Introduction
Good news everyone!
Last week, a new Endpoint security policy experience in Microsoft Endpoint Manager was released. Among the new policies, you will find a brand new way of managing your Microsoft Defender Antivirus. This new policy type, offers the long-sought for tri-state configurations consisting of No, Yes and Not-configured, which simplifies things greatly.
I do think these new policies will make management a lot easier. Once all of your configurations eventually has transitioned away from regular device configuration profiles, the general view of security measures taken on your devices within Microsoft Intune, will improve by a lot.
This is not a typical A-Z guide, but rather my first and brief look into the new options. All of this of course, based on my own production environment. Curious? Read on. 🙂
Microsoft Intune
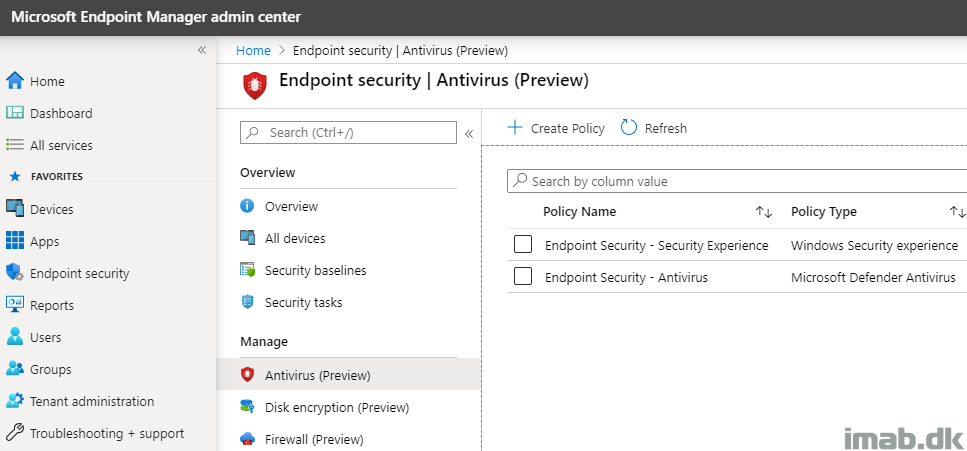
For good measures and before going into details, I’ll start off by showing where this new policy type is being configured.
As usual, this takes places in the Microsoft Endpoint Manager admin center: https://endpoint.microsoft.com/
- Endpoint security -> Antivirus (Preview)
Below is an illustration from my environment, where I have configured policies for both of the new policy types within Antivirus.
Creating Policy
When creating the profile, you have the option to select between macOS as well as Windows 10:

Similar to the selection of platform, you have another two options in regards to what’s being managed: Microsoft Defender Antivirus or Windows Security experience:
Antivirus Settings
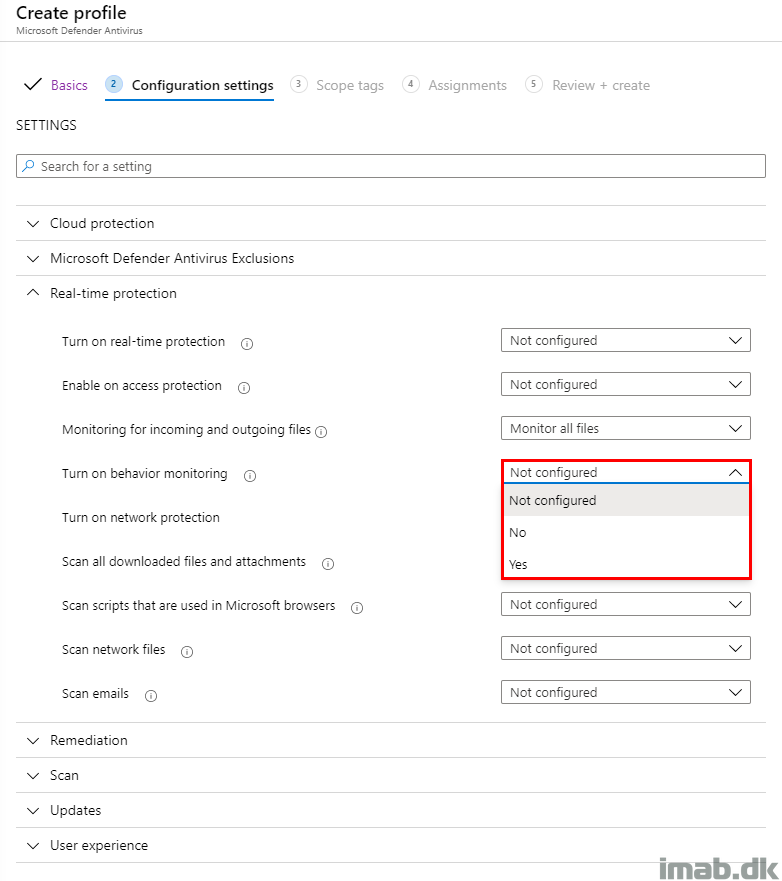
As mentioned in the introduction, these new policies are being delivered with 3 configuration states, which makes it a lot easier to roll back a given setting if necessary.
