Introduction
I just very recently discovered, that a new version of the Security Baseline for Windows 10 was made available in Microsoft Endpoint Manager Intune.
It’s been a while since the last version, more than a year in fact, so it was a pleasant surprise seeing an update on this area.
Security Baselines, and those for Windows 10 in particular, consist of a lot settings. So I wondered what’s changed and started browsing and comparing the various settings via the admin portal.
Then I realized how that’s not very optimal, and began looking for alternatives. I eventually got myself into trying something new, and went on to compare the Security Baselines Profiles using Powershell and the Microsoft Graph. The result of that journey is this post. 🙂
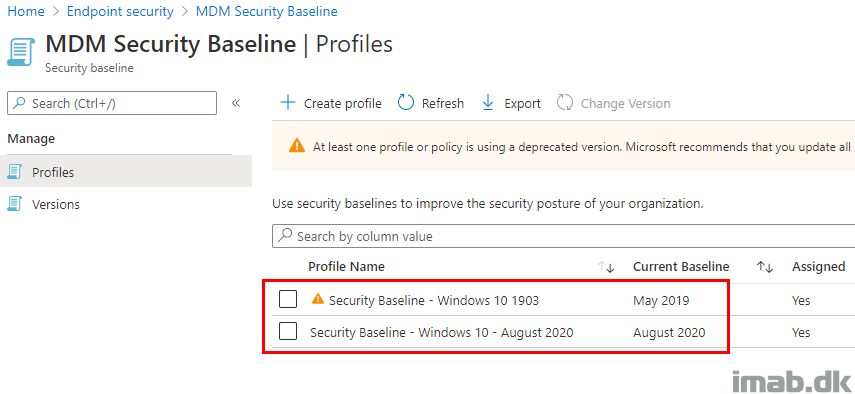
Security Baselines
First things first. The admin portal do have a built in method to compare the baselines, based on their default and out-of-the-box values. This is alright, but not sufficient if you want to compare the actual profiles, and want to know exactly where you are differentiating from the default and recommended values.
The admin portal does also show settings, which are not matching the default baseline, but the reporting here is not live and instant (and can be a bit overwhelming). Querying the Graph API is instant though, and we can limit the output to just about the details we need.
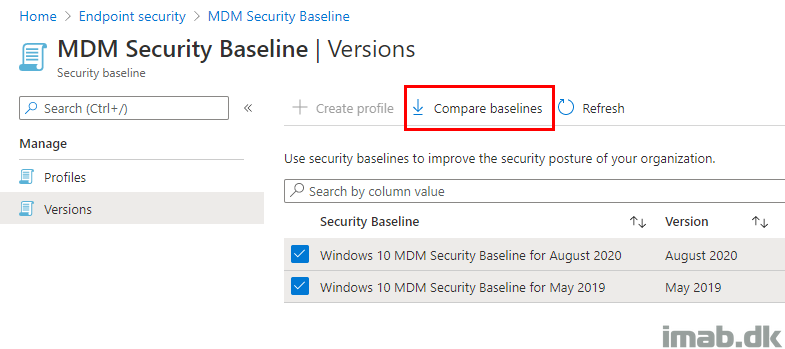
