Introduction
First off, bear with me here during the intro. I know introductions usually are boring, but I do have a few words to share with you first.
The following is by no means any substitution for any other Modern Driver Management solution out there. This is purely me exploring, learning and sharing that experience with anyone who’s interested. When I find something useful, I usually try to do my own thing for various reasons, but mainly to learn and also for being less dependent on others work and future maintenance plans.
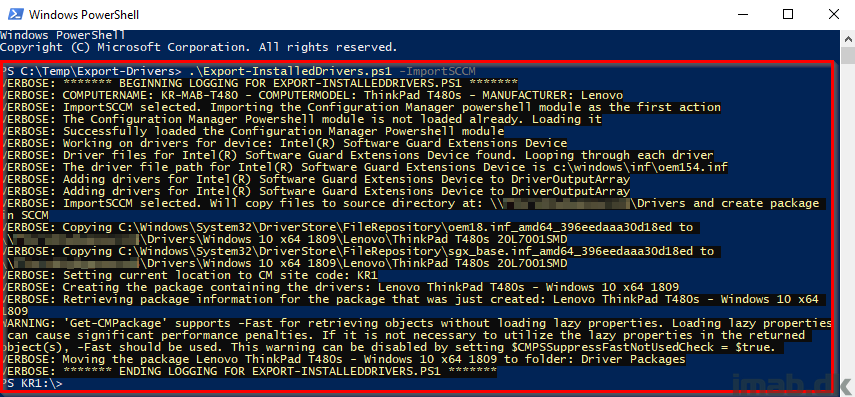
Now, this post is primarily about a Powershell script and how that Powershell script is designed to run on a given device and export the device drivers into your ConfigMgr source file library or locally. In the process, the script is able to create a regular package in ConfigMgr containing those drivers. The post is also about how to use the regular packages for applying drivers, but the script is what took the most of my time 🙂
The idea here is, that you fire up a given device with a given version of Windows (preferably Windows 10) and install ALL the drivers (preferably the latest drivers) and verify that everything works in that combination of Windows, drivers and hardware model.
Note: Most vendors provide a tool which checks online for latest drivers and gives you option to install those. This is pretty handy when building new drivers for a given computer model.
Now knowing that everything works, this is the drivers you want to apply to future deployments of this computer model, so you run the script and everything is automatically exported and a package in ConfigMgr is created.
In lack of a better name, this is what I call ‘Almost Modern Driver Management‘. 😀
PS. If you’re looking for a truly nifty and ‘modern’ approach, I suggest you head over to SCConfigMgr.com and take a peek at their solutions for both BIOS and drivers.