Previously and with the configuration with the regular Device Configuration Profiles, this was possibly a one-way street, which translated into either Configured or Not configured.
Conflicting Settings
The settings available from these new Antivirus policies, are also settings which are available in regular Device Configuration Profiles as well as in the Security Baselines. This makes for some interesting combinations, if one is not awake and aware of any other configurations made throughout the environment.
The reporting in this scenario, is similar to the rest of the reporting in Microsoft Intune. The overview will bring a traditional pie chart, which will quickly summarize the status for you:
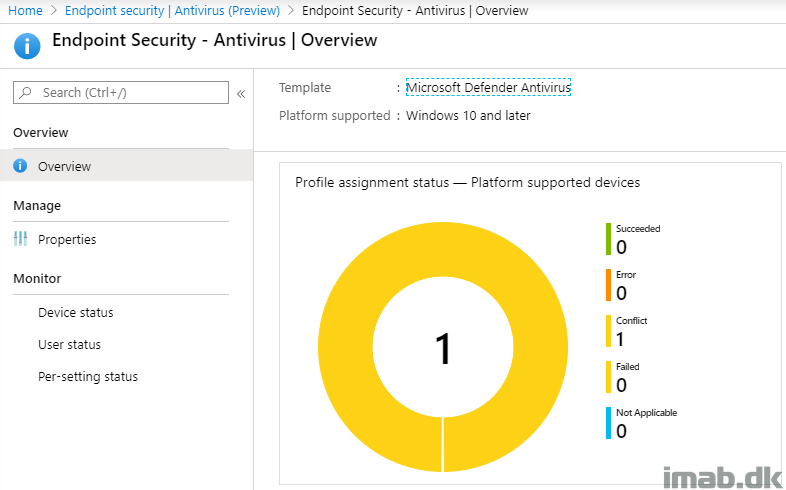
In case of a conflict, which is likely to happen unless you pre-allign each and every setting with any other configurations made, the Per-setting status is helpful to tell you exactly which setting that is in conflict:
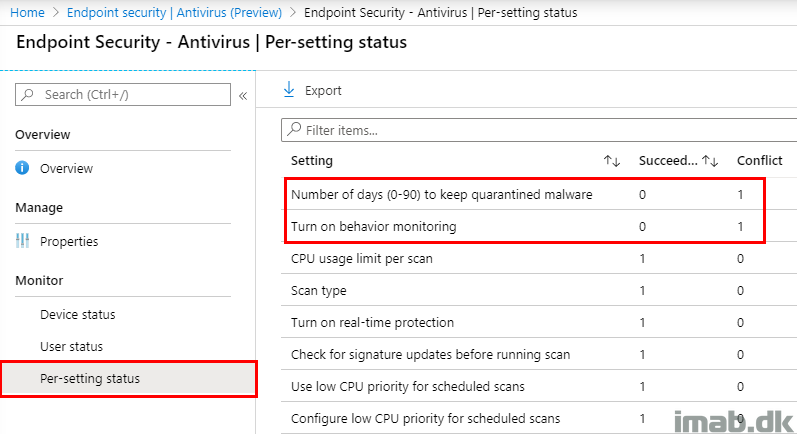
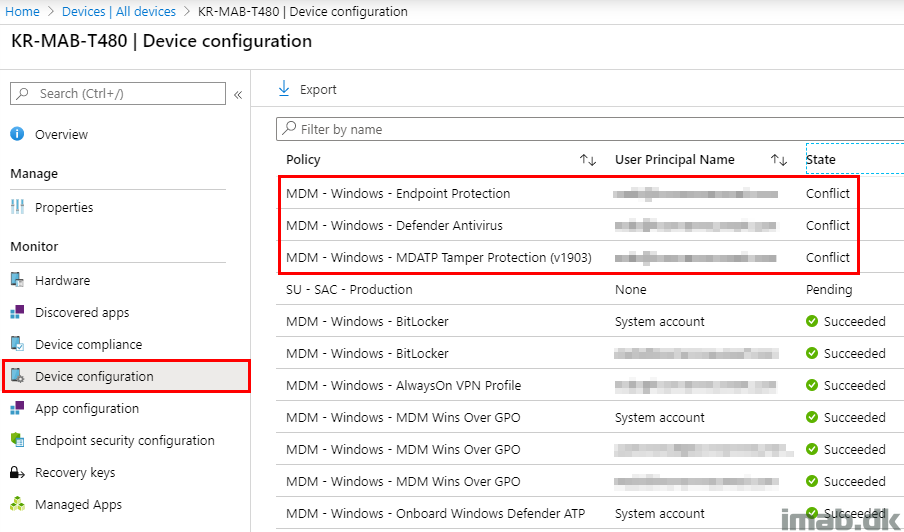
Moving on finding out more about the conflicting settings, and where those are coming from, browsing the device which is having conflicts, will reveal some further details.
