Introduction
Last week I gave an example on how to leverage Microsoft Intune and Conditional Access to restrict access to Exchange Online for iOS devices. This week, I’m continuing the use of Microsoft Intune and Conditional Access, and will give an example on how to restrict access to company e-mail if not using a Windows 10 1803 device. All of this based on a computer co-managed with both Microsoft Intune and Configuration Manager.
So basically; no e-mails if not running on the latest and greatest version of Windows 10 on my co-managed device.
Requirements
Before going deep dive here, I’m just gonna list the requirements for this exact scenario:
- AAD P1 license for Conditional Access
- Intune license
- Computer registered in Azure
- Computer enrolled into Intune
- In this scenario, the computer is Co-managed with Configuration Manager and as of such, a bunch of other requirements in order for that to work properly, see: https://www.imab.dk/flipping-the-switch-how-to-enable-co-management-in-configuration-manager-current-branch/
- Compliance policy workload switched to Intune for Co-managed devices
- In this scenario, the computer is Co-managed with Configuration Manager and as of such, a bunch of other requirements in order for that to work properly, see: https://www.imab.dk/flipping-the-switch-how-to-enable-co-management-in-configuration-manager-current-branch/
Configuration in Intune
Compliance Policy
First off I’m going to cover the compliance policy used in my example. The compliance policy is essentially a set of rules and settings that a device must follow to be considered compliant. And in this case, if not compliant = no access to company e-mails in Exchange Online.
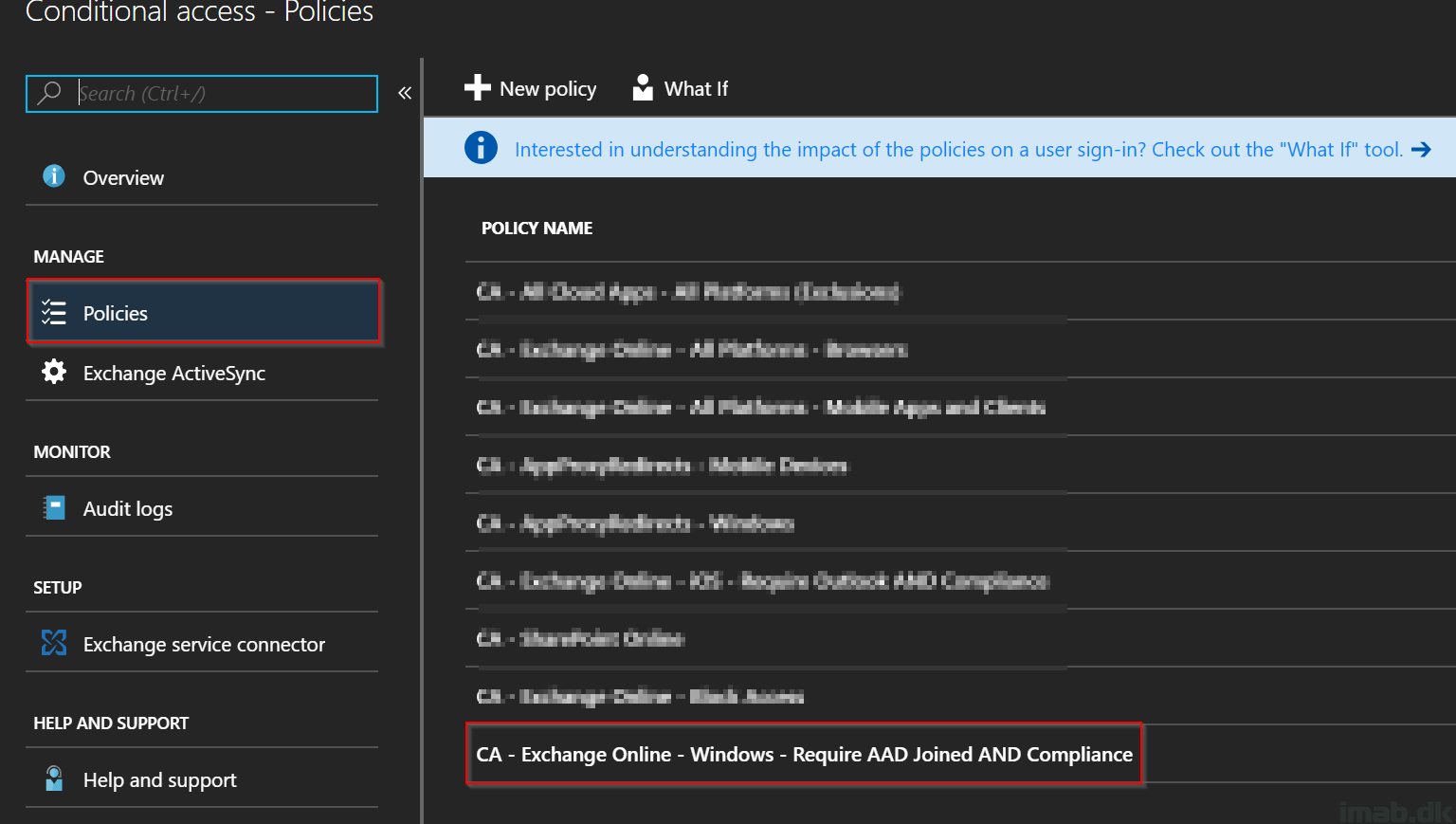
- Log into the Azure portal at portal.azure.com and locate or search for the Microsoft Intune blade and go to Device compliance -> Policies
- Once located, create a new Compliance policy on + Create Policy as shown below:
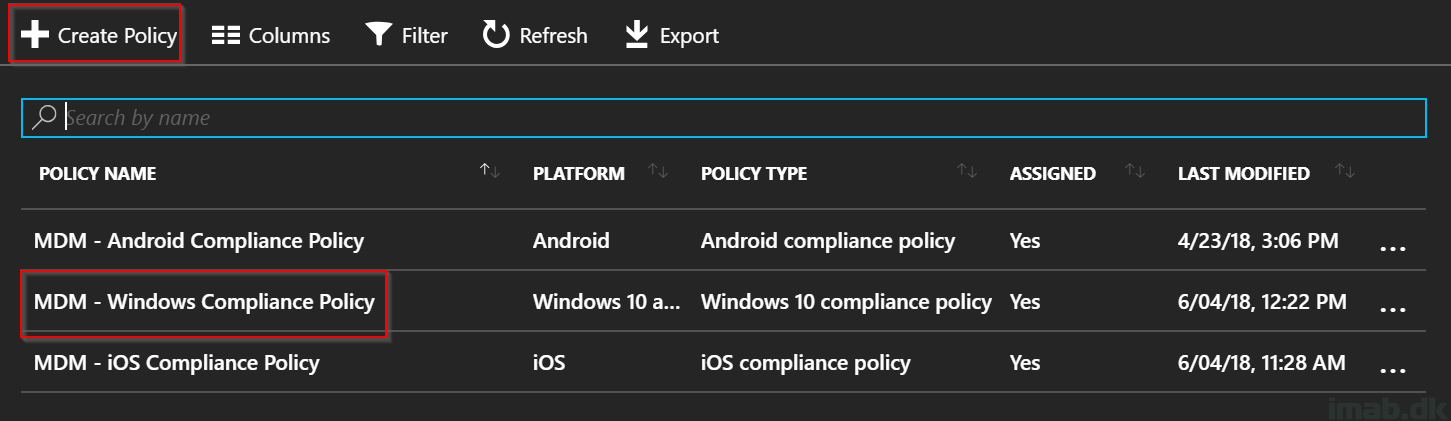
- Give it a suitable name and description. For inspiration, mine is called: MDM – Windows Compliance Policy
