Introduction
CMPivot is a utility which was introduced with SCCM 1806 (System Center Configuration Manager).
In short, it’s a utility which enables us to query all currently connected devices for information in real-time.
This is extremely useful in a variety of situation, where a great example of such will be in case of a malware outbreak.
In case of a malware outbreak, a lot of questions becomes relevant to answer quickly:
- How many devices are infected?
- Which devices are not infected?
- Are the malware spreading?
- etc.
CMPivot to the rescue!
WannaCry?
For the sake of the example, I’m going to use threat indicators from the infamous WannaCry ransomware. Unless you have been hiding under a rock, everyone should be familiar with WannaCry at this point 🙂
Handpicked threat indicators out of many:
- Windows Service
- Running Process
- Files
- Registry entries
- Software in Run
Windows Service
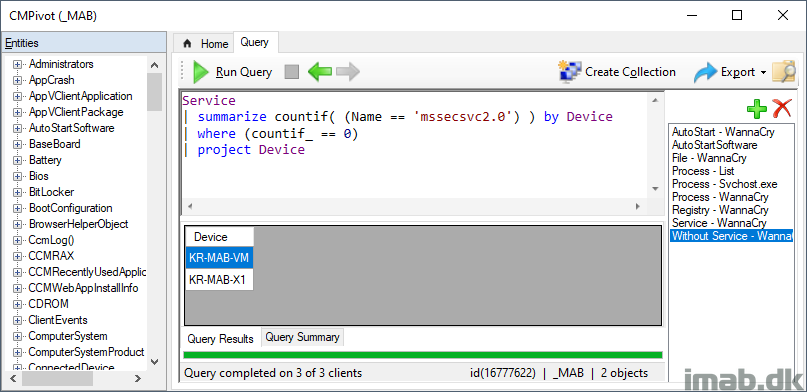
WannaCry installs a service onto the infected system called Microsoft Security Center (2.0) Service (mssecsvc2.0). You can use below query to locate all devices with this service in question:
Service | where Name == 'mssecsvc2.0'
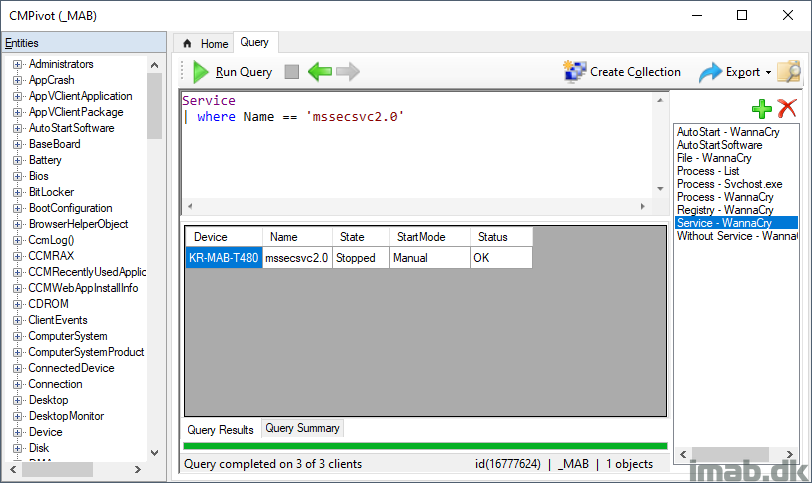
You can also do the opposite, and locate all devices not yet infected with the service and run following query instead.
Note: This can be very handy if you want to target the devices not yet infected with some sort of kill switch.
