Introduction
First off, this is probably not for everyone. ConfigMgr and WSUS can deploy updates to the O365 ProPlus client just fine and most needs are probably satisfied this way. However, if you are interested in more visibility before, during and after deploying O365 updates to your users – read on!
After updating ConfigMgr to 1706 (from 1610 and 1702) something changed in the behavior of installing O365 ProPlus updates. Previously, in 1610 and 1702, the behavior was actually quite transparent for the end user: A restart flag is set and the update is installed after the computer restarts. This actually meant that you could deploy any update to o365 ProPlus and not worry about notifying your users about anything but the coming restart (which is somewhat similar to the behavior of standard software updates for Windows)
Coming ConfigMgr 1706, this changed dramatically to in-app notifications as well as forced shutdown of apps (and potential loss of unsaved work) if the right circumstances was in place. Also, when the apps are shut down, nothing is being displayed to notify the user about the progress, so most users will re-open the Office apps right away creating even more problems.
The Microsoft Docs article for the change in behavior is outlined right here: https://docs.microsoft.com/en-us/sccm/sum/deploy-use/manage-office-365-proplus-updates#restart-behavior-and-client-notifications-for-office-365-updates
I urge anyone managing O365 updates with ConfigMgr to give it a read and take notes of all the possible outcomes when deploying O365 updates this way. To quote the important ones (note all the maybe’s, which makes the experience really inconsistent):
- A pop-up notification might not display until the user clicks the icon in the notification area. In addition, if the notification area has minimal space, the notification icon might not be visible unless the user opens or expands the notification area
- If the deadline is in the past or configured to start as soon as possible, running Office apps might be forced to close without notifications (they do – yay)
- The in-app notification bar does not display on an Office app that is running before the update is downloaded. After the update is downloaded, the in-app notification displays only for newly opened apps (the yellow in-app bar is inconsistent. Sometimes it shows, sometimes it doesn’t. Reopening apps or not)
So, enough with the ranting. Above is the facts about the poor user experience when running ConfigMgr 1706. Below will be how I used something totally different to create visibility for our users.
Powershell App Deployment Toolkit!
We all know the infamous Powershell App Deployment Toolkit: http://psappdeploytoolkit.com/. (And if you don’t, that’s another day and another blog post 🙂
Below is exactly how (and along the lines, why) I chose to leverage the use of the Powershell Deployment Toolkit and the ODT to deploy O365 updates in my organization.
Configuration
Create the Office Deployment Tool .xml file (Update.xml)
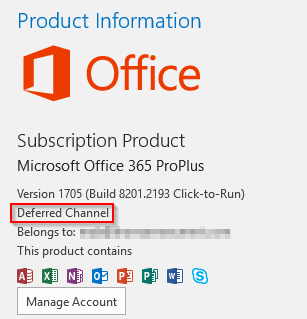
The ODT relies on a .xml file. That is whether you want to update or downgrade your Office 365 ProPlus installation. In this scenario I want to update, and for this I can specify exactly what build I want to update to. If you don’t specify a version, you will be updated to the latest build in your channel. A lot of the content in the .xml is optional, and something you also can manage through ConfigMgr or GPOs.
This is exactly the .xml file I’m using to update my Monthly Channel (previously called Current Channel) clients to the latest build. I manage the channel through GPOs, which is why you don’t see the channel being set in my .xml.
