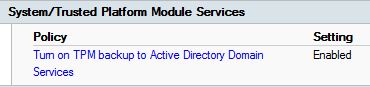
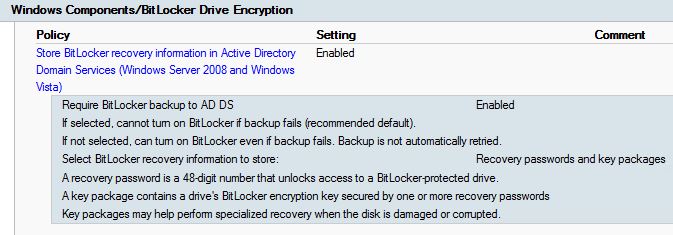
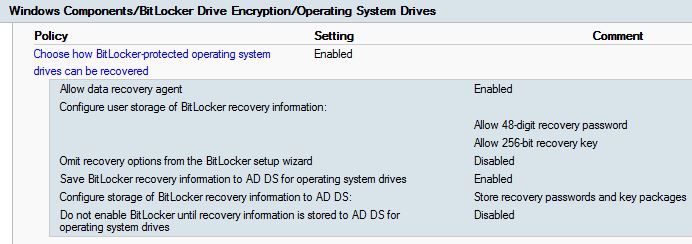
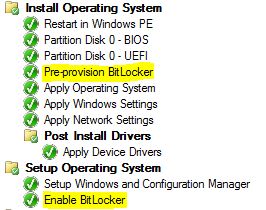
For security reasons, we have decided to join specific computers, serving a specific role to a workgroup instead of our domain. While being in a workgroup in the DMZ, we still had the need to manage them using ConfigMgr.
I had no previous experience in managing DMZ workgroup computers, so I had to gather the required know-how.
This is what I did:
- Listed the limitations regarding workgroup clients. (No Active Directory)
- Created the proper boundaries for the workgroups clients. (If no boundaries are created, all clients will be considered as a slow client)
- Made sure that port 80 (CM) and port 8530 (WSUS) are forwarded to through the firewalls to the new network.
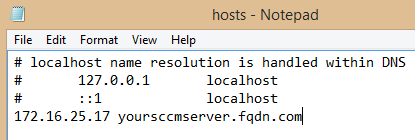
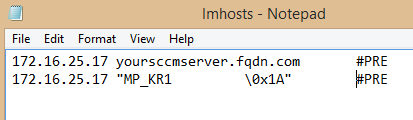
As the workgroup clients are on their own network, and without DNS to give them information about which and where to locate a Management Point, we had to make following changes to the host files (C:\Windows\System32\drivers\etc) on the clients:
With these changes in place, you can install the CM client with following commandline: “ccmsetup.exe” SMSSITECODE=SITECODE SMSMP=yoursccmserver.fqdn.com
If installing the client from an OSD task sequence, you cannot use the SMSSITECODE property (We have a seperate OSD TS for these clients joining a workgroup).
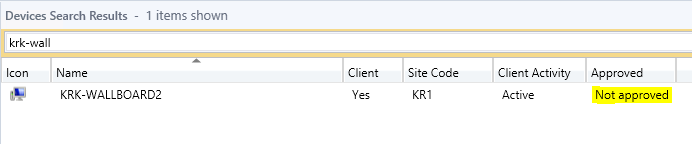
When the client is installed successfully, you will be able to see the client in the SCCM console. Note that the client is not automatically approved (This can be changed to automatically auto approve all sorts of clients, but is not recommended)
After manually approving the client in the console, the client will start to download policies from the Management Point. (To speed up this process, you can restart the ccmexec service)
In the initial phase of getting this to work, it’s a really good idea to watch the proper log files, to see what actually happens, and in case of any errors, take the required actions.
These are some of the important client logs to consider:
LocationServices.log
ClientIDManagerStartup.log
Policyagent.log
Enjoy… 🙂