Introduction
I find this highly relevant to share at this day. Especially in regards to yesterday’s ‘false positive’ situation, where a lot of system admins got a good scare, when Defender for Endpoint reported that “Suspicious ‘PowEmotet’ behavior was blocked’ on a high percentage of the enrolled devices.
What I really mean by this, is that when you have the option to reduce the attack surface of your environment, you should look into doing so ASAP.
Let’s say yesterdays situation was real, and you for whatever reason didn’t have behavior monitoring enabled in Microsoft Defender Antivirus. You would regret that pretty soon after being hit, when you realize that it could have been prevented.
Same goes for above. Rather look into enabling this new ASR (Attack Surface Reduction) rule today, rather than later after being compromised.
Attack Surface Reduction
The ASR rule in question is this: Attack surface reduction rules | Microsoft Docs and as noted, the rule with an GUID of 56a863a9-875e-4185-98a7-b882c64b5ce5 is not yet available in neither ConfigMgr nor Intune.
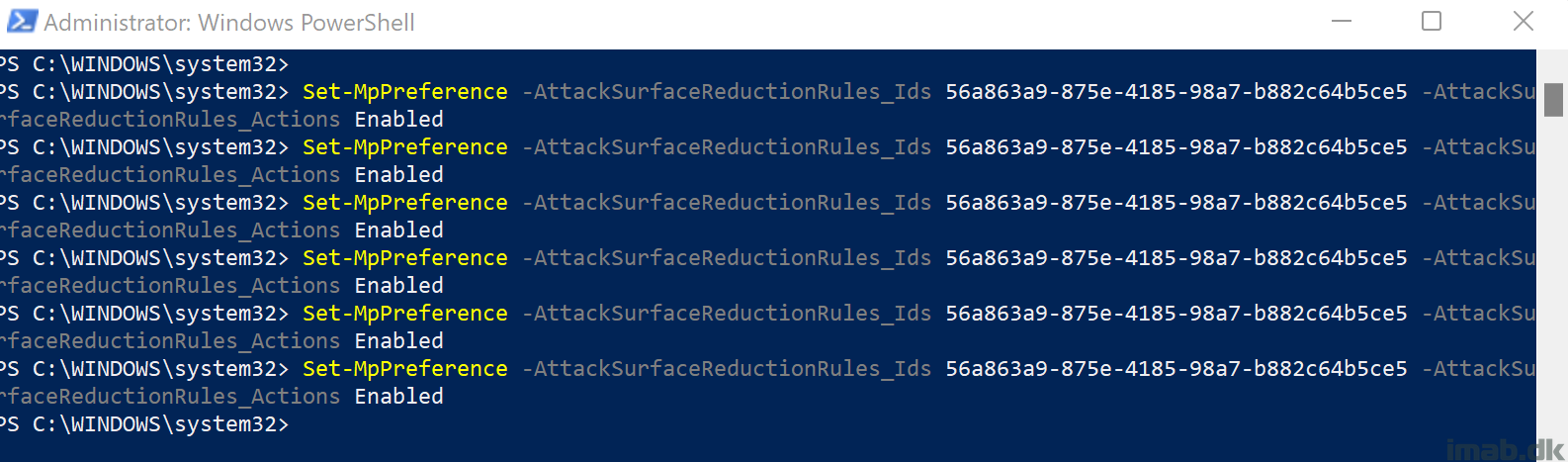
This means, you will have to use PowerShell or OMA-URI in order to configure the rule today. I’ve chosen to use PowerShell:
Enable