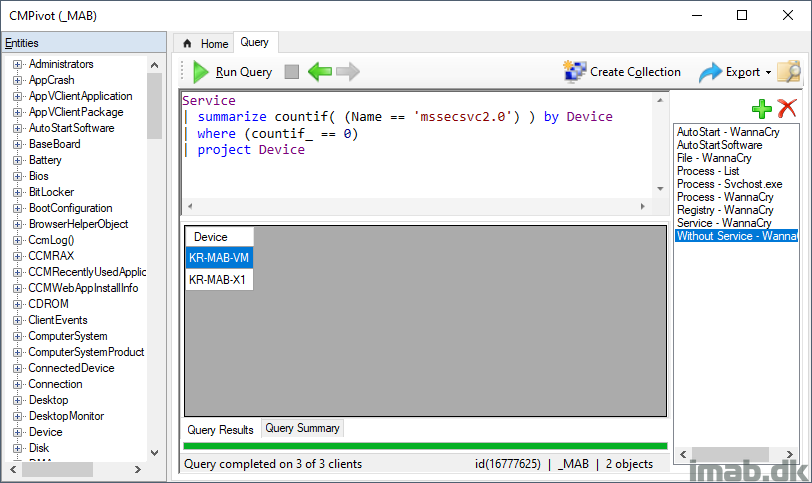
Service | summarize countif( (Name == 'mssecsvc2.0') ) by Device | where (countif_ == 0) | project Device
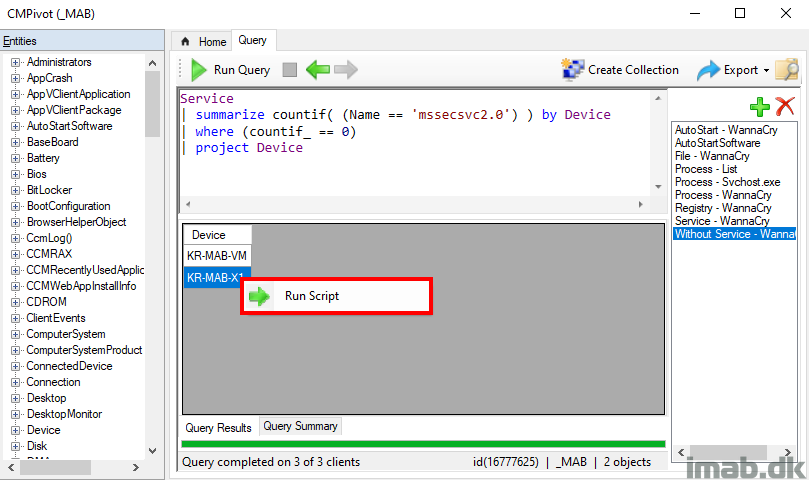
When right clicking the devices in the Query Results view, you will find the option to Run Scripts.
This is the option to use, if you want to target the devices right here and right now with some sort of action.
Those familiar with Microsoft Defender ATP knows that MDATP has an option to isolate the machine preventing it from further spreading the malware. You have the option here to script something similar, blocking all traffic in the Windows Firewall except ConfigMgr or simply disable all network adapters if the heat is on:
Get-NetAdapter | ? Status -eq Up | Disable-NetAdapter -Confirm:$False
Running Process
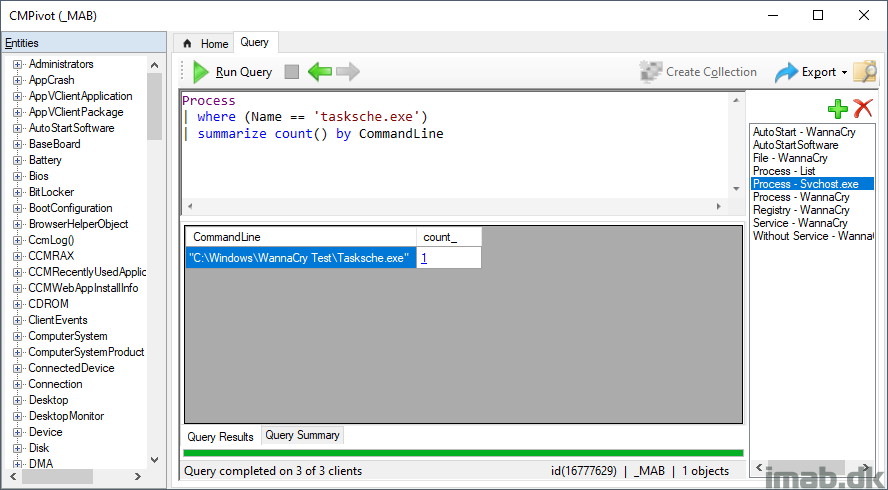
WannaCry obviously also leaves some processes running, one of them being tasksche.exe closely resembling the well-known taskschd.exe. Find devices where this bad process is running by running following query:
Process | where (Name == 'tasksche.exe') | summarize count() by CommandLine
In this example, I’m also counting how many devices as well as summarizing on the commandline.
