Introduction
This is the first and initial blog post of an upcoming series, all concerning how one can secure their endpoints using Microsoft Intune.
The posts are meant to serve as titbits, quickly giving the reader an understanding of a specific feature.
The posts are not released in any particular order, and the topics discussed are based on what I’m currently looking into, in my own environment.
Therefore and as usual, this is not a typical and standard walk through, but more a look into how I’m initially taking on the discussed topic. Curios? Read on! 🙂
Controlled Folder Access
Controlled Folder Access is not a particular new feature, as it was introduced with Windows 10 1709. That doesn’t make it any less interesting though.
In short, CFA can be enabled to prevent unauthorized changes to the files on a given device. CFA does so by protecting the folders and only allow changes to the content of those, if those changes are made by a trusted or white listed application.
Applications are added to the trusted list based upon their prevalence and reputation. Applications that are highly prevalent throughout the organization, and that have never displayed any malicious behavior, are deemed trustworthy and automatically added to the list. Applications can of course be trusted manually as well.
Audit CFA
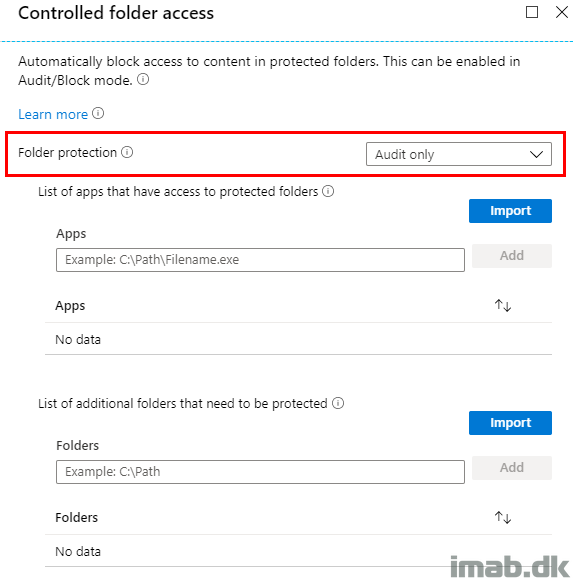
I recommend to start off your CFA journey, by auditing the behavior and to measure the impact. This is done by configuring Controlled Folder Access and folder protection to Audit only as shown below:
Separate Configuration Profiles
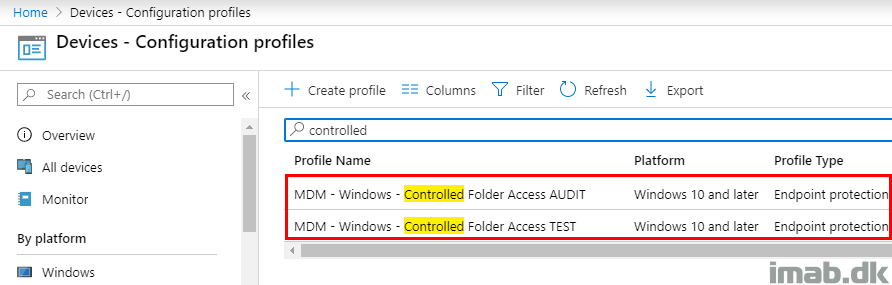
What I also recommend, is that you separate CFA into its own Configuration Profiles. This goes for both auditing and having CFA enabled for testing purposes: Create a Configuration Profile for both AUDIT and the actual TESTING.
Mixing the settings for CFA with other settings, will just make the including and excluding of groups used for assignments more difficult. Keep it simple for now and keep stuff separated. Once you are moving everything to production, you may include CFA into a more general Endpoint Protection Configuration Profile.
Assignments
Auditing of CFA is something you might as well do on all of your devices. Getting some insights to, what possibly is being blocked throughout your organization is a great idea.
Below is my example of assigning this to all my co-managed devices, in the various versions of Windows 10.
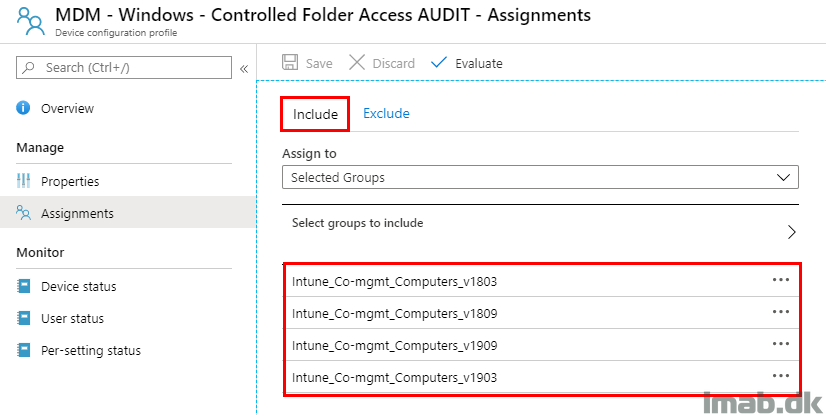
As an exclusion to the enablement of auditing, I exclude the group consisting of devices which has CFA set to enabled.
