Introduction
This is something I currently just have done myself, in our own environment, and while it’s neither super technical nor advanced, then I figured it deserved some attention regardless.
I assume most hybrid (co-managed) environments still look towards Group Policy when doing this, because it’s easy and what we’ve always been doing. I’m regularly asked to change our desktop wallpaper and lock screen images, and when things needs to be done in a hurry, you usually stick to the easy solution.
This time though, I was stubborn and insisted on moving away from Group Policy and do it with Intune. The process made up this short blog post. 🙂
Group Policy
When coming from group policy, configuring lock screen image and desktop wallpaper, this is respectively done for the computer (computer configuration) and the user (user configuration), and would typically require 2 Group Policy objects (unless mixing user and computer configurations, but that’d be a mess in my opinion).
Lock screen image
Below is the illustration taken directly from my production environment, and while still configuring something with group policy in this area (yikes), the lock screen policy is no longer configured. Notice that this is a computer configuration:
Desktop Wallpaper
Below is the illustration, also taken directly from my production environment, where the desktop wallpaper policy no longer is configured. Also notice this is a user configuration:
Microsoft Endpoint Manager Intune
Now, transitioning the lock screen and desktop wallpaper policy to Microsoft Endpoint Manager is easy, and obviously takes place in the Microsoft Endpoint Manager admin center: https://endpoint.microsoft.com/
Create a new device configuration profile (Device restrictions) for Windows 10:

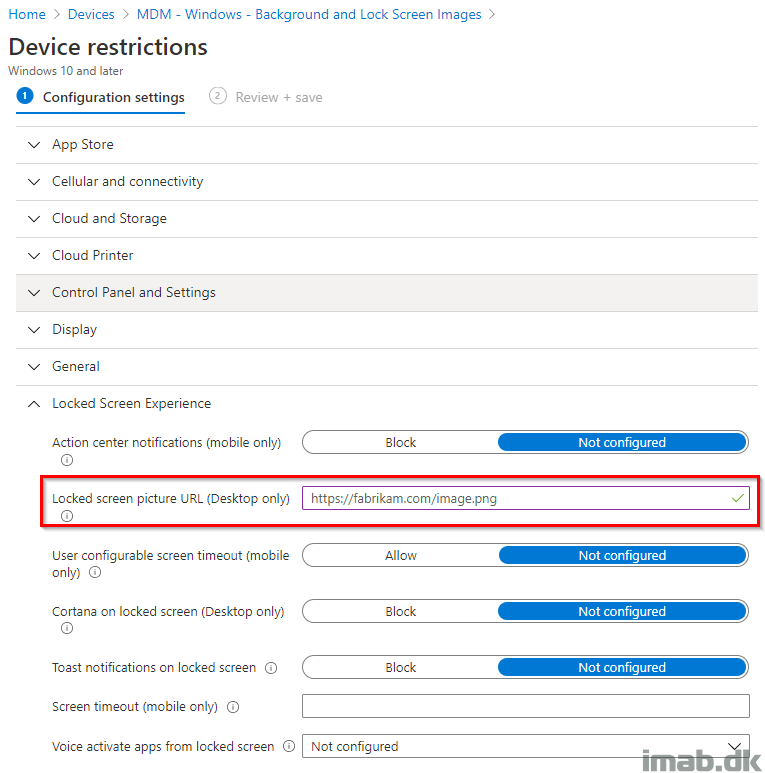
Browse to the Locked Screen Experience options.
Notice how the tooltip suggests that this should be a https source. This is not entirely necessary or required, and can be a local source too if configured like so: file:///C:/Windows/lockscreen.png
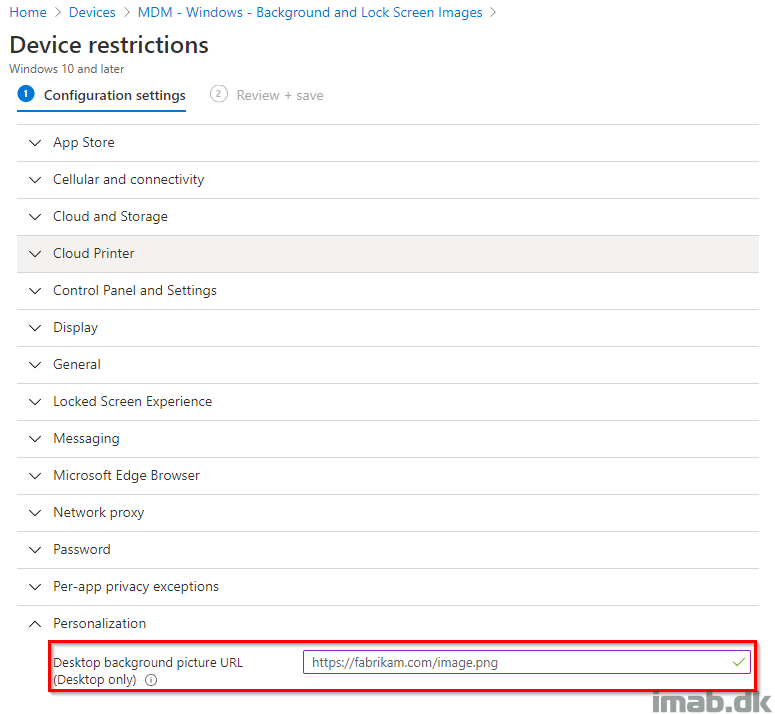
Browse to the Personalization options.