- Click on Settings -> Device Properties
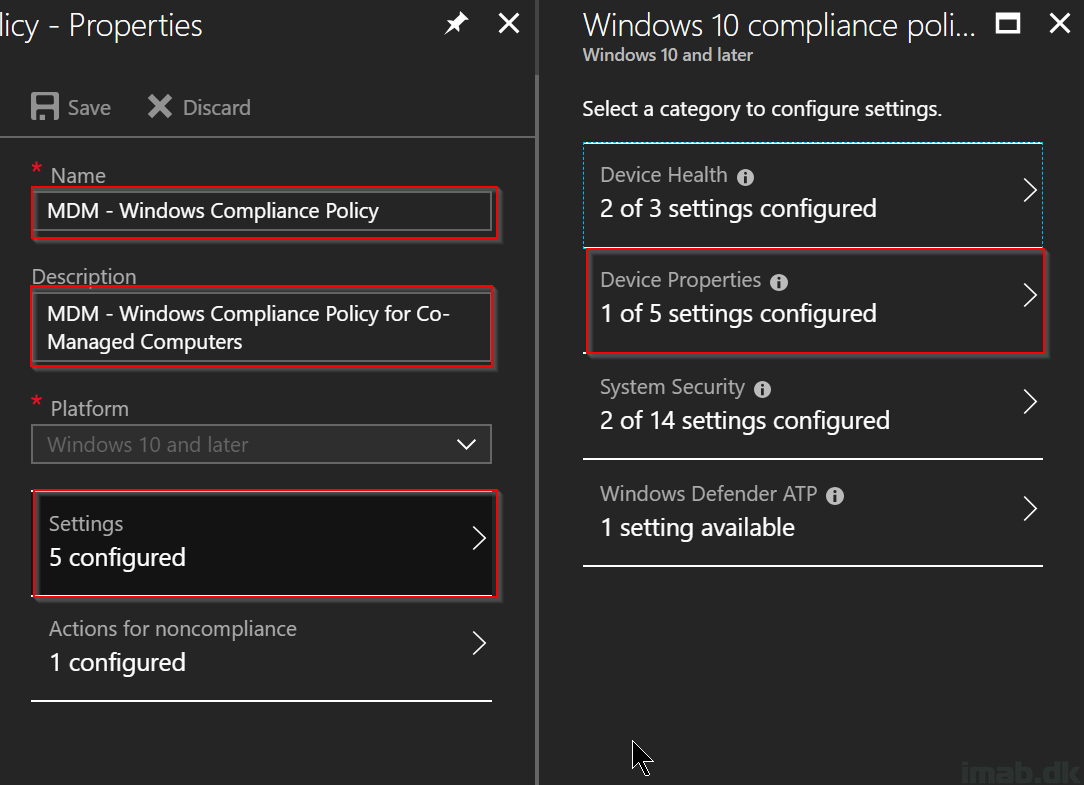
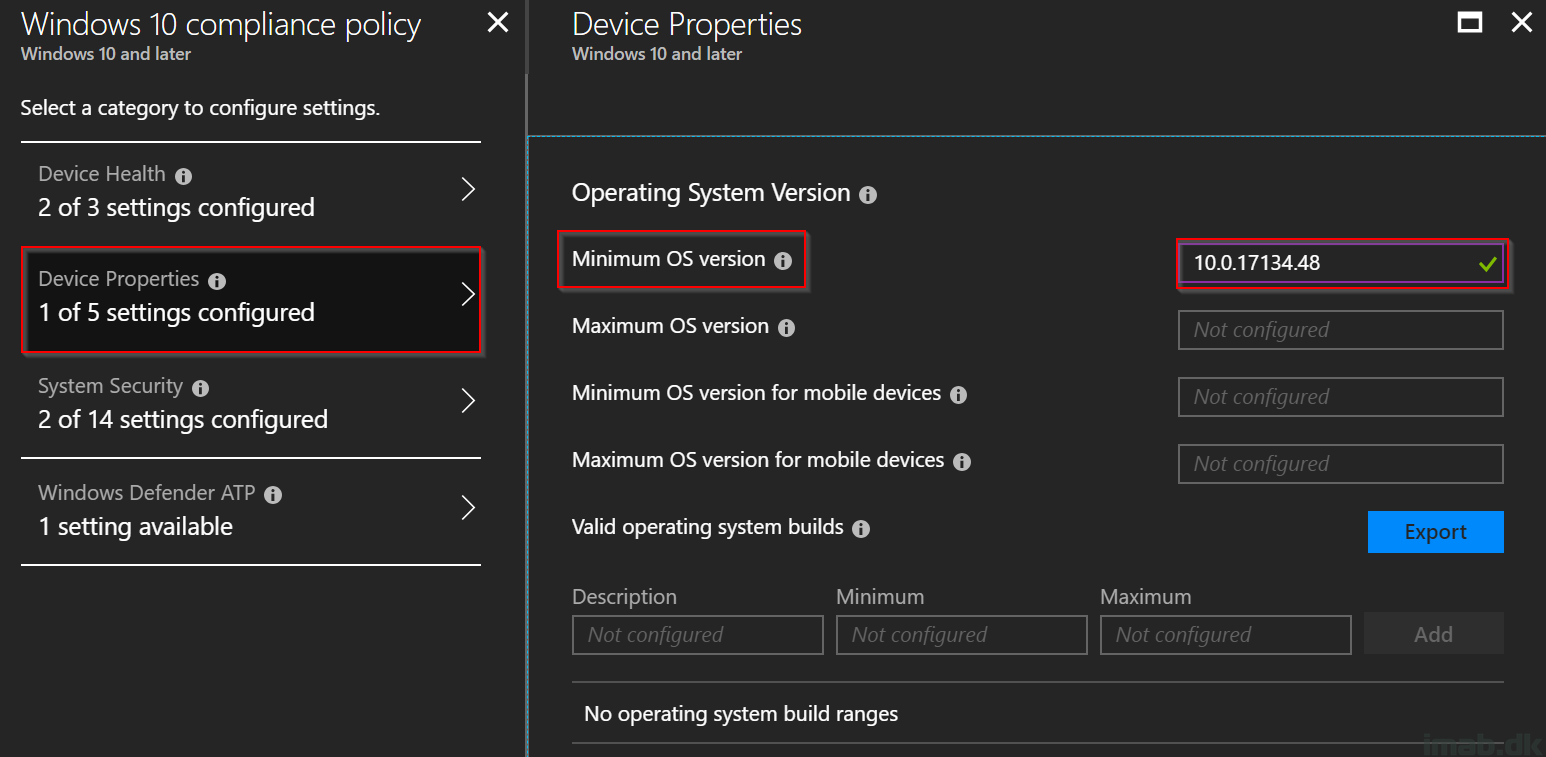
- Configure the Device Properties section as shown below
- Minimum OS version: 10.0.17134.48 (equals Windows 10 1803)
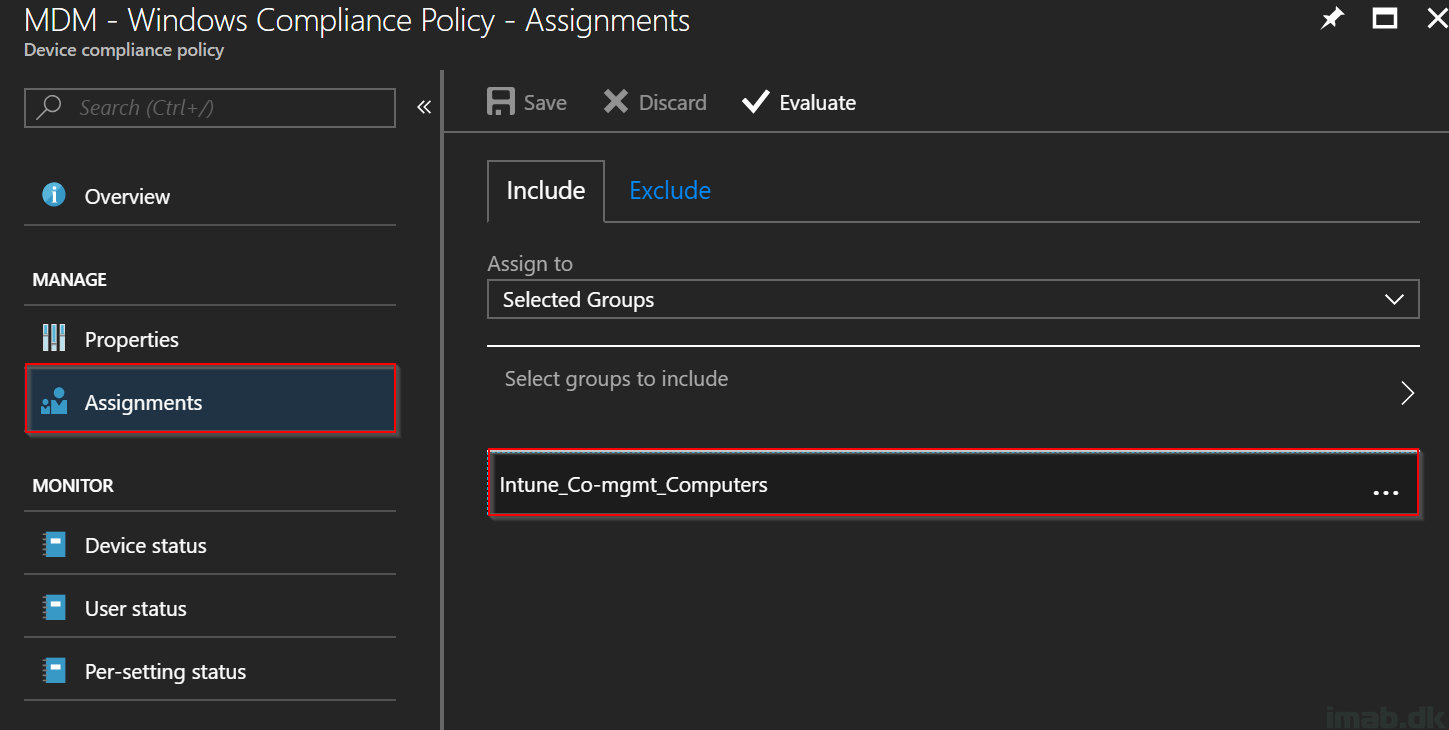
- Next, assign the Compliance Policy. In my Co-management test scenario, I’m assigning the policy to my co-managed computers. Depending on environment, this can be groups of users as well. Change as it fits your needs
Conditional Access
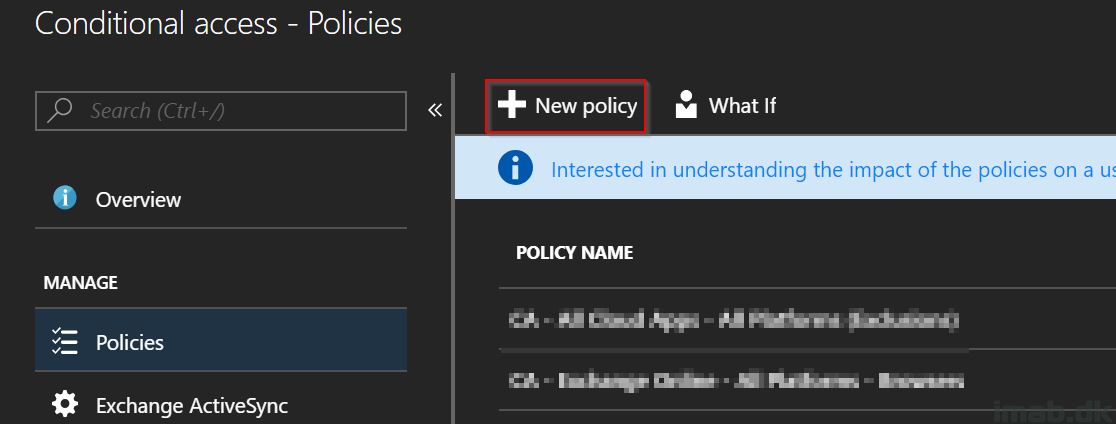
- Next up is the Conditional Access policy. This one is also created and managed through the Azure portal, in the Intune section -> Conditional Access.
