Introduction
In line with traditional practice on my blog, I’m kicking off my posts with an introduction – this time is no different.
The topic is something new however, and that’s even though I have been a frequent SCUG.DK attendee the past many years. I don’t dare to make a promise about making this an habit either, but I do think this event in particular deserves a written summary. So here goes my very first of it’s kind; the summary of SCUG.DK Fall Edition starring David James also known as @djammmer on Twitter.
And by the way, I’m not used to doing summaries – so please bare with me if I missed something obvious. I took notes and did a lot of pictures while tweeting live from the event, so there’s a slight chance I missed out on a thing or two. Apologies in advance.
Also, during this event there was a dedicated request to do tweets with the #MMSMOA hashtag for the chance of winning a trip to MMS 2018 Desert Edition, so if browsing Twitter for interesting Tweets, you will find some of them located on both #SCUGDK and #MMSMOA. 🙂

Event Sponsor
The event was sponsored by 1E.com and they delivered a world class session on their product 1E Tachyon: Next Generation Endpoint Investigation, Mitigation & Remediation

1E launched their entire presentation with these three poking questions on IT security:
- When a breach occurs, can your teams respond immediately and remediate fully, at scale?
- Do you know all of the software that your business is running, whether good or bad?
- Do you know if all the software in your business is current, patched and secure?

1E continued their presentation and before heading into the demo of their software, 1E asked another great set of questions:
Are you happy with 80% patch compliance? Would you leave your front door 20% open?
Moving on to the demonstration of Tachyon, 1E presented the ability to do following operations related to a breach in a very short amount of time:
- Listing running software in less than a second
- Listing devices with active connection to the bad IP address
- Isolating the device with connection to the bad IP address
- Search for executable files based on hash value
- Deleting the malware files
- Blocking connections to the bad IP address by adding rules into the Windows Firewall
I did do a few pictures during the presentation, but regardless of me being front row, I don’t think the pictures themselves displays it very well. However, below picture is taken from the client being isolated and therefore no longer has access to the Internet and thus unable to do more harm to the environment.
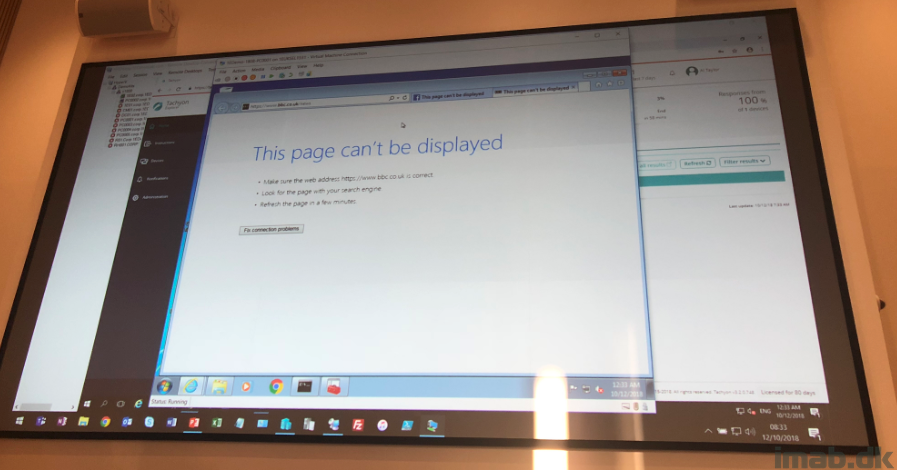
David James
On to the main event and the fact that David James was touring the SCUG (System Center User Group) meetings in the Nordic countries. As seen on below pictures, David James brought some real crazy and impressive Powerpoint skills.
Joking a side, the lack of creativity in the Powerpoint presentation was indeed made up for in the actual content, which I think is a deliberate choice made by David. 🙂
Following part is some of the most interesting topics made by David James during his presentation at the SCUG.DK meeting, Fall Edition 2018.