Notice how the tooltip suggests that this should be a https source. This is not entirely necessary or required, and can be a local source too if configured like so: file:///C:/Windows/wallpaper.png
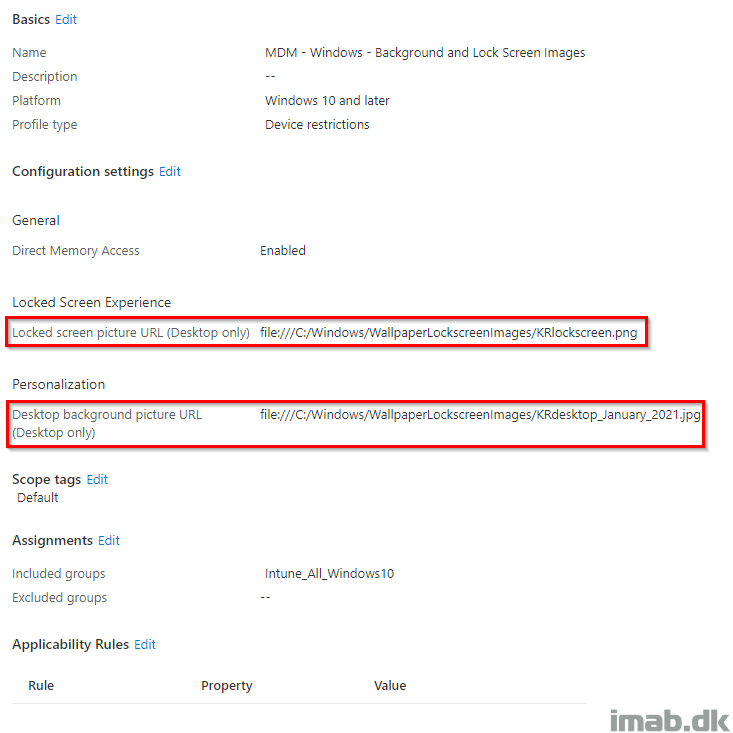
When done configuring above, you have a device configuration profile similar to below illustration, which can be assigned to your devices:
What’s happening on the device?
Once the policy has applied to your device, you will see your configuration made above, create entries in following location in the registry:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\PersonalizationCSP
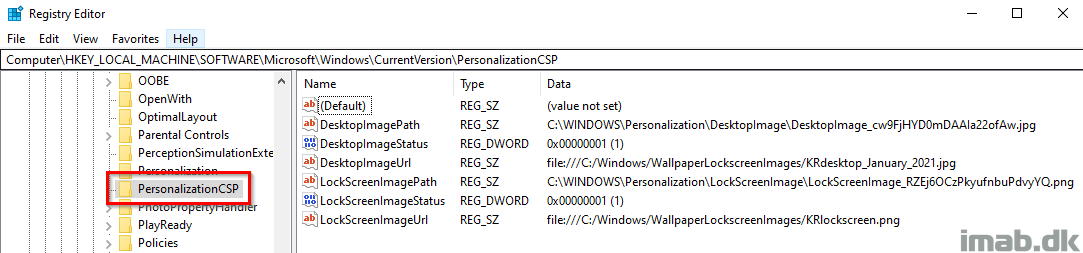
The DesktopImageStatus and LockScreenImageStatus values are defined as following (so this will be a place to look, if something is not working as expected):
- 1 – Successfully downloaded or copied.
- 2 – Download or copy in progress.
- 3 – Download or copy failed.
- 4 – Unknown file type.
- 5 – Unsupported URL scheme.
- 6 – Max retry failed.
- 7 – Blocked, SKU not allowed
What else?
I deploy the source files via Configuration Manager, packaged as an .MSI. This can obviously be done with Intune as well. Notice I do something similar for our screensaver (that might turn into another blog post).
Don’t mind me obfuscating some business applications. As usual, this is taken directly from my own production device.