- Create a new Conditional Access policy on +New Policy as shown below:
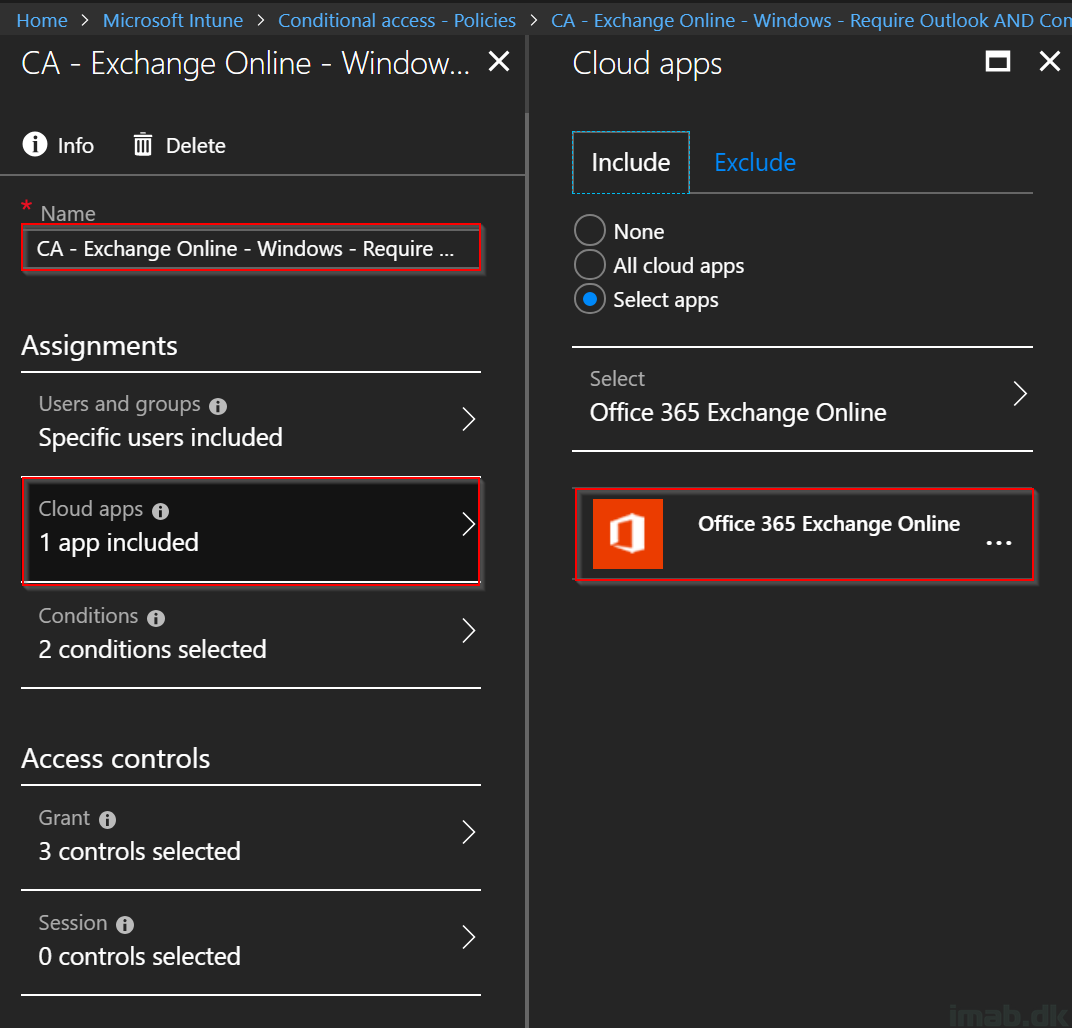
- Give it a suitable name. For inspiration, mine is called: CA – Exchange Online – Windows – Require AAD Joined AND Compliance
- Assign the policy to the desired user or a group consisting of users (not a bad idea to test this on a single user first)
- Select Office 365 Exchange Online in the Cloud apps section
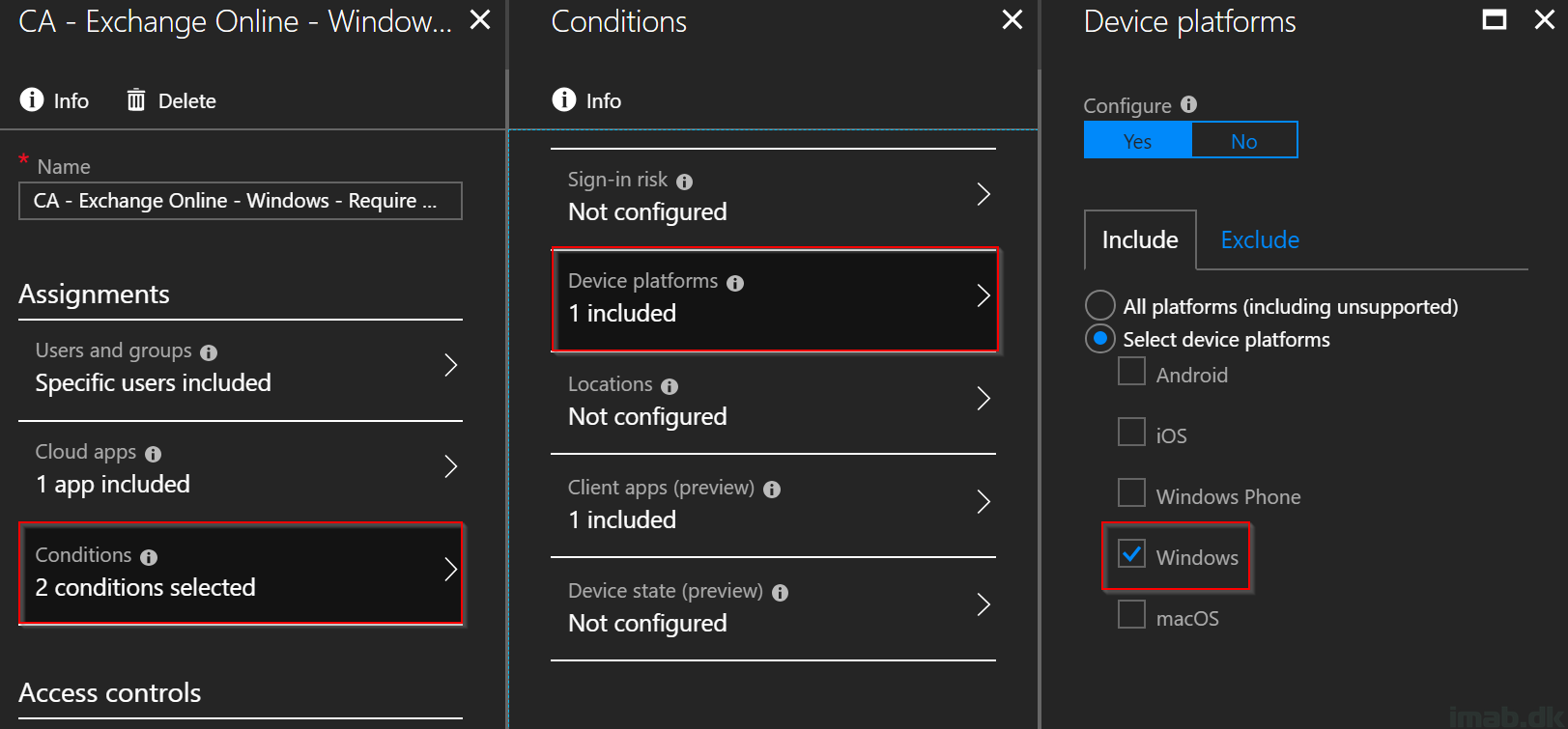
- In the Conditions section, select Device platforms and select Windows as shown below