Set-MpPreference -AttackSurfaceReductionRules_Ids 56a863a9-875e-4185-98a7-b882c64b5ce5 -AttackSurfaceReductionRules_Actions Enabled
Disable
Set-MpPreference -AttackSurfaceReductionRules_Ids 56a863a9-875e-4185-98a7-b882c64b5ce5 -AttackSurfaceReductionRules_Actions Disabled
ConfigMgr
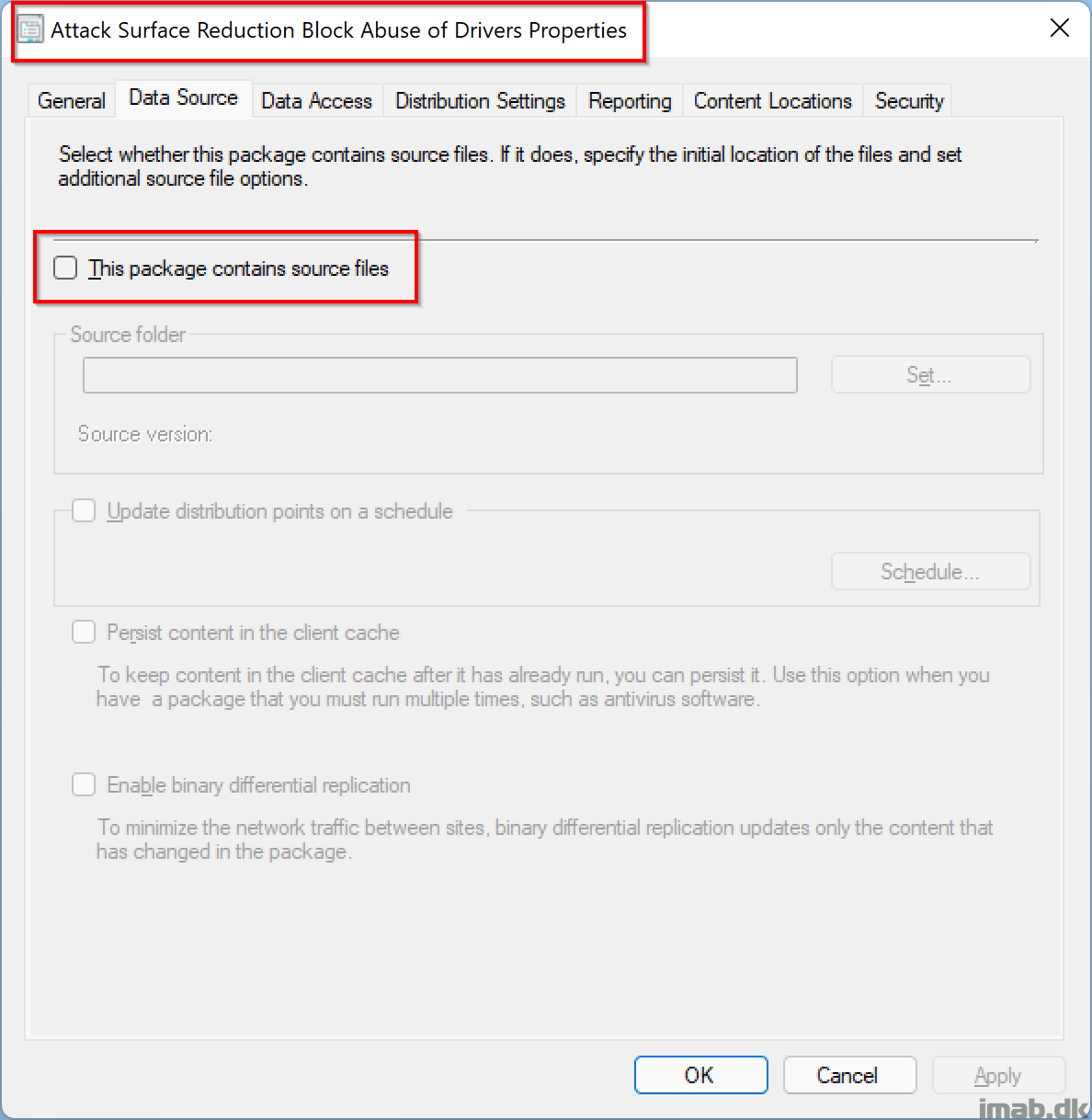
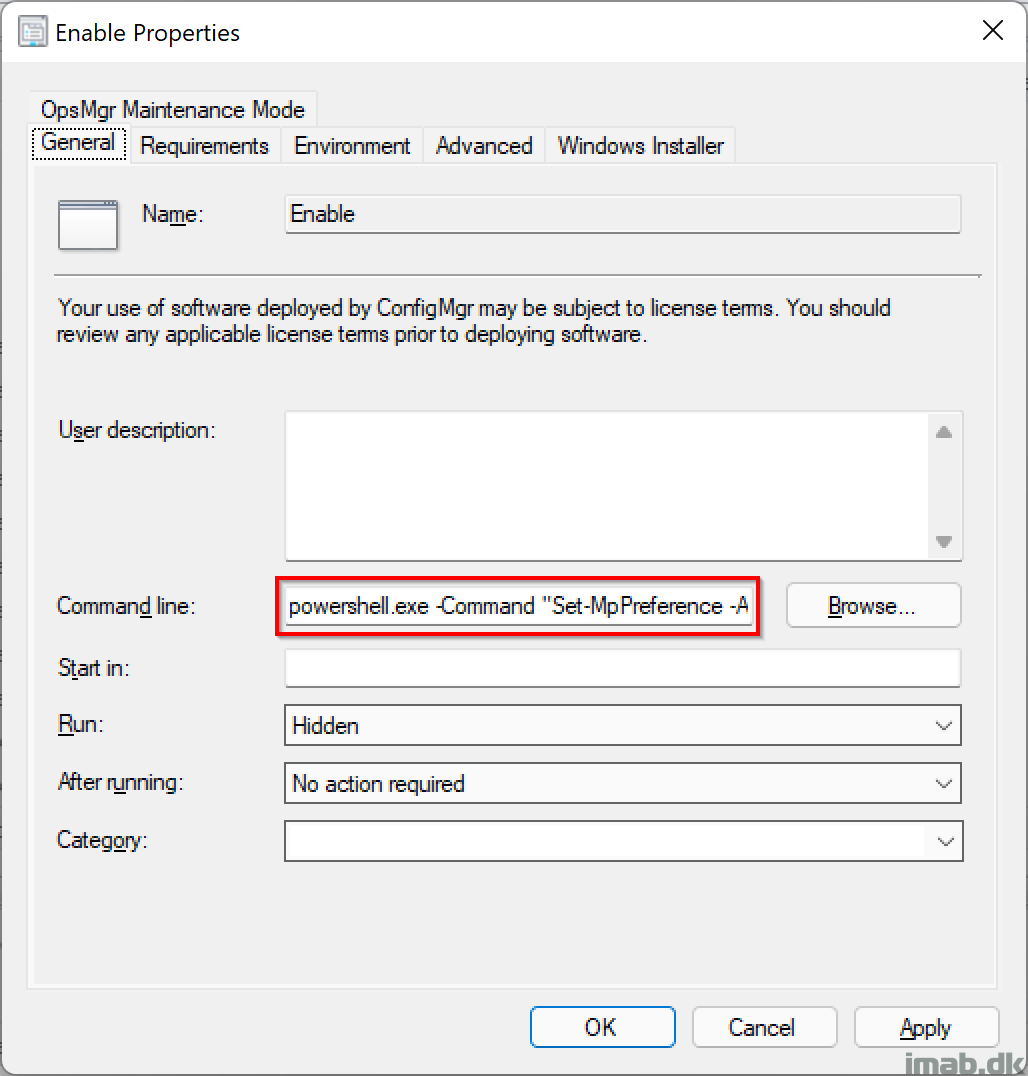
To use above with Configuration Manager, you simply create an old school package, without source files and a program like so:
powershell.exe -Command "Set-MpPreference -AttackSurfaceReductionRules_Ids 56a863a9-875e-4185-98a7-b882c64b5ce5 -AttackSurfaceReductionRules_Actions Enabled"
Did it work?