This is done to prevent conflicts in Intune. In this example, I have a specific group consisting of my test devices:
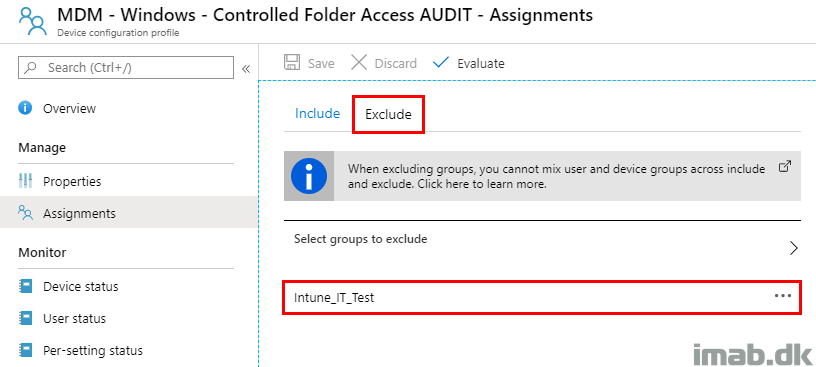
The very same group, is being used as the primary assignment on the equivalent Configuration Profile which is enabling CFA:
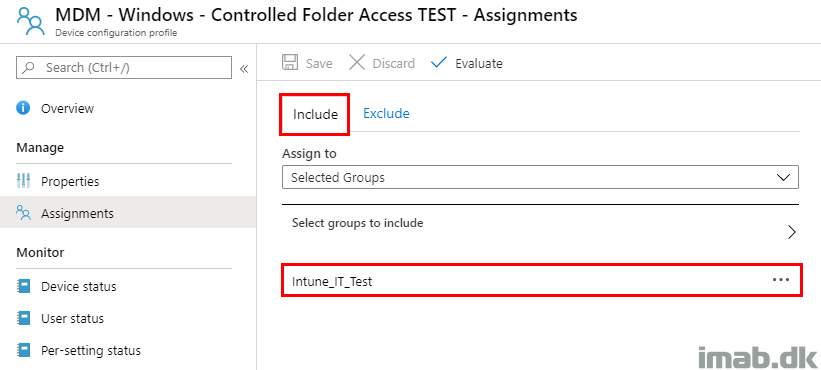
Enable CFA
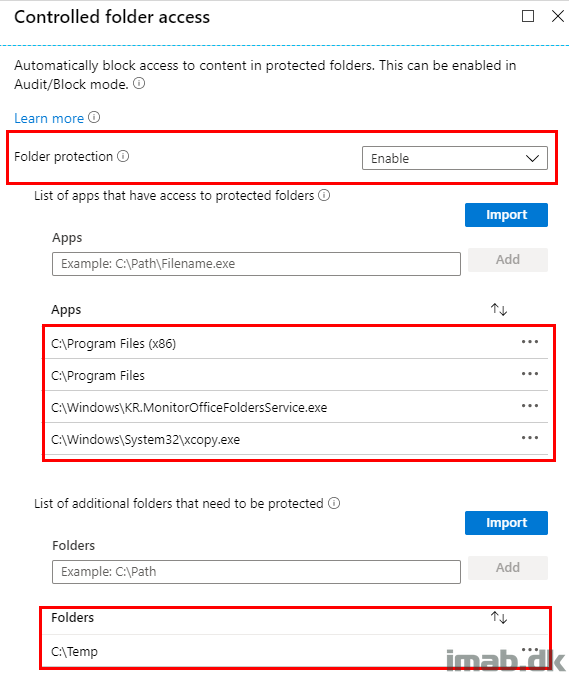
Enabling CFA is done by configuring Controlled Folder Access and folder protection to Enable as shown below.
What you will realize from measuring the impact, is that quite a bit might end up getting blocked. That especially goes for any third party applications you may have installed, doing changes on your device.
In below example, I have added an in house application as well as xcopy.exe to the trusted list of apps. In addition to that, I ended up simply trusting all applications from within the programfiles folders. This is probably not recommended, but may vary depending on what other security measures, that are taken on the devices.
- xcopy.exe is kind of an oddity, as this *should* be trusted by default. However, I found that xcopy.exe got blocked when used in scripts, used in deployments of applications with Configuration Manager.
Also, you have the option to protect additional folders. In the same example below, I have added C:\Temp as an additional protected folder.
Testing
In regards to testing Controlled Folder Access, Microsoft have a dedicated demo site for the Windows Defender features over at: https://demo.wd.microsoft.com
A sneak peek of the site is below, where CFA in particular have been highlighted.