- Continuing in the Conditions section, select Client apps (preview) and select Mobile apps and desktop clients as shown below (modern authentication will cover apps running modern authentication while other clients will cover most legacy apps. ActiveSync clients is held out on purpose in this demo due to the limit on additional conditions)
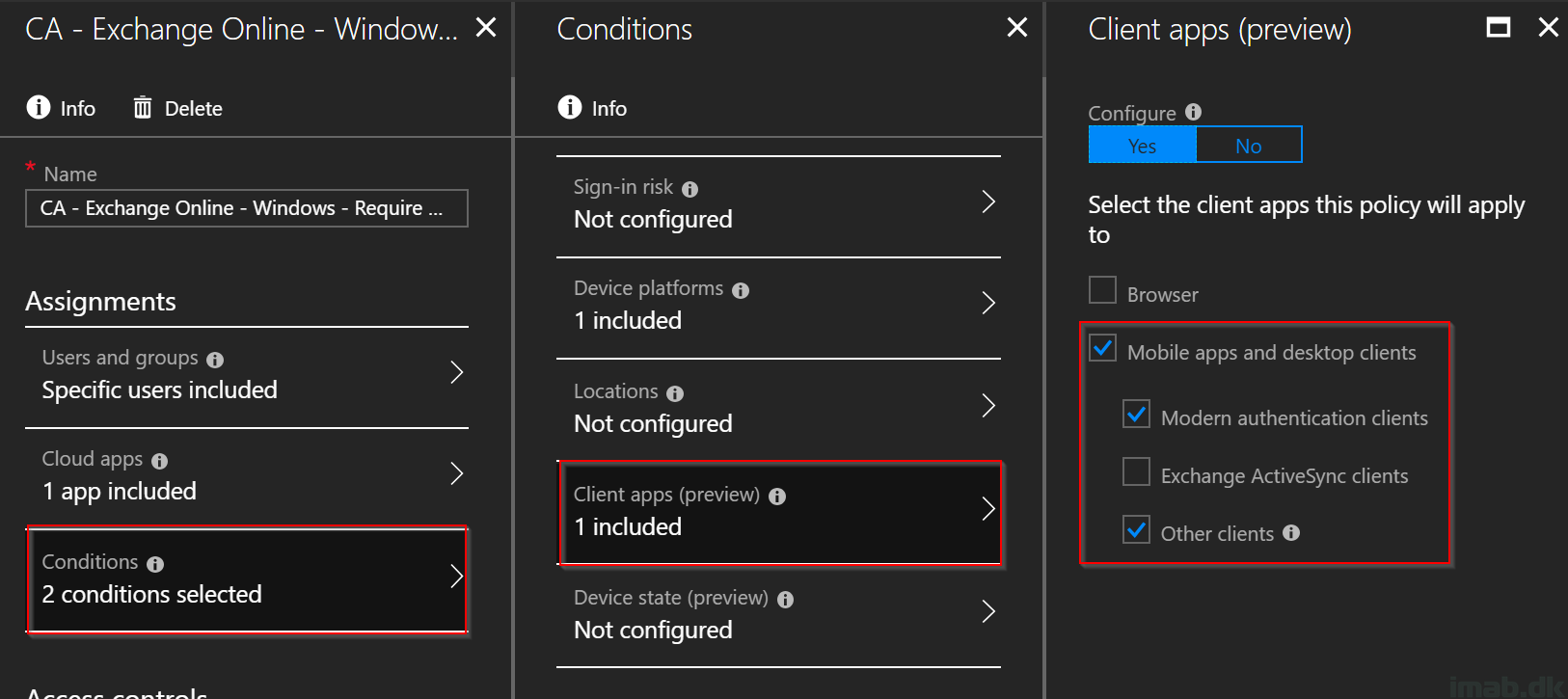
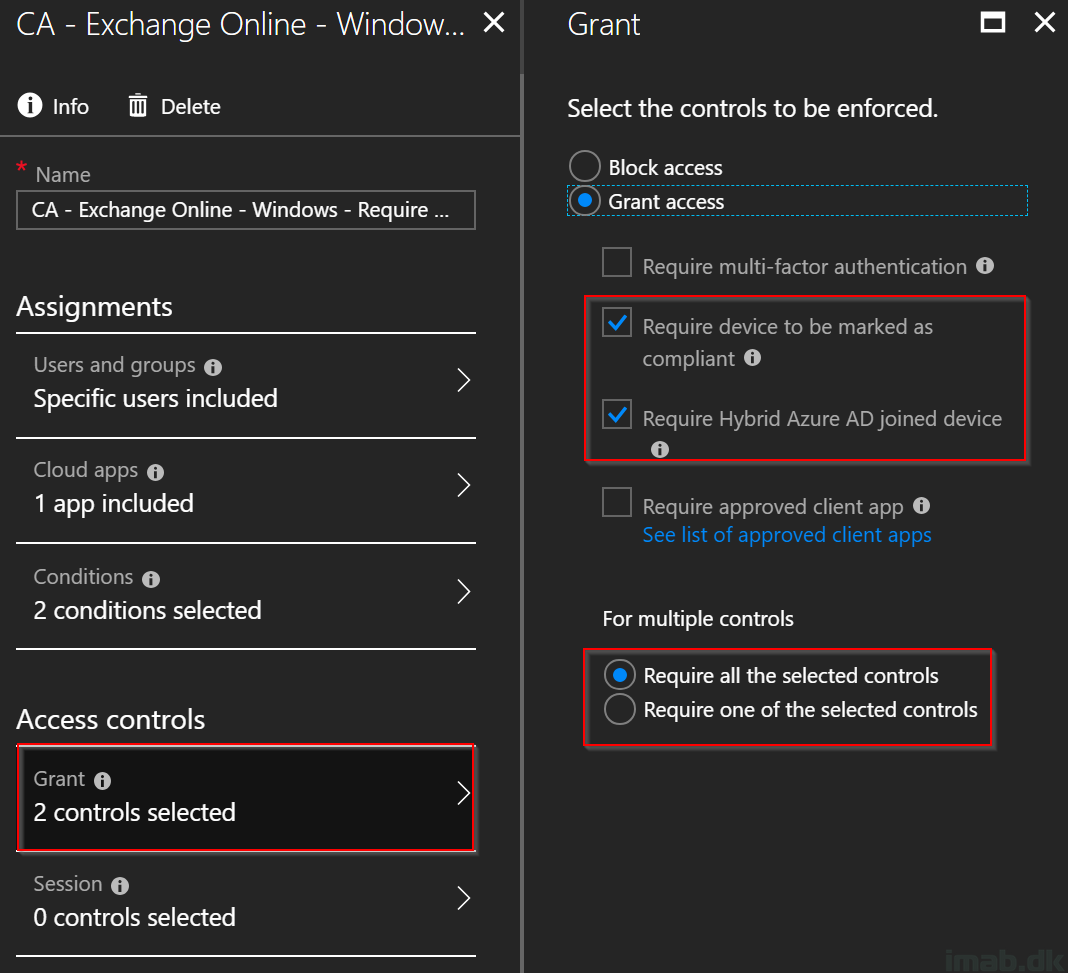
- Moving on to the final step; Grant. Select Grant access to Require device to be