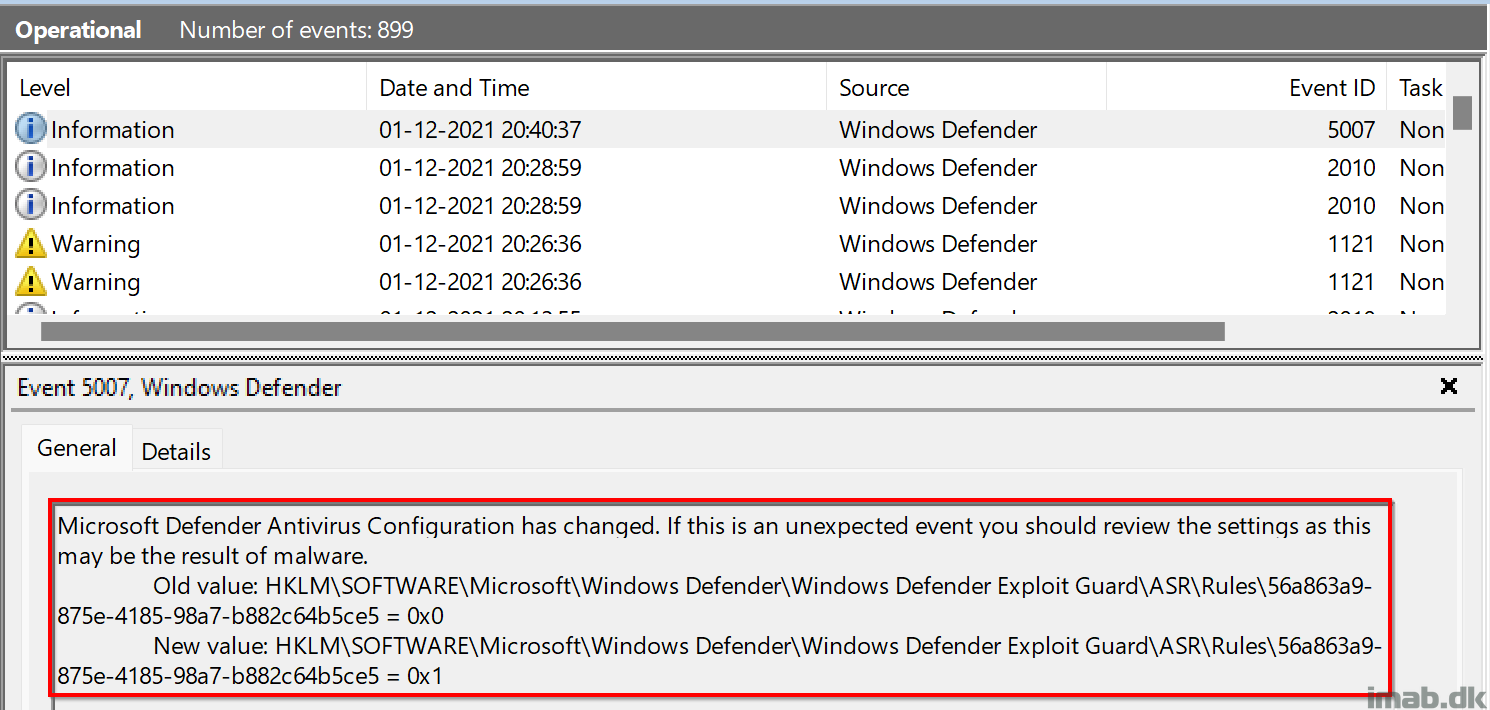
The following event log: Microsoft-Windows-Windows Defender/Operational will reveal when changes to the Defender configuration is being made. When the ASR rule is being enabled, you will se the value go from 0 to 1 like below illustration:
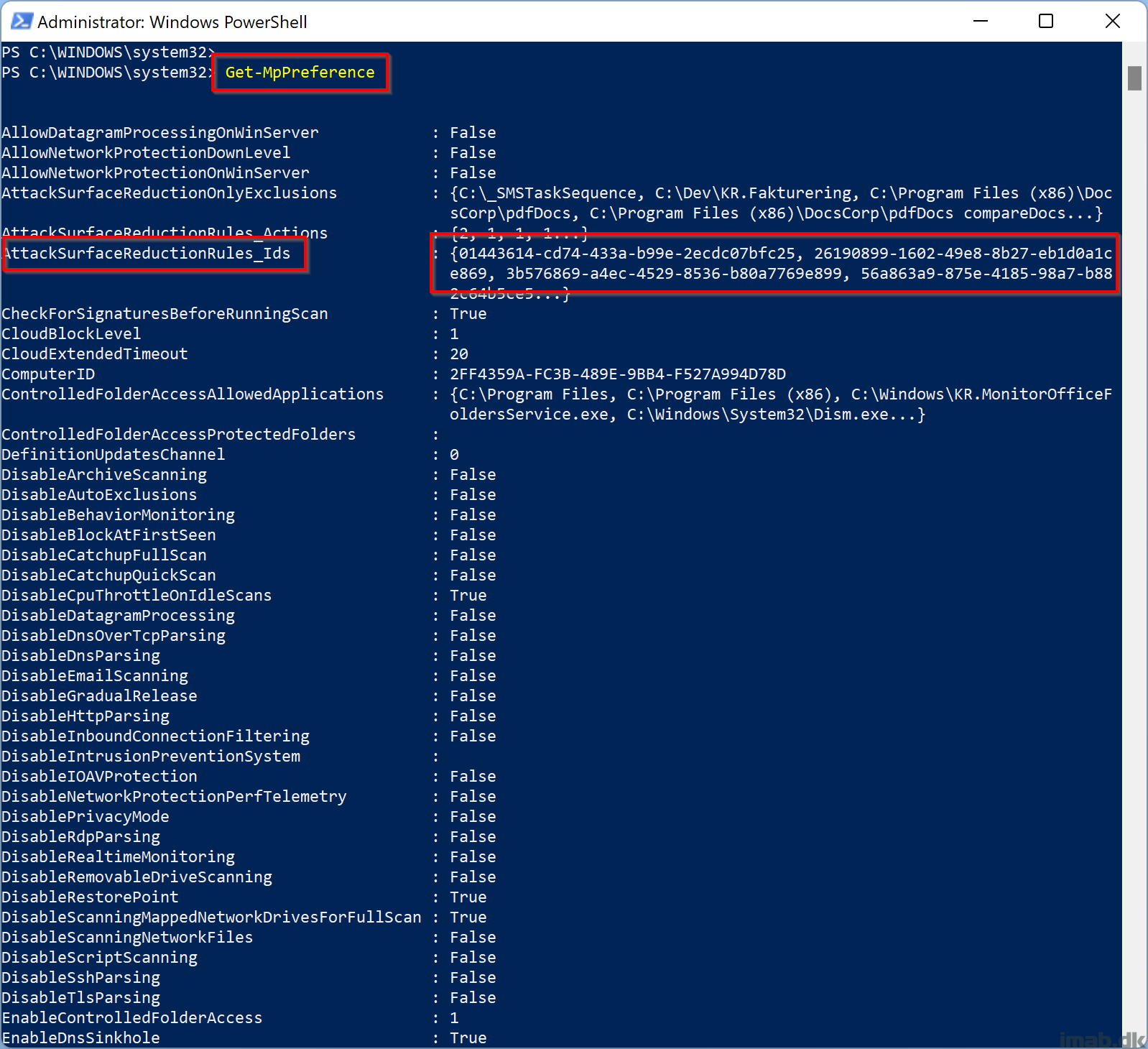
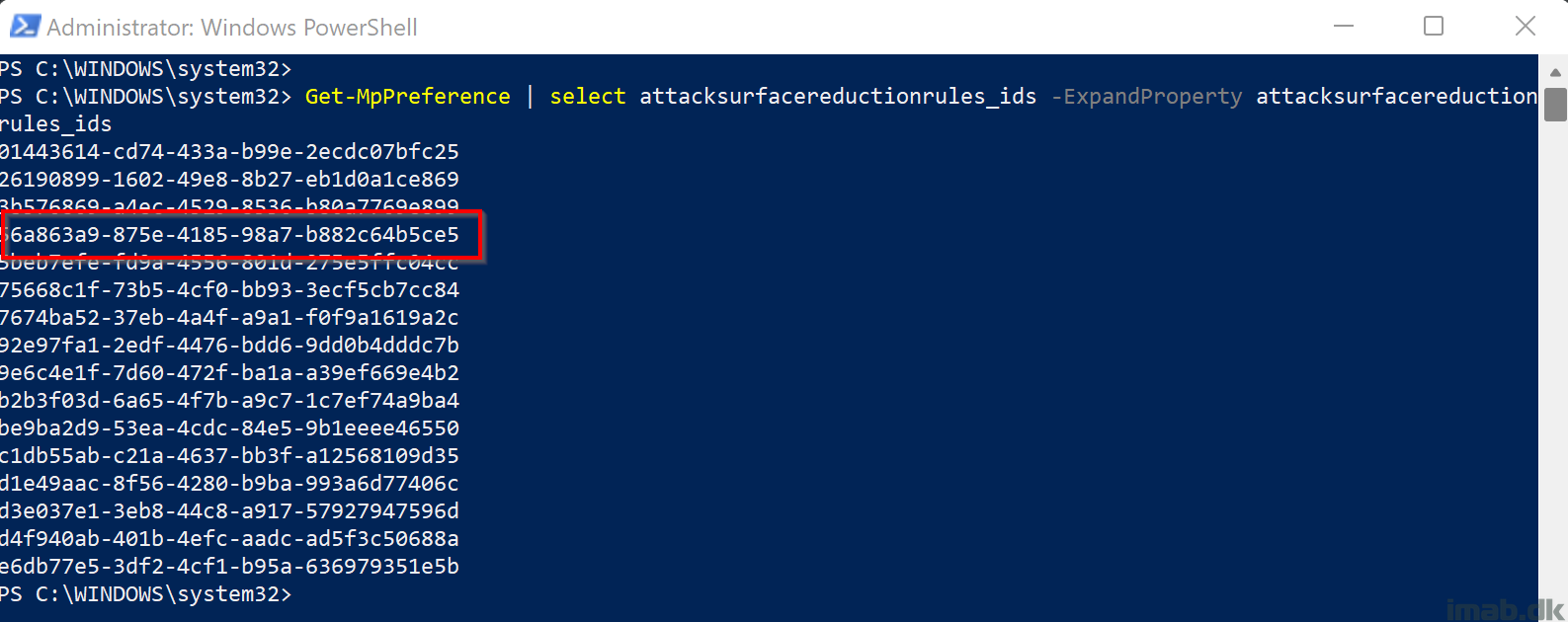
You can also run the Get-MpPreference cmdlet:
Grab the AttackSurfaceReductionRules in a more readable format like so:
Get-MpPreference | select attacksurfacereductionrules_ids -ExpandProperty attacksurfacereductionrules_ids
When enabled, you will find the GUID on the list as illustrated below:
ENJOY 🙂
Hi Martin, thanks for a great post.
I just tested to deploy this rule using OMA-URI.
When that policy hits the client, all other policies enabled using the normal GUI are gone.
So the client only have this new rule applied.
I used this guide where it also says that multiple policies should be merged.
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#mem
Have you seen this?