First off, a short introduction of the man himself:

And then David turned the tables and started asking the crowd questions, which continued throughout the session and made the entire session really really worthwhile. David, being the IT professional he is, referenced this as telemetry. I believe most IT pros will recognize the reference to telemetry here 🙂

But before moving on, David presented us for the most asked and common question and statement he hears all the time: “Is SCCM dead?” and “SCCM is dead!”
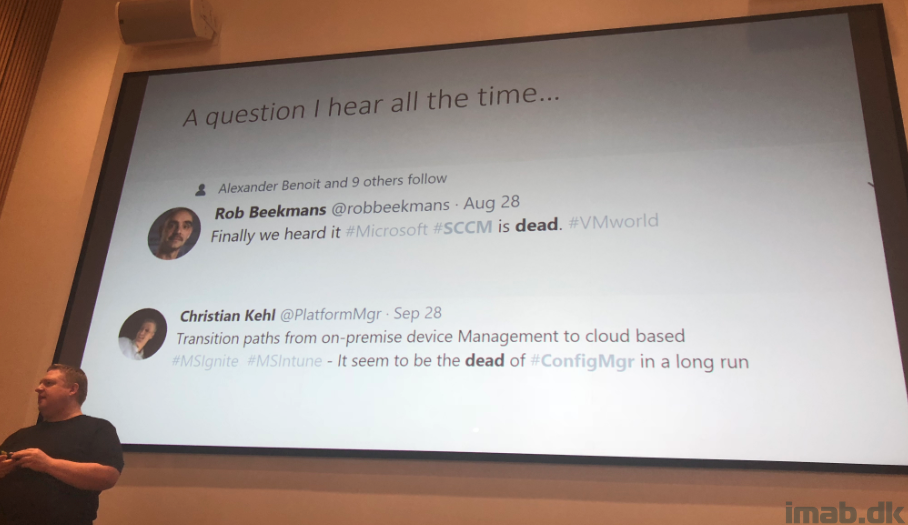
Which David in return answered with following statements:
- SCCM can only support X digit build numbers – it dies when the build is getting too high 😀
- TP (Technical Preview) releases every month last 12 month
- Team twice as big as 12 months ago
- SCCM is not going away!
Quote David James: “SCCM and Intune isn’t about either or – it’s about using the best of both worlds”
Moving further into the presentation, David built his presentation on some initial knowledge about Moore’s law: Moore’s Law is the observation made by Intel co-founder Gordon Moore that the number of transistors on a chip doubles every year while the costs are halved.
Moore’s law translates into the fact that computers are getting faster and cheaper, but still needs management and security.

After the introduction to Moore’s law, David started talking about telemetry on what’s being collected in SCCM and how the team uses the various information for decision-making.
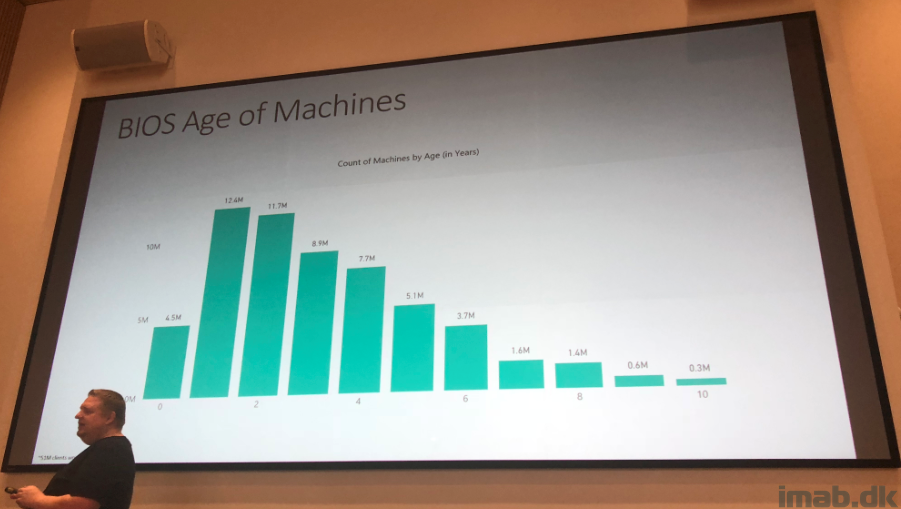
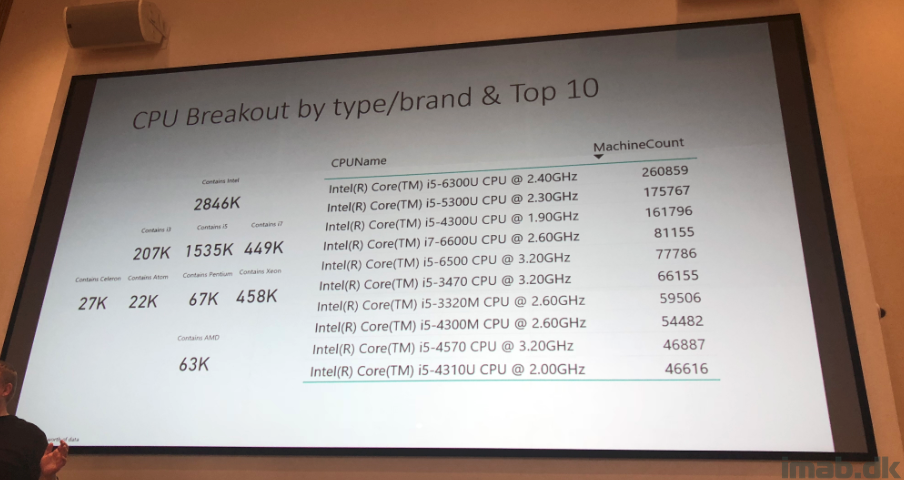
David then continued on how they leverage the cloud to respond to some of the obstacles that Moore’s law is giving us all. I will let the picture do the talking:

David finished off before the lunch break, by displaying some raw numbers on the SCCM side of things.

And David continued the interesting statements after the lunch break, getting the attention of the audience with this exciting slide:
- ConfigMgr should work faster
- ConfigMgr should work everywhere
- ConfigMgr should harness the power of the cloud
- ConfigMgr should harness the power of the community

And then displaying how SCCM has evolved on the faster part:
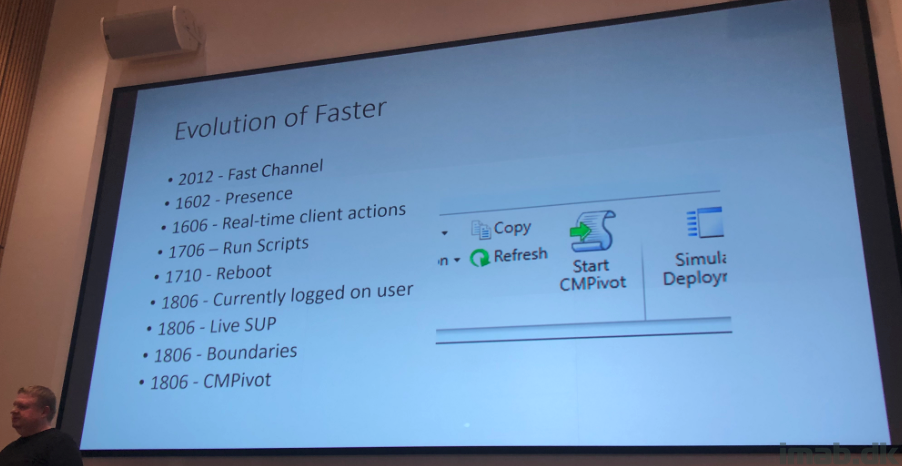
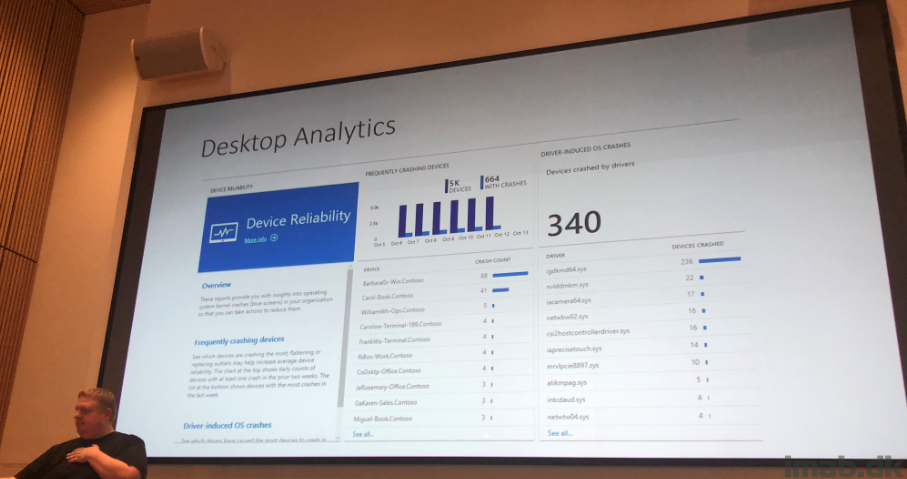
Finishing off the day with briefly touching base with Desktop Analytics which will be an expansion of Windows Analytics as we know it.
Quote David James: “Do you want to know which users keeps crashing Excel because they need 64GB of RAM?”
Wrap-up
This concludes my very first summary of a SCUG.DK event. A lot of pictures are displayed in the post, and that’s because I believe pictures in this regard does a much better job in telling the story than plain text.
David James is a real treat to listen to and I’m looking forward to meeting him again.
If you made it this far – thank you for reading. Let me know if this was useful 🙂