marked as compliant (the compliance policy will have effect here), Require Hybrid Azure AD joined device (the device has to be joined to an on-prem AD and registered in AAD)
- Select Require all the selected controls as well, which logically will create an AND between the two controls and thus require both of them
End user experience
So, enough with the configuration. How does it turn out from an end users perspective?
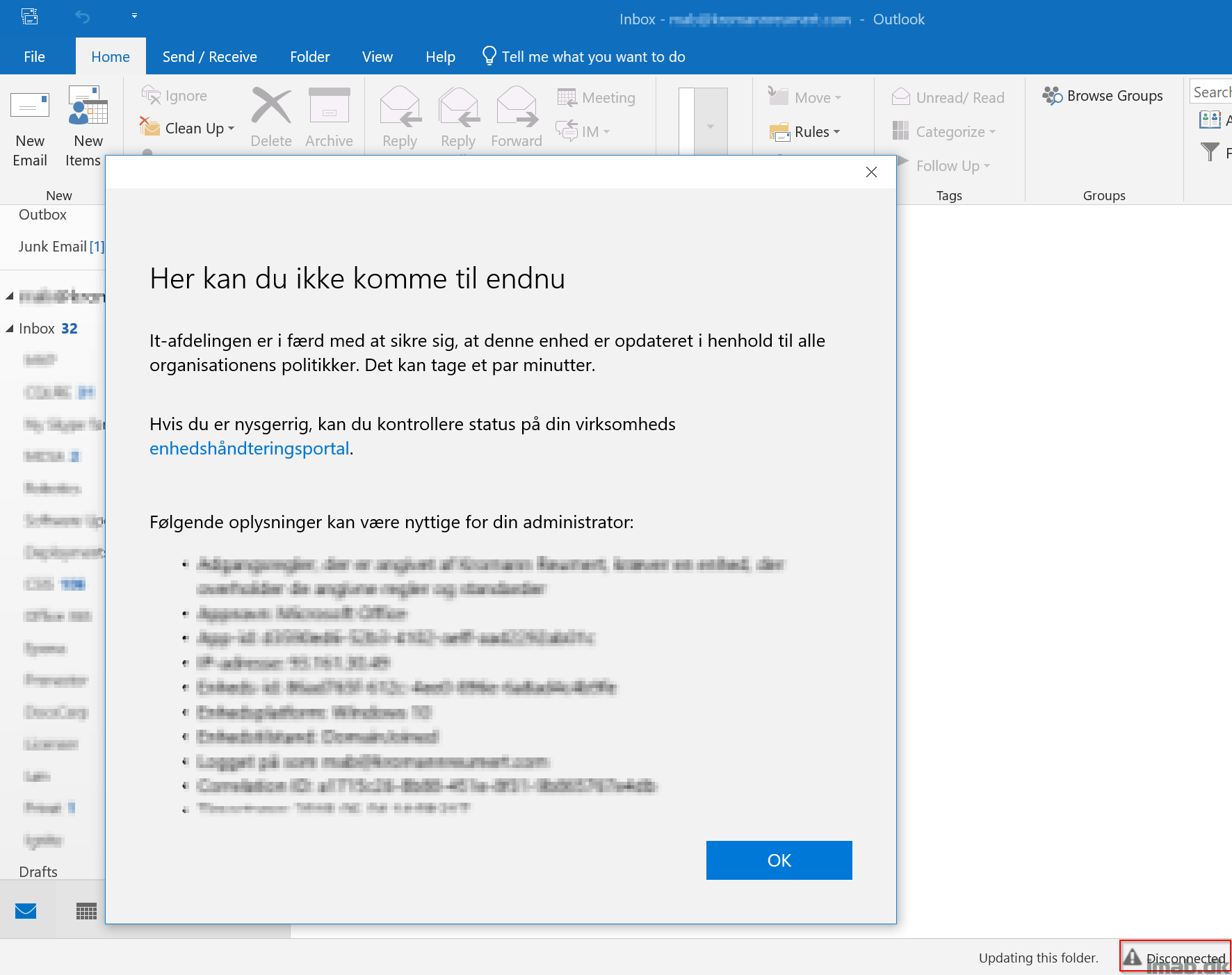
- Launching Outlook from a Windows 10 1709 ADD joined device and therefore non-compliant (sorry about the danish message)