<Configuration>
<Add OfficeClientEdition="32" Version="16.0.8730.2127" OfficeMgmtCOM="True" >
<Product ID="O365ProPlusRetail">
<Language ID="en-us" />
<ExcludeApp ID="Groove" />
<ExcludeApp ID="InfoPath" />
<ExcludeApp ID="Publisher" />
<ExcludeApp ID="SharePointDesigner" />
</Product>
</Add>
<Logging Level="Standard" Path="C:\Windows\Temp" />
<Display Level="None" AcceptEULA="TRUE" />
<Property Name="AUTOACTIVATE" Value="1" />
<Property Name="FORCEAPPSHUTDOWN" Value="TRUE" />
</Configuration>
Create the folder structure
This is optional and just an illustration of how I do it. I have a complete folder structure in my source file library equal to something similar to this:
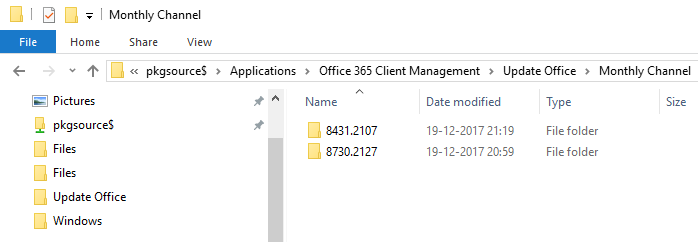
8431.2107 and 8730.2127 are build numbers and is respectively version 1708 and 1711. Complete list of all the builds numbers and release dates for Monthly and Semi-Annual channel, look here!
Inside each build number, I have the Powershell Deployment Toolkit:
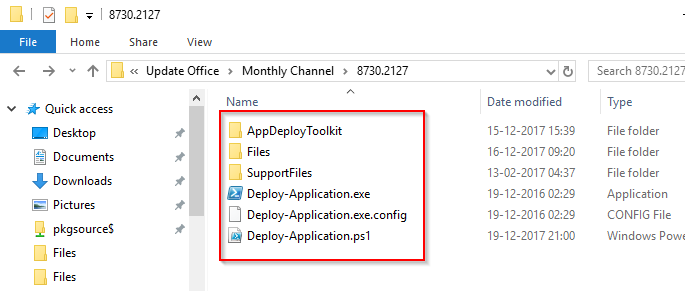
Inside the Files folder, I put my newly created Update.xml along side the Setup.exe from the ODT and a Update.bat file (which is what we will have the PS Deployment Toolkit running) containing following:
@echo off
“%~dp0setup.exe” /configure “%~dp0Update.xml”
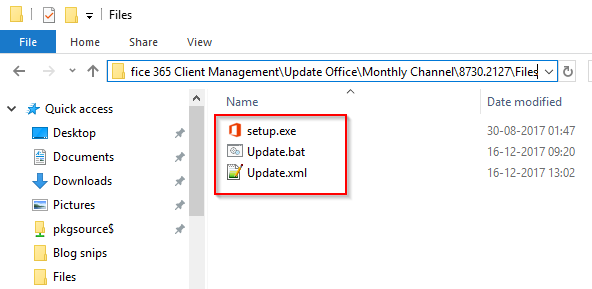
I’m using a batch file to wrap the installation into, for the diversity and simplicity. If needed I can quickly edit the batch file, update DPs and move on (opposed to edit the PowerShell script)
Roll-back and downgrade
If needed, you can have the ODT (Setup.exe) to downgrade the version of Office 365 ProPlus as well. This is also done configuring the proper settings in an .xml file.
Below is my .xml file used to downgrade Office 365 ProPlus. Notice ForceDowngrade=”True” which is required if you are moving backwards (a SaaS like this, is meant to move forward 🙂 Again, take a look at this page for knowledge about the different versions/builds for your channel: here!
<Configuration>
<Add OfficeClientEdition="32" Version="16.0.8431.2107" OfficeMgmtCOM="True" ForceDowngrade="True">
<Product ID="O365ProPlusRetail">
<Language ID="en-us" />
<ExcludeApp ID="Groove" />
<ExcludeApp ID="InfoPath" />
<ExcludeApp ID="Publisher" />
<ExcludeApp ID="SharePointDesigner" />
</Product>
</Add>
<Logging Level="Standard" Path="C:\Windows\Temp" />
<Display Level="None" AcceptEULA="TRUE" />
<Property Name="AUTOACTIVATE" Value="1" />
<Property Name="FORCEAPPSHUTDOWN" Value="TRUE" />
</Configuration>
This I wrap into a Downgrade.bat as well inside the Files folder of the Powershell Deployment Toolkit. (In a separate folder. For a separate package in ConfigMgr.)