Also, wouldn’t it make a cool exercise, if I could determine if the same settings was added and removed myself via the Graph and Powershell, plus display if my actual profiles are diverging from the defaults? 🙂
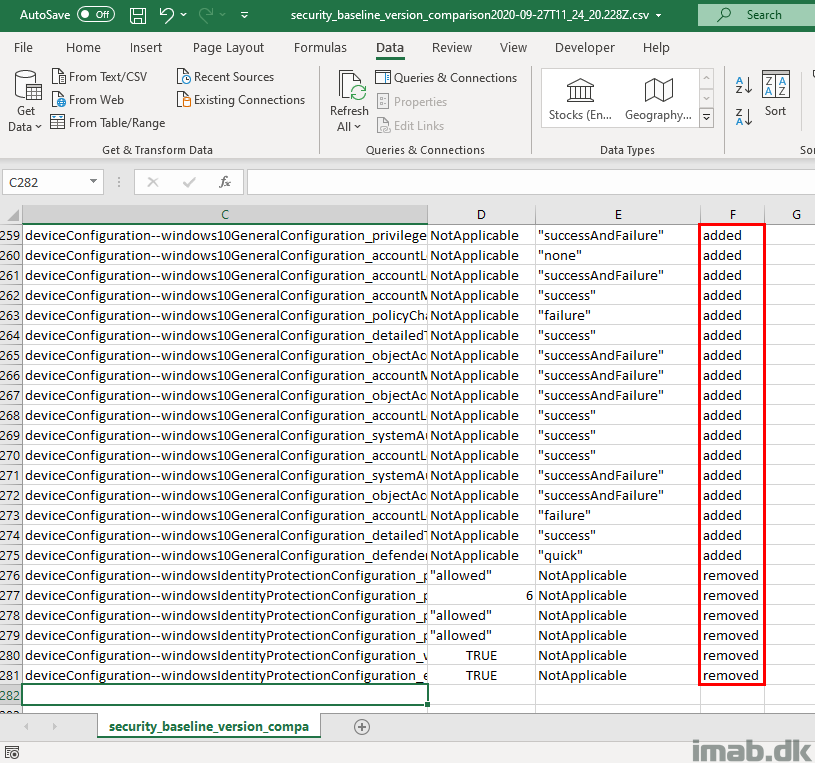
Below is the default exported .csv after some quick formatting to make it readable.
Authentication with Microsoft Graph API
Authentication is obviously required and there are many ways to do so.
The official documentation on the topic is here: https://docs.microsoft.com/en-us/mem/intune/developer/intune-graph-apis and a nice walkthrough of putting it to use here: https://oofhours.com/2019/11/29/app-based-authentication-with-intune/
In this particular scenario, I don’t find it necessary to have the authentication automated, thus I’m connecting to the Graph API on demand using this method: Connect to Microsoft Graph for Intune with Powershell ISE Add-ons
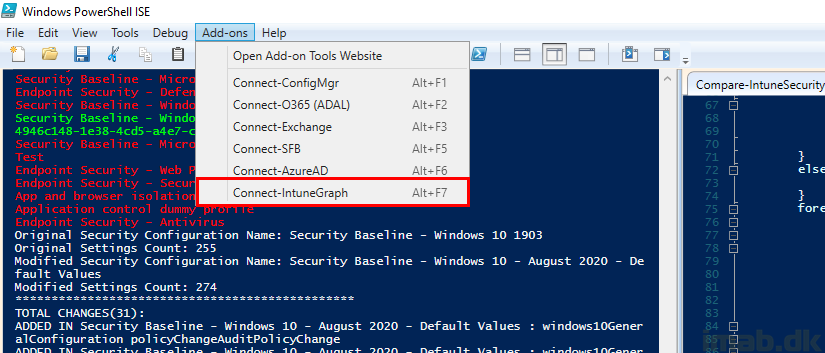
PowerShell
The entire Powershell script I created is available from my GitHub page: https://github.com/imabdk/Powershell/blob/master/Compare-IntuneSecurityConfigs.ps1
All you need to do, in order to successfully run the script and compare 2 security configurations, is to:
- Make sure you are authenticated with the Microsoft Graph API
- Replace the names of the profiles in the very beginning of the script (highlighted below)
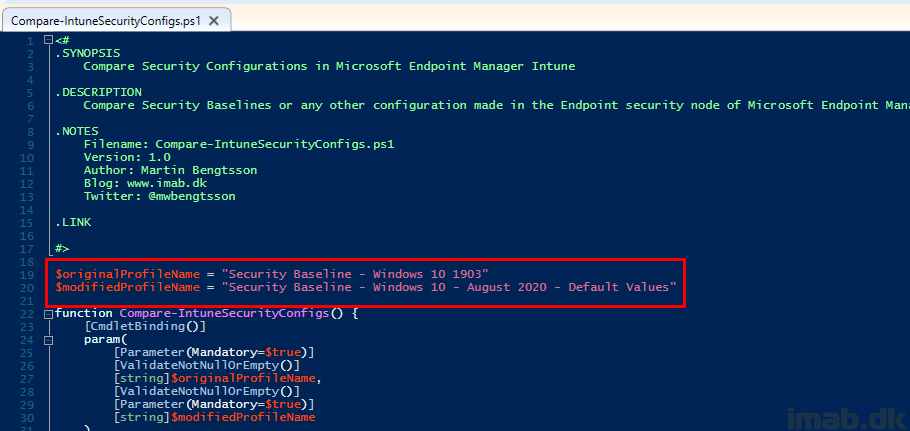
In my scenario, I’m comparing my existing and old Security Baseline from May 2019 containing own changes, with a Security Baseline based on August 2020, containing default values.