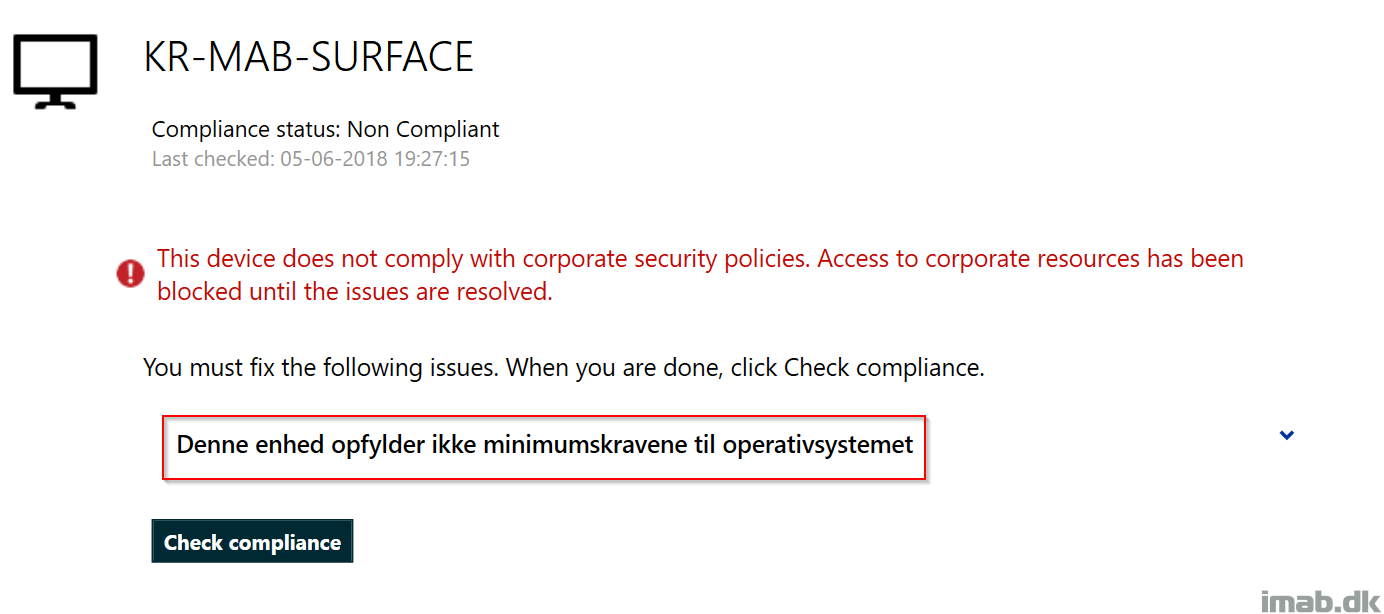
And when checking compliance in Software Center (Yes, that works with Intune in a Co-management scenario), I see following error (Again, sorry for the danish message). It says that the device doesn’t meet the minimum requirements for the OS.
And of course, if coming from a Windows 1803 device (compliant) AND AAD hybrid joined I’m granted access. Voila!
Please leave a comment, if this was useful 🙂
Very helpful indeed. Thanks!
Thank you 🙂