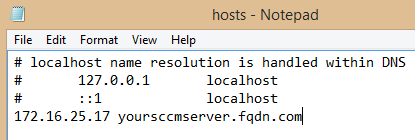
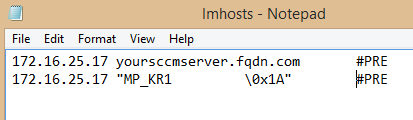
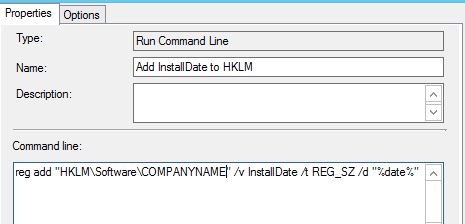
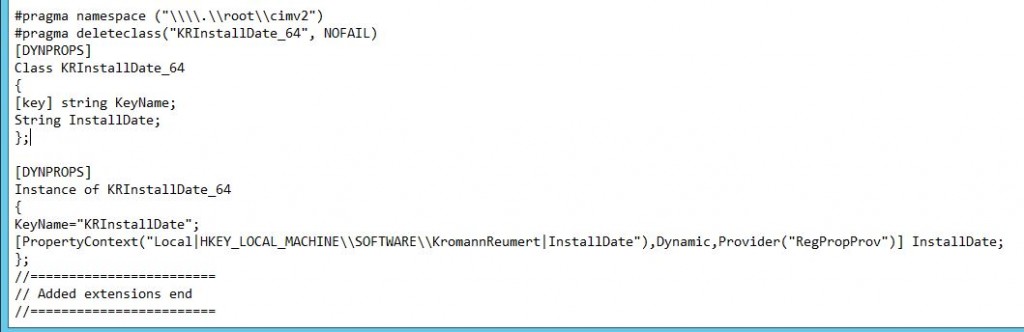
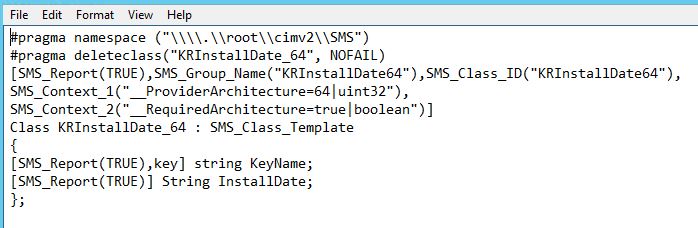
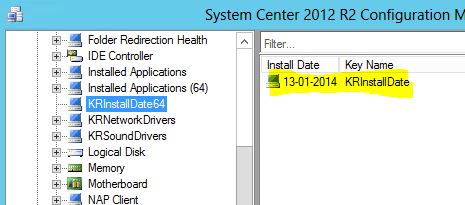
I’m currently investigating some potential boundary issues related to the use of AD sites. Therefore I was looking for some more details on how content download is behaving considering slow and fast links in the environment.
This is some of the tests I did and the results thereof:
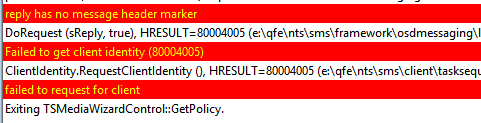
Action: Deploying software-package as available to a client which is within a slow boundary.
Result: Policy is received and entry in Software Center visible. Launching the installation gives following entry in the execmgr.log:
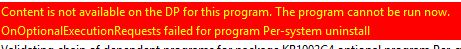
Action: Change the deployment options to Download content from distribution point and run locally when the client is within a slow or unreliable boundary. Refresh machine policy, and run the installation from Software Center again.
Result: This time execmgr.log immediately respondend with a successful content request.
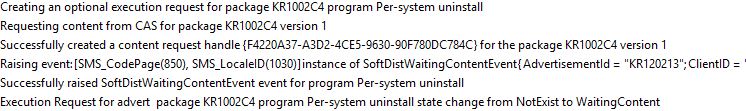
And while digging further into LocationServices.log, do notice following entries:
Distribution Point=’http://DP1.MYDOMAIN.COM/SMS_DP_SMSPKG$/KR1002C4′, Locality=’REMOTE’, DPType=’SERVER’, Version=’7958′, Capabilities='<Capabilities SchemaVersion=”1.0″><Property Name=”SSLState” Value=”0″/></Capabilities>’, Signature=’http://DP1.MYDOMAIN.COM/SMS_DP_SMSSIG$/KR1002C4′, ForestTrust=’TRUE’,
Distribution Point=’http://DP2.MYDOMAIN.COM/SMS_DP_SMSPKG$/KR1002C4′, Locality=’REMOTE’, DPType=’SERVER’, Version=’7958′, Capabilities='<Capabilities SchemaVersion=”1.0″><Property Name=”SSLState” Value=”0″/></Capabilities>’, Signature=’http://DP2.MYDOMAIN.COM/SMS_DP_SMSSIG$/KR1002C4′, ForestTrust=’TRUE’,
Locality=’REMOTE’, which identifies the client as being in a slow and unreliable boundary, which in this case is very true, but the software deployment is still running because of the change of options on the deployment.
When a client is within a fast and reliable boundary of the site, the entry would look like this, as in the locality of the client is local.
Distribution Point=’http://DP1.MYDOMAIN.COM/SMS_DP_SMSPKG$/KR1002C4′, Locality=’LOCAL’, DPType=’SERVER’, Version=’7958′, Capabilities='<Capabilities SchemaVersion=”1.0″><Property Name=”SSLState” Value=”0″/></Capabilities>’, Signature=’http://DP1.MYDOMAIN.COM/SMS_DP_SMSSIG$/KR1002C4′, ForestTrust=’TRUE’,
Client logs to consider when troubleshooting boundaries and content download:
execmgr.log
ClientLocation.log
LocationServices.log