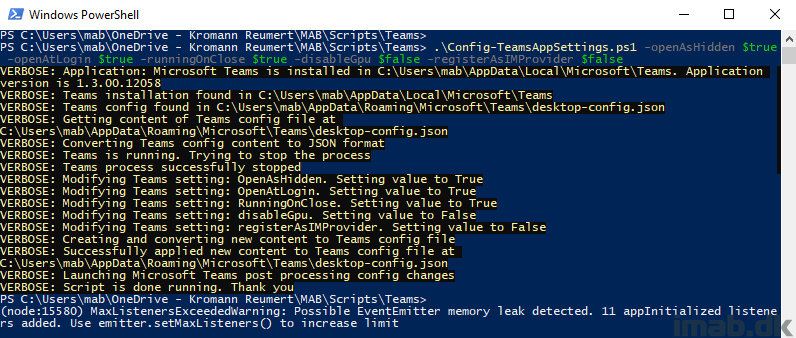
Introduction
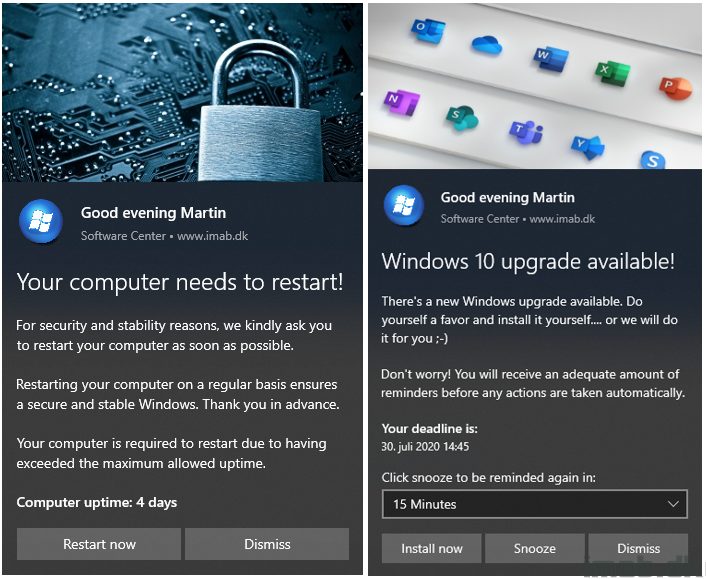
This is just a brief storytelling on, how you can add more user-friendliness and flexibility to your Windows as a Service process with Configuration Manager.
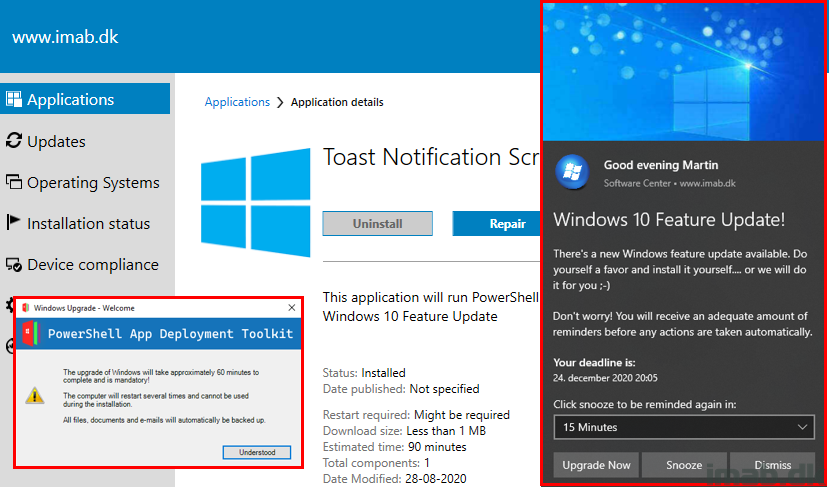
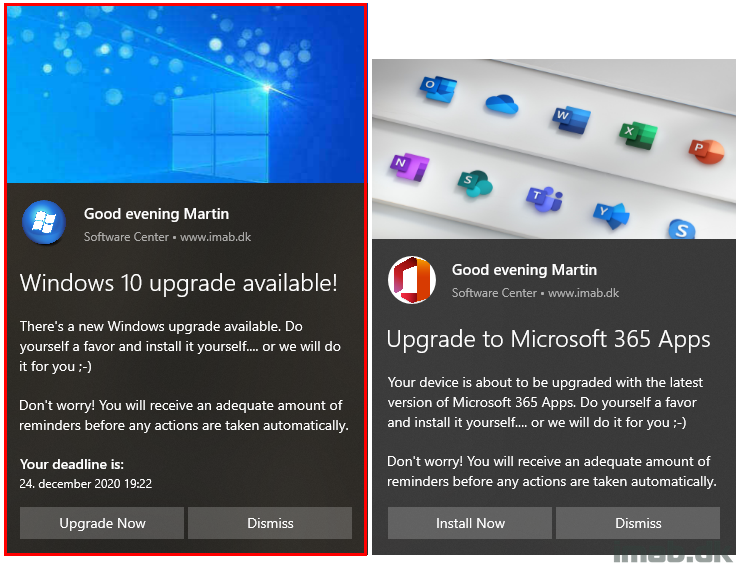
That be whether you fancy using Task Sequences or Feature Updates, this post will show you how you can wrap the process into an initial Toast Notification, which again sends the end-user into a PowerShell App Deployment Toolkit experience, which again will run either the Task Sequence or the Feature Update automatically.
Carrot on a stick: All the binaries used in these examples, are available for download throughout the post. That goes for PSADT as well as exported ConfigMgr applications.