@echo off
“%~dp0setup.exe” /configure “%~dp0Downgrade.xml”
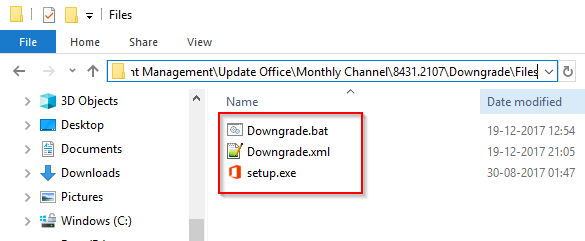
The above configurations is made to actually download the differences in bits directly from the Office CDN. This is also something to consider if using this method. However, you can specify SourcePath=”” to let the installation grab the bits from a local source if desired. Microsoft has specified the download sizes in this post here!
<Add OfficeClientEdition="32" OfficeMgmtCOM="True" SourcePath="\\Server\Share\Monthly Channel" >
Deployment
With all of above in place, you will be ready for deployment with ConfigMgr. Note that I assume that you know your way around the Powershell Deployment Toolkit.
To target the update of Office to the proper computers, I use collections. ConfigMgr is able to inventory a lot of useful information regarding the Office 365 ProPlus client which includes the current version, channel etc:
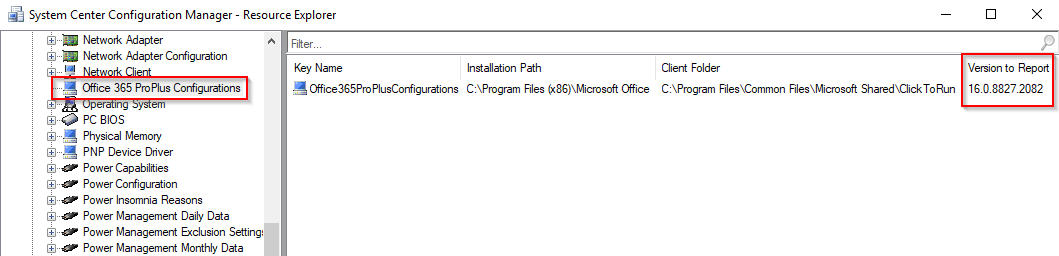
This query example will give you all computers that: Has Office 365 ProPlus installed, runs on Current Channel set through GPO and is NOT already on the latest 1711 build. (This should probably be altered to fit your needs and environment, depending on various factors)
select SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client from SMS_R_System inner join SMS_G_System_ADD_REMOVE_PROGRAMS_64 on SMS_G_System_ADD_REMOVE_PROGRAMS_64.ResourceID = SMS_R_System.ResourceId inner join SMS_G_System_OFFICE365PROPLUSCONFIGURATIONS on SMS_G_System_OFFICE365PROPLUSCONFIGURATIONS.ResourceID = SMS_R_System.ResourceId where SMS_G_System_ADD_REMOVE_PROGRAMS_64.DisplayName like "Microsoft Office 365 ProPlus%" and SMS_G_System_OFFICE365PROPLUSCONFIGURATIONS.GPOChannel = "Current" and SMS_R_System.NetbiosName not in (select SMS_R_System.NetbiosName from SMS_R_System inner join SMS_G_System_OFFICE365PROPLUSCONFIGURATIONS on SMS_G_System_OFFICE365PROPLUSCONFIGURATIONS.ResourceID = SMS_R_System.ResourceId where SMS_G_System_OFFICE365PROPLUSCONFIGURATIONS.VersionToReport = "16.0.8730.2127")
With this in place, you will have isolated the computers in need of being a target for your Office 365 ProPlus update.