Specific File
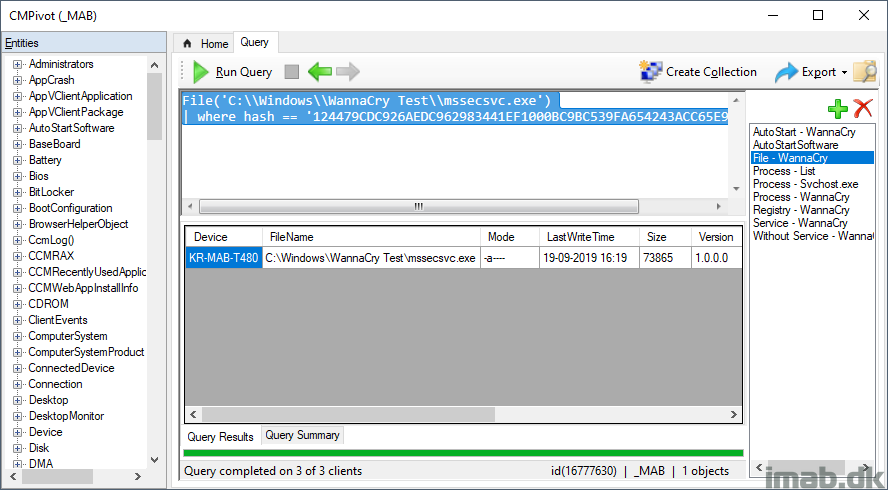
Further to being specific about WannaCry, WannaCry also leaves behind a bunch of files. You can locate devices having very specific files stored using below query. This query will find THE file matching on the hash value.
Note: This might prove really useful if the actual malware haven’t been executed for whatever reason, but only the payload delivered. This means there’s a fighting chance to stop it before hell breaks lose 🙂
File('C:\\Windows\\WannaCry Test\\mssecsvc.exe')
| where hash == '124479CDC926AEDC962983441EF1000BC9BC539FA654243ACC65E9EC962DCA60'
Registry Entries
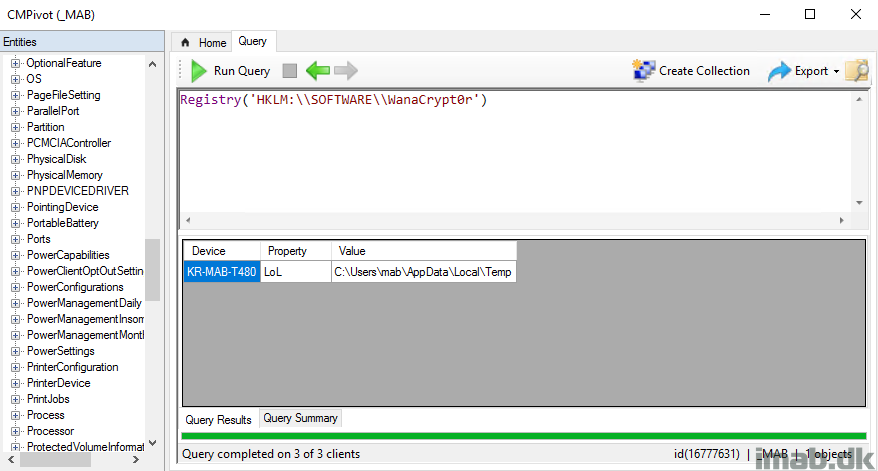
No malware without altering the registry. This simple query will find devices where the specific registry key exists:
Registry('HKLM:\\SOFTWARE\\WanaCrypt0r')
