Introduction
This past week I went back to basics with Configuration Manager, as I was working with some applications where I needed the deployments to behave differently based on various factors.
Some may resort to creating individual applications or even packages for each specific need, but there are more clever ways of doing it.
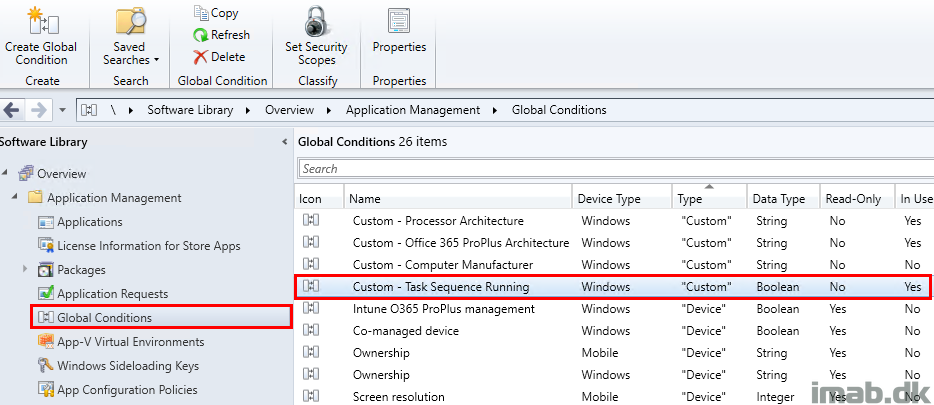
For instance, in this specific case, I had different sets of binaries to be used, varying based on the architecture of Office 365 ProPlus installed. I also wanted something different to happen, whether the installation was happening with a task sequence or not.
So again, this is something a single Application in combination with the proper Global Conditions can cater for. No need to create several Applications or Packages. Curious? Continue reading 🙂