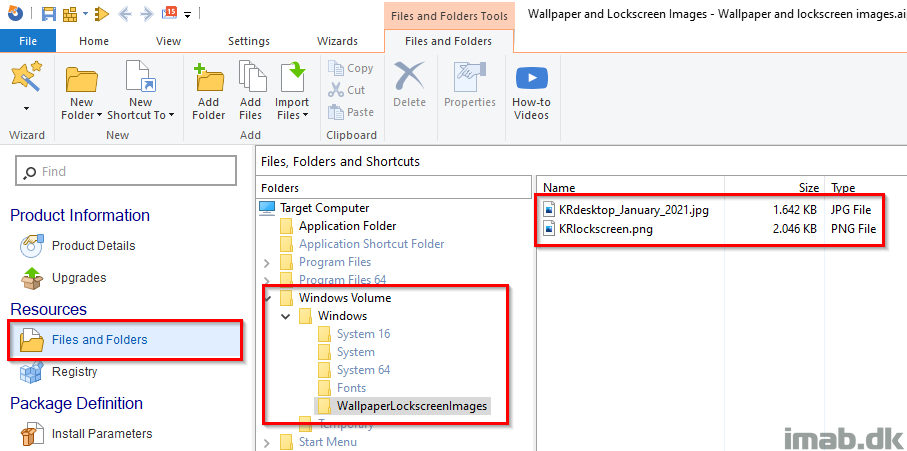
I build the MSI using Advanced Installer, and the configuration needed here, is super straightforward:
Pros?
- If management ask me how many devices have gotten the new wallpaper / lock screen images installed, I can give them exact numbers coming from reporting in ConfigMgr
- Versioning when using an .msi makes it really easy to know exactly which files are installed, and automatically cleans up old files which are no longer a part of the .msi, and thus no longer in use.
ENJOY 🙂
How is your workload configured in your co-management config on MEM config managed to use both gpo’s and Intune?
I have everything switched to intune. This will not prevent GPO’s from applying, though if a conflict you can configure the MDM equivalent to win: https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-controlpolicyconflict
Hello, how do you get the background to update immediately? I’m using Intune to push background images to devices, but changes are applied only after a device restarts or the user logs off and logs back into it. Thank you.
This is tied to the explorer.exe process, so typically a reboot is required or you restart explorer.exe manually (I do that myself for testing, but not something I do for the devices in production)
How are you pushing images it keeps failing with all the methods I’ve tried
I’m actually packaging them into .msi and deploy them with any regular method you use for .msi deployment 🙂
What Intune license do you need for this??
I’m no licensing expert, but if you’re licensed for Intune in general, that’s all you need. My example is taken from a co-managed environment, and that’s not a separate license. EMS license, which includes Intune, also licenses use for ConfigMgr, though you should consult with your MS partner 🙂
Perhaps another way of asking this is – Which Windows Version does this work with? A lot of the built in Intune ‘policies’ will only work with windows Enterprise. If you’re using W10 Pro for example, half of the configurable settings have no effect.
Will this work with W10 Pro?
Is it possible to have this run once in intune? The idea here is to have the wallpaper policy run once during autopilot. user logs on with our company wallpaper, but if the user changes it thereafter we don’t want it to revert back to the company wallpaper.
Please note this only applies to Windows 10 Enterprise edition. I found out the hard way. My company uses 10 Pro so this doesn’t work. I have to use a powershell script.
Yeah, if you’re using anything other than enterprise, you will have to create the registry entries with a powershell script or something similar 🙂
Is there a way to deploy a wallpaper to a device just once during the autopilot process? Like that the user get’s the company wallpaper and thereafter they can change it to what they want.
hi
we have this PersonalizationCSP configured via intune, set it to our hybrid join machine. but the machine seem still to get the lock screen from “Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SystemProtectedUserData\S-1-5-18\AnyoneRead\LockScreen”
any idea ?
It’s important to note here that those Intune Configuration template will ONLY work on Windows 10 Enterprise, if you are running windows 10 pro or business those CSPs will not work. Unless you are in S mode or if SetEduPolicies in SharedPC CSP is set.
Source: https://docs.microsoft.com/en-us/windows/client-management/mdm/personalization-csp
Hi,
Do you have a tutorial on how to build MSI using the Advanced Installer?
We tested the background and lock screen using local file setting as above and the policy only needs two “//”. The desktop and lock screen only works like this file://C:
Strange. I’m not sure what MS docs I was using at the time, but my policy indeed has three forward slashes, at the policy works just fine. 🙂
the config file works great but… how to we define the type of display..fit, fill,stretch..etc..am thinking not possible without script..
If you wanted to update your lock screen in the future, would you place a new image in the same location with the same name or would you place an image with a different file name there and update your Locked screen picture URL with the new name?
I would place a new image with a new file in the same location and update the locked screen with a new name. I’ve seen that windows will cache the old image, if reusing the name. 🙂
Can i have something to rotate it on daily basis – or look in an repo like https ( using blob storage ) and pick up based on date – like image of dd-mm-yyyy.jpg to match windows settings ?