In my scenario, I found that all of my Device configuration profiles, which are managing settings related to Endpoint protection was having conflicts (some of those created for the purpose of this blog):
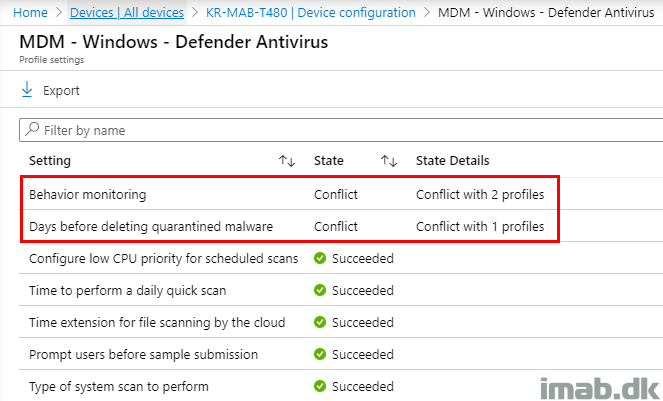
Digging further into each profile, you will find the same information as you initially found, though the wording used here often is a bit different.
- Note: I think this sometimes can lead to confusion. Some of the same settings, which can be managed with different features, has often different wordings depending on where they are being browsed. In this scenario “Days before deleting quarantined malware” and “Number of days (0-90) to keep quarantined malware” are referring to the same setting. While this is easy to figure out in this scenario, it’s not always like that IMHO. 🙂
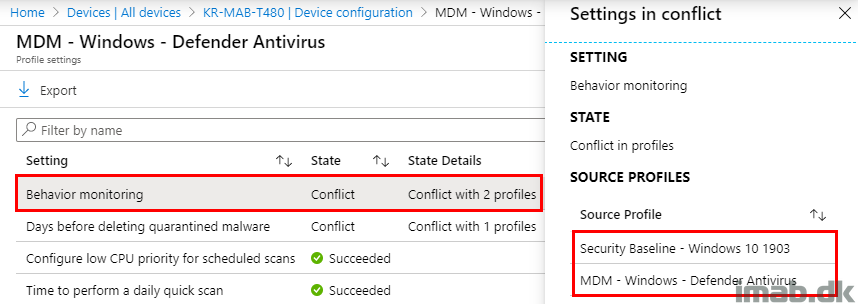
In the same view as above, and when highlighting one of the conflicts, a new blade will appear.
This blade will usually reveal which profiles across entire Microsoft Intune, including Security Baselines, that are having conflicts.
- Note: I might need stronger coffee, but this seems unexpected. The profile comes out as in conflict with itself, but is missing to list the new Antivirus policy? 🙂
Planning and Assignments
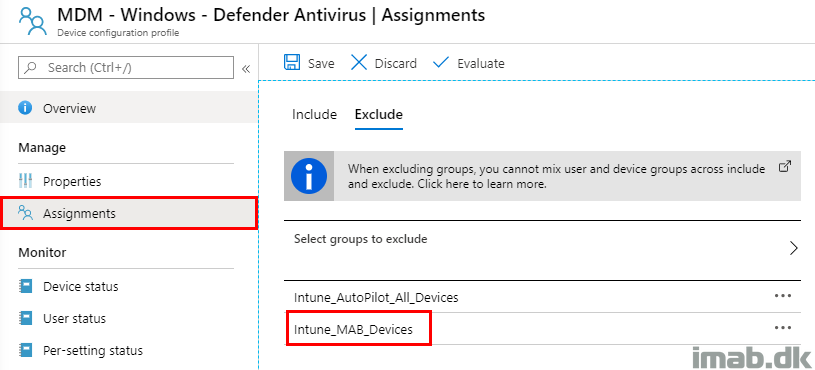
While making your way into the new delicious Endpoint security policies, I suggest that you make the proper planning for tests and exclusions.
I believe the transition here, requires some extra attention and thoroughness, seeing some of the settings found in the new Antivirus policies possibly span across several previous and different configurations (Endpoint Protection, Device Restrictions as well as Security Baselines).
More information
ENJOY 🙂
We’ve just started the transition to Intune and Autopilot for our company to see if we can switch from on-premise to cloud managed devices and articles like these are very helpful in finding our way around Intune and new possibilities in Intune. Thanks for your efforts!
Thank you Marcel – great motivation to do more 🙂
Hello which is a better way to go when configuring profiles vs policies? IF you create a profile and assign to a specific group and then you have MDATP is it better to configure in MEM End point security policies and assign to groups or thru profiles ?