Finally
Now there’s only a few steps left, but I assume you already know how to:
- Customize your Powershell Deployment Toolkit to your needs
- Close the Office apps, and keep them closed (prevent users from starting any, until the installation is done)
- Keep the user notified during the entire process through custom dialogs
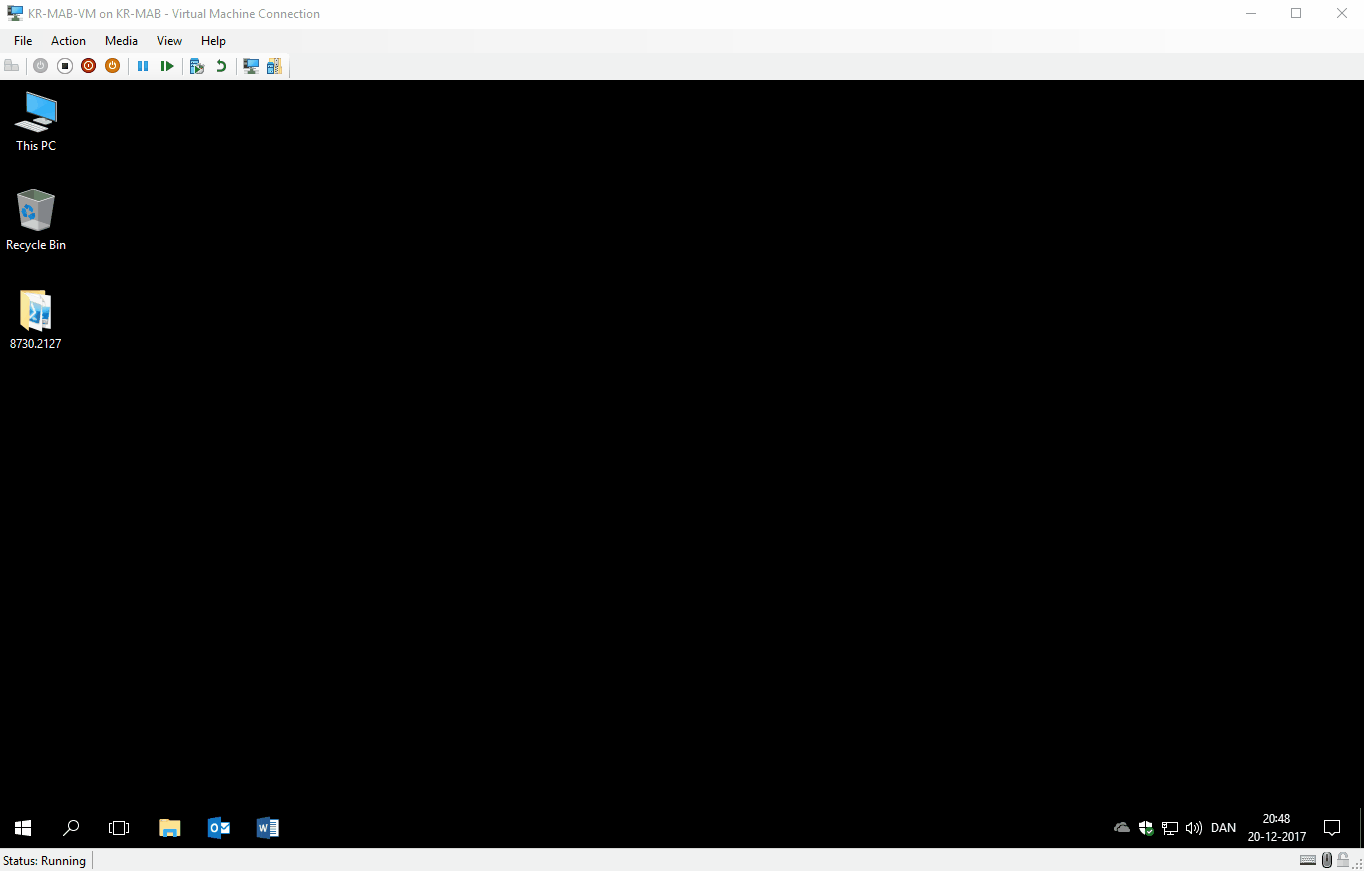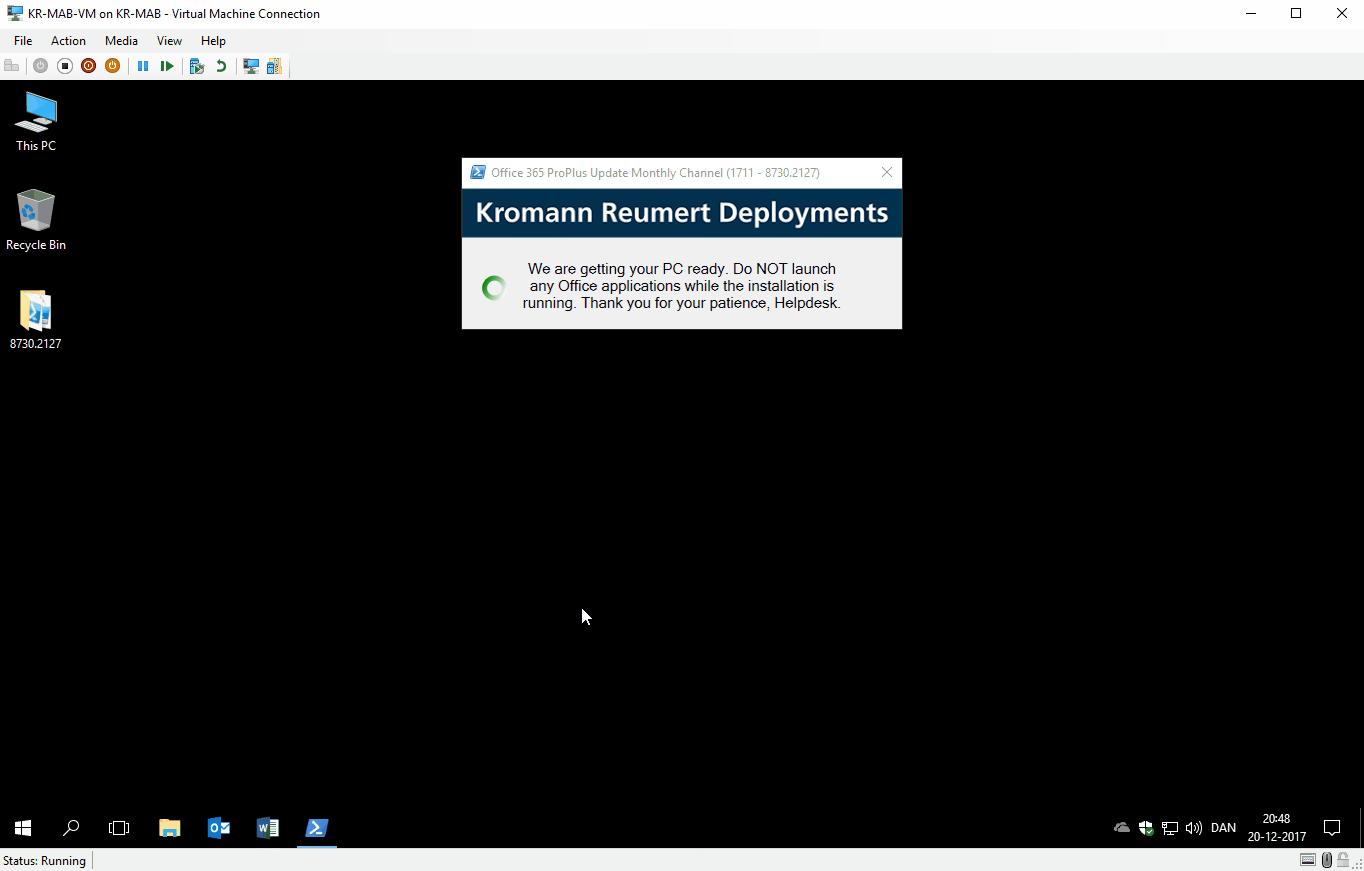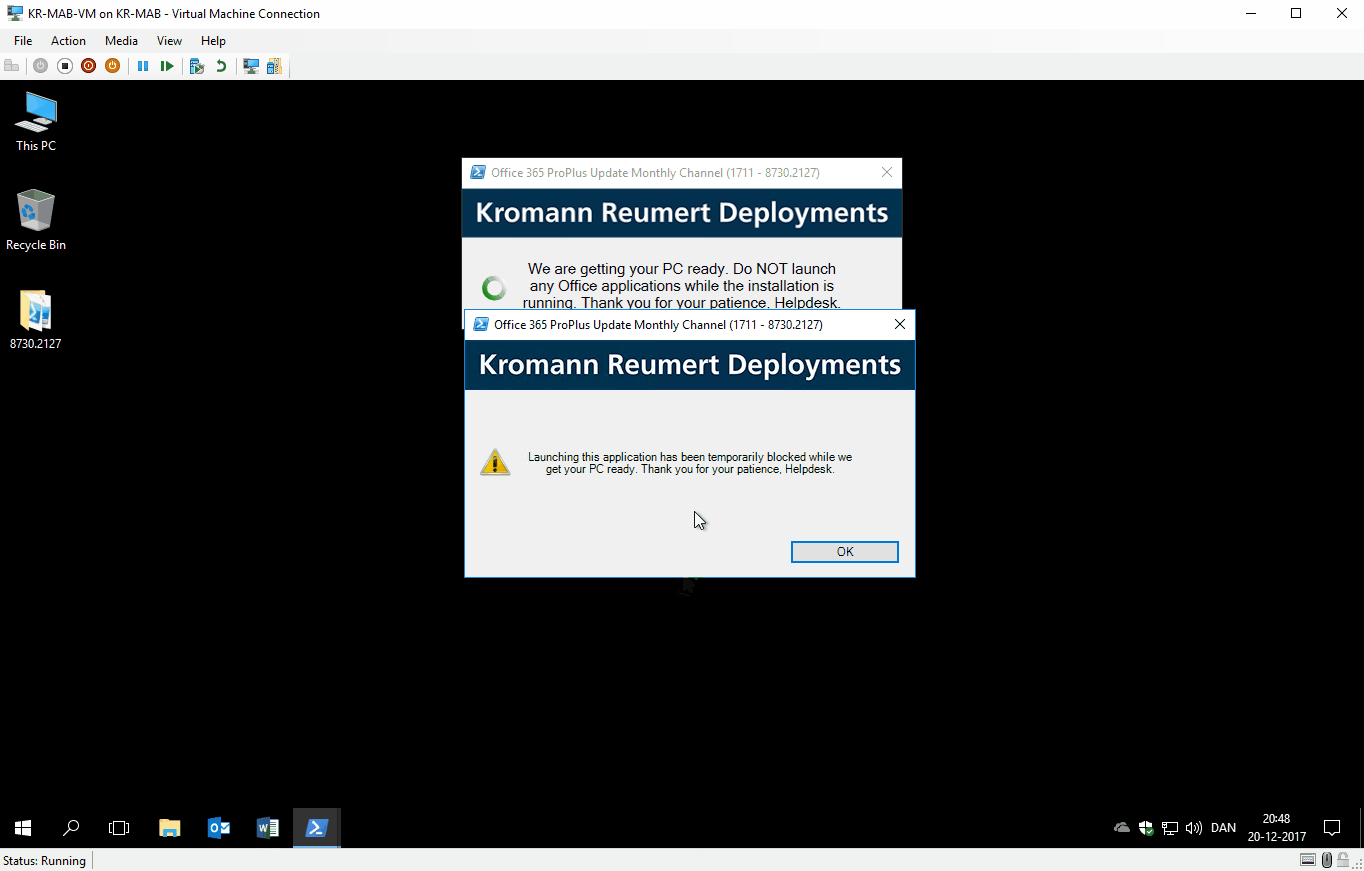