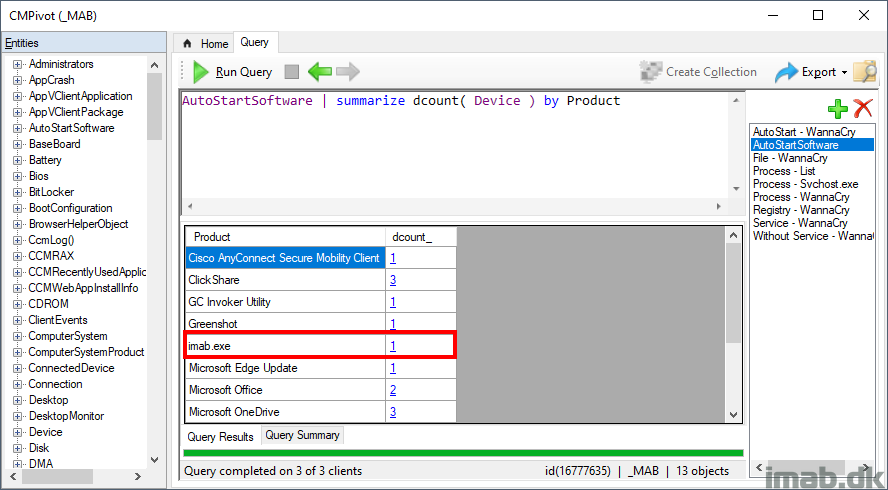
AutoStart Software
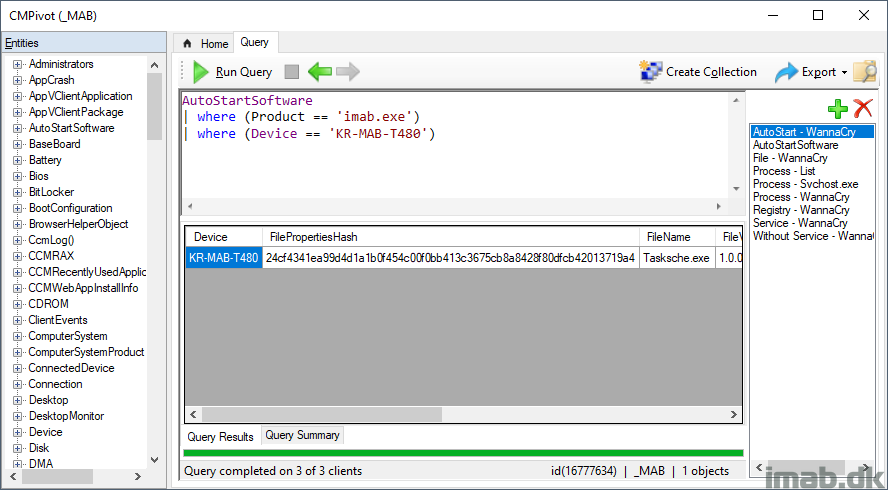
A lot of malware including WannaCry puts their doings into Run of Windows. As of such, it’s quite relevant to track down what and where is automatically being run with Windows. Do so for a specific device, for a specific product using this query:
AutoStartSoftware | where (Product == 'imab.exe') | where (Device == 'KR-MAB-T480')
Or get all software being automatically run with Windows for all devices in the collection using this:
AutoStartSoftware | summarize dcount( Device ) by Product
Hit me up in the comment section down below if any questions.
ENJOY 🙂
Awesome example of CMPivot and whilst hopefully not for WannaCry does show the power that can be leveraged by this tool with some excellent samples that we can re-use in our own environments.
Thank you Andy 🙂