hybrid joined and we have the CMG and Azure storage to push out deployments such as this. Do you have any ideas on how this can be checked on devices that are not connected to the corporate network and display a notification based on it? Is it possible to see the last password change for the computer or user account locally?
Yeah, you can query the active net adapters using powershell to see if any of them are connected to the corporate lan. If not, return a value which you can act on and display a toast notification. It’s doable alright 🙂
Unfortunately that won’t work because we are not trying to force them to remain connected to VPN all the time. I am just trying to remind them to connect when the password is near expiration. Do you have any other ideas?
Hi Marin
Thank you for the notification PowerShell script. Working as expected..
If we donot have SCCM in the environment, how can I execute the .\New-ToastNotification.ps1 -Config .\config-toast-adpwexpiration.xml. Thank you in advance
This is great. Can you have a button perform an action, like CTRL+ALT+DEL? Assuming we’ll need to custom call that or build in the New-ToastNotification.ps1.
Good Morning,
Is this only used for devices enrolled in SCCM, or can it be used for Intune devices.