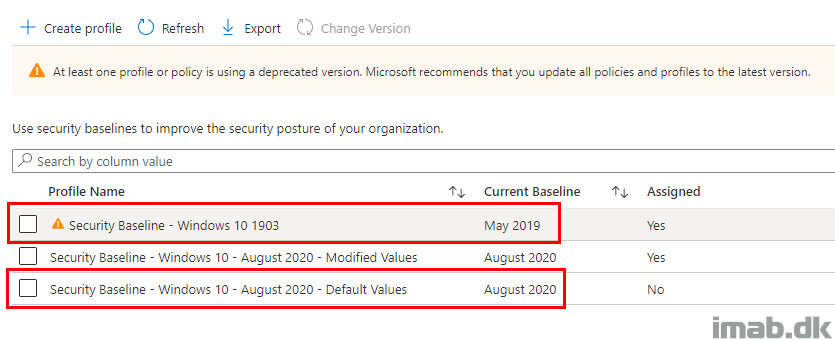
Result
When the script is successfully run, a .txt file will open containing all the details.
In the very beginning, details about the Security Baselines that are being compared:
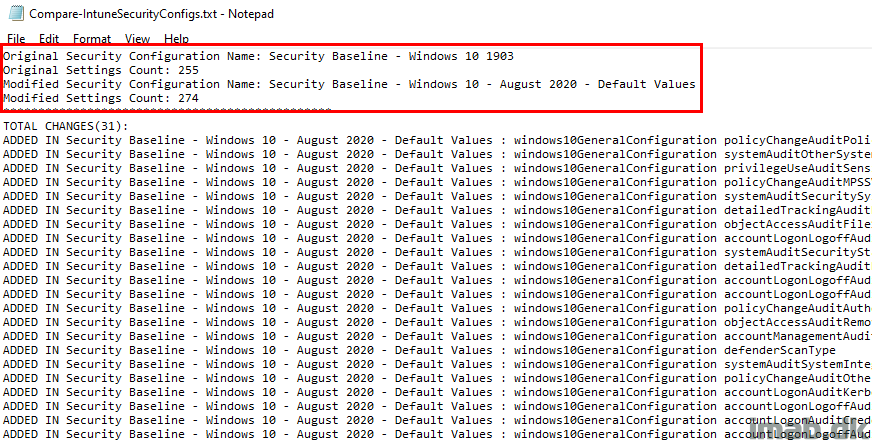
Next, details about which settings that are added and removed:
- This matches what the built in comparison also tells me in the exported .csv file 🙂
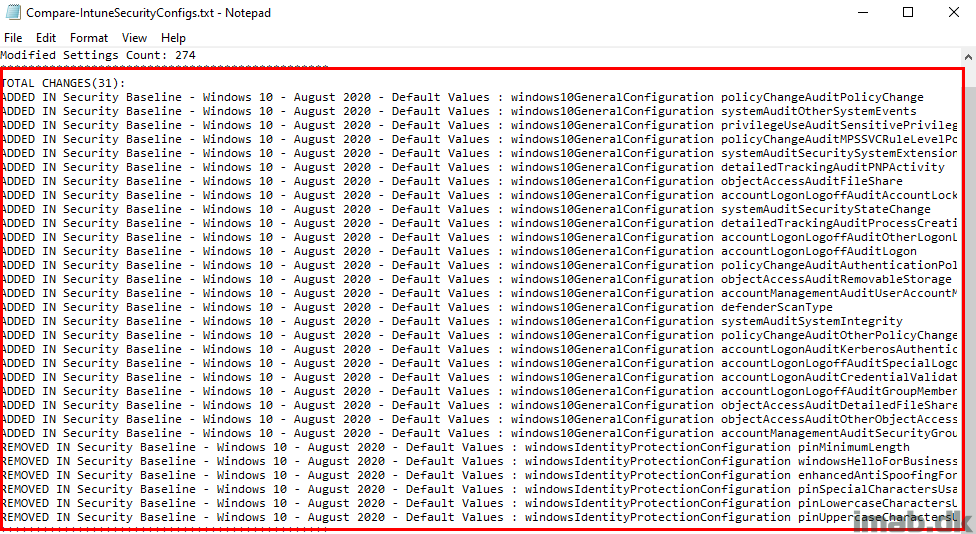
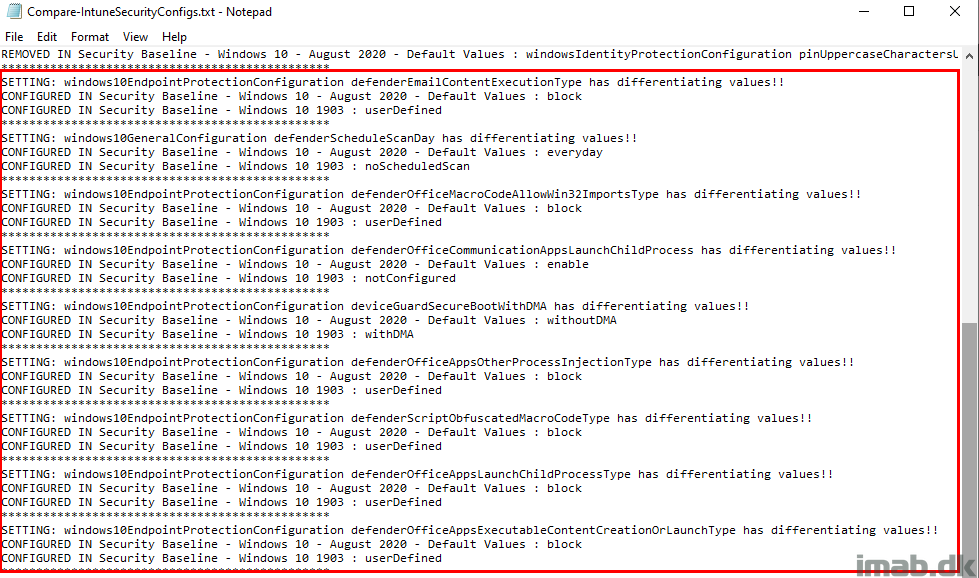
And in the end, details about where the 2 Security Baselines are different from each other.
- This is particular useful, if you have several Security Baselines and lost track of what changes you have made compared to default and recommended values.
Go and try it out for yourself.
ENJOY 🙂
Hi,
Great script and very useful.
Noticed that not all differences are captured.
Noticably any setting that is not just enabled/disabled or not configured, but is more complex in nature. For instance, changes in the firewall sections are not compared.
Maybe something for version 2.0 ? 🙂