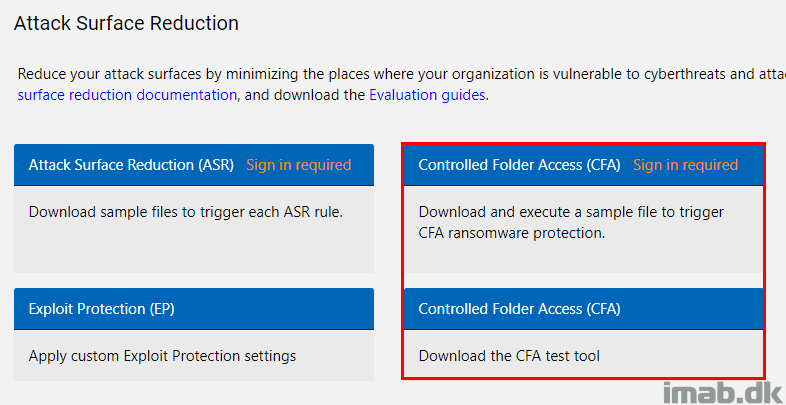
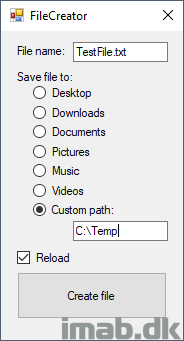
Downloading the CFA test tool, enables you to simulate an untrusted application doing changes to your device.
Monitoring
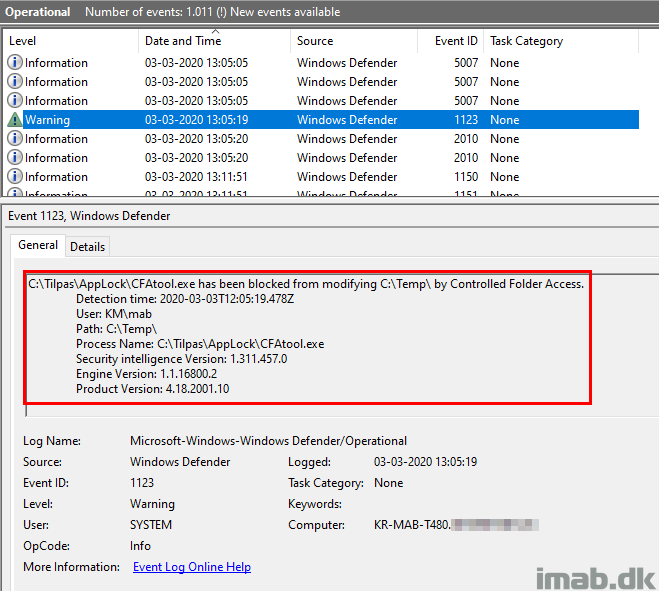
When actions are being blocked by CFA, entries are logged into the event log. Below is the example where the CFA test tool from above, is writing a .txt file to the custom protected folder: C:\Temp.
- Note: The even log in question here is Microsoft-Windows-Windows Defender/Operational
Microsoft Defender ATP
If you are using Microsoft Defender ATP, Controlled Folder Access events are logged here as well. This enables you to query your devices real time using the advanced hunting option. This is particular useful when auditing your entire organization. This will reveal if you need to white list applications manually (and you will). 🙂
- Find the Microsoft Defender ATP portal here: https://securitycenter.windows.com
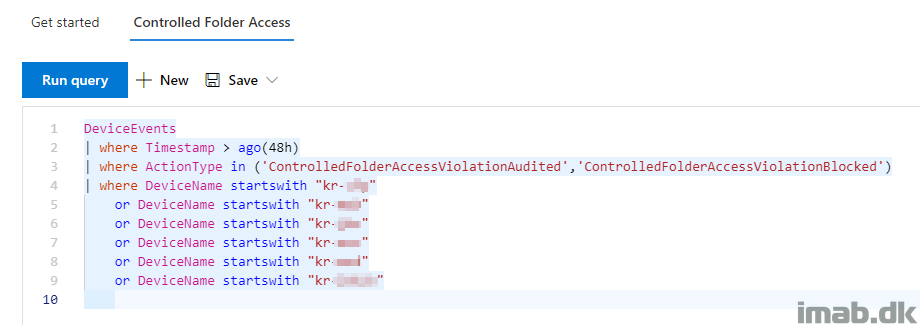
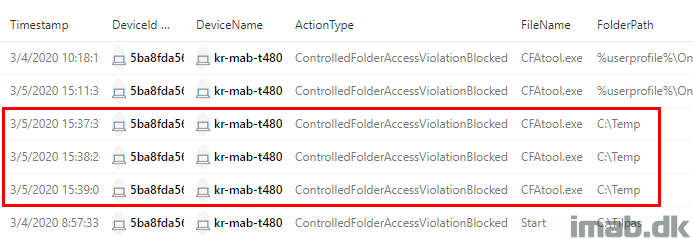
Below is the KQL query used to query specific devices. This can be the devices, where CFA is enabled for testing purposes.

DeviceEvents
| where Timestamp > ago(48h)
| where ActionType in ('ControlledFolderAccessViolationAudited','ControlledFolderAccessViolationBlocked')
| where DeviceName startswith "imab1"
or DeviceName startswith "imab2"
ENJOY 🙂
Thank you for the post, I look forward to testing soon.