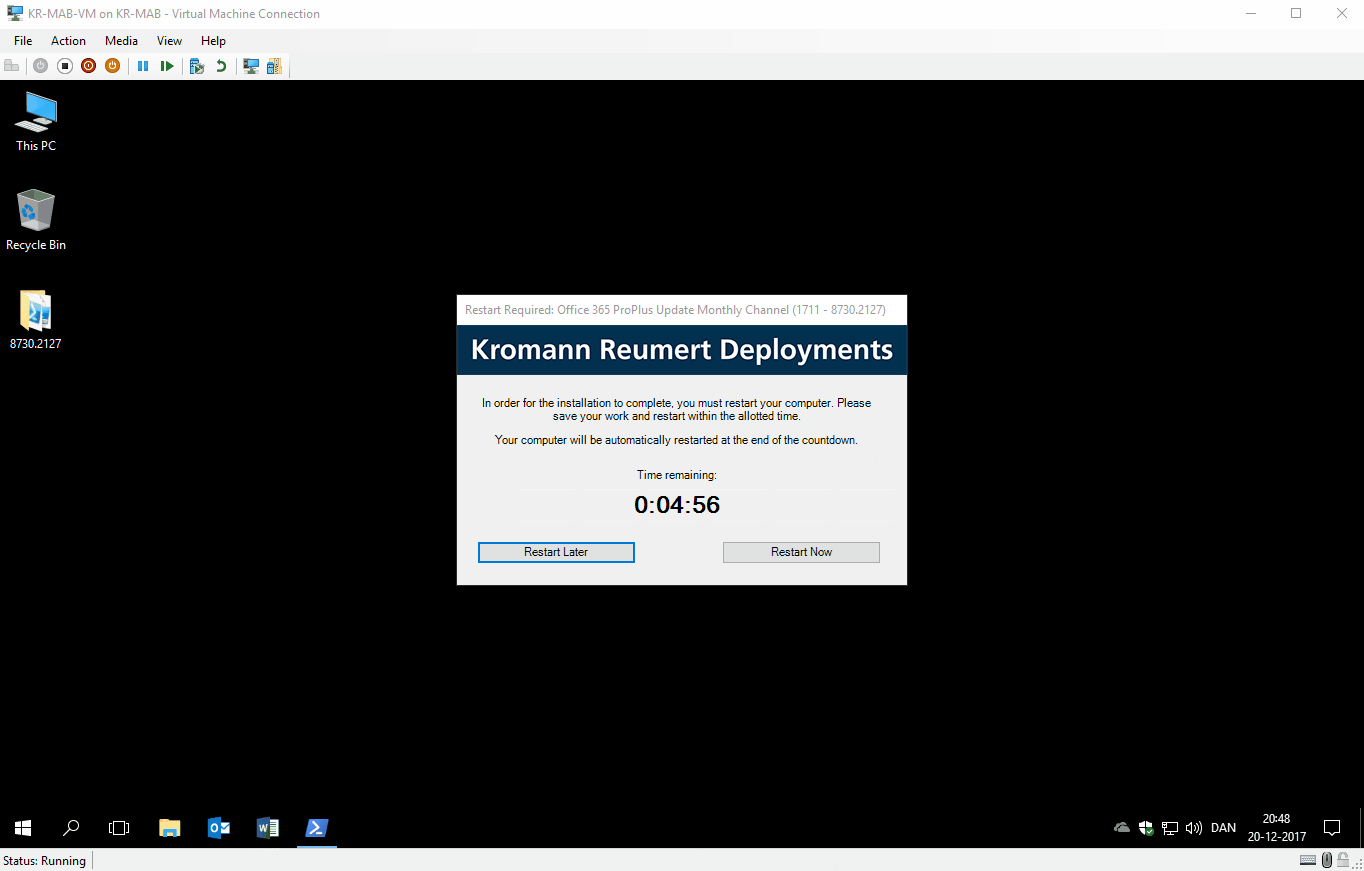
- Show a friendly restart dialog, prompting the user to restart within allotted time
- Create a package in ConfigMgr, distribute to your favorite DPs
- Test the deployment
- Deploy to your users
- Be happy about the process being a lot smoother in regards to user friendliness.
GIF of everything in action: Installation running, user trying to open